BIP Brochure2010 简化版
- 格式:pdf
- 大小:1.37 MB
- 文档页数:17

MASTER OF BUSINESS ADMINISTRATION(MBA)ACADEMIC MANUALThe Claflin Imperative:Preparing Professionals for Leadership and Service in a Multicultural, Global and Technological SocietySchool of BusinessClaflin UniversityOrangeburg, South Carolina2005-2006ABOUT THIS MANUALThis manual provides information regarding the Master of Business Administration (MBA) Program offered by Claflin University for the 2005-2006 academic years. Please refer to the Claflin University Catalog 2004-2007 for information concerning all of the undergraduate programs offered by Claflin University and general academic policies.The statements made in this manual are for informational purposes only and should not be construed as the basis of a contract between a student and this institution. Claflin University reserves the right to revise information, including but not limited to academic requirements for graduation, with providing actual or constructive notice to individual students. Every effort will be made to keep students advised of any changes. Notices of changes made by the University or by the School of Business will be available in the Office of the Director of the MBA Program.Although every reasonable effort was made to present the information contained in this manual with factual accuracy, Claflin University assumes no responsibility for editorial, clerical or printing errors. Copies of this manual may be obtained from the Office of the Director of MBA Program (803-535-5200).Student ResponsibilityEach student is responsible for the proper completion of the requirement of his/her academic program as set out in this manual. While faculty advisers are available to assist in this regard, the primary responsibility rests with individual students.Unpublished ChangesClaflin University reserves the right to add or drop programs and courses, to change fees, to change the calendar which has been published and to institute new requirements when such changes appear desirable. Every effort will be made to minimize the inconvenience such changes might create for students. Suitable substitutions will be allowed for required courses, which have been withdrawn.ComplianceClaflin University offers equal opportunity in employment, admissions and education activities in compliance with civil rights laws set out below:•Title VI of the Civil Rights Act of 1964“No person in the United States shall, on the basis of race, color or national origin, be excluded from participation in, be denied the benefits of, or be subjected todiscrimination under any educational program or activity receiving federal financial assistance.”•Title IX of the Education Amendment of 1972“No person in the United States shall, on the basis of sex, be excluded fromparticipation in, be denied the benefits of, or subjected to discrimination under any educational program or activity receiving federal financial assistance.”•Section 504 of the Rehabilitation Act of 1973“No otherwise qualified handicapped individual in the United States…shall, solely by reason of his handicap, be excluded from the participation in, be denied thebenefits of, or be subjected to discrimination under any program or activityreceiving federal financial assistance.”•Section 303 of the Age Discrimination Act of 1975“No person in the United States shall, on the basis of age, be excluded fromparticipation in, be denied the benefits of, or be subjected to discrimination underany program or activity receiving federal financial assistance.”MESSAGE FROM THE PRESIDENTIt gives me great pleasure to welcome you to the Master of Business Administration Program at historic Claflin University. The University continues to do the work that distinguishes it from other peer institutions. The commitment to be the best is evident in the quality of students who chose to attend the University. The level of experience and professional knowledge of the faculty, and the depth of services provided to our students ensure that the learning experience is positive. In fact, commitment to academic excellence is our first priority.As we confront the struggles of living in an environment where change is the norm, we are fortunate to be part of an academic community dedicated to seeking truth. Our approach to graduate study encompasses the intellectual, spiritual, and communal components of humanity that are imperative as we continue to seek meaning in our current lives, understand the complexities of the global situation, and build hope for and faith in the future. Therefore, as you study to develop the leadership skills necessary for effective management in a variety of venues, we encourage you to remain vigilant in your service to humanity.The Claflin University family is dedicated to providing you support as you pursue your graduate degree. We are confident that you will find the required resources necessary to make your studies a success.Henry N. TisdalePresidentCLAFLIN UNIVERSITY GUIDING PRINCIPLES :Commitment to ExcellenceCommitment to Valuing PeopleCommitment to Being Customer FocusedCommitment to Quality Educational ProgramsCommitment to Financial ResponsibilityTABLE OF CONTENT PAGE About This ManualStudent ResponsibilityUnpublished ChangesComplianceMessage From The PresidentClaflin’s University Guiding PrinciplesReference DirectoryAcademic CalendarSpring Semester 2005Summer Semester 2004Claflin UniversityHistoryMissionPhilosophyAccreditationThe CampusDivision of Business AdministrationIntroduction and ObjectivesAcademic ProgramsAccreditationFaculty/StaffMaster of Business Administration (MBA)Introduction and ObjectivesAdmissionsAdmissions RequirementAdmissions PeriodApplication ProceduresAdmission CriteriaAdmission StatusGraduation RequirementsMBA Expenses and Financial AidTuition and FeesRefund PolicyFinancial AidTABLE OF CONTENT PAGE MBA Academic Standards and RequirementsRegistrationCourse LoadTransfer CreditsGrading SystemAcademic CreditRepeating CoursesIndependent StudyWithdrawal from the UniversitySatisfactory Academic ProgressCommencementConfidentiality of Student RecordsTranscriptsStudents RegulationsAcademic DishonestyPolicy Concerning DrugsPolicy Concerning Sexual AssaultPolicy Concerning Sexual HarassmentStudent ServicesLibraryCareer Counseling & DevelopmentCafeteria ServicesAthletic ActivitiesUniversity ID CardParkingMBA CurriculumMBA CoursesCourse ScheduleCourse DescriptionQUICK REFERENCE DIRECTORY-Admissions Office………………………………………………………...(803) 535-5471 Ms. Katherine R. Boyd Suite #5, Tingley HallDean of Enrollment Management-Academic Affairs………………………………………………………...…(803) 535-5401 Dr. Howard D. Hill………………………………………… Suite #9, Tingley Hall PresidentVice-Campus Information……………………….………………………………(803) 535-5000-MBA Program……………………….……………………………………..(803) 535-5745Dr. Diane Prince, Director Room#105 GTK Building-School of Business………………...……………………………………….(803) 535-5202 Dr. Harpal S. Grewal, Dean…………………………….Room#102, GTK Building-School of Education…………………………………….……………….…(803) 535-5225BowenHallDean….…………………..………..Room#137,,Dr.-School of Humanities and Social Sciences…………….…………………(803) 535-5233 Dr. Peggy S. Ratliff, Dean…………………………………Room #3, Trustee Hall-School of Natural Sciences and Mathematics……………………………(803) 535-5433 Dr. Verlie Tisdale, Dean………………………………..Room#207, JST Building-Events Information Line…………………………………………………..(803) 535-5392-Financial Aid……………………….………………………………….…. .(803) 535-5720 Ms. Sheri Jefferson, Director ……………………………….Suite#12, Tingley Hall-Food Services…………………………………………………..…………..803) 535-5261-Game Room………………………………………………………………(803) 535-5592 Mr. Hampton Jordon, Coordinator Campus Center, Lower Level-Infirmary (Health Services)……………………………………………….(803) 535-5328 Mrs. Thelma Middleton, Nurse University Infirmary Building-Institutional Planning and Assessment…………………………………..(803) 535-5219 Dr. Zia Hasan, Vice President Suite ___, Tingley Hall-Leadership Development Center…………………………………………(803) 535-5400 Dr. Roosevelt Ratliff, Assistant Vice President Leadership Center Building-Library……………………………………………………………………(803) 535-5309 Ms. Marilyn Pringle, Head Librarian H.V. Manning Library-Post Office………………………………………………………………..(803) 535-5353 Ms. Annette Mack Living and Learning Center-President…………………………………………………………………..(803) 535-5412 Dr. Henry N. Tisdale Suite#7, Tingley Hall-Public Relations…………………………………………………………..(803) 535-5351 Ms. Helene Carter, Director Suite#7, Tingley Hall-Reprographics Services Center…………………………………………..(803) 535-5474 Ms. Brenda Sylvester Russell Street Campus-Security…………………………………………………….(803) 535-5444 or 535-5445 Mr. Kenneth McCaster, Chief Check-Student Accounts…………………….…………………………………….(803) 535-5432 Ms. Hattie Harmon, Cashier Suite#12, Tingley Hall-Student Activities…………………………………………………………(803) 535-5591 Mr. Hampton Jordon, Director Campus Center, Lower Level-Student Development and Services………………………………………(803) 535-5341 Dr. Leroy Durant, Vice President Room#107, Layman Hall-Toll Free Number…………………………………………………………(800) 922-1276 (Admission and Financial Aid)-University Mailing Address:-Claflin University-400 Magnolia Street-Orangeburg, SC 29115CLAFLIN UNIVERSITY400 Magnolia StreetOrangeburg, South CarolinaSPRING ACADEMIC CALENDAR20058 Saturday 9:00-10:00 Orientation for new MBA’sJanuaryStudentsMBAfor10:00–2:00RegistrationBeginMonday ClassesJanuary10beginsregistrationLatedayLastto Register and/or Add ClassesFridayJanuary14Monday Dr,Martin Luther King Jr., Holiday17JanuaryClasses Suspended –Office and Library ClosedMBA Classes will still meetFebruary 1 – 28 Tuesday Black History MonthFridayFebruary 9 Tuesday MBA MFAT TestFebruary 15 Tuesday MBA Graduation ApplicationDeadlineFebruary 20-23 Sunday Religious Emphasis WeekWednesdayFebruary 28 - Monday - Mid-Semester examinationbyInstructors)March5 Saturday (ScheduledMarch 7 Monday Mid-Semester Grades are due inEnrollmentManagementofOfficeMarch 7-11 Monday - Spring BreakFriday Classes SuspendedAcademic Calender 2005 – 2006 (Continued)Spring 2005Resume14 Monday ClassesMarchsubmitChangestoGradeLastinstructorsdayforLast day for changing “Incomplete” forFall semester 2004March 21 - Monday - Advisement and Pre-registration period forAprilFridaySummer 2005 and Fall 2005 Semester.1March 23 Wednesday Last day to withdraw from classwithout penaltyMarch 25 - 28 Friday - Easter BreakClosedMonday OfficesResumeMarch29 Tuesday ClassesApril 4 -9 Monday - Faculty EvaluationsSaturdayApril 30 – May 5 Saturday - Final ExaminationsThursdaydayreporting grades to the Office offorMonday LastMay9ManagementEnrollment11 Tuesday HoodingCeremonyMayServiceBaccalaureate13 FridayMayConvocationMay14 Saturday Commencement400 Magnolia StreetOrangeburg, South CarolinaSUMMER ACADEMIC CALENDAR2005May 21 Saturday RegistrationMay 23 Monday Classes beginMay 30 Monday Memorial Day (Holiday)May 31 Tuesday Last day to add classesJune 10 Friday MBA Graduation Application Deadline June 20 Monday Last day to drop classes without a penalty July 4 Monday Independence Day holidayJuly 5 Tuesday Classes resumeJuly 20 – Aug 1 Tuesday – F inal examinationsMondayAugust 1 Monday L ast day of classesAugust 2 Tuesday Grades due in the Office of EnrollmentManagement400 Magnolia StreetOrangeburg, South CarolinaFALL ACADEMIC CALENDAR2005newforMBA’s20 Saturday 9:00-10:00OrientationAugustforStudentsMBARegistration10:00–2:00BeginMonday Classes22Augustdayto Register and/or Add ClassesLast26AugustFridaySeptember 5 Monday Labor Day HolidayClasses Suspended –Office and Library ClosedSeptember 6 Tuesday Classes resumeSeptember 28 Wednesday MBA MFAT TestOctober 10-14 Monday - Mid-Semester examinationsbyinstructors)Friday(ScheduledOctober 17 Monday Last day for instructors to submitforchangingdayGradeLastChanges.Springand2005for“Incompletes”2005.SummerFebruary 28 - Monday - Mid-Semester examinationInstructors)byMarch5 Saturday (ScheduledMarch 7 Monday Mid-Semester Grades are due inEnrollmentManagementofOfficeMarch 7-11 Monday - Spring BreakFriday Classes SuspendedAcademic Schedule Spring 2006Preparing Professionally for Leadership and Service in a Multi-Cultural, Global and Technological SocietyCLAFLIN UNIVERSITYHistoryThe origin of Claflin may be traced to the founding of the Baker Biblical Institute in Charleston, South Carolina, in 1866. It was within the confines of a building belonging to this institution that the South Carolina Mission Conference was organized on April 2, 1866. Leaders of the Mission Conference played crucial roles in the organization of Claflin University on December 18, 1869. Members of this group included Samuel Weston and Joseph Sasportas, along with a number of other prominent churchmen. Boston philanthropist Lee Claflin and his son, Massachusetts Governor William Claflin, provided the initial financing for the purchase of the property of the Orangeburg Female Academy on which the new college was located. Dr. Alonzo Webster and the Reverend T. Willard Lewis played prominent roles in securing this site.Dr. Webster was named the first president of Claflin University. During his administration, the Baker Biblical Institute was moved to Orangeburg in 1971 and merged with Claflin University.On March 12, 1872, the South Carolina General Assembly approved an act which designated the South Carolina State Agricultural and Mechanical Institute as a coordinate department of Claflin University. This arrangement lasted from 1875 until 1896, when the South Carolina General Assembly passed an Act of Separation, which severed the State Agricultural and Mechanical Institute from Claflin University and established the separate entity, which eventually became South Carolina State University.From 1872 onwards, Claflin University offered instruction in the arts and sciences, literature and crafts. The first class in the Normal Department graduated in 1879 while the College Department granted its first diploma in 1882.Since the administration of Dr. Webster to the current administration, six additional presidents have served Claflin University. The Reverend Mr. Edward Cooke followed Dr. Webster in 1872. The Reverend Mr. L.M. Dunton succeeded to the presidency upon the retirement of the Reverend Mr. Cooke in 1884. On the resignation of Dr. Dunton in 1992, Dr. J.B. Randolph was elected to this office. J.J. Seabrook succeeded him in 1945.In September 1955, President Seabrook resigned from the presidency of Claflin University. Dr. Hurbert Vernon Manning replaced him on June 1, 1956. On March 16, 1984, Dr. Oscar Allan Rogers, Jr., was named the seventh president of Claflin.Upon Dr. Rogers’ retirement, Dr. Henry N. Tisdale assumed the presidency on June 1, 1994.MISSIONClaflin University is a progressive, independent, liberal arts, co-educational, historically Black institution that is affiliated with the United Methodist Church. It was chartered and continues to provide educational excellence and to prepare students without regard to gender, race, religion or ethnic origin. It is committed to offering quality undergraduate programs, select graduate programs, and viable continuing education opportunities.At the undergraduate level, the university ensures that students receive a liberal arts education designed to produce graduates who understand themselves as well as historical and social forces that impact the world. Their academic experiences will include an understanding of religious and aesthetic values in a universal context and a thorough grounding in their chosen discipline. Their education will incorporate the use of technology and exposure to recent scientific developments and inculcate critical thinking and communication skills in order to prepare them for leadership and service in a global and multicultural society.At the graduate level, students are provided instruction to enhance the analytical and comprehensive research acumen necessary for professional growth and leadership. Continuing education programs create avenues for students to complete their educational objectives and develop skills necessary for their professional and personal fulfillment. Undergirding the Mission is the University’s commitment to excellence in all its endeavors.PHILOSOPHYClaflin University was founded to provide education primarily for a people who were seriously in need of intellectual training and spiritual support. Her founders were humanitarians and courageous visionaries. These qualities are interwoven in the philosophy of Claflin.From her earliest days, Claflin has been committed to certain principles. The Charter declares not only the academic purpose but also the Christian responsibility of the institution. Claflin strives to fulfill her commitment by providing a liberal arts education in an environment that also encourages the spiritual growth of the students. Claflin is concerned that her students develop into dedicated individuals who are firmly committed and who relate successfully to the whole society. Thus, the institution has a program, which provides for social and cultural growth as well as academic and religious growth. Claflin University has designed a special medium to stimulate and motivate the learning process of her students. The curriculum is designed so that students may perceive the correlation among the several disciplines as these disciplines relate to the community and to the world. With this integrated approach, students have the opportunity to perceive the contributions of varied ethnic groups, including those of the African-American. At the center of the whole is the desire to guide each student toward achievement of his/her greatest capability.ACCREDITATIONClaflin is accredited by the Commission on Colleges of the Southern Association of Colleges and Schools (1866 Southern Lane, Decatur, Georgia 30033-4097: Telephone number 404-679-4501) to award the bachelor’s degree and the Master of Business Administration degree. The University Senate of the United Methodist Church approves it. The National Association accredits its Education Program for the Accreditation of Teacher Education (NCATE) and by the South Carolina Board of Education.The University’s School of Business is nationally accredited by the Association of Collegiate Business Schools and Programs (ACBSP) to offer the Bachelor of Science in Business Administration, Bachelor of Science in Management, Bachelor of Science in Marketing and Bachelor of Science in Organizational Management programs.THE CAMPUSClaflin’s historic 38-acre campus is located in Orangeburg, South Carolina, on a site formerly occupied by the Orangeburg Female Academy. A county of 91,000, Orangeburg is located 40 miles south of Columbia, the capital of South Carolina.ADMINISTRATIVE BUILDINGTingley Memorial HallTingley Memorial Hall is the main administration building. Mr. Samuel Herbert Tingley, of Rhode Island, erected it in memory of his beloved wife, Mrs. Adella Malvina Tingley. This building is listed in the National Register of Historic Places.ACADEMIC BUILDINGSBowen HallThis building, constructed in 1900, formerly housed the college library. It presently houses the Division of Education, the Department of Teacher Education, and the General Education Computer Laboratory, the Freshman College, one classroom and offices. Calhoun-Downs-Laymen HallConstructed in 1949 for use as a science faculty, this two-story brick structure has been remodeled and houses Claflin’s bookstore and the offices of Counseling and Placement and Cooperative Education, as well as the Department of Art.Grace T. Kennedy Business and Communications BuildingErected in 1992, this building houses classrooms and offices for the Division of Business Administration including MBA Program, the Department of English and Foreign Languages, and the Department of Mass Communication. It also contains a video/radio studio, two computer laboratories and an auditorium.Jonas T. Kennedy Health and Physical Education CenterThis modern facility was occupied in 1980. Constructed through the generosity of Dr. and Mrs. Jonas T. Kennedy and the United Methodist Church, this structure houses the Department of Health and Physical Education. The center contains a 2,000-seat arena.Lee BuildingErected in 1898, this is one of the older remaining structures on the campus. It has served as a college library and now houses the Author Rose Museum.W. Vernon Middleton Fine Arts CenterThe Fine Arts Center was completed in 1968. This building is a contemporary structure containing an auditorium with a seating capacity of over 750 persons, 4 classrooms, 8 seminar rooms, 2 dressing rooms, 2 practice rooms and several well-equipped offices.Pearson Music StudioThis building was erected in 1947, and put into use for the 1947-1948, school term. It contains an auditorium-rehearsal room, two classrooms, band rehearsal room and two offices. This structure was remodeled several times through the generosity of Dr. Daisey E. Pearson and Claflin.James S. Thomas Science CenterThis facility was erected in 1973. It is named in honor of Bishop J. S. Thomas, a prominent Claflin alumnus. It provides classrooms, laboratories, and offices for biology, chemistry, mathematics and computer science departments.H.V. Manning LibraryRESIDENCE HALLSC.L. Asbury HallThis women’s residence hall was erected in 1961 to replace Wilson Hall. The building is a three-story structure with a canteen, a laundry room, recreation rooms and two guest rooms. The building is well equipped and accommodates 128 young women.Fred P. Corson Hall was erected in 1964. The building is a three-story brick structure housing the university dining hall, two-floor residence area for young women and the Orange and Maroon Club.Mary E. Dunton HallMary E. Dunton Hall, a women’s residence hall, was erected in 1957 to replace the old Mary E. Dunton Hall, which was destroyed by fire in 1955. This building is a three-story brick structure. The building was named in honor of Mrs. Mary E. Dunton, wife of the late President Dunton.High-Rise Residence HallApproximately 220 male students are housed in this modern facility, erected in 1970. Rising to a height of six floors, this brick building is completely air-conditioned and equipped with all modern living facilities.SRC South, North, East and WestSouth house (96) male honor and regular senior males. North house (72). East house (48) honor and senior females. West house (72) junior and senior females.Preparing Leaders for the Twenty-First CenturySCHOOL OF BUSINESSThe School of Business prepares students for successful careers in business professions. More job opportunities for men and women educated in the managerial techniques of business operations and administration will be available in our expanding business sector. The demand for salaried managers and administrators will continue to grow as firms increasingly depend on well-trained professionals.GENERAL OBJECTIVESStudents who complete the degree requirements in Business Administration will:1.develop the knowledge, analytical ability and balanced judgment to solve businessproblems;2.understand individual disciplines in the business world as well as theinterrelationship of each discipline to the world;3.understand necessary techniques for dealing with the economic, social and politicalenvironment of the business firm, especially quantitative techniques andcommunication skills;4.possess the needed skills for jobs that will be available upon graduation as well asfor jobs that will be created in the future;5.develop an appreciation of and respect for industry’s role in the development ofWestern Civilization; and6.receive encouragement and preparation to pursue advanced Ph.D, DBA andprofessional certifications.ACADEMIC PROGRAMSThe School of Business offers the following degree programs:-Master of Business Administration (MBA) with concentration in:FinanceGeneral BusinessManagementMarketing-Bachelor of Science (B.S.) in Business Administration with concentrations in Accounting (General Accounting Track) and (Public Accounting Track)Finance-Bachelor of Science (B.S.) in Business Administration with non-business minor-Bachelor of Science (B.S.) in Organizational Management (for non-traditional students through the Division of Continuing and Professional Studies).-The Business Division provides support to the Department of Mathematics and Computer Science to offer a Bachelor of Science (B.S.) degree in Management Information System (This program is housed in the Department of Mathematics and Computer Science).-The Business Division provides support to the Department of Health and PhysicalEducation, to offer Bachelor of Science degree (B.S.) in Sports Management.-A minor in Business Administration.ACCREDITATIONThe Association of Collegiate Business Schools and Programs (ACBSP) has nationally accredited Claflin University to offer the degree of Bachelor of Science in Business Administration (B.S.B.A.) and the two-year degree completion program of Bachelor of Science in Organization Management (B.S.O.M), through the School of Business and Division of Business Administration.FACULTY/STAFFHarpal S. GrewalPh.D, The Ohio State UniversityProfessor and Division Chair(Economics, Finance, Quantitative Methods)Dr. Diane PrincePh.D, University of Tennessee - KnoxvilleProfessor and MBA Director(Management, Marketing, Quantitative Methods)Dr. Thomas GarsombkeSusan E.M. DavisMBA, University of RochesterAssistant Professor(Management, Finance, Leadership, Org. Behavior)Munir HassanPh.D, University of Nebraska-LincolnAssociate Professor(Finance, Economics, Production and Operations Management) Nora M. MartinPh.D Nova Southeastern UniversityAssistant Professor(Marketing)Tara H. SaracinaMBA, Georgia State UniversityCPA, GeorgiaAssistant Professor(Accounting)Robercine LinderB.S., Organizational ManagementClaflin UniversityDivision Administrative AssistantMaster of Business AdministrationMBAThe Master of Business Administration (MBA) program at Claflin University is designed to provide a high quality education that promotes the students potential as managers, entrepreneurs, leaders and socially responsible individuals. The program strives to teach students to think logically, communicate effectively, develop an understanding and appreciation of the global business environment, be guided by high ethical standards, and develop the conceptual and analytical skills needed to succeed in professional roles in business, industry or public service. MBA graduates are expected to pursue careers in mid and upper management.Objectives:-Provide students a high quality, caring, open and diverse learning environment-Develop and integrate analytical skills for decision-making that incorporateglobal, ethical and culturally diverse dimensions-Provide adequate skills in assessing organizational performance and developingapproaches for improvements-Provide leadership and interpersonal skills to become successful businessprofessionals-Provide technological skills not only for jobs that will be available upon graduation but also for jobs that will be created in the future.。

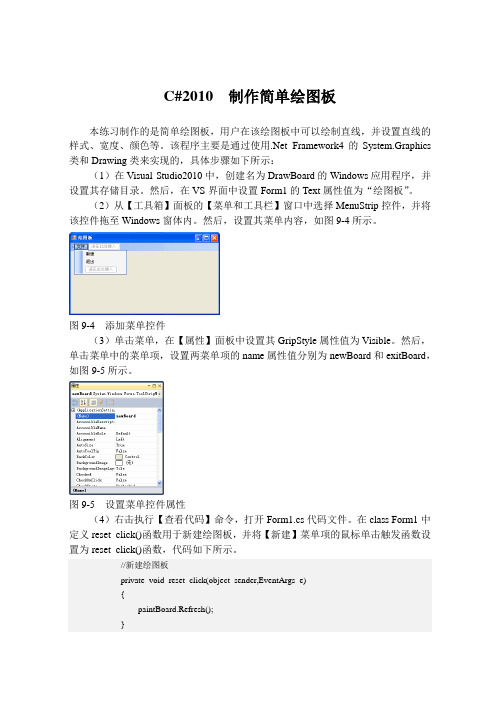
第1章Project入门本章内容:了解Microsoft Office Projeev 2007 产品系列了解优秀的项目管理工具如何帮助完成任务启动ProjccC Standard 或Preject Profcssioilal,辨别Projcct 窗口的主要组成部分使用视图以不同方式显示项目计划的详细信息使用报表打印项目计划的详细信息创建项目计划和输入项目开始日期设葢?页目的工作和非工作时间输入项目计划属性项目管理是一门实践丰富的艺术与科学。
不论您正在参与项目管理,还是将妥进行项目管理,阅读本书都是一个绝佳的学习机会。
就其核心而言,项目管理是一种融合技能与工具的“工具箱”,有助于预测和控制组织工作的成果。
除了项目,组织还有其他工作。
项目(如电彬项目)与持续业务(()ng <)ingOpuratkm)(如工资单服务)截然不同,因为项目是临吋性的工作,产生唯一性的成果或最终结果。
凭借优秀的项目管理系统,您可以解决以下问题:妥取得项目的可交付成果,必须执行什么任务,以何种顺序执行?应于何时执行每一个任务?谁来完成这些任务?成本是多少?如果某些任务没有按计划完成,该怎么办?对那些关心项目的人而言,交流项目详情的最佳方式是什么?良好的项目管理并不能保证每个项目一定成功,但不良的项目管理却会是失败的成因之一。
在您的项目管理工具箱中> Microsoft Office Projcct 2007应是最帑用的工具之一。
本书会介绍如何使用Projcct建立项目计划(包括任务和资源的分配),如何使用Project 中扩展的格式化特性来组织和格式化项目计划的详细信息,如何跟踪实际工作与计划是否吻合,以及当工作与计划脱轨时如何采取补救措施。
如果是刚刚接触项目管理,可以在此处暂停,先阅读附录A,然后再继续阅读本章。
这样做不会占用多长时间,有助于恰当地评估和组织自己的项目日程安排需求,进而利用Projccl•建立稳固的计划O本书的大部分练习围绕着一个虚构的电彬公司(Souchridge Video and Film Productions)笫I部分管理简单项目展开。

FIRST Robotics Competition Software Release NotesFRC 2010The FIRST Robotics Competition (FRC) software includes three separateprogramming environments—LabVIEW™, Wind River® Workbench, andSun™ SPOT Java™ Development Kit for FRC. Use any environment todevelop the robotics program you want to run on the CompactRIO device.Use LabVIEW to program a robot in the LabVIEW graphical programmingenvironment or to develop a desktop application. Use Wind RiverWorkbench to program a robot in C or C++. Use the Sun SPOT JDK toprogram a robot in Java.These release notes contain system requirements and installationinstructions for the FRC software.Read the System Requirements section of this document before you installthe FRC software and then follow the instructions in the Installing theFRC2010 Software section. Read the Where to Go from Here section ofthis document for information about programming resources. ContentsSystem Requirements (2)LabVIEW (2)Wind River Workbench (2)Sun SPOT JDK (2)Installing the FRC2010 Software (2)Activating the FRC Software (4)Where to Go from Here (5)FIRST Robotics Competition Software Release Notes System RequirementsThe FRC software has the following requirements.LabVIEW•Windows Vista/XP/2000 (To use this version of LabVIEW with Windows 2000, you must have Windows 2000 Service Pack 3 or later.)•2.4 GB of disk space Note Refer to the LabVIEW Release Notes , at /manuals , for a complete list of system requirements for LabVIEW.Wind River Workbench•Windows XP Professional for (32-bit), Service Pack 2•Windows Vista Business for (32-bit), Service Pack 1Sun SPOT JDK•Windows Vista/XP/2000•300 MB of disk spaceInstalling the FRC 2010 SoftwareBefore you install the FRC software, consider that the FRC software includes the LabVIEW 8.6.1 Full Development System. If you install and activate the FRC software over LabVIEW 8.6.0, you must uninstall the FRC software and reinstall LabVIEW 8.6.0 after the FRC license expires. Alternatively, you can upgrade to LabVIEW 8.6.1 and reactivateLabVIEW using the LabVIEW 8.6.1 serial number.Complete the following steps to install the FRC software. Ensure you have a working Internet connection to complete activation after installation.1.Log on as an administrator or as a user with administrator privileges.2.Disable any automatic virus detection programs before you install. Some virus detection programs interfere with installation.3.Insert the FIRST Robotics Competition Software DVD Disc 1. 4.Follow the instructions that appear on the screen. If necessary, insert the FIRST Robotics Competition Software DVD Disc 2 when prompted.NoteIf the installer does not open automatically, browse to the DVD root directory, double-click setup.exe to launch the installer, and then follow the instructions thatappear on the screen.© National Instruments Corporation 3FIRST Robotics Competition Software Release Notes5.In the Product List , select the products you want to install.By default, the FRC Software installs all three programmingenvironments. You must select Do not install for the productsthat you do not want to install.6.Click the Next button.7.Follow the instructions that appear on the screen.8.When prompted, enter the serial number printed on the DVD sleeve.Note The Vision Assistant Hot Fix window is a required step in the installation process. Continue to follow the instructions that appear on the screen to complete installation.9.(Wind River Workbench, new users) Complete the following steps toinstall Wind River Workbench.a.Follow the instructions that appear on the screen.b.On the Installer-Choose Activation Type page, selectPermanent activation and browse to the Distributions\Wind River directory on the NI2010FRC2 DVD.c.Select the FirstRobotics_2010_install.txt file andclick the Open button.Note The FirstRobotics_2010_install.txt file contains the installation keys and licensing necessary to install and activate Wind River Workbench. Wind River renames this file to install.txt and installs the file in the WindRiver directory.d.Click the Next button and continue to follow the instructions thatappear on the screen.10.(Wind River Workbench, returning users) If the Wind River Workbenchsoftware for FRC 2009 exists on the host computer, complete thefollowing steps to install the Wind River Workbench software forFRC 2010.a.Follow the instructions that appear on the screen.a.On the Installer-Existing Product Activation File page, select Enter new activation information .b.On the Installer-Choose Activation Type page, select Permanent activation .c.Browse to the Distributions\Wind Riverdirectory on the NI2010FRC2 DVD and selectFirstRobotics_2010_install.txt .d.On the Installer-Choose Installation Filters page,select Custom Installation.FIRST Robotics Competition Software Release Notes e.On the Installer-Custom Installation page, place a checkmark next to each product and click the Install button.f.After the Overall Installation Progress bar displays (installed7 of 7 selected products), click the Next button andcontinue to follow the instructions that appear on the screen.11.At the end of installation, choose to Run License Manager toactivate the product(s) and click the Next button to launch the NI Activation Wizard.12.Select the Automatically activate through a secure Internetconnection option and click the Next button.13.If necessary, enter the serial number printed on the DVD sleeve.14.After installation and activation, enable any virus detection programsyou disabled.15.Navigate to the FIRST Web site at /frccontrolsystem to download required updates for theprogramming environment you install.Note (Wind River) The WPI Library for Wind River does not function until you download the most up-to-date WPI Library at /frccontrolsystem .Activating the FRC SoftwareIf you did not Run License Manager to activate the product(s) at the end of installation, you must activate the National Instruments portions of the software.Complete the following steps to use the NI License Manager to activate the FRC software.1.Select Start»All Programs»National Instruments»NI License Manager to display the NI License Manager.2.In the Local Licenses tree, navigate to LabVIEW 8.6.1»DevelopmentSystem»FIRST Robotics Competition and ensure the icon for the FIRST Robotics Competition item is a full yellow box. A full yellow box designates an activated or otherwise fully featured, expiring license.3.If the icon is not a full yellow box, right-click the FIRST Robotics Competition item and select Activate from the shortcut menu.4.When the NI Activation Wizard appears, select to Automatically activate through a secure Internet connection and enter the serial number printed on the FIRST Robotics Competition software DVD sleeve, if necessary.5.Close the NI License Manager.Where to Go from HereRefer to the FRC Community Web site at http://firstcommunity./for official information about FRC, including rules andregulations as well as support information.If you program a robot in LabVIEW, you can refer to the followingdocuments to get started building an application for FRC:•Getting Started with LabVIEW for the FIRST RoboticsCompetition—Use this manual to learn about the LabVIEW graphicalprogramming environment and the basic LabVIEW features you canuse to build FRC applications. Access this manual by navigating to theNational Instruments\LabVIEW 8.6\manuals directory andopening FRC_Getting_Started.pdf.•LabVIEW Robotics Programming Guide for the FIRST RoboticsCompetition—Use this manual to access information about roboticsprogramming concepts, reference information about the FIRSTRobotics Competition VIs, and guidelines for troubleshooting inLabVIEW. Access this manual by navigating to the NationalInstruments\LabVIEW 8.6\manuals directory and openingFRC_Programming_Guide.pdf.•LabVIEW Help—Use the LabVIEW Help to access information aboutLabVIEW programming concepts, step-by-step instructions, andreference information. The LabVIEW Help also contains informationabout the FIRST Robotics Competition VIs and dialog boxes. Accessthe LabVIEW Help by selecting Help»Search the LabVIEW Help inLabVIEW.If you program a robot in Wind River Workbench, you can refer to thefollowing documents to get started building an application for FRC:•C/C++ Programming Guide for the FIRST RoboticsCompetition—Use this manual to access information about roboticsprogramming concepts, reference information about the WPI RoboticsLibrary, and guidelines for troubleshooting in Wind River Workbench.Access this manual by navigating to the WindRiver\docs\extensions\FRC directory and opening C Programming Guidefor FRC.pdf.•Wind River Workbench User’s Guide—Use this guide to accessinformation about building and debugging an application in WindRiver Workbench. Access this guide by selecting Help»HelpContents in Wind River Workbench and navigating to the Wind RiverDocumentation»Guides»Host Tools»Wind River WorkbenchUser’s Guide 3.0, VxWorks Version book on the Contents tab.© National Instruments Corporation5FIRST Robotics Competition Software Release NotesIf you program a robot in the Sun SPOT JDK, you can refer to the followingdocuments to get started building an application for FRC:•Release Notes for Java Programming—Use these release notes toaccess information about installing the WPILib Sun SPOT JDKextensions you can use to program a robot in Java. Access these releasenotes by navigating to the FRCJava directory and opening Releasenotes for Java programming.pdf.• C and Java Programming Guide for FRC—Use this guide to accessinformation about robotics programming concepts in Java, referenceinformation about the WPI Robotics Library, and guidelines fortroubleshooting in Java. Access this guide by navigating to theFRCJava directory and opening C and Java Prog ramming Guidefor FRC.pdf.FIRST Robotics Competition Software Release National Instruments, NI, , and LabVIEW are trademarks of National Instruments Corporation.Refer to the Terms of Use section on /legal for more information about NationalInstruments trademarks. Other product and company names mentioned herein are trademarks or tradenames of their respective companies. For patents covering National Instruments products/technology,refer to the appropriate location: Help»Patents in your software, the patents.txt file on yourmedia, or the National Instruments Patent Notice at /patents.© 2008–2009 National Instruments Corporation. All rights reserved.375248A-01Oct09。








2010英语二text1Text 1 is a passage from the 2010 English II exam. The text discusses the benefits and drawbacks of children's use of digital media, focusing specifically on the impact it has on their reading habits. In this article, we will explore the main points of the text and provide a detailed analysis of its content.The passage starts by highlighting the increasing popularity of digital media among children. It points out that children are spending more time using digital devices, such as computers, smartphones, and tablets, which offer a wide range of entertainment options. While the text acknowledges the potential educational value of digital media, it also raises concerns about the negative effects it may have on children's reading habits.One of the main concerns mentioned in the text is the impact of digital media on children's attention span. It argues that the fast-paced nature of digital content, with its constant stimuli and instant gratification, may make it difficult for children to engage in sustained reading. The text suggests that this can lead to a decline in their ability to focus and comprehend longer texts, which are essential skills for academic success.Another issue raised in the passage is the potential loss of critical thinking and analytical skills. The text argues that the interactive and multimedia nature of digital media can limit children's exposure to complex and nuanced narratives, thus hindering their ability to think critically and deeply about the content they consume. It suggests that children may become passive consumers of information rather than active readers and learners.Moreover, the passage discusses the impact of digital media on children's reading habits in terms of the types of content they choose. It points out that children often prefer shorter, easily digestible pieces of information, such as social media posts and online articles, over longer and more challenging texts, such as books. The text suggests that this preference for instant gratification and quick information may lead to a decline in the overall quality of children's reading material and their exposure to diverse perspectives.Despite these concerns, the passage also acknowledges the potential benefits of digital media for children's reading habits. It mentions that digital platforms can provide access to a wide range of reading materials, including e-books, online libraries, and educational websites. The text argues that when used properly, digital media can enhance children's reading skills by providing interactive and engaging learning experiences.In conclusion, the passage discusses the benefits and drawbacks of children's use of digital media on their reading habits. While digital media offers various entertainment and educational opportunities, it also raises concerns about children's attention span, critical thinking skills, and reading material preferences. The passage emphasizes the importance of finding a balance between digital and traditional reading experiences, ensuring that children develop the necessary skills to engage with both forms of media.。

Hardening Windows ApplicationsolleB - olle@About this documentThis paper is aimed at Windows developers in the hope of explaining how Windows' security features can be used to better secure their applications. It is not a complete guide to the Windows security model and may skip details that were deemed unimportant at the time of writing. Please bear that in mind while reading. Thank you.Introduction to Windows securityIn this introductory chapter some basic concepts of the Windows security model are explained in just enough detail to understand the material presented in the following chapters. If you are already familiar with how the Windows model of access control works, feel free to skip ahead and use this chapter for reference only. Another great reference is the MSDN section on Access Control available at /en-us/library/aa374860.aspx.Security Descriptors and Access Control ListsA central concept in the Windows security model is the Security Descriptor (defined by the SECURITY_DESCRIPTOR structure) which contains all security related information about an instance of an operating system resource. The Security Descriptor for a particular resource can, assuming the current user has sufficient access to the resource, be queried and set from an application in order to inspect and/or modify its components. These components are:• A bitfield of control flags that describe properties of the Security Descriptor•The Security Identifier (or SID) that uniquely identifies the owner of the resource•The SID of a security group (which is only used for POSIX compatibility)• A System Access Control List (or SACL) which controls auditing of access to the resource • A Discretionary Access Control List (or DACL) that controls access to the resourceAll components of a Security Descriptor (except for the control flags) are optional. A resource with a Security Descriptor with no DACL would mean that no access control restrictions apply to the resource and all access is granted to everyone, this is commonly called a “Null DACL”.The SACL and DACL are both lists of Access Control Entries (or ACEs) which contain:•The type of the ACE (e.g. deny, allow, audit)• A bitfield that controls the inheritance properties of the ACE (i.e. can or can't be inherited)•The SID of the “trustee” to which this entry applies• A bitfiled (called an “access mask”) that defines what types of access are governed by this entryWhen the DACL of a resource is checked against the “Access Token” of a requesting thread, the Access Control Entries are checked in order and when an ACE where the “access mask” matches the type of access and where the SID in the ACE matches either a user or group SID in the “Access Token”, access is immediately granted or denied depending on the type of ACE encountered. Should no ACEs in the DACL match the requesting Access Token, access is always denied. One could say the DACLs are checked in a “first match, default deny” mode.Objects and HandlesThe Windows NT kernel is built on a concept of kernel “objects” that represent different resources of different types (file, process, timer, etc.). These are, simply put, reference-counted data structures which share a common header (defined by the OBJECT_HEADER structure). The common object header contains, among other things, information about which type an object is an instance of and a pointer to a Security Descriptor which controls access to the object. All instances of object types that can be accessed by name (and some that can't, like processes and threads) have to have a Security Descriptor defined and are referred to by Microsoft documentation as “Securable Objects”. The Security Descriptor of a Securable Object can be read and set through the user-mode accessible APIs such as “(Get|Set)SecurityInfo” and “(Get|Set)KernelObjectSecurity”.To expose kernel objects to user-mode applications, the concept of a “Handle” is used. The handle is defined as a pointer-wide value that the kernel uses to keep track of user-mode references to an instance of an object. When an object access is requested from the application (such as when opening a file by name or creating a new semaphore object) the requested kernel object instance is created (if it doesn't already exist) and an opaque handle value is associated with it and returned to the requesting process. The handles are kept track of by the kernel on a per-process basis (to maintain the inter-process security boundary) and objects are dereferenced when the handle is closed (using CloseHandle or on process termination).Before the kernel grants the requesting user a handle, it first checks the Security Descriptor of the object instance against the “Access Token” of the requesting thread. It is during this access check that DACLs are used to permit (or explicitly deny) access and SACLs are used to generate audit events.Tokens and PrivilegesWe have made reference to the “Access Token” of the thread requesting a handle to a particular resource from the kernel. This Access Token is a kernel object which describes the security context of a process (or thread within a process) and thus defines which operating system resources and functions it can be granted access to. The Access Token contains all the relevant security information needed to make access control decisions, including the SIDs identifying user ID and group membership, the current state of system “Privileges”, and on Windows Vista and later information about the “Integrity Level” and “Elevation Status” of the Token.Each process has a “Primary Token” associated with it from process creation. This token can, assuming required privileges are held, be manipulated in order to restrict or raise the access of a particular process (e.g. by using the user-mode accessible “CreateRestrictedToken” or “SetTokenInformation” APIs). A certain thread within a process can also be temporarily assigned an “Impersonation Token” in order to, for example, act on behalf of a certain user (see the “ImpersonateLoggedOnUser” and “SetThreadToken” APIs).The primary means of controlling access to resources in Windows is the DACL defined in the Security Descriptor, however, there are additional system “Privileges” that control access to system functions such as working with audit event logging or managing storage volumes. Privileges that override normal security are also defined, such as the privileges to backup and restore files without regard for DACLs, take ownership of files without regard for DACLs, and the big one; “Act as partof the operating system” also known as the “TCB” Privilege which allows the creation of arbitrary Access Tokens without user authentication (see the “LogonUser” API).Privileges can be granted to a user or group of users and are usually included in a “disabled” state in the Primary Token. Before using a privilege it is necessary to “enable” it by manipulating the Access Token of the current thread or process. This provides a means of enabling a certain privilege only for a specific thread in a process by assigning an Impersonation Token with the desired Privilege enabled to that thread. All other threads in the process would then be unaffected. Windows features related to securityThis chapter introduces some of the Windows features that are related to security and describes how they are implemented and how they can be used by developers. If no comments are made about availability, features are supported on Windows XP SP3 / Windows Server 2003 SP1 and later. Restricted TokensIn order for an application to “drop” privileges and access rights in order to run sensitive code, the Windows security model allows the creation of a “Restricted” version of an Access Token. This Token can delete Privileges so they can't be enabled and used, set attributes of existing user and group SIDs so that they can't be used used to grant access in DACL checks and restrict the SIDs used in DACL checks to a subset of the SIDs defined in the Token. To create a Restricted Token, an application calls the “CreateRestrictedToken” API with a handle to the Token to be restricted, it is then provided with a handle to a copy of that Token that has been restricted.A Restricted Token can be assigned to a thread or, more interestingly, can be used with the “CreateProcessAsUser” API to start a new process with the Restricted Token as Primary Token. Even though setting the Primary Token is usually a privileged operation that requires the “SeAssignPrimaryTokenPrivilege” system Privilege, if the Token passed to “CreateProcessAsUser” is a restricted token of the calling processes own Primary Token then the Privilege isn't needed. The Desktop security boundaryAll interactive logins (both on a console or via RDP) are assigned a “Session”. Prior to Windows Vista, the first interactive logon was assigned a Session ID of 0 (Zero). In Windows Vista and later versions, Session 0 is reserved for Windows Services and the first logon becomes Session 1. Within a session there are one or more “Windows Stations”, these Window Stations are Securable Objects that contain a Clipboard and one or more “Desktops”. The only interactive Window Station is the first one, which is named “Winsta0” and is associated with the users' input and display devices. A user cannot directly interact with any other Window Stations in the Session.A Desktop is also a Securable Object which acts as a container for user interface objects like windows and the messages that create interactions between them. These user interface objects (sometimes called “User Objects” in Microsoft documentation) are not Securable Objects but belong to the Win32 environment which is more properly called the “Windows subsystem”.Since the Desktop object is a Securable Object it can be used to enforce a security boundary between two Win32 applications running in different security contexts. Since the Win32environment does not enforce any security boundary between windows and since these messages can contain information such as function pointers this means that processes with windows on the same Desktop can directly influence each other in nasty ways. For an example of what can happen when an unsuspecting application receives malicious messages see the 2002 “Shatter Attack”[0].An example of where Microsoft uses this feature would be the “WinLogon” Desktop, which is the first Desktop of a session where the user logon interaction takes place and which is protected by a very restrictive DACL. This is also the Desktop which is activated when you press the “Secure Attention Sequence” (i.e. Ctrl-Alt-Del) and on which the UAC “Elevation” dialog is presented. Since these sensitive user interactions are performed on a separate “secured” Desktop, any applications in the users security context will not be able to meddle with them. An example would be a key-logger that uses “Windows Hooks” (see the “SetWindowsHookEx” API) which would not be able to intercept key-presses when a different Desktop is active and cannot gain access to the “secured” Desktop to install its hook because of the restrictive DACL on the Desktop Object.This feature can be used in applications that have similar sensitive interactions with the user, such as credential entry or document signing dialogs to protect them from simple key-loggers and modification by other processes.Imagine you were creating a new sandbox process with a Restricted Token to run some potentially hostile code. Since the new process inherits its Desktop from the parent process, it can interact with other applications on the Desktop by posting Win32 messages to their windows. To stop this you could create a new (non-interactive) Window Station and a Desktop Object on that Window Station by using “CreateWindowStation“ and “CreateDesktop” with suitable default DACLs[1] and assign the new process to the sandbox Desktop by passing its name in the “lpDesktop” member of the “STARTUPINFO” structure parameter to the “CreateProcess” API. In a real-world example the Chromium browser uses this technique to strengthen the sandboxing of its rendering processes[2]. Job objectsIn the release of Windows 2000 and the advent of “Terminal Services” (now referred to as “Remote Desktop Services”) Windows went from supporting only one interactive logon at a time to a model with a potentially very large number of simultaneous users. Microsoft then had to solve the problem of a single user consuming more than a “fair share” of the total system resources and thus degrading service to the other users. The solution implemented was the Job Object. The Job Object is a Securable Object which acts as a container for processes (that belong to the same Session) and enforces a limiting policy on them.Examples of the limits that can be imposed on processes associated with a Job Object are:•Maximum number of processes associated with the job (preventing “fork-bombs”).•Restrictions on committed memory (preventing physical memory starvation).•Execution time limits to prevent runaway processes (killing off endless loops).•Prohibit the calling of sensitive system APIs such as “SystemParametersInfo”.•Prohibit threads from changing the interactive Desktop using the “SwitchDesktop” API.•Prohibit access to user interface objects such as the Clipboard.As you can see from this non-exhaustive list, Job Objects can be very useful when running code that can potentially misbehave given unexpected input, for example file format parsers and other complex processing tasks. Job Objects make a good strengthening component of a sandbox foruntrusted code or can just be used to limit the amount of damage a component of your application can do when processing malformed input. The Chromium browsers sandbox uses Job Objects to limit the impact of running untrusted code on the system[2].Mandatory Integrity ControlWindows Vista introduced a new concept to the Windows security model called Mandatory Integrity Control or “MIC”. A new type of ACE was introduced in the SACL, called a “Mandatory Label” where the SID can specify an “Integrity Level” and the attributes define a policy as follows:•No Write Up - A process of lower integrity cannot modify a higher integrity object•No Read Up - A process of lower integrity cannot get read access to a higher integrity object •No Execute Up - A process of lower integrity cannot execute a higher integrity objectA few Integrity Level values are predefined by Windows, these are Untrusted (0), Low (4096), Medium (8192), Medium+ (8448), High (12288), System (16384) and Protected (20480).The default Integrity Level and policy for Securable Objects which do not have a Mandatory Label explicitly defined is Medium and No Write Up. For process objects No Read Up is also the default. When a process is created it inherits the Integrity Level of its parent process, except in the case where the executable file that is used to start the process has an explicit Mandatory Label with Integity Level lower than the parent process. In that case, the new process is started with the lower Integrity Level. For a process to set a Mandatory Label with a higher Integrity Level than its own on a Securable Object, its Acces Token has to have the “SeRelabelPrivilege” Privilege, though any process which has acquired “WRITE_OWNER” access (often called “Take ownership” rights) to an object can set a Mandatory Label on it with an Integrity Level equal or lower to that of its own. Note that, since the Integrity Level of a process is defined by a Mandatory Label ACE in the SACL of the process' Primary Token, there can be no separation between threads within the process, even though these threads can have differing Integrity Levels defined in their Security Descriptors. This means that if you would like to run some code at Integrity Level “Low”, you probably want to spawn a new process to contain it. This can be done by passing a Token that has a Mandatory Label ACE in its SACL to the “CreateProcessAsUser” API.Mandatory Labels are “Mandatory” in that they are checked before the DACL is checked in every access check performed by the system, however they are not defined by Microsoft as a security boundary in that bypasses of the “Mandatory” controls are not treated as security bugs. In effect what Microsoft is telling us is that we should not rely on a timely fix to such a bug and therefore not build software that depends on only this function for security.An example of an application that uses MIC for additional security is Microsoft's own Internet Explorer 7 (on Vista and later). IE7 introduced a new feature called Protected-Mode[3], which is basically running the whole browser in a “Low” Integrity Level process. This prevents attackers who have gained control of the browser to modify the system, as all user applications and resources are at Integrity Level “Medium” (and Windows system resources and services can be even higher) though it does nothing to prevent the browser from stealing the users' information as only the “No Write Up” policy is used. In an application with less dependancies (such as a separate process with clearly defined interfaces to the parent application) it would probably be easier to implement the full policy set, though “No Write Up” is a pretty good start.User Account ControlUser Account Control or “UAC” was introduced in Windows Vista along with many other security improvements and is probably the most misunderstood security feature Microsoft has ever released. The point of UAC is to make logged in Administrators run in the security context of the “standard user” most of the time and only enabling their Administrative rights when explicitly needed (through a process called “Elevation”). This is referred to as running in “Admin Approval Mode”. With this restriction, Microsoft hope to “persuade” developers of third-party applications not to assume that their application would run with Admin privileges and, as an example, not attempt to store its configuration in the “Program Files” directory or the HKEY_LOCAL_MACHINE hive. This lowering of privileges is implemented by an extension to the Access Token, where a Token can include a “Link” to another Token and information about which type it is (“Elevated” or not). When Administrators log in, their initial process receives a Primary Token with the same group membership and system Privileges as a standard user would. This Token also has a link to the “full” Administrator Access Token and a flag that indicates that the current Token is “limited”.To determine if an Access Token is a “limited” Token with a “full” Linked Token attached, call the “GetTokenInformation” API with the “TokenElevationType” information class and check for the “TokenElevationTypeLimited” value. Then, to retrieve a handle to the “full” Linked Token call “GetTokenInformation” with the “TokenLinkedToken” information class.To enable the “full” Access Token on (or “Elevate”) a process, a new service was created called the Application Information Service (AIS or “AppInfo”) which displays the user with a Consent dialog before switching the Primary Token of the target process to the “full” Token. Operating system functions have been altered to call into the AIS and request elevation when it is deemed necessary, for example when copying a file to a DACL-protected directory.To allow applications that legitimately require Admin privileges to continue doing so, a way of requesting Admin privileges on startup was introduced through the application “Manifest”[4]. When the “requestedElevationLevel” key is set to either “highestAvailable” or “requireAdministrator” in the Manifest, the “CreateProcess” API will call AIS to display the Elevation prompt.There are actually two different kinds of Elevation prompts, the normal Consent dialog that users in Admin Approval Mode see when Elevating to perform an action which requires Admin rights and the Credential entry dialog which other users will see if, for example, attempting to install a software package or run an application with a Manifest which specifies it requires Admin rights. Note that in this case there is no Linked Token as the Elevated process will run with the security context of the user that entered the credentials as Primary Token (this is commonly called Over-The-Shoulder or “OTS” Elevation after the intended usage scenario).Microsoft has stated in documentation and through communications that UAC does not implement a security boundary and, thus, bypasses for UAC Elevation will not be considered security flaws. As an application developer, it is important to follow the Microsoft guidelines on UAC so as not to annoy your users with unnecessary Elevation prompts or put them in danger by always requiring Admin rights to run and nullifying the benefit of running as a standard user.User Interface Privilege IsolationSince MIC was introduced in Windows Vista, we now have applications running on the same Desktop but with different Integrity Levels. Remembering the Desktop security boundary, we recognize that these applications can mess with each other since they share the same user interfaceobjects and can pass Win32 messages to each other. To help mitigate this issue, Microsoft has implemented a new feature called User Interface Privilege Isolation or “UIPI” which provides a “Message Filter”, a list of Win32 message types allowed to be passed between windows of different Integrity Levels. The allowed message types in this Message Filter can be altered using the “ChangeWindowMessageFilter” API, however processes at or below “Low” Integrity Level are not allowed to change the Message Filter.Just as with MIC and UAC, UIPI is not treated as a security boundary by Microsoft, in fact they even provide ways around it for “Accessibility” functions such as the built in on-screen keyboard.Memory protection and exploit mitigationHistorically, a great number of critical security vulnerabilities in Microsoft software have been caused by unsafe memory accesses, such as out-of-bounds array indexing and pointer arithmetic.It is a well established fact that such bugs are hard to avoid when programming in C or C++ and since most of the Windows code-base is C (with C++ a close second), Microsoft have worked hard to create operating system technologies, programming libraries and compiler features that make it harder to exploit security bugs and easier to write secure code. All of these are available to third-party application developers that wish to benefit from the hard work Microsoft has put in since Bill Gates' famous “Trustworthy computing” memo[5]. We won't go into a lot of detail as to how these different technologies work, just briefly describe them and how an application developer can make use of them.The oldest of these technologies is the stack overflow protection [6], otherwise known as /GS after the compiler flag that enables it. /GS detects memory writes to stack-allocated buffers that exceed the buffers bounds and corrupt the stack by inserting a “cookie” value in each stack frame that is checked after every copy/move operation to make sure it hasn't been overwritten. /GS has been a default-enabled compiler option since Visual Studio 2003 and if you haven't disabled it, it is already protecting you from many common unbounded write operations to stack allocated buffers, although you shouldn't be using it as a “cheap” way around ridding your code of bounds-checking errors.To help avoid such bugs (and more), the Microsoft Security Development Lifecycle or SDL[11] project maintains a list of “banned” API calls[12] that have historically been hard to use in a safe way. This document also provides safer alternatives to these APIs that should be considered instead.A popular technique[13] that is often used to simplify exploitation of stack-corrupting bugs is to overwrite the saved pointer to a Structured Exception Handling[14] exception handler routine and trigger an exception, thereby redirecting execution to the known address of an exploit payload. Microsoft has implemented two features in Windows to make this technique harder to use, SafeSEH and SEHOP. The SafeSEH linker feature provides Windows with a table of known exception handler routines so that it can verify that the saved function pointer taken from the stack when an exception occurs is in fact a valid exception handler. To verify that your executables and libraries are using SafeSEH, use the “/SAFESEH” linker option[15] which will abort the linker with an error if it cannot produce a SafeSEH table for an image. SEHOP is an operating system feature in Windows Vista and later that, for compatibility reasons, isn't enabled by default on client systems and needs to be enabled by a registry change[16].Windows has also implemented security features protecting heap structures from corruption, for example by an unbounded copy operation to a dynamically allocated buffer. The most simple of these protections (safe unlinking) is available in Windows SP2 and later, while the stronger protections are available on Windows Vista and later, where applications can enable them by callingthe “HeapSetInformation” API with the “HeapEnableTerminationOnCorruption“ information class. Another two Windows features designed to make exploitation of security bugs harder are Data Execution Prevention and Address Space Layout Randomization features or DEP and ASLR. These features act together to make the life of exploit developers a pain, DEP[7] by using the CPUs' memory page permission feature to ensure that instructions can only be executed from memory pages marked as “code”, which are also write-protected. This has the benefit of preventing the CPU from executing code from the stack or other data areas and makes writing exploit payloads harder. Because of compatibility issues, DEP can be enabled in a few different modes and many clients systems run in the “OptIn” mode where only applications that indicate DEP-compatibility[8] will be protected. To enable DEP for a process on a system with an “OptIn” policy, while at the same time making sure DEP is permanently enabled and cannot be switched off in an attack, developers can call the “SetProcessDEPPolicy“ API in an application initialization routine.ASLR is complementary to DEP in that it prevents the generic DEP bypass method of re-using snippets of code from legitimate executable images in memory[9] by making the memory locations of loaded executable images (as well as the location of the stack) hard for the attacker to guess. As with DEP, an application that wishes to take advantage of this protection needs to indicate compatibility for it using a linker option[10]. Please note that this flag needs to be used when linking all DLLs in a process, not just on the main executable. ASLR is supported on Windows Vista and later and the linker option is available in Visual Studio 2005 SP1 and later. Strategies for hardening Windows applicationsStanding on Microsoft's shouldersThe exploit mitigations in both Windows and the Visual Studio toolchain are always evolving and, as you have seen, most of them are extremely “cheap” to implement in an existing project. To make sure you receive the full benefit of these technologies, make sure to build your software with the latest possible version of the compiler, linker, libraries and templates. This of course applies equally to third-party source code, libraries and components you might be using in your project.To gain additional wisdom from the Microsoft security process, read the Microsoft simplified implementation of the SDL document[17] that covers the security specific development practices mandated within Microsoft. Remember that the SDL is an iterative process so make sure you go back and check for new information when a revision is made to the documentation!Microsoft has developed a number of software libraries aimed at helping developers write more secure code, one such library is SafeInt[18] which allows you to perform safer integer calculations in C++ by using templates to do runtime checking for integer overflows. A version of SafeInt has even been integrated into Visual Studio 2010[19]. If you are forced to use C (i.e. cannot for some reason compile the code as C++ with Visual Studio) then the Windows SDK has included similar functionality for strict C in the “intsafe.h” header[20] since the Vista release. Another example is the "Secure Template Overload” functionality[21] in the Microsoft C runtime library (CRT) that can automatically convert some unsafe API calls into their safer counterparts.。


2010考研英语二逐词逐句精讲册The 2010 Postgraduate Entrance Examination English II Word by Word Detailed Explanation Book is a comprehensive guide for students preparing for the exam. This article aims to provide a detailed analysis of the book's content, highlighting its key features and benefits.The book begins with an introduction to the format and structure of the English II exam. It explains the different sections, including reading comprehension, vocabulary, grammar, and translation. This provides students with a clear understanding of what to expect in the exam and helps them plan their preparation accordingly.The first section of the book focuses on reading comprehension. It provides a step-by-step guide on how to approach and answer different types of reading comprehension questions. The book emphasizes the importance of careful reading and understanding the main idea of each passage. It also provides strategies for answering questions related to inference, vocabulary, and tone. The detailed explanations and examples help students improve their reading comprehension skills and increase their chances of scoring well in this section.The next section of the book covers vocabulary. It provides a comprehensive list of commonly tested words and phrases, along with their meanings and usage. The book includes exercises and practice questions to help students reinforce their understanding of these words. It also provides tips on how to expand vocabulary and improve word recognition skills. The systematic approach to vocabulary building in this book is extremely helpful for students looking to enhance their language proficiency.The grammar section of the book is another valuable resource for students. It covers various grammar topics, including tenses, articles, prepositions, and sentence structure. The book explains each concept in a clear and concise manner, making it easy for students to grasp and apply the rules. It also provides practice exercises to reinforce learning and assess understanding. The grammar section of this book is particularlyuseful for students who need to brush up on their grammar skills and eliminate common mistakes.The final section of the book focuses on translation. It provides a range of translation exercises, covering different types of sentences and language structures. The book explains the key principles of translation and provides strategies for accurate and effective translation. It also includes model answers and explanations to help students understand the nuances of translation. This section of the book is beneficial for students who need to improve their translation skills and prepare for the translation component of the exam.In conclusion, the 2010 Postgraduate Entrance Examination English II Word by Word Detailed Explanation Book is a valuable resource for students preparing for the exam. Its comprehensive coverage of reading comprehension, vocabulary, grammar, and translation makes it a comprehensive guide for exam preparation. The detailed explanations, examples, and practice exercises help students enhance their language skills and increase their chances of success in the exam. Whether used as a self-study resource or as a supplement to classroom instruction, this book is an essential tool for students aiming to excel in the English II exam.。

目錄簡介 (1)Publisher 2010:快速瀏覽 (2)建立外觀出色的出版物 (2)節省時間並簡化工作 (3)適時運用正確的工具 (3)讓您更有自信分享出版物 (4)Publisher 2010:深入瞭解 (5)輕鬆存取線上範本增強設計! (5)自訂範本並重複使用自訂內容 (6)建置組塊增強設計! (7)與 Publisher 使用者社群共享全新設計! (8)編輯和使用相片工具全新和增強的設計! (10)物件對齊技術全新設計! (12)精細印刷樣式全新設計! (12)即時預覽全新設計! (14)貼上時即時預覽全新設計! (14)隱藏草稿區全新設計! (16)頁面導覽全新設計! (17)功能區全新設計! (18)Backstage 檢視全新設計! (19)整合的列印體驗全新設計! (20)商業與數位印刷支援增強設計! (21)發佈成 PDF 或 XPS 增強設計! (23)語言工具增強設計! (24)儲存和管理客戶清單 (25)傳送電子報 (25)功能位置 (27)版本比較 (33)常見問題集 (38)需求\揭露 (42)簡介Microsoft® Publisher 2010 提供簡單易用的設計工具,能讓您建立、列印和共享具有專業品質的行銷資料和出版物。
經過更新的使用者介面讓工作更有效率,增強的相片工具讓您獲得更精確的結果,視覺化的指南則能幫助您導覽出版物並查看列印內容。
無論您需要摺頁冊、傳單、目錄或電子報,您都可以用更低的花費和更少的工作量自行製作。
Publisher 2010 讓您輕鬆建立屬於自己的成功宣傳方式。
Publisher 2010:快速瀏覽實現您的創意您不必是專業設計師,就能夠製作出專業的行銷和宣傳資料。
各種預先設計好可自訂的範本,以及簡單好用的設計工具,都可幫助您快速將創意付諸實行,建立視覺效果豐富的出版物。
建立外觀出色的出版物您的內容外觀會大幅影響對象接收資訊的意願。

OverviewOracle BI Publisher (formerly known as XML Publisher) is a revolutionary reporting and document output management solution from Oracle. Oracle BI Publisher report formats can be designed using Microsoft Word or Adobe Acrobat, the tools that are easy to use, and most users are already familiar with. Oracle BI Publisher also allows you to create reports from multiple data sources.Oracle BI Publisher can be used as a stand-alone reporting product or integrated with the Oracle Business Intelligence Suite Enterprise Edition. You will start by logging in to BI Publisher and create reports from various data sources, such as Oracle Database, Web services, RSS feeds, and Files. You will also create parameterized report that uses LOVs.Because BI Publisher is integrated with Oracle BI Enterprise Edition, you can also create the BI publisher reports based on Oracle BI Answers request, and also based on Oracle BI Server subject area. However, these topics are briefly discussed in this tutorial. For more details, you can refer to the OBE titled "Integration of Oracle BI Publisher with Oracle Business Intelligence Enterprise Edition, 10.1.3.2."Also, you will be guided through the steps to create and publish RTF templates in MS Word by connecting to BI Publisher. You will also schedule the report, and view the saved data.ScenarioYou will be using various data sets for this OBE. For example, you will create a simple employee salary report based on the human resources (HR) sample schema of the Oracle Database. For the File data set, you will use the demo files and templates that are provided with BI Publisher. For the BI Answers request and BI Server subject area,SH.rpd is used, which is based on the SH schema of the database, and so on.To continue with the steps listed in the topics, you should have installed the required software and performed the other setup as mentioned in the following topic, Prerequisites.PrerequisitesBefore starting this tutorial, you should:1.Have access to or have installed Oracle Database 10g (preferably version 10.2)2.Have access to or have installed the sample schemas (HR, OE, and SH specifically)3.Have access to or have installed Oracle BI Publisher and Oracle BI PublisherDesktop 10.1.3.2.You can install BI Publisher Desktop by clicking the Template Builder link in BI Publisher: When you have successfully installed BI Publisher Desktop, the BI Publisher menu and BI Publisher toolbars are displayed in MS Word.Note: Oracle BI Publisher Desktop was formerly known as Template Builder, and ismainly used for building the RTF templates for BI Publisher reports in MS Word4.Have created a user for installing the BI Publisher scheduler schema tables by performing the following:Create a BIPSched user with the required privileges in the database by logging in toSQL* Plus as the sys or system user:SQL> create user bipsched identified by bipscheddefault tablespace userstemporary tablespace tempquota unlimited on users;SQL> grant connect, resource to bipsched;Note: The name of the user can be any appropriate name.5.Have set up the proxy parameters (to avoid any firewall problems with the Web Services and RSS data set reports) in the xmlpserverstart.bat file or the oc4j.cmd file as per your installation.Modify the following line, which defines JAVA_HOME. (Observe the proxy parametersin bold.):• "%JAVA_HOME%\bin\java" %JVMARGS% -jar -Dhttp.proxyHost= <> -Dhttp.proxyPort=<Port> "%OC4J_JAR%"%CMDARGS%Restart xmlpserver or oc4j as the case may be.If you want to create reports based on Oracle BI Answers request and Oracle BI Server subject area, then you should also:1.Have access to or have installed Oracle BI EE 10.1.3.2 including Oracle BI Publisherand Oracle BI Publisher Desktop 10.1.3.2.You can follow the instructions as listed in the OBE " Installing the Oracle Business Intelligence Suite Enterprise Edition on Windows."2.Have created an ODBC connection to the Oracle Database, and set up the SH.rpd metadata repository by following the steps listed in the OBE "Creating Interactive Dashboards and Using Oracle Business Intelligence Answers." Also, it is strongly recommended that you go through this tutorial to know the steps involved in creating an Answers request, creating a dashboard page, and so on.3.Have set up the integration between BI Publisher and Oracle BI EE:If you have included BI Publisher Enterprise, when you installed Oracle BI Enterprise Edition, then Oracle BI installer will set up the integration with the Presentation Services, by setting host name, port, and URL values. However, you need to set the Administrator password from the BI Administration tool as follows:1. Select All Programs > Oracle Business Intelligence > BI Administration.2. Select Open > Online. ( To open SH.rpd online, enter Administrator as User nameand leave the Password field blank.)3. Select Manage > Security > Users > Administrator, and check out theAdministrator user.4. In the properties, set the password for the Administrator user and click OK.If the Integration with Presentation Services is not set up at the time of Oracle BI EE installation, you can also set up this integration from BI Publisher as follows:1. From the Admin page, under Integration, select Oracle BI Presentation Services.2. Enter the following information about your BI Presentation Services server:• Server Protocol – Select http or https• Server Version – Select v4• Server – Enter the server host name (for example, )• Port for the server – The default port is 9704.• Administrator Username and Password• URL Suffix – The default value is analytics/saw.dll.Getting StartedFor getting started with BI Publisher, perform the steps listed in each of the following subtopics:Logging In to Oracle BI PublisherSetting PreferencesLogging In to Oracle BI Publisher:To log in to BI Publisher, perform the following steps:1.Enter the URL for BI Publisher in a browser window which is of the format:http://<hostname>:<port>/xmlpserver/ (for example,http://localhost:9704/xmlpserver/)The Log In screen for the BI Publisher appears. Enter Administrator as theUsername and Password. Click Sign In.Note: Ensure that you have the correct password for the Administrator user in BI Publisher, else you may face problems in logging in to BI Publisher.Also, on Windows, depending on the type of installation you have done, you can invoke BI Publisher as follows:• If you have installed BI Publisher along with Oracle BI Enterprise Edition, then you can select All Programs > Oracle Business Intelligence > BI Publisher from the Start menu.If you have installed BI Publisher in stand-alone mode, then select All Programs > Oracle - OracleHome > BI Publisher Server from the Start menu.OracleHome - refers to Oracle Home name, where you installed Oracle BIPublisher.2.This displays the Welcome screen for BI Publisher.Note: As you have logged in as the Administrator, the welcome page displays the Reports, Schedules, and Admin tabs. For the users who do not have administrator privileges, the Admin tab is not displayed.Setting PreferencesTo change the preferences, perform the following steps:1. Click Preferences link. (highlighted in the screen below):The Preferences screen is displayed with the General Preferences and Account tabs.2. Observe the options on the General Preferences tabbed page, and select theappropriate options for UI Language, Reports Locale, Reports Time Zoneaccording to your requirements. Click Apply.Note: You can also enable the accessibility option.3. To edit the password settings for the Administrator account, click the Accounttab.Change the password for Administrator as required by entering the current and new passwords in the screen. Click Apply to save the preference settings.Note: If you have installed BI Publisher along with Oracle BI Enterprise Edition, forthe integration between these to work, for any given user account , you should set the same password in BI Administration Tool and in BI Publisher. (Refer toPrerequisites section for setting up integration between BI Publisher and Oracle BI EE.)Creating a BI Publisher Report Based on Oracle DatabaseIn this topic, you will create an employee salary report based on the HR schema of Oracle Database. To create a BI Publisher report based on a query directed to Oracle Database, perform the following steps:1. Before you create a query based on Oracle Database, you need to define theconnection details in the Admin tab.Click the Admin tab. Click JDBC Connection found under the Data Sources sectionof the page.2. In the JDBC Data Sources screen displayed, click demo to edit the connectiondetails for this datasource.Note: You can also add a new data source and define the connection details.3. In the Update Data Source screen, enter the following details:Connection String: This is of the format: jdbc:oracle:thin:@<Host name>: <Port>:<SID>,for example, a sample connection string may look like:jdbc:oracle:thin:@myhost:1521:orclUser Name: oePassword: oeDatabase Driver Class: oracle.jdbc.driver.OracleDriver (This is the default.) Do not click Cancel or Apply.4. After entering the above details, click Test Connection.When the confirmation message is displayed saying that the connection is established successfully, click Apply to save the connection details.Note: OE schema also gives access to HR schema.5. Click Reports to go back to the Reports page.Click My Folders , and click Create a New Folder link (found in the Folder and Report Tasks section).Enter Learn as the folder name and click Create. (You will save the reports you create in this tutorial in this folder.)6. To create report based on Oracle Database, navigate to My Folders > Learn, andclick Create a New Report.Enter Based on OracleDB as the name of the report, and click Create.7. The report is displayed in the Learn folder in BI Publisher.Click the Edit link under the name of the report to open the report in Edit mode.8. In the General Settings section of the Report Properties, select demo from theDefault Data Source drop-down list.Click the Save icon (found at the top-left corner) to save the changes.9. Click Data Model and click New to define the data source for this report.10. In the Data Set screen that appears,ensure that SQL Query is selected as Type, and demo is selected as Data Source.Select the Cache Results check box,and click Query Builder to define the query.11. The Query Builde r screen appears, ensure that HR is selected from the Schemadrop-down list. is displays objects from HR schema on the left. Click EMPLOYEES and DEPARTMENTS tables to add them to the Model canvas on the right.12. Define a join between these two tables as follows:Click the box beside the DEPARTMENT_ID column in the DEPARTMENTS table.(See the following screens.)Similarly click the box beside the DEPARTMENT_ID column in the EMPLOYEES table. These boxes when marked for joins turn to light gray.Also note that a fine line joining the tables appears in the Model canvas.Hint: Take the help of the screens below:13. Select the following columns from the tables (by selecting the check boxes beside thecolumn names):-Select FIRST_NAME, LAST_NAME, HIRE_DATE, and SALARY columns from the EMPLOYEES table-Select DEPARTMENT_NAME from the DEPARTMENTS table.14. Click Conditions, and move the DEPARTMENT_NAME, to appear first in the listYou can use these icons beside each column to move the columns up or down.Similarly, move SALARY and other columns, so that the final list appears like this:15. Click Results to see how the query results appear in Query Builder.Click Save to save the query.16. This will take you back to the Data Set screen, with the query you created reflected inthe SQL Query text area. Click Save to save the BI Publisher report.17. If required, you can further edit the query manually. For example, instead ofdisplaying the FIRST_NAME and LAST_NAME columns separately, you may want to concatenate both these columns and display this as a single columnEMPLOYEE_NAME.So you can modify the query as:select DEPARTMENTS.DEPARTMENT_NAME as DEPARTMENT_NAME,EMPLOYEES.FIRST_NAME || ' '||ST_NAME asEMPLOYEE_NAME,EMPLOYEES.HIRE_DATE as HIRE_DATE,EMPLOYEES.SALARY as SALARYfrom HR.DEPARTMENTS DEPARTMENTS,HR.EMPLOYEES EMPLOYEESwhere DEPARTMENTS.DEPARTMENT_ID=EMPLOYEES.DEPARTMENT_IDClick Save again to save the changes to the query. Note: Ensure that a space is included in the query (as in the example) between the FIRST_NAME andLAST_NAME columns in the concatenation string of EMPLOYEE_NAME. Also, note that once you have edited the query manually, you will not be able to edit the query in Query Builder.18. Click View to view the report. Because you have not defined a template, you canview only XML data. Click View again to view the XML data.Note: You may not be able to interpret the XML data, but you may want to check whether the BI Publisher report is returning some valid data by viewing the XML data before creating a template for the report. Creating and publishing templates iscovered in the next topic.Creating Report Layouts Using BI Publisher Desktop (Template Builder) in MS WordIn this topic, you create RTF template for a BI Publisher report and publish it. You will also work with multiple templates for a report, and view the report data using these templates in various formats. Note: All the subtopics in this topic are continuous, so follow the instructions, and do not close any applications or windows as mentioned in the steps.Creating an RTF Template with a Table and ChartPublishing the Template for a BI Publisher ReportFormatting the Templates Using MS Word Native FeaturesCreating and Publishing Multiple Templates for a ReportViewing Report Data in BI Publisher Using TemplatesCreating an RTF Template with a Table and Chart1. Start the MS Word application from the program menu.From the Oracle BI Publishermenu, select Log On.Note: The Oracle BI Publisher menu is displayed in MS Word only when you have successfully installed the Oracle BI Publisher Desktop as mentioned in step 3 of the Prerequisites section. Also, observe the BI Publisher toolbar in MS Word, with the Data, Insert, Preview, Tools, and Help menus. Observe the various options in thesemenus.2. In the Login screen that appears, enter Administrator as the Username andPassword, and click Login.The first time when you connect, you may be asked for the report server URL, enter the URL which is of the format:http://<Host>:9704/xmlpserver3. This displays the Open Template window. Ensure that BI Publisher is selected fromthe Workspace drop-down list.Navigate and select the Based on Oracle DB report that you have created from My Folders> Learn. Click Open Report.Note: When you open the report you will not see any data in the MS Word document, but this will load the XML data definitions from the query to facilitate the defining of a template.4. In the Word document that loads this report, select Insert> Table Wizard on the BIPublisher toolbar to define a format for the table data in the query.5. This displays the Table Wizard. Select Table and click Next.6. In the next step, ensure that ROWSET/ROW is selected as the Grouping Field, andclick Next.7.In the next step, click to include all the available columns in thetable. .8. In the next step, select Department Name from the Group By drop-down list, ensurethat the Group above option is selected, and accept the defaults for other options.Click Next.9. In the next step, select Salary from the Sort By drop-down list, and select theoptions Descending and Number to sort the Salary column in descending order.Click Next.10. In the next step you can edit the labels of the columns as required. Accept thedefaults and click Finish.The template you created looks like this:Important Note: The BI Publisher Desktop Template Builder has just created a table for you. Notice the words and letters with the gray background. These are called form fields. Form fields are Word objects that allow you to reference other data (for example, a mail merge letter). BI Publisher uses form fields in two ways:First is to reference data fields from the report definition (like YEAR and MONTH).The second use is to embed instructions that control how the data fields will be laid out (like G-Group By, F- For Each , and E- End).If you are curious to know what these instructions are, double-click the form field and view the Help text. It is important to treat these form fields carefully and not accidentally delete or move them. Doing so will change the layout of the table in your report. Also, you can add or modify your own form fields with XSL commands to do more sophisticated things with the table layout.Also, you can additionally use MS Word's native formatting features on this template, such as changing the background and text colors, adding a title, and so on. This is covered in the next topic.11. You can also add a chart in the template. For example, you can add a chart todisplay the average employee salaries by department in this report.To add a chart to the template, select Insert > Chart.12. In the Chart window that appears, define the graph characteristics by following theinstructions listed below carefully:Drag Salary to the Values field and Department Name to the Labels field. Also, select Average from the Aggregation drop-down list for the Salary. (These are highlighted in the screen below.)Select Pie Chart from the Type drop-down list for the graph. Click Preview to preview how the graph looks like, and click OK.Note: If you do not like the style and type of the graphs in the preview, you can change them after the preview or later.13. Now the template along with the graph in the Word document looks like this:14. Select the File> Save As option. Enter Based_On_OracleDB.rtf as the name ofthe template, and click Save.Do not close the file or log out of BI Publisher.Note: You can save the file in any local folder on your system, but you have to save the template in the .rtf format (not in the .doc format).15. You can also preview how the template looks like with the data by selectingOracle BI Publisher> Preview Template, and then selecting a format like PDF to view the data.The graph looks like this:Publishing the Template for a BI Publisher ReportYou can directly publish a template that you have created in MS Word for a BI Publisher report, provided:• You are connected to BI publisher from MS Word• The BI Publisher report is opened in MS Word• The template is saved in RTF formatTo publish the Based_On_OracleDB.rtf template that you created in MS Word, and then view data for the report in BI Publisher using this template, perform the following steps: (Note that the template you have created satisfies all the above criteria.)1. In MS Word, select the Oracle BI Publisher> Publish Template As option.Note: If you have not saved the template in RTF format, it may prompt you to save the template in RTF format first before publishing.2. The Upload as new dialog box appears.Enter Template1 as the template name, and click OK.template is added to the BI Publisher report. Click OK again.Back to TopicFormatting the Template Using MS Word Native FeaturesIn this topic, you will modify the Based_On_OracleDB.rtf template that you have created using the MS Word native features, such as changing the background and text colors, adding a title, and so on.Perform the following steps:1. The basic Based_On_OracleDB.rtf template that you have created is shown below:Make the following changes using the MS Word features:1. Change the fonts for all the fields, that is Department Name, EmployeeName, Hire Date, and Salary to Arial.2. Select 12 as the font size for the Department Name, and 10 as the font sizefor other fields.3. Change the text color for the Department Name field to dark blue, highlight thebackground for this field by cyan, and make it Bold.4. Also ensure that the Employee Name and Hire Date (text and date fields) areleft justified, and the Salary (Number) filed is right justified. Use the align leftand align right icons on the toolbar.The table in the template should look like the screen below after thesechanges:2. Edit the Hire Date field to add the appropriate format as follows:1. Double-click the text field for Hire Date below the column header. (See thescreen below.)In the Text Form Field Options dialog box that appears, select Date from the Type drop-down list, select m/dd/yyyy from the Date format drop-down list, and click OK.3. Similarly, edit the Salary field now to add an appropriate format as follows:1. Double click the Salary field below the column header.In the Text Form Fields dialog box that appears, select Number from the Type drop-down list, enter the Default Number as 99,999,999.99, select the format that has a $ in the beginning as shown, and click OK.Now the table in the template should look like this:4. Add a title Employee Salary Report to the template, and format the text color andfonts as you require. You can also add an image or a clip art to the template. (Resize it to fit your template better.)You can also insert a header or footer in template.5. Save the file as Based_On_OracleDB_1.rtf.(Do not close the file or log out of BI Publisher.)Creating and Publishing Multiple Templates for a BI Publisher ReportgIn the previous topic, you have already created another templateBased_On_OracleDB_1.rtf for the Based on Oracle DB report, for which you have already published a simple template. You can create many templates with different formats and styles, and publish them for a single report.To publish the Based_On_OracleDB_1.rtf template created from MS Word, perform the following steps:1. (If not already opened) Open the Based on OracleDB BI Publisher report asfollows:.In MS Word, select the BI Publisher> Open Template option.Open the Based on OracleDB report from the path My Folders>Learn.2. In MS Word, select the Oracle BI Publisher> Publish Template As option.3. This opens the Upload as new dialog box.Enter Template2 as the template name, and click OK.After the template is uploaded, it displays the following message. Click OK again.Note: You have added two different templates for the same report Based onOracleDB. You can modify the template file, and publish it as different template each time you modify.4. If you have time, perform the following steps to edit the chart in the template file tochange the graph style, and publish it as Template3:Right-click the chart in the template and select BI Publisher Chart to edit the chart:Ensure that Average is selected as the Aggregation for the Salary, selectRegatta as the graph Style, and add Average Employee Salaries byDepartment as the Title.Click Preview, and then click OK.modified template as Template3 (as shown in the screens below):Viewing Report Data in BI Publisher Using Templates1. (If not logged in) Log in to Oracle BI Publisher as Administrator.2. Navigate to My Folders>Learn, and click the View link below the Based onOracleDB report.3. You can see that the report is displayed using Template1 that you have published.Also,you can see the other templates that you have published for the report in the drop-down list.Scroll down to see the table data in HTML format. A portion of the data is shown below:Scroll down to see the graph:Note: You can also view the data in other formats, such as PDF, RTF, MS Excel, and so on.4. Similarly, view the report data in PDF format using Template2 and Template3.The data and graph in PDF format using Template2 are shown below:The data and graph in PDF format using Template3 are shown below:Creating a Report with Parameters and List of ValuesIn this topic, you create a report with parameters and list of values. To create a report with parameters and list of values, perform the following steps:1. (If not logged in) Log in to BI publisher as Administrator , and navigate to MyFolders> Learn .Click the report icon beside the Based on OracleDB report.2. This displays additional report actions in Folder and Report Tasks.Click Copy Report and then click Paste from Clipboard to paste it in the samefolder. (See the screens below):Rename this copied report Report with Parameters and LOVs.3. Click the Edit link below the report to open the report in Edit mode.Click New Data Set1 found under the Data Model node in the Report pane on the left to edit the SQL Query for the report. Observe the screen below:4. This displays the SQL Query for the report on the right.Edit the query to add a bind variable dname in the query as in the following: (Observe the last line.)select DEPARTMENTS.DEPARTMENT_NAME as DEPARTMENT_NAME,EMPLOYEES.FIRST_NAME ||' '||ST_NAME asEMPLOYEE_NAME,EMPLOYEES.HIRE_DATE as HIRE_DATE,EMPLOYEES.SALARY as SALARYfrom HR.DEPARTMENTS DEPARTMENTS,HR.EMPLOYEES EMPLOYEESwhere DEPARTMENTS.DEPARTMENT_ID=EMPLOYEES.DEPARTMENT_IDand DEPARTMENTS.DEPARTMENT_NAME =:dnameClick Save to save the query.5. Click the Parameters node in the Report pane on the left and click New to create aparameter.6. This displays the Parameter screen on the right, in which define the following:Enter dname as the name of the parameter, and select String as the Data Type.Enter Sales in the Default Value field, and select Text as the Parameter Type.Also, enter Enter Department Name as the Display Label. (See the screen below.)Click Save to save the changes to the report.7. Click View to view the report data using Template2 in PDF format.Note that the report data is displayed with the default parameter value, that is for Sales department.8. You can enter the names of other departments to see the data.For example, in the parameter field enter Shipping as the department name and click View again to see the data for the Shipping department:9. Click Edit to edit the report and define a List of Values to be used with this parameterdname.In the Report pane displayed on the left, click List of Values, and click New to createa new list of values.10. In the List of Values screen that appears on the right, ensure that demo is selectedas the Data Source, and click Query Builder to define a query for defining a list ofvalues.11. In the Query Builder screen that displays the HR schema tables on the left, clickDEPARTMENTS to add it to the Model canvas on the right, and selectDEPARTMENT_NAME column (by selecting the check box beside it).Click Save.This takes you back to the List of Values screen again which displays the query.Click Save to save the changes to report:12. Click dname under the Parameters node in the Report pane on the left to edit it andassociate it with the List of Values that you have created:。
2010/2011ImmersiongProgram HCIA & Company Portfoliop p pOpen to the world, Open to possibilities我们的历史2005年,HCIA团队在香港创建,从公益活动开始,为学生提供免费的赴港实习机会。
我们先后支持43名学生到位于香港长江集团中心的讯汇金融公司实习,并组织志愿者前往东南亚海啸灾区开展援助工作。
2006年,由曾经供职于著名风险投资机构、国际投资银行和战略咨询机构的职业人士组成了HICA的核心管理团队,他们拥有包括斯坦福大学麻省理工学院工商管理硕士等学位。
同时,来自商业、技术及教育行业的数名资深人士组成了HCIA国际化的顾问团队。
我们的见习项目合作伙伴扩展到财富500强公司,并积极开拓海外实习项目,包括德国的JO&KE企业实习。
这一年,我们与联合国儿童基金会合作,共同参与河南艾滋村儿童公益活动。
们与联合国儿童基金会合作共同参与河南艾滋村儿童公益活动2007年,HCIA团队与香港十多家企业合作,提供了超过500个企业实习机会。
同年我们与香港城市大学、香港大学建立合作关系,开始大学交换项目,并正式推出我们的核心高端项目——“国际商业精英项目”Business Elite Program,开始在内地及港澳台名校大学生提供交流培训方案,给中国学生及有经验的个人提供新的机遇。
HCIA加入中国香港商会成为中国香港商会正式企业会员。
2008年,我们提供了超过1000个大学交换和企业实习项目机会,并开始在斯坦福大学、哈佛大学、麻省理工学院、剑桥大学等一流学府推广商业精英项目。
同年,我们为清华北大的学生提供了20个国际领导奖学金名额,资助他们赴港参加“国际商业精英交换项目。
5月,HCIA无国界志愿者组织的志愿者前往四川地震灾区开展援助工作。
交换项目”5月HCIA“无国界志愿者组织”的志愿者前往四川地震灾区开展援助工作2009年,我们开始与斯坦福大学东亚研究中心建立合作关系,共同开展“国际商业精英项目”。
随着HCIA行业地位的不断提升,我们承担起更多的企业社会责任。
这一年,在全国范围内举办的公益商业面试大赛、商业策划书大赛等活动中,HCIA为全国近百名优秀大学生提供了免费赴港交流和培训机会。
2009年,我们成立斯雅有限公司(HCIA & Company),正式在中港两地运营,HCIA从此开始公司化管理。
同年,斯雅公司成功加入中国美国商会,成为中国美国商会正式企业会员。
2010年,我们与香港大学亚洲研究中心、香港政策研究所、财富500强企业成功举办商业体验项目。
成功在上海金茂君悦酒店、北京东方君悦酒店举办第二届全国模拟面试大赛,提供免费商业体验名额给优秀大学生;以商会企业会员身份,成功推荐优秀校友加入中国香港商会、中国美国商会。
友加入中国香港商会中国美国商会商业体验计划项目介绍商业体验计划项目由斯雅有限公司主办,目的是希望能藉由大学交换、企业研习,促进来自不同地区及文化背景的青年学生与知名大学教授、著名企业专业人士有交流和互动的机会。
通过专业培训、企业体验以及系列专景的青年学生与知名大学教授著名企业专业人士有交流和互动的机会通过专业培训企业体验以及系列专业策划大赛,加深合作企业、知名高校和参与者的相互了解,实现三方共赢的最终目标。
项目分为五部份一) 大学课程大学课程部份由香港大学亚洲研究中心、香港政策研究所联合举办,课程由知名大学的优秀教授或行业的资深专家任教,为学员提供领导力及专业商业策划书撰写培训。
授课教师通常担任著名金融机构、知名企业的高级顾问,他们不仅具有国际认可的高等学历,也拥有丰富的业内知识、出色的教学经验和广泛的人脉网络。
二) 企业体验二)企业体验香港大学课程完结以后,学生将开始企业体验计划。
计划由知名企业高层(公司高级副总裁、董事、区域总裁、顾问等)亲临负责,通过企业体验、见习了解企业的日常运作、核心工作、企业文化以及远景。
同时学员需要通过采访企业客户、管理层以及专业人士,搜集并分析相关资料,结合在香港大学所学习的商业策划书撰写技巧为相关企业起草企业商业策划书。
商业体验计划项目介绍三)商业策划报告三) 商业策划报告在项目的过程中,学生需要按照香港大学亚洲研究中心、香港政策研究所以及公司的要求,根据公司现有发展情况、市场分析、竞争性分析、产品与服务、市场与销售、宏观环境分析方法、PEST分析法、政治环境、经济环境、社会文化环境、技术环境、企业的各个部门以及人才需要分析,完成商业策划报告及演说,并接受相关项目机构颁发的项目参与证书和针对报告及演说的推荐信。
四) 商业策划书比赛商业策划书比赛是由斯雅有限公司及项目相关企业赞助的比赛项目。
这项赛事主要考察学员对公司运作、战略制定与实施、市场开拓和培育、财务数值分析及市场变化的综合分析和随机应变能力。
商业策划案:检验学员系统性的战略思考能力,全面把握一个行业的能力及文字说服力。
学员将根据公司提出的不同研究课题,以某产品的营销策略为主线,从行业调查、市场现状分析、消费者市场细分、企业目标、执行方案、产品分析及成本与收益分析等方面,完成一套切实可行的商业策划书。
五) 领导力实践商业体验计划结束后,学员可以根据其在香港大学所学习的领导力技巧,向斯雅有限公司所举办的企业社会责商业体验计划结束后学员可以根据其在香港大学所学习的领导力技巧向斯雅有限公司所举办的企业社会责任项目提出“领导力发展”申请。
申请者可以申请成为斯雅公益活动的管理层,并担任领导职务。
申请者需要向斯雅有限公司提供完整的学期工作计划、领导力策划书以及项目发展纲领。
申请者需要向斯雅有限公司提供完整的学期工作计划领导力策划书以及项目发展纲领商业体验计划日程安排第一天/ Day 1 08:30-09:00香港大学集合08:3009:00 09:00-09:15 开幕式:港大校方代表致辞09:15-11:45讲师课题:香港与大陆市场经济环境分析11:45-13:30 午休13:30-16:30讲师课题:企业策划书撰写指导一13:3016:30 讲师课题:企业策划书撰写指导16:30-17:00 小组针对课题进行组内讨论并与讲师交流17:00-18:00 晚餐、休息18:00-20:00 公司Orientation 20:00-23:0020:0023:00 小组设计市场调研问卷内容,分配调查任务回顾商业策划书撰写的方法,小组内分工并收集相关资料第二天/ Day 2 09:00-11:30 讲师课题:企业策划书撰写指导二11:30-12:0011:30-12:00 小组针对课题进行组内讨论并与讲师交流12:00-13:30 午休学生进行市场调研工作13:30-16:00 讲师课题:如何成为跨国人才16:00-16:3016:00-16:30 小组针对课题进行组内讨论并与讲师交流16:30-17:30 结业典礼:香港大学高层颁发证书并合影留念17:30-19:00 晚餐、休息19:00-23:00 整理调查问卷结果,小组内分享,总结分析商业策划书分工起草网上收集资料组内讨论商业策划书分工起草,网上收集资料,组内讨论商业体验计划日程安排第三天/ Day 308:30全体同学公司集合08:3009:0008:30-09:00 公司高层致词09:00-12:00 公司介绍,香港金融市场介绍12:00-13:30 午休13:30-17:00 客户案例分析17:00-19:00 晚餐、休息19:00-23:00 商业策划书相关部分的撰写第四天/ Day 408:30全体同学公司集合09:00-11:30 参观香港证券交易所,了解香港金融市场11:30-13:30 午休13:30-17:00 投资风险管理模拟实战17:00-18:00 讨论商业策划书的核心部分18:00-19:30 晚餐、休息19:30-23:00 完成商业策划书终稿,成果展示PPT及团队展示PPT 19302300完成商业策划书终稿成果展示PPT及团队展示PPT 第五天/ Day 508:30全体同学公司集合08:30-11:00 导师辅导小组预演商业策划书展示环节,并完善PPT 1100120011:00-12:00 公司考试12:00-13:30 午休13:30-18:30 各小组项目成果展示,团队展示,公司高层点评18:30-19:30 颁发证书和高层推荐信19:30-20:30 结幕礼19:30-20:30香港大学我曾经学习过的地方谁不愿,与高端校友无间交流,超越般同窗之情,分流超越一般同窗之情分享国际经历?融入名校名企,超越你自己港大交换| 企业高层推荐信|英文研习报告课堂瞬间,拍摄于香港大学。
港大课程内容:领导知识经济学会计学市场营销法律经济及商业策划书撰写财富五百强企业香港研习“以前我从未想到离开校园,还能有这么多的学习机会”港大交换| 企业高层推荐信|英文研习报告谢同学,上海财经大学本科生,斯雅商业体验项目校友,拍摄于苏黎世金融集团,2010年1月.想了解更多关于研习生他们今年在香港企业的工作内容、照片、视频,请下载我们的宣传册完整版想了解更多关于研习生他们今年在香港企业的工作内容照片视频下载地址: http://brochure.hcia.hk, 或登录我们的项目网站,了解更多: http://2010.hcia.hk企业商业研习研习报告演说Life -ChangeLife Change.Lifelong港大交换| 企业高层推荐信|英文研习报告Fabian Sinn, 斯雅商业体验项目校友,拍摄于2010年苏黎世金融集团香港你知你潜力有多大有没有决像他们那样在香港宵达为公作付,发挥你潜力你想知道你的潜力有多大吗?有没有决心像他们那样在香港通宵达旦的为了公司工作付出,发挥你的潜力?从这里开始!想进一步了解他们在香港企业里的演讲及演讲报告,请登录他们的演说展示网站: www.bpc.hk证书不会改变世界,我们留给拥有证书的人去改变A certificate will neverchange the world.We leave that to thepeople who have them.港大交换| 企业高层推荐信|英文研习报告香港大学官方证书、五百强企业高层推荐信、企业英文研习报告书、企业商业策划书大赛证书证书是代表签发机构对他们的认可,想进一步了解香港大学,请浏览香港大学官方网站: www.hku.hk,精英人脉在香港扩展工作之外更广阔的天空港大交换| 企业高层推荐信|英文研习报告国际大学教授、高层人脉:提前建立国际知名大学高层人脉关系;跨国企业管理层及专业人士:增强业界专业交流扩展人脉;跨国企业管理层及专业人士:增强业界专业交流、扩展人脉;往届校友:主要分布在投资银行、商业银行、跨国咨询公司、跨国消费品合约保证信心可靠ContractGuarantee港大交换| 企业高层推荐信|英文研习报告斯雅公司凭借五年的项目运营经验,合约保证公司的商业体验项目的具体日程安排、证书,合约内会列明无效退款,保障参加者利益,令参加者拥有100%的保证承诺及不会浪费一分一毫。