TCP Performance in Coded Wireless Mesh Networks
- 格式:pdf
- 大小:291.86 KB
- 文档页数:11

FAMILY DATASHEETMR Cloud-Managed Wireless Access PointsOverviewThe Meraki MR series is the world’s first enterprise-grade line of cloud-managed WLAN access points. Designed for challenging enterprise environments, the MR access points use advanced Wi-Fi 6 technologies, including MU-MIMO, OFDMA, beam forming and channel bonding, to deliver the throughput and reliable coverage required by demanding business applications.Centralized cloud managementThe award-winning Cisco Meraki cloud-managed architecture provides powerful and intuitive centralized management while eliminating the costand complexity of traditional on-site wireless controllers. Seamlessly manage campus-wide Wi-Fi deployments and distributed multi-site networks with zero-touch access point provisioning, network-wide visibility and control, cloud-based RF optimization, seamless firmware updates, and more. With an intuitive browser-based user interface, Meraki WLAN configures in minutes without training or dedicated staff. Adding new sites to a network takes minutes,not hours or days, and there’s no need to train additional staff to monitor ormanage the remote networks. Meraki devices self-provision, enabling largecampus and multi-site deployments without on-site IT.Class-leading enterprise featuresThe MR series comes equipped with industry-leading features that make them ideal for demanding enterprise deployments:• Self-configuring, plug-and-play deployment• 802.11ax MU-MIMO with up to eight spatial streamsbuilt for voice and video• Integrated enterprise security and guest access• Dedicated radio for security and RF optimization with integrated spectrum analysis (indoor models)• Integrated intrusion detection and prevention system (WIDS/WIPS)• Self-learning application-aware traffic analytics engine• Flexible group policy engine for creating and applying application-aware policies by network, device-type, and end user• Integrated Bluetooth® IoT radio• Self-healing, zero-configuration mesh• Role-based administration and automatic, scheduled firmware upgrades delivered over the web• E-mail and text message alerts upon power loss, downtime, or configuration changesBluetooth ® Low Energy be con nd sc nning r dio Dedic teddu l-b nd sc nning nd security r dio2.4 GHz 802.11b/g/n/ x5 GHz 802.11 /n/ c/ xEnterprise security and a dedicated radio The MR series comes equipped with complete out-of-the-box enterprise-class security. Segment wireless users, applications, and devices; secure your network from attacks; and enforce the right policies for each classof users. A built-in stateful policy layer 3/layer 7 firewall, 802.1X/RADIUS support, and native Active Directory integration deliver fine-grained access control, while a guest access firewall provides secure, internet-only guest Wi-Fi in just one click. Integrated network access control (NAC) provides end-user antivirus scanning for accurate client device posture assessment to protect your wired and wireless network against virus infections. Indoor APs feature a radio dedicated to full-time scanning, rogue AP containment, and automatic RF optimization. With Air Marshal, it is possible to set up a real-time wireless intrusion detection and prevention system (WIDS/WIPS) with user-defined threat remediation policies and intrusion alarms, enabling secure wireless environments without complex setup or systems integration. Auto RF eliminates the need for manual RF configuration by scanning the environment for utilization, interference, and other metrics, and computing the optimal channel and power settings for every AP in the network. Meraki WLANs are fully HIPAA and PCI compliant. Meraki MR APs integrate with Cisco Umbrella™ (formerly OpenDNS) offering a cloud-delivered first line of defense against security threats like malware, ransomware, and phishing. Cisco Umbrella, the industry’s first secure internet gateway, protects client devices at the DNS layer. The integration ensures DNS blind spots are proactively monitored and not exposed to malicious security threats.Cisco ISE with change of authorization (CoA) provides secure access for authorized guests, oversight on guest onboarding, and identifies potential BYOD security threats.Combine Meraki MR access points and Meraki MS switches to eliminate manual per-access-port configurations and reduce installation costs with SecureConnect, which automatically authorizes the MR access point and deploys security profilesfacilitate optimization of opening hours, marketing campaigns, and staffing policies.PRESENCE ANALYTICS (FOR NON-ASSOCIATED CLIENTS)facilitates seamless discovery of Apple devicesDEVICE REPORTING AND ANALYTICSacross VLANs, rounding out a full BYOD-centricfeature set.Combine Meraki MR access points with Meraki cloud-based mobile device management (MDM)—called Meraki Systems Manager—to monitor each of your organization’s devices, showing useful metrics including client hardware/software information and recent location, and centrally manage your corporate devices with a great degree of granularity. Log in with remote desktop or command-line, push new applications, and remotely lock and erase devices. Meraki SM provides secure and seamless client onboarding by encouraging devices connecting to corporate Wi-Fi to enroll into Systems Manager and encrypting networktraffic between a user’s device and the access point.Auto-tunneling VPN technologyLeveraging the Meraki cloud architecture, site-to-site VPNs can be enabled via a single click without any command-line configurations or multistep key permission setups. Complete with IPsec encryption, deploy the following architectural setups within minutes:• Teleworker VPN: Securely extend the corporate LAN to remote sites wirelessly using the MR series with your own server or a Meraki MX• Site-to-site VPN: Multi-branch VPN with WAN optimization and Ccontent filtering (using Meraki MX security appliance)• Secure roaming: Layer 2 and layer 3 roaming for large campus environmentsDistributed packet processingMeraki devices execute packet processing at the edge. Each wireless access point features a high-performance CPU that enforces layer 3-7 firewall policies, applicaiton QoS, network access control (NAC), and more. Meraki networks scale seamlessly—add capacity by simply deploying more APs–without concern for controller bottlenecks or choke points.Every Meraki wireless access point is built with the packet-processing resources to secure and control its client traffic without need for a wireless LAN controller. Meraki APs are built with a high-performance CPU, hardware-accelerated encryption, and extended memory resources to implement stateful firewall policies, voice and video optimization, and even layer 7 traffic classification and QoS.Cloud-managed network assurance Meraki HealthA unified network infrastructure platform allows IT organizations to achieve faster issue remediation, maximize uptime, and optimize performance.By ingesting data from a complete network infrastructure platform, the Meraki Health heuristics engine rapidly identifies anomalies impacting wireless end users’ experiences across every stage of client connectivity—association, authentication, IP addressing, and DNS availability—for rapid root-cause analysis and response.Global scalabilityUsing Meraki Health, immediate visibility is provided to identify problematic APs and clients, gain actionable insights to pinpoint stages of failure, and determine if users are able to accessthe network. Remotely identify problematic devices anywhere across a campus or thousandsof separate geographical sites and access built-in live troubleshooting tools. Globally apply network data collection to extract insights and make configuration changes at scale to optimizeWi-Fi performance.AnalyticsRich analytics ensure performance levels withcolor-coded historical metrics—signal quality, client count, wireless latency, channel utilization, anddata rates—allowing for time-based correlationto significant events. Real-time analytics are provided for specific access points as well as individual wireless clients. Client timelines include automated root-cause identification and suggested remediation for client connectivity failures.their location, and you want them to have the right access at the right time.Prepare for what’s nextM R57The Meraki MR57 Wi-Fi 6E accesspoint delivers an improved wirelessnetwork that is faster and more reliableand designed for dense environments,high-bandwidth applications like videocalls, and services that require ultra-low latency like augmented and virtualreality. In the era of hybrid work andmeetings that bridge the physical andthe virtual, you need a network thatworks with your team, not against it.Wi-Fi 6E networks offer the “wired-like” experience that collaboration toolsrequire for a seamless, inclusive, andsecure experience.Smart spaces and automated processesthat depend on IoT devices withinmanufacturing, shipping, and logisticsfacilities no longer have to suffer fromslow Wi-Fi and intermittent connectivity.Wi-Fi 6E helps remediate these issueswith wired-like Wi-Fi speeds and aclean spectrum for every automationneed. Manufacturers can use robotsand automatically guided vehicles inwarehouses where they require ultra-low latency with the highest reliability.* Power over Ethernet injector and DC adapter sold separatelyProduct options: indoor Wi-Fi 6M R36(H)Next-generation entry-level high-performance WI-Fi 6 AP with security-scanning radio and Bluetooth® Low Energy included.Next-generation in-room hotel Next-generation AP with Wi-Fi 6technology. Ideal for medium-densitylocations with security scanning andBluetooth® Low Energy included.One 2.4 GHz 802.11b/g/n/ax One 5 GHz 802.11a/n/ac/ax One 2.4 GHz 802.11b/g/n/ax One 5 GHz 802.11a/n/ac/ax* Hardware capableM R46(E)M R56 Next-generation AP with Wi-Fi 6 technology. Ideal forhigh-density locations or focused wireless coverage withsecurity scanning, Bluetooth® Low Energy, and externalantenna option.One 2.4 GHz 802.11b/g/n/axOne 5 GHz 802.11a/n/ac/axOne WIDS/WIPS* Hardware capableM R86Rugged/outdoor high-performance Wi-Fi 6 wireless for outdoor campuses, industrial, point-point links, and outdoor location services.Rugged/outdoor highest-performance Wi-Fi 6 with Multigigabit for tough RF and high-density environments.One 802.11b/g/n/axOne 802.11a/n/ac/axOne WIDS/WIPSOne Bluetooth® radio1.7 Gbit/sec max rateTwo 2:2 MU-MIMO and OFDMA with beamforming One 802.11b/g/n/axOne 802.11a/n/ac/axOne WIDS/WIPSOne Bluetooth® radio3.5 Gbit/sec max rateFour 4:4 MU-MIMO and OFDMA with beamforming* Hardware capableProduct options: indoor Wi-Fi 5M R30H M R42(E)M R52/53(E)Usage Basic wireless, value-designed deployments.In-room hotel ordormitory deploymentsthat must service IP-enabled devices.Entry-level 802.11acwave 2 for future-proofdeployments.General purpose802.11ac wave 2 forcampus and enterprise,with external antennaoption.High-performance802.11ac wave 2 withMultigigabit for high-density campus, andMU-MIMO, with externalantenna option.M R70M R74M R84Rugged/outdoor general purpose WLAN for outdoor campuses, industrial, point-to-point links, and outdoor location services.Highest-performance 802.11ac wave 2 with Multigigabit for tough RF and high-density environments.One 802.11b/g/n One 802.11a/n/ac One 802.11b/g/n/ac One 802.11a/n/acT o learn more, visit 。
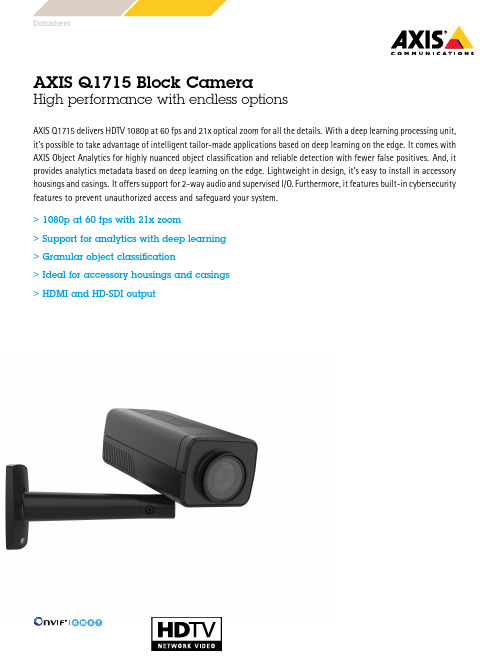
DatasheetAXIS Q1715Block CameraHigh performance with endless optionsAXIS Q1715delivers HDTV1080p at60fps and21x optical zoom for all the details.With a deep learning processing unit, it’s possible to take advantage of intelligent tailor-made applications based on deep learning on the edge.It comes with AXIS Object Analytics for highly nuanced object classification and reliable detection with fewer false positives.And,it provides analytics metadata based on deep learning on the edge.Lightweight in design,it’s easy to install in accessory housings and casings.It offers support for2-way audio and supervised I/O.Furthermore,it features built-in cybersecurity features to prevent unauthorized access and safeguard your system.>1080p at60fps with21x zoom>Support for analytics with deep learning>Granular object classification>Ideal for accessory housings and casings>HDMI and HD-SDI outputAXIS Q1715Block Camera CameraImage sensor1/2.8”progressive scan RGB CMOSLens Varifocal,4-84.6mm,F1.6-F4.5Horizontal field of view:76°–3.6°Vertical field of view:42°–2.2°Autofocus,P-Iris controlDay and night Automatically removable infrared-cut filterMinimum illumination 1080p25/30fps with Forensic WDR and Lightfinder2.0: Color:0.1lux at50IRE F1.5B/W:0.02lux at50IRE F1.51080p50/60fps with Forensic WDR and Lightfinder2.0: Color:0.2lux at50IRE F1.5B/W:0.04lux at50IRE F1.5Shutter speed1/66500s to2sPan/Tilt/Zoom Zoom:21x optical100preset positions,control queue,adjustable zoom speedUploadable PTZ driverSystem on chip(SoC)Model ARTPEC-7Memory2048MB RAM,1024MB FlashComputecapabilitiesDeep learning processing unit(DLPU)VideoVideo compression H.264(MPEG-4Part10/AVC)Baseline,Main and High Profiles H.265(MPEG-H Part2/HEVC)Main ProfileMotion JPEGResolution1920x1080HDTV1080p to160x90Frame rate Up to60/50fps(60/50Hz)in all resolutionsHDMI and HD-SDI are limited to30fps in1080pVideo streaming Multiple,individually configurable streams in H.264,H.265and Motion JPEGAxis Zipstream technology in H.264and H.265Controllable frame rate and bandwidthVBR/ABR/MBR H.264/H.265Low latency modeVideo streaming indicatorImage settings Saturation,contrast,brightness,sharpness,Forensic WDR:up to120dB depending on scene,white balance,day/nightthreshold,tone mapping,local contrast,EIS,exposure mode,exposure zones,defogging,compression,rotation:auto,0°,90°,180°,270°including Corridor Format,dynamic text and imageoverlays,polygon privacy mask,mirroring of imagesScene profiles:forensic,vivid,traffic overviewAudioAudio encoding SDI:AES324bit,48kHzHDMI:LPCM24bit,48kHzNetwork:AAC-LC8/16/32/44.1/48kHz,G.711PCM8kHz,G.726ADPCM8kHz,Opus8/16/48kHz,LPCM48kHzAudio input/output External microphone input or line input,ring power,network speaker pairingNetworkSecurity IP address filtering,HTTPS a encryption,IEEE802.1x(EAP-TLS)a network access control,user access log,centralized certificatemanagementNetwork protocols IPv4,IPv6USGv6,ICMPv4/ICMPv6,HTTP,HTTPS a,HTTP/2,TLS a,QoS Layer3DiffServ,FTP,SFTP,CIFS/SMB,SMTP,mDNS (Bonjour),UPnP®,SNMP v1/v2c/v3(MIB-II),DNS/DNSv6,DDNS, NTP,NTS,RTSP,RTP,SRTP/RTSPS,TCP,UDP,IGMPv1/v2/v3,RTCP, DHCPv4/v6,SSH,SIP,LLDP,CDP,MQTT v3.1.1,Secure syslog(RFC 3164/5424,UDP/TCP/TLS),Link-Local address(ZeroConf)System integrationApplication Programming Interface Open API for software integration,including VAPIX®,metadata,and AXIS Camera Application Platform(ACAP);specifications at/developer-community.ACAP includes Native SDK andComputer Vision SDK.One-click cloud connectionONVIF®Profile G,ONVIF®Profile M,ONVIF®Profile S,andONVIF®Profile T,specification at Support for Session Initiation Protocol(SIP)for integration withVoice over IP(VoIP)systems,peer to peer or integrated withSIP/PBX.Event conditions Audio:audio clip playing,audio detectionDevice status:above operating temperature,above or belowoperating temperature,below operating temperature,IP addressremoved,network lost,new IP address,ring power overcurrentprotection,storage failure,system ready,within operatingtemperature,shock detectionDigital audio:digital signal contains Axis metadata,digital signalhas invalid sample rate,digital signal missing,digital signal OKEdge storage:recording ongoing,storage disruptionI/O:digital input,manual trigger,virtual inputMQTT subscribePTZ:PTZ malfunctioning,PTZ movement,PTZ preset positionreached,PTZ readyScheduled and recurring:scheduled eventVideo:average bitrate degradation,day-night mode,live streamopen,tamperingEvent actions Record video:SD card and network shareMQTT publishUpload of images or video clips:FTP,SFTP,HTTP,HTTPS,networkshare and emailPre-and post-alarm video or image buffering for recording oruploadNotification:email,HTTP,HTTPS,TCP and SNMP trapPTZ:PTZ preset,start/stop guard tourOverlay text,external output activation,play audio clip,zoompreset,day/night mode,make callData streaming Event dataBuilt-ininstallation aidsLeveling guide,pixel counter,license plate capture assistantAnalyticsAXIS ObjectAnalyticsObject classes:humans,vehicles(types:cars,buses,trucks,bikes)Trigger conditions:line crossing,object in area,time in area BETAUp to10scenariosMetadata visualized with trajectories and color-coded boundingboxesPolygon include/exclude areasPerspective configurationONVIF Motion Alarm eventMetadata Object data:Classes:humans,faces,vehicles(types:cars,buses,trucks,bikes),license platesConfidence,positionEvent data:Producer reference,scenarios,trigger conditionsApplications IncludedAXIS Object AnalyticsAXIS Video Motion DetectionSupportedAXIS Audio Spectrum VisualizerSupport for AXIS Camera Application Platform enablinginstallation of third-party applications,see /acapCybersecurityEdge security Software:Signed firmware,brute force delay protection,digestauthentication,password protection,AES-XTS-Plain64256bitSD card encryptionHardware:Secure boot,Axis Edge Vault with Axis device ID,signed video,secure keystore(CC EAL4+,FIPS140-2level2certified hardware protection of cryptographic operations andkeys)Network security IEEE802.1X(EAP-TLS)a,IEEE802.1AR,HTTPS/HSTS a,TLSv1.2/v1.3a,Network Time Security(NTS),X.509Certificate PKI,IP address filteringDocumentation AXIS OS Hardening GuideAxis Vulnerability Management PolicyAxis Security Development ModelAXIS OS Software Bill of Material(SBOM)To download documents,go to /support/cybersecu-rity/resourcesTo read more about Axis cybersecurity support,go to/cybersecurityGeneralCasing Aluminum and plastic casingColor:NCS S9000-NSustainability PVC free,BFR/CFR freePower Power over Ethernet(PoE)IEEE802.3at Type2Class4Typical:12.4W,max14.2W10–28V DC,typical12W,max13.5WWhen PoE Class3is selected:Power over Ethernet IEEE802.3af/802.3at Type1Class3Typical:11.7W,max12.9W10–28V DC,typical10.8W,max12.4WConnectors Shielded RJ4510BASE-T/100BASE-TX/1000BASE-T PoEI/O:6-pin2.5mm terminal block for four configurable inputsRS485/RS422,2pcs,2pos,full duplex,terminal block3.5mm mic/line in,3.5mm line outDC inputHDMI Type D,BNC for SDII2C for AXIS TQ1809–LE HousingSecurity lock slotStorage Support for microSD/microSDHC/microSDXC cardSupport for SD card encryption(AES-XTS-Plain64256bit)Recording to network-attached storage(NAS)For SD card and NAS recommendations see Operating conditions -20°C to50°C(-4°F to122°F) Humidity10–85%RH(non-condensing)Storage conditions -40°C to65°C(-40°F to149°F) Humidity5-95%RH(non-condensing)Approvals EMCEN55035,EN55032Class A,EN61000-3-2,EN61000-3-3,EN61000-6-1,EN61000-6-2,FCC Part15Subpart B Class A,ICES-3(A)/NMB-3(A),KS C9832Class A,KS C9835,RCM AS/NZS CISPR32Class A,VCCI Class ASafetyCAN/CSA C22.2No.62368-1,IEC/EN/UL62368-1,IS13252EnvironmentIEC60068-2-1,IEC60068-2-2,IEC60068-2-6,IEC60068-2-14,IEC60068-2-27,IEC60068-2-78NetworkNIST SP500-267Dimensions Height:66x80x195mm(2.6x3.1x7.7in)Weight650g(1.4lb)IncludedaccessoriesInstallation guide,Windows®decoder1-user license,stand,connector kit,TORX®T20screw driver,RESISTORX®L-key,terminal block connectorOptionalaccessoriesAXIS TQ1809-LE Housing T92G bAXIS T8415Wireless Installation ToolAXIS Surveillance CardsFor more accessories,see VideomanagementsoftwareAXIS Companion,AXIS Camera Station,video managementsoftware from Axis Application Development Partners availableat /vmsLanguages English,German,French,Spanish,Italian,Russian,SimplifiedChinese,Japanese,Korean,Portuguese,Polish,Traditional Chinese Warranty5-year warranty,see /warrantya.This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit.(),and cryptographic software written by Eric Young (*****************).b.The HDMI and SDI outputs are not available when the camera is mounted in the TQ1809-LE Housing.©2021-2023Axis Communications AB.AXIS COMMUNICATIONS,AXIS,ARTPEC and VAPIX are registered trademarks ofAxis AB in various jurisdictions.All other trademarks are the property of their respective owners.We reserve the right tointroduce modifications without notice.T10167715/EN/M13.3/2304。

Legal informationCopyright and License© Copyright 2019 HP Development Company, L.P.Reproduction, adaptation, or translation without prior written permission is prohibited, except as allowedunder the copyright laws.The information contained herein is subject to change without notice.The only warranties for HP products and services are set forth in the express warranty statementsaccompanying such products and services. Nothing herein should be construed as constituting anadditional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.Edition 1, 10/2019Trademark CreditsAdobe®, Adobe Photoshop®, Acrobat®, and PostScript® are trademarks of Adobe Systems Incorporated.Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries.macOS is a trademark of Apple Inc., registered in the U.S. and other countries.AirPrint is a trademark of Apple Inc., registered in the U.S. and other countries.Google™ is a trademark of Google Inc.Microsoft®, Windows®, Windows® XP, and Windows Vista® are U.S. registered trademarks of MicrosoftCorporation.UNIX® is a registered trademark of The Open Group.iiiT able of contents1 Printer overview (1)Warning icons (1)Potential shock hazard (2)Printer views (2)Printer front view (2)Printer back view (4)Interface ports (4)Control-panel view (5)How to use the touchscreen control panel (7)Printer specifications (8)T echnical specifications (8)Supported operating systems (11)Mobile printing solutions (12)Printer dimensions (13)Power consumption, electrical specifications, and acoustic emissions (15)Operating-environment range (15)Printer hardware setup and software installation (16)2 Paper trays (17)Introduction (17)Load paper to Tray 1 (multipurpose tray) (17)Load Tray 1 (multipurpose tray) (18)Tray 1 paper orientation (19)Use alternative letterhead mode (24)Enable Alternative Letterhead Mode by using the printer control-panel menus (24)Load paper to Tray 2 (24)Load Tray 2 (24)Tray 2 paper orientation (26)Use alternative letterhead mode (29)Enable Alternative Letterhead Mode by using the printer control-panel menus (29)Load paper to the 550-sheet paper tray (30)Load paper to the 550-sheet paper tray (30)550-sheet paper tray paper orientation (32)Use alternative letterhead mode (35)Enable Alternative Letterhead Mode by using the printer control-panel menus (35)ivLoad paper to the 2 x 550-sheet paper trays (36)Load paper to the 2 x 550-sheet paper trays (36)2 x 550-sheet paper tray paper orientation (38)Use alternative letterhead mode (41)Enable Alternative Letterhead Mode by using the printer control-panel menus (41)Load paper to the 2,700-sheet high-capacity input paper trays (41)Load paper to the 2,700-sheet high-capacity input paper trays (41)2,700-sheet HCI paper tray paper orientation (43)Use alternative letterhead mode (45)Enable Alternative Letterhead Mode by using the printer control-panel menus (45)Load and print envelopes (46)Print envelopes (46)Envelope orientation (46)Load and print labels (47)Manually feed labels (47)Label orientation (48)3 Supplies, accessories, and parts (49)Order supplies, accessories, and parts (49)Ordering (49)Supplies and accessories (50)Maintenance/long-life consumables (51)Customer self-repair parts (51)Dynamic security (52)Configure the HP toner-cartridge-protection supply settings (53)Introduction (53)Enable or disable the Cartridge Policy feature (53)Use the printer control panel to enable the Cartridge Policy feature (54)Use the printer control panel to disable the Cartridge Policy feature (54)Use the HP Embedded Web Server (EWS) to enable the Cartridge Policy feature (54)Use the HP Embedded Web Server (EWS) to disable the Cartridge Policy feature (55)Troubleshoot Cartridge Policy control panel error messages (55)Enable or disable the Cartridge Protection feature (55)Use the printer control panel to enable the Cartridge Protection feature (56)Use the printer control panel to disable the Cartridge Protection feature (56)Use the HP Embedded Web Server (EWS) to enable the Cartridge Protection feature (56)Use the HP Embedded Web Server (EWS) to disable the Cartridge Protection feature (57)Troubleshoot Cartridge Protection control panel error messages (57)Replace the toner cartridges (58)T oner-cartridge information (58)Remove and replace the cartridges (59)Replace the imaging drums (62)Imaging drum information (62)Remove and replace the imaging drums (63)Replace the toner-collection unit (66)T oner-collection unit information (66)vRemove and replace the toner-collection unit (67)Replace the staple cartridge (M776zs model only) (70)Staple cartridge information (70)Remove and replace the staple cartridge (71)4 Print (73)Print tasks (Windows) (73)How to print (Windows) (73)Automatically print on both sides (Windows) (74)Manually print on both sides (Windows) (74)Print multiple pages per sheet (Windows) (75)Select the paper type (Windows) (75)Additional print tasks (76)Print tasks (macOS) (77)How to print (macOS) (77)Automatically print on both sides (macOS) (77)Manually print on both sides (macOS) (77)Print multiple pages per sheet (macOS) (78)Select the paper type (macOS) (78)Additional print tasks (79)Store print jobs on the printer to print later or print privately (79)Introduction (79)Create a stored job (Windows) (79)Create a stored job (macOS) (80)Print a stored job (81)Delete a stored job (81)Delete a job that is stored on the printer (81)Change the job storage limit (82)Information sent to printer for Job Accounting purposes (82)Mobile printing (82)Introduction (82)Wi-Fi, Wi-Fi Direct Print, NFC, and BLE printing (82)Enable wireless printing (83)Change the Wi-Fi Direct name (83)HP ePrint via email (83)AirPrint (84)Android embedded printing (85)Print from a USB flash drive (85)Enable the USB port for printing (85)Method one: Enable the USB port from the printer control panel (85)Method two: Enable the USB port from the HP Embedded Web Server (network-connectedprinters only) (85)Print USB documents (86)Print using high-speed USB 2.0 port (wired) (86)Method one: Enable the high-speed USB 2.0 port from the printer control panel menus (86)Method two: Enable the high-speed USB 2.0 port from the HP Embedded Web Server (network-connected printers only) (87)vi5 Copy (88)Make a copy (88)Copy on both sides (duplex) (90)Additional copy tasks (92)6 Scan (93)Set up Scan to Email (93)Introduction (93)Before you begin (93)Step one: Access the HP Embedded Web Server (EWS) (94)Step two: Configure the Network Identification settings (95)Step three: Configure the Send to Email feature (96)Method one: Basic configuration using the Email Setup Wizard (96)Method two: Advanced configuration using the Email Setup (100)Step four: Configure the Quick Sets (optional) (104)Step five: Set up Send to Email to use Office 365 Outlook (optional) (105)Introduction (105)Configure the outgoing email server (SMTP) to send an email from an Office 365 Outlookaccount (105)Set up Scan to Network Folder (108)Introduction (108)Before you begin (108)Step one: Access the HP Embedded Web Server (EWS) (108)Step two: Set up Scan to Network Folder (109)Method one: Use the Scan to Network Folder Wizard (109)Method two: Use Scan to Network Folder Setup (110)Step one: Begin the configuration (110)Step two: Configure the Scan to Network Folder settings (111)Step three: Complete the configuration (118)Set up Scan to SharePoint (118)Introduction (118)Before you begin (118)Step one: Access the HP Embedded Web Server (EWS) (118)Step two: Enable Scan to SharePoint and create a Scan to SharePoint Quick Set (119)Scan a file directly to a SharePoint site (121)Quick Set scan settings and options for Scan to SharePoint (122)Set up Scan to USB Drive (123)Introduction (124)Step one: Access the HP Embedded Web Server (EWS) (124)Step two: Enable Scan to USB Drive (124)Step three: Configure the Quick Sets (optional) (125)Default scan settings for Scan to USB Drive setup (126)Default file settings for Save to USB setup (126)Scan to email (127)Introduction (127)Scan to email (127)Scan to job storage (129)viiIntroduction (129)Scan to job storage on the printer (130)Print from job storage on the printer (132)Scan to network folder (132)Introduction (132)Scan to network folder (132)Scan to SharePoint (134)Introduction (134)Scan to SharePoint (134)Scan to USB drive (136)Introduction (136)Scan to USB drive (136)Use HP JetAdvantage business solutions (138)Additional scan tasks (138)7 Fax (140)Set up fax (140)Introduction (140)Set up fax by using the printer control panel (140)Change fax configurations (141)Fax dialing settings (141)General fax send settings (142)Fax receive settings (143)Send a fax (144)Additional fax tasks (146)8 Manage the printer (147)Advanced configuration with the HP Embedded Web Server (EWS) (147)Introduction (147)How to access the HP Embedded Web Server (EWS) (148)HP Embedded Web Server features (149)Information tab (149)General tab (149)Copy/Print tab (150)Scan/Digital Send tab (151)Fax tab (152)Supplies tab (153)Troubleshooting tab (153)Security tab (153)HP Web Services tab (154)Networking tab (154)Other Links list (156)Configure IP network settings (157)Printer sharing disclaimer (157)View or change network settings (157)Rename the printer on a network (157)viiiManually configure IPv4 TCP/IP parameters from the control panel (158)Manually configure IPv6 TCP/IP parameters from the control panel (158)Link speed and duplex settings (159)Printer security features (160)Introduction (160)Security statements (160)Assign an administrator password (160)Use the HP Embedded Web Server (EWS) to set the password (160)Provide user access credentials at the printer control panel (161)IP Security (161)Encryption support: HP High Performance Secure Hard Disks (161)Lock the formatter (161)Energy-conservation settings (161)Set the sleep timer and configure the printer to use 1 watt or less of power (161)Set the sleep schedule (162)Set the idle settings (162)HP Web Jetadmin (163)Software and firmware updates (163)9 Solve problems (164)Customer support (164)Control panel help system (165)Reset factory settings (165)Introduction (165)Method one: Reset factory settings from the printer control panel (165)Method two: Reset factory settings from the HP Embedded Web Server (network-connectedprinters only) (166)A “Cartridge is low” or “Cartridge is very low” message displays on the printer control panel (166)Change the “Very Low” settings (166)Change the “Very Low” settings at the control panel (166)For printers with fax capability (167)Order supplies (167)Printer does not pick up paper or misfeeds (167)Introduction (167)The printer does not pick up paper (167)The printer picks up multiple sheets of paper (171)The document feeder jams, skews, or picks up multiple sheets of paper (174)Clear paper jams (174)Introduction (174)Paper jam locations (174)Auto-navigation for clearing paper jams (175)Experiencing frequent or recurring paper jams? (175)Clear paper jams in the document feeder - 31.13.yz (176)Clear paper jams in Tray 1 (13.A1) (177)Clear paper jams in Tray 2 (13.A2) (182)Clear paper jams in the fuser (13.B9, 13.B2, 13.FF) (188)ixClear paper jams in the duplex area (13.D3) (194)Clear paper jams in the 550-sheet trays (13.A3, 13.A4) (199)Clear paper jams in the 2 x 550 paper trays (13.A4, 13.A5) (206)Clear paper jams in the 2,700-sheet high-capacity input paper trays (13.A3, 13.A4, 13.A5, 13.A7) (213)Resolving color print quality problems (220)Introduction (220)Troubleshoot print quality (221)Update the printer firmware (221)Print from a different software program (221)Check the paper-type setting for the print job (221)Check the paper type setting on the printer (221)Check the paper type setting (Windows) (221)Check the paper type setting (macOS) (222)Check toner-cartridge status (222)Step one: Print the Supplies Status Page (222)Step two: Check supplies status (222)Print a cleaning page (222)Visually inspect the toner cartridge or cartridges (223)Check paper and the printing environment (223)Step one: Use paper that meets HP specifications (223)Step two: Check the environment (223)Step three: Set the individual tray alignment (224)Try a different print driver (224)Troubleshoot color quality (225)Calibrate the printer to align the colors (225)Troubleshoot image defects (225)Improve copy image quality (233)Check the scanner glass for dirt and smudges (233)Calibrate the scanner (234)Check the paper settings (235)Check the paper selection options (235)Check the image-adjustment settings (235)Optimize copy quality for text or pictures (236)Edge-to-edge copying (236)Improve scan image quality (236)Check the scanner glass for dirt and smudges (237)Check the resolution settings (238)Check the color settings (238)Check the image-adjustment settings (239)Optimize scan quality for text or pictures (239)Check the output-quality settings (240)Improve fax image quality (240)Check the scanner glass for dirt and smudges (240)Check the send-fax resolution settings (242)Check the image-adjustment settings (242)Optimize fax quality for text or pictures (242)Check the error-correction setting (243)xSend to a different fax machine (243)Check the sender's fax machine (243)Solve wired network problems (244)Introduction (244)Poor physical connection (244)The computer is unable to communicate with the printer (244)The printer is using incorrect link and duplex settings for the network (245)New software programs might be causing compatibility problems (245)The computer or workstation might be set up incorrectly (245)The printer is disabled, or other network settings are incorrect (245)Solve wireless network problems (245)Introduction (245)Wireless connectivity checklist (245)The printer does not print after the wireless configuration completes (246)The printer does not print, and the computer has a third-party firewall installed (246)The wireless connection does not work after moving the wireless router or printer (247)Cannot connect more computers to the wireless printer (247)The wireless printer loses communication when connected to a VPN (247)The network does not appear in the wireless networks list (247)The wireless network is not functioning (247)Reduce interference on a wireless network (248)Solve fax problems (248)Checklist for solving fax problems (248)What type of phone line are you using? (249)Are you using a surge-protection device? (249)Are you using a phone company voice-messaging service or an answering machine? (249)Does your phone line have a call-waiting feature? (249)Check fax accessory status (249)General fax problems (250)The fax failed to send (250)No fax address book button displays (250)Not able to locate the Fax settings in HP Web Jetadmin (250)The header is appended to the top of the page when the overlay option is enabled (251)A mix of names and numbers is in the recipients box (251)A one-page fax prints as two pages (251)A document stops in the document feeder in the middle of faxing (251)The volume for sounds coming from the fax accessory is too high or too low (251)Index (252)xiPrinter overview1Review the location of features on the printer, the physical and technical specifications of the printer,and where to locate setup information.For video assistance, see /videos/LaserJet.The following information is correct at the time of publication. For current information, see /support/colorljM776MFP.For more information:HP's all-inclusive help for the printer includes the following information:●Install and configure●Learn and use●Solve problems●Download software and firmware updates●Join support forums●Find warranty and regulatory informationWarning iconsUse caution if you see a warning icon on your HP printer, as indicated in the icon definitions.●Caution: Electric shock●Caution: Hot surface●Caution: Keep body parts away from moving partsPrinter overview1●Caution: Sharp edge in close proximity●WarningPotential shock hazardReview this important safety information.●Read and understand these safety statements to avoid an electrical shock hazard.●Always follow basic safety precautions when using this product to reduce risk of injury from fire orelectric shock.●Read and understand all instructions in the user guide.●Observe all warnings and instructions marked on the product.●Use only a grounded electrical outlet when connecting the product to a power source. If you do notknow whether the outlet is grounded, check with a qualified electrician.●Do not touch the contacts on any of the sockets on the product. Replace damaged cordsimmediately.●Unplug this product from wall outlets before cleaning.●Do not install or use this product near water or when you are wet.●Install the product securely on a stable surface.●Install the product in a protected location where no one can step on or trip over the power cord.Printer viewsIdentify certain parts of the printer and the control panel.Printer front viewLocate features on the front of the printer.2Chapter 1 Printer overviewPrinter front view3Printer back viewLocate features on the back of the printer.Interface portsLocate the interface ports on the printer formatter. 4Chapter 1 Printer overviewControl-panel viewThe control panel provides access to the printer features and indicates the current status of the printer.NOTE:Tilt the control panel for easier viewing.The Home screen provides access to the printer features and indicates the current status of the printer.screens.NOTE:The features that appear on the Home screen can vary, depending on the printerconfiguration.Control-panel view5Figure 1-1Control-panel view?i 12:42 PM6Chapter 1 Printer overviewHow to use the touchscreen control panelPerform the following actions to use the printer touchscreen control panel.T ouchT ouch an item on the screen to select that item or open that menu. Also, when scrolling T ouch the Settings icon to open the Settings app.How to use the touchscreen control panel 7SwipeT ouch the screen and then move your finger horizontally to scroll the screen sideways.Swipe until the Settings app displays.Printer specificationsDetermine the specifications for your printer model.IMPORTANT:The following specifications are correct at the time of publication, but they are subject to change. For current information, see /support/colorljM776MFP .T echnical specificationsReview the printer technical specifications.Product numbers for each model ●M776dn - #T3U55A ●Flow M776z - #3WT91A ●Flow M776zs - #T3U56APaper handling specificationsPaper handling features Tray 1 (100-sheet capacity)Included Included Included Tray 2 (550-sheet capacity)IncludedIncludedIncluded8Chapter 1 Printer overview550-sheet paper trayOptional Included Not included NOTE:The M776dn models accept one optional550-sheet tray.Optional Included Included2 x 550-sheet paper tray and standNOTE:The M776dn models accept one optional550-sheet tray that may be installed on top of thestand.Optional Not included Not included2,700-sheet high-capacity input (HCI) paper trayand standNOTE:The M776dn models accept one optional550-sheet tray that may be installed on top of theoptional printer stand.Printer standOptional Not included Not included NOTE:The M776dn models accept one optional550-sheet tray that may be installed on top of theoptional printer stand.Inner finisher accessory Not included Not included Included Automatic duplex printing Included IncludedIncludedIncluded Included Included10/100/1000 Ethernet LAN connection with IPv4and IPv6Hi-Speed USB 2.0Included Included IncludedIncluded Included IncludedEasy-access USB port for printing from a USBflash drive or upgrading the firmwareIncluded Included Included Hardware Integration Pocket for connectingaccessory and third-party devicesHP Internal USB Ports Optional Optional OptionalOptional Optional OptionalHP Jetdirect 2900nw Print Server accessory forWi-Fi connectivity and an additional Ethernet portOptional IncludedIncludedHP Jetdirect 3100w accessory for Wi-Fi, BLE, NFC,and proximity badge readingPrints 45 pages per minute (ppm) on Letter-sizepaper and 46 ppm on A4-size paperEasy-access USB printing for printing from a USBIncluded Included Includedflash driveT echnical specifications9Included Included Included Store jobs in the printer memory to print later orprint privatelyScans 100 pages per minute (ppm) on A4 andIncluded Included Included letter-size paper one-sidedIncluded Included Included 200-page document feeder with dual-headscanning for single-pass duplex copying andscanningNot included Included Included HP EveryPage T echnologies including ultrasonicmulti-feed detectionNot included Included Included Embedded optical character recognition (OCR)provides the ability to convert printed pages intotext that can be edited or searched using acomputerIncluded Included Included SMART Label feature provides paper-edgedetection for automatic page croppingIncluded Included Included Automatic page orientation for pages that haveat least 100 characters of textIncluded Automatic tone adjustment sets contrast,Included Includedbrightness, and background removal for eachpageIncluded Included Includedfolders on a networkIncludedSend documents to SharePoint®Included IncludedIncluded Included Included NOTE:Memory reported on the configurationpage will change from 2.5 GB to 3 GB with theoptional 1 GB SODIMM installed.Mass storage: 500 GB hard disk drive Included Included IncludedSecurity: HP Trusted Platform Module (TPM)Included Included IncludedT ouchscreen control panel Included Included IncludedRetractable keyboard Not included Included Included 10Chapter 1 Printer overviewFax Optional Included IncludedSupported operating systemsUse the following information to ensure printer compatibility with your computer operating system.Linux: For information and print drivers for Linux, go to /go/linuxprinting.UNIX: For information and print drivers for UNIX®, go to /go/unixmodelscripts.The following information applies to the printer-specific Windows HP PCL 6 print drivers, HP print driversfor macOS, and to the software installer.Windows: Download HP Easy Start from /LaserJet to install the HP print driver. Or, go tothe printer-support website for this printer: /support/colorljM776MFP to download the printdriver or the software installer to install the HP print driver.macOS: Mac computers are supported with this printer. Download HP Easy Start either from /LaserJet or from the Printer Support page, and then use HP Easy Start to install the HP print driver.1.Go to /LaserJet.2.Follow the steps provided to download the printer software.Windows 7, 32-bit and 64-bit The “HP PCL 6” printer-specific print driver is installed for this operating system aspart of the software installation.Windows 8.1, 32-bit and 64-bit The “HP PCL-6” V4 printer-specific print driver is installed for this operating systemas part of the software installation.Windows 10, 32-bit and 64-bit The “HP PCL-6” V4 printer-specific print driver is installed for this operating systemas part of the software installation.Windows Server 2008 R2, SP 1, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2012, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2012 R2, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2016, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2019, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Supported operating systems11macOS 10.13 High Sierra, macOS 10.14 MojaveDownload HP Easy Start from /LaserJet , and then use it to install the print driver.NOTE:Supported operating systems can change.NOTE:For a current list of supported operating systems and HP’s all-inclusive help for the printer, go to /support/colorljM776MFP .NOTE:For details on client and server operating systems and for HP UPD driver support for this printer, go to /go/upd . Under Additional information , click Specifications .●Internet connection●Dedicated USB 1.1 or 2.0 connection or a network connection● 2 GB of available hard-disk space ●1 GB RAM (32-bit) or2 GB RAM (64-bit)●Internet connection●Dedicated USB 1.1 or 2.0 connection or a network connection●1.5 GB of available hard-disk spaceNOTE:The Windows software installer installs the HP Smart Device Agent Base service. The file size is less than 100 kb. Its only function is to check for printers connected via USB hourly. No data is collected. If a USB printer is found, it then tries to locate a JetAdvantage Management Connector (JAMc) instance on the network. If a JAMc is found, the HP Smart Device Agent Base is securelyupgraded to a full Smart Device Agent from JAMc, which will then allow printed pages to be accounted for in a Managed Print Services (MPS) account. The driver-only web packs downloaded from for the printer and installed through the Add Printer wizard do not install this service.T o uninstall the service, open the Control Panel , select Programs or Programs and Features , and then select Add/Remove Programs or Uninstall a Programto remove the service. The file name isHPSmartDeviceAgentBase.Mobile printing solutionsHP offers multiple mobile printing solutions to enable easy printing to an HP printer from a laptop, tablet, smartphone, or other mobile device.T o see the full list and to determine the best choice, go to /go/MobilePrinting .NOTE:Update the printer firmware to ensure all mobile printing capabilities are supported.●Wi-Fi Direct (wireless models only, with HP Jetdirect 3100w BLE/NFC/Wireless accessory installed)●HP ePrint via email (Requires HP Web Services to be enabled and the printer to be registered with HP Connected)●HP Smart app ●Google Cloud Print12Chapter 1 Printer overview。

IntroductionTN-5524-8PoE SeriesThe ToughNet TN-5500 series M12 PoE managed Ethernet switches are designed for railway applications, such as rolling stock, and wayside installations. The TN series switches use M12 and othercircular connectors to ensure tight, robust connections, and guarantee reliable operation against environmental disturbances, such as vibration and shock. The TN-5524-8PoE series Ethernet switches provide 24 Fast Ethernet M12 ports with 8 IEEE 802.3af compliant PoE (Power-over-Ethernet) ports. The PoE switches are classified as power source equipment (PSE) and provide up to 15.4 watts of powerper port, and can be used to power IEEE 802.3af compliant powered devices (PDs) (such as surveillance cameras, wireless access points, and IP phones). Models with an extended operating temperature range of -40 to 75°C are also available. The TN-5500-PoE seriesEthernet switches are compliant with mandatory sections of EN 50155, covering operating temperature, power input voltage, surge, ESD, and vibration, as well as conformal coating and power insulation, making the switches suitable for a variety of industrial applications.• Advanced PoE management function• IPv6 Ready logo awarded (IPv6 Logo Committee certified)• Leading EN50155-compliant PoE switches for rolling stock applications• DHCP Option 82 for IP address assignment with different policies • EtherNet/IP and Modbus/TCP industrial Ethernet protocol supported• Turbo Ring and Turbo Chain (recovery time < 20 ms @ 250 switches), RSTP/STP , and MSTP for network redundancy • IGMP snooping and GMRP for filtering multicast traffic• Port-based VLAN, IEEE 802.1Q VLAN, and GVRP to ease network planning• QoS (IEEE 802.1p/1Q and TOS/DiffServ) to increase determinism • IEEE 802.3ad, LACP for optimum bandwidth utilization• TACACS+, SNMPv3, IEEE 802.1X, HTTPS, and SSH to enhance network security• SNMPv1/v2c/v3 for different levels of network management • RMON for efficient network monitoring and proactive capability • Bandwidth management prevents unpredictable network status • Lock port allows access by only authorized MAC addresses • Port mirroring for online debugging• Automatic warning by exception through email, relay output • Line-swap fast recovery• Automatic recovery of connected device’s IP addresses•LLDP for automatic topology discovery in network management software• Configurable by web browser, Telnet/serial console, CLI, and Windows utility• Panel mounting installation capabilityTechnologyStandards:IEEE 802.3af for Power-over-Ethernet IEEE 802.3 for 10BaseTIEEE 802.3u for 100BaseT(X) IEEE 802.3x for Flow ControlIEEE 802.1D-2004 for Spanning Tree Protocol IEEE 802.1w for Rapid STPIEEE 802.1s for Multiple Spanning Tree Protocol IEEE 802.1Q for VLAN Tagging IEEE 802.1p for Class of Service IEEE 802.1X for AuthenticationIEEE 802.3ad for Port Trunk with LACPSoftware FeaturesManagement: IPv4/IPv6, SNMP v1/v2c/v3, Telnet, LLDP, Port Mirror, Syslog, RMON, BootP, DHCP Server/Client, DHCP Option 66/67/82, TFTP, SMTP, RARP, HTTP, HTTPS, SNMP inform, Flow Control, Back pressure flow controlFilter: 802.1Q VLAN, Port-Based VLAN, GVRP, IGMPv1/v2, GMRP, Static MulticastRedundancy Protocols: STP/RSTP, MSTP, Turbo Ring v1/v2, Turbo Chain, Link AggregationSecurity: RADIUS, TACACS+, SSL, SSH, Port Lock, Broadcast Storm Protection, Rate LimitTime Management: SNTP, NTP Server/Client, IEEE 1588v2 PTP (software-based)Industrial Protocols: EtherNet/IP, Modbus/TCPMIB: MIB-II, Ethernet-like MIB, P-BRIDGE MIB, Q-BRIDGE MIB, Bridge MIB, RSTP MIB, RMON MIB Group 1, 2, 3, 9Switch PropertiesPriority Queues: 4Max. Number of VLANs: 64VLAN ID Range: VID 1 to 4094IGMP Groups: 256InterfaceFast Ethernet: Front cabling, M12 D-coded 4-pin female connector, 10/100BaseT(X) auto negotiation speed, F/H duplex mode, and auto MDI/MDI-X connectionConsole Port: M12 A-coded 5-pin male connectorAlarm Contact: 2 relay outputs in one M12 A-coded 5-pin male connector with current carrying capacity of 3 A @ 30 VDCPower RequirementsInput Voltage: 24 VDCOperating Voltage: 16.8 to 30 VDC Input Current: 8.4 (max.) @ 24 VDC Overload Current Protection: Present Connection: M23 connectorReverse Polarity Protection: PresentPhysical CharacteristicsHousing: MetalIP Rating: IP40 protection (optional protective caps available for unused ports)Dimensions: 390 x 132 x 122.3 mm (15.35 x 5.20 x 4.81 in)Weight: 3,506 g (7.73 lb)Installation: Panel-mounting kitEnvironmental LimitsOperating Temperature: -40 to 75°C (-40 to 167°F)Storage Temperature: -40 to 85°C (-40 to 185°F)Ambient Relative Humidity: 5 to 95% (non-condensing)Altitude: 2000 mPlease contact Moxa if you require products guaranteed to function at higher altitudesStandards and CertificationsSafety: UL/cUL 508EMI: FCC Part 15 Subpart B Class A, EN 55032 Class A EMS:IEC 61000-4-2 ESD: Contact: 6 kV; Air: 8 kV IEC 61000-4-3 RS: 80 MHz to 1 GHz: 20 V/m IEC 61000-4-4 EFT: Power: 2 kV; Signal: 2 kV IEC 61000-4-5 Surge: Power: 2 kV; Signal: 2 kV IEC 61000-4-6 CS: 10 V IEC 61000-4-8Rail Traffic: (for panel-mounting installations) EN 50155*, EN 50121-4, EN 45545-2*This product is suitable for rolling stock railway applications, as defined by the EN 50155 standard. For a more detailed statement, click here: /doc/specs/EN_50155_Compliance.pdfShock: EN 50155, IEC 61373Freefall: IEC 60068-2-32Vibration: EN 50155, IEC 61373Note: Please check Moxa’s website for the most up-to-date certification status.MTBF (mean time between failures)Time: 663,533 hrsStandard: Telcordia SR332WarrantyWarranty Period: 5 yearsDetails: See /warrantyOrdering InformationOptional Accessories (can be purchased separately)Power Cords, M12 Connectors, Protective Caps: See the EN 50155 Switch Accessories datasheet for detailsMXview: Moxa industrial network management software with 50, 100, 250, 500, 1000, or 2000 nodesEDS-SNMP OPC Server Pro: OPC server software that works with all SNMP devicesABC-01-M12: Configuration backup and restoration tool for TN series managed Ethernet switches, 0 to 60°C operating temperatureM12 ConnectorsM12/M23 CordsEN 50155 Switch AccessoriesCBL-M12D(MM4P)/RJ45-100 IP671-meter M12-to-RJ45 Cat-5C UTP Ethernet cable with IP67-rated 4-pin male D-coded M12 connectorM12D-4P-IP68Field-installable M12 D-coded screw-in sensor connector, 4-pin male, IP68-ratedM12X-8PMM-IP67-HTGField-installable M12 X-coded crimp type, slim design connector, 8-pin male, IP67-ratedCBL-M23(FF6P)/Open-BK-100 IP671-meter M23-to-6-pin power cable with IP67-rated 6-pin female M23 connectorCBL-M12XMM8P-Y-300-IP673-meter M12-to-M12 Cat-5 UTP Ethernet cable withIP67-rated 8-pin male X-coded crimp type M12 connectorCBL-M12XMM8PRJ45-Y-200-IP672-meter M12-to-RJ45 Cat-5 UTP Ethernet cable with IP67-rated 8-pin male X-coded crimp type M12 connectorCBL-M12XMM8P-Y-100-IP671-meter M12-to-M12 Cat-5 UTP Ethernet cable withIP67-rated 8-pin male X-coded crimp type M12 connectorCBL-M12(FF5P)/OPEN-100 IP671-meter M12-to-5-pin power cable with IP67-rated 5-pin female A-coded M12 connectorM12A-5P-IP68Field-installable M12 A-coded screw-in sensor connector, 5-pin female, IP68-ratedM12 IP67 Protective CapsM23 ConnectorsA-CAP-M12F-MMetal cap for M12 female connectorA-PLG-WPM23-01M23 cable connector, 6-pin female, crimp typeA-CAP-M12M-MMetal cap for M12 male connector。

syntcp 用法syntcp 是一个网络工具,用于在计算机网络中进行 TCP 连接的测试和诊断。
它可用于验证 TCP/IP 网络配置、检测网络延迟和丢包、以及分析网络连接的性能。
下面是使用 syntcp 的一些基本用法。
1. 安装 syntcp 工具。
你可以在官方网站或第三方软件仓库中找到适用于你的操作系统的 syntcp 版本,并按照指示进行安装。
2. 启动 syntcp。
一旦安装完成,你可以打开终端或命令提示符窗口,并输入"syntcp" 命令来启动 syntcp 工具。
3. 创建 TCP 连接。
使用 "syntcp" 命令加上目标服务器的 IP 地址和端口号来创建一个 TCP 连接。
例如,"syntcp 192.168.0.1 80" 将尝试连接到 IP 地址为192.168.0.1、端口号为 80 的服务器。
4. 检测网络延迟和丢包。
在建立连接后,syntcp 将会显示连接的详细信息,包括连接时间、往返时间(RTT)和丢包率等。
这些指标可以帮助你评估网络的性能和稳定性。
5. 分析连接性能。
通过监控 syntcp 的输出,你可以获得连接的吞吐量、带宽和错误率等信息。
这些数据有助于诊断网络连接中的问题和瓶颈,并进行性能优化。
6. 退出 syntcp。
当你完成测试或诊断后,可以按下 Ctrl + C 组合键来退出syntcp 工具。
总之,syntcp 是一个强大的工具,可用于 TCP 连接的测试和分析。
通过了解syntcp 的用法,你可以更好地评估和优化计算机网络的性能。
记得在使用 syntcp 进行测试时,尽量选择合适的环境,避免对生产环境造成不必要的干扰。




无线环境TCP优化及评估测试1新技术介绍1.1 研究背景和目的TCP协议:Transmission Control Protocol 传输控制协议TCP是一种面向连接(连接导向)的、可靠的、基于字节流的传输层(Transport layer)通信协议,由IETF的RFC 793说明(specified)。
在简化的计算机网络OS或者TCP/IPI模型中,它都完成传输层所指定的功能,它负责对应用层提供服务。
TCP应用运行模型如下:图一、OSI和TCP/IP模型的传输层在3G的数据传输网络中主要也是采用中TCP协议来完成数据业务的传输。
目前3G无线网络数据处理的机制:NO_DISCARD,最大程度重传,RLC按序发送数据,TCP协议是基于有线网络的协议,其并未考虑现有无线特性。
这些机制最终导致与上层TCP超时降低拥塞窗口的机制存在一定的矛盾,很多的情况下,无线侧为了不丢弃数据,无节制的重传最终反而导致TCP的超时。
为了解决TCP传输协议在3G无线网络中运用的出现的无线重传超时和TCP抖动问题特做此课题来进行研究如何是TCP协议搞好的在3G无线传输网络中使用。
1.2 实现原理算法功能首先我们来介绍TCP协议:它提供可靠的连接服务,采用三次握手建立一个连接第一次握手:建立连接时,客户端发送syn包(syn=j)到服务器,并进入SYN_SEND状态,等待服务器确认;SYN:同步序列编号(Synchronize Sequence Numbers)。
第二次握手:服务器收到syn包,必须确认客户的SYN(ack=j+1),同时自己也发送一个SYN包(syn=k),即SYN+ACK包,此时服务器进入SYN_RECV状态;第三次握手:客户端收到服务器的SYN+ACK包,向服务器发送确认包ACK(ack=k+1),此包发送完毕,客户端和服务器进入ESTABLISHED状态,完成三次握手,客户端与服务器开始传送数据。
图二、TCP传输数据报文每个数据报文使用TCP协议传输都要经过上图的传输过程。

中国移动通信企业标准QB-╳╳-╳╳╳-╳╳中国移动统一DPI设备技术规范T e c h n i c a l S p e c i f i c a t i o n o f D e e p P a c k e tI n s p e c t i o n E q u i p m e n t f o r C M C C版本号:1.0╳╳╳╳-╳╳-╳╳发布╳╳╳╳-╳╳-╳╳实施中国移动通信集团公司发布目录前言 (IV)1范围 (1)2规范性引用文件 (1)3术语、定义和缩略语 (2)3.1定义和术语 (2)3.2缩写 (2)4设备概述 (2)4.1统一DPI定义 (2)4.2适用场景 (3)4.2.1场景一:PS侧 (3)4.2.2场景二:IDC出口 (3)4.2.3场景三:省网出口 (3)4.2.4场景四:省网网间出口 (3)4.2.5场景五:骨干网网间出口 (3)4.3复用方式 (3)4.3.1方式一:分光复用(可选) (3)4.3.2方式二:原始报文镜像复用 (3)4.3.3方式三:会话级数据复用 (3)4.3.4方式四:统计级数据复用 (3)5设备结构 (4)5.1设备结构图 (4)5.2模块功能描述 (4)5.3接口描述 (4)6设备功能要求 (5)6.1识别功能 (5)6.2分析统计功能 (6)6.2.1流量流向及业务占比分析统计 (6)6.2.2网站分析统计 (6)6.3控制功能 (6)6.3.1串接模式下的控制功能 (6)6.3.2并接模式下的控制功能(可选) (7)6.4复用功能 (7)6.4.1分光复用(可选) (7)6.4.2原始报文镜像复用 (7)6.4.3会话级数据复用 (8)6.4.4统计级数据复用 (8)6.5安全功能 (8)6.5.1DDoS攻击监控 (8)6.5.2文本/图片还原 (8)6.5.3软件还原(仅对PS侧场景要求) (8)6.6回填功能 (8)6.7非对称流量归并功能 (9)6.8数据回放功能 (9)6.9原始数据留存功能(仅对PS侧场景要求) (9)6.10用户在线状态查询功能(仅对PS侧场景要求) (9)6.11上报告警功能要求(仅对PS侧场景要求) (9)7接口物理要求 (9)7.1线路接口 (9)7.2复用、配置接口 (10)8接口格式要求 (10)8.1镜像接口 (10)8.2会话数据接口 (10)8.2.1文件接口 (10)8.2.2实时接口(仅对PS侧场景要求) (11)8.2.3数据要求 (12)8.3统计数据接口 (23)8.3.1接口概要 (23)8.3.2通信流程 (24)8.3.3统计指标集 (24)8.4配置接口 (27)8.4.1接口概要 (27)8.4.2消息格式 (28)9设备性能要求 (43)9.1流量识别和控制指标 (43)9.2转发性能指标(仅对串接设备要求) (43)9.3复用性能要求 (44)9.4节能要求 (44)10时间同步要求 (44)11可靠性要求 (44)12网管要求 (45)12.1配置管理 (45)12.2查询设备信息 (46)12.2.1设备硬件信息 (46)12.2.2设备网络信息 (46)12.3查询设备状态 (47)12.3.1设备负荷 (47)12.4设备状态管理 (48)12.4.1故障管理 (48)12.5性能管理 (48)12.6安全管理 (48)13操作维护要求 (49)13.1可管理性 (49)13.2可维护性 (49)13.3易用性 (49)14附录 (50)14.1附录A状态编码 (50)14.2附录B消息类型定义 (50)14.3附录C策略回应错误类型 (51)14.4附录D XDR类型编码 (51)14.5附录E统计报表类型编码 (51)14.6附录F浏览工具 (51)14.7附录G门户应用集合 (52)14.8附录H E MAIL事务类型编码 (52)15编制历史 (54)前言本规范对中国移动网内使用的深度包检测(DPI)设备的功能和性能提出要求,是部署统一DPI设备需要遵从的技术文件。

低开销的无线网络编码机会路由协议设计吴强;范建华;阚宝强;卢紫毅【摘要】Aiming at the problem of sending redundant in opportunistic routing protocols based on wireless Mesh network coding, this paper proposes a wireless Mesh network coding opportunistic routing protocol based on dynamic redundancy control, and the transmitting process of this class of protocols is modeled and analyzed by linear space theory. It uses null space acknowledgement to evaluate the amount of update information, and dynamically adjusts node sending redundancy according to total update information. In addition, a forwarding priority scheduling mechanism is introduced to avoid duplicate transmissions of the same linear space from different forwarding nodes. Simulation experimental results show that the protocol improves 30%~100% network throughout and 20%~45% normalized transmission cost compared with MORE protocol.%针对基于无线 Mesh 网络编码的机会路由协议的节点转发冗余问题,从线性空间的角度对该类协议的信息传输过程进行建模与分析,提出一种基于动态冗余控制的无线 Mesh 网络编码机会路由协议。

目录第1章 QoS简介.....................................................................................................................1-11.1 简介....................................................................................................................................1-11.2 传统的分组投递业务..........................................................................................................1-11.3 新业务引发的新需求..........................................................................................................1-21.4 拥塞的产生、影响和对策...................................................................................................1-21.4.1 拥塞的产生..............................................................................................................1-21.4.2 拥塞的影响..............................................................................................................1-31.4.3 对策.........................................................................................................................1-31.5 几种主要的流量管理技术...................................................................................................1-4第2章流量监管和流量整形配置............................................................................................2-12.1 简介....................................................................................................................................2-12.1.1 流量监管..................................................................................................................2-12.1.2 流量整形..................................................................................................................2-32.1.3 接口限速..................................................................................................................2-52.2 配置流量监管.....................................................................................................................2-62.2.1 建立配置任务...........................................................................................................2-62.2.2 配置流量监管列表....................................................................................................2-72.2.3 配置流量监管策略....................................................................................................2-72.2.4 检查配置结果...........................................................................................................2-72.3 配置流量整形.....................................................................................................................2-82.3.1 建立配置任务...........................................................................................................2-82.3.2 配置流量整形...........................................................................................................2-82.3.3 检查配置结果...........................................................................................................2-92.4 配置接口限速.....................................................................................................................2-92.4.1 建立配置任务...........................................................................................................2-92.4.2 配置接口限速.........................................................................................................2-102.4.3 检查配置结果.........................................................................................................2-102.5 配置举例...........................................................................................................................2-102.5.1 流量监管配置示例..................................................................................................2-102.5.2 流量整形配置示例..................................................................................................2-12第3章拥塞管理配置..............................................................................................................3-13.1 简介....................................................................................................................................3-13.1.1 拥塞管理策略...........................................................................................................3-13.1.2 拥塞管理技术的对比................................................................................................3-53.2 配置先进先出队列..............................................................................................................3-63.2.1 建立配置任务...........................................................................................................3-63.2.2 配置FIFO队列的长度.............................................................................................3-73.3 配置优先队列.....................................................................................................................3-73.3.1 建立配置任务...........................................................................................................3-73.3.2 配置优先列表...........................................................................................................3-83.3.3 配置缺省队列...........................................................................................................3-93.3.4 配置队列长度...........................................................................................................3-93.3.5 在接口上应用优先列表组.........................................................................................3-93.3.6 检查配置结果.........................................................................................................3-103.4 配置定制队列...................................................................................................................3-103.4.1 建立配置任务.........................................................................................................3-103.4.2 配置定制列表.........................................................................................................3-113.4.3 配置缺省队列.........................................................................................................3-113.4.4 配置队列长度.........................................................................................................3-123.4.5 配置各队列每次轮询发送的字节数........................................................................3-123.4.6 在接口上应用定制列表..........................................................................................3-123.4.7 检查配置结果.........................................................................................................3-133.5 配置加权公平队列............................................................................................................3-133.5.1 建立配置任务.........................................................................................................3-133.5.2 配置加权公平队列..................................................................................................3-143.5.3 检查配置结果.........................................................................................................3-143.6 配置RTP队列..................................................................................................................3-143.6.1 建立配置任务.........................................................................................................3-143.6.2 在接口上应用RTP队列.........................................................................................3-153.6.3 配置最大预留带宽..................................................................................................3-163.6.4 检查配置结果.........................................................................................................3-163.7 优先队列配置举例............................................................................................................3-16第4章拥塞避免配置..............................................................................................................4-14.1 简介....................................................................................................................................4-14.2 配置WRED........................................................................................................................4-34.2.1 建立配置任务...........................................................................................................4-34.2.2 启用WRED............................................................................................................4-44.2.3 配置WRED计算平均队长的指数............................................................................4-44.2.4 配置WRED各优先级参数.......................................................................................4-44.2.5 检查配置结果...........................................................................................................4-5第5章基于类的QoS配置.....................................................................................................5-15.1 简介....................................................................................................................................5-15.1.1 流分类......................................................................................................................5-25.1.2 标记.........................................................................................................................5-25.1.3 DSCP......................................................................................................................5-35.1.4 标准的PHB.............................................................................................................5-35.1.5 基于类的队列CBQ(Class Based Queue)..........................................................5-4 5.2 配置流分类.........................................................................................................................5-45.2.1 建立配置任务...........................................................................................................5-45.2.2 在类视图中定义匹配类的规则.................................................................................5-55.2.3 检查配置结果...........................................................................................................5-6 5.3 配置基于类的标记动作.......................................................................................................5-75.3.1 建立配置任务...........................................................................................................5-75.3.2 配置标记报文的DSCP值........................................................................................5-85.3.3 配置标记报文的IP优先级值...................................................................................5-85.3.4 配置标记FR报文的DE标志位的值........................................................................5-85.3.5 配置标记ATM信元的CLP标志位的值...................................................................5-85.3.6 配置标记MPLS EXP域的值...................................................................................5-95.3.7 配置标记VLAN优先级8021P的值.........................................................................5-9 5.4 配置基于类的流量监管和流量整形动作.............................................................................5-95.4.1 建立配置任务...........................................................................................................5-95.4.2 配置基于类的流量监管动作...................................................................................5-105.4.3 配置基于类的流量整形动作...................................................................................5-105.4.4 检查配置结果.........................................................................................................5-11 5.5 配置基于类的流量限速动作..............................................................................................5-115.5.1 建立配置任务.........................................................................................................5-115.5.2 配置基于类的流量限速动作...................................................................................5-125.5.3 检查配置结果.........................................................................................................5-12 5.6 配置CBQ动作.................................................................................................................5-125.6.1 建立配置任务.........................................................................................................5-125.6.2 配置AF..................................................................................................................5-135.6.3 配置WFQ..............................................................................................................5-135.6.4 配置最大队列长度..................................................................................................5-145.6.5 配置EF.................................................................................................................5-145.6.6 检查配置结果.........................................................................................................5-14 5.7 配置基于类的WRED动作...............................................................................................5-155.7.1 建立配置任务.........................................................................................................5-155.7.2 配置基于类的WRED丢弃方式.............................................................................5-155.7.3 配置基于类的WRED的丢弃参数.........................................................................5-165.7.4 检查配置结果.........................................................................................................5-16 5.8 配置流量策略...................................................................................................................5-175.8.1 建立配置任务.........................................................................................................5-175.8.2 定义策略并进入策略视图.......................................................................................5-175.8.3 为流分类指定流动作..............................................................................................5-185.8.4 检查配置结果.........................................................................................................5-185.9 配置策略嵌套动作............................................................................................................5-185.9.1 建立配置任务.........................................................................................................5-185.9.2 配置策略嵌套动作.................................................................................................5-195.9.3 检查配置结果.........................................................................................................5-205.10 应用策略.........................................................................................................................5-205.10.1 建立配置任务.......................................................................................................5-205.10.2 应用策略..............................................................................................................5-215.10.3 检查配置结果.......................................................................................................5-215.11 调试CBQ.......................................................................................................................5-215.12 配置举例.........................................................................................................................5-225.12.1 基于类的队列配置举例........................................................................................5-225.12.2 策略嵌套配置举例...............................................................................................5-26第6章 QPPB配置..................................................................................................................6-16.1 简介....................................................................................................................................6-16.2 配置QPPB.........................................................................................................................6-26.2.1 建立配置任务...........................................................................................................6-26.2.2 配置路由策略...........................................................................................................6-36.2.3 应用路由策略...........................................................................................................6-46.2.4 定义类及类的匹配规则............................................................................................6-46.2.5 配置基于类的动作....................................................................................................6-46.2.6 定义流量策略...........................................................................................................6-46.2.7 在接口下应用流量策略............................................................................................6-46.2.8 在接口下应用QPPB................................................................................................6-56.2.9 检查配置结果...........................................................................................................6-56.3 QPPB配置举例..................................................................................................................6-56.4 故障排除...........................................................................................................................6-11第7章链路效率机制配置.......................................................................................................7-17.1 简介....................................................................................................................................7-17.1.1 IP报文头压缩..........................................................................................................7-17.1.2 链路分片与交叉.......................................................................................................7-27.2 配置IP报文头压缩.............................................................................................................7-37.2.1 建立配置任务...........................................................................................................7-37.2.2 启动IP头压缩........................................................................................................7-47.2.3 配置TCP头压缩的最大连接数................................................................................7-47.2.4 配置RTP头压缩的最大连接数................................................................................7-57.2.5 检查配置结果...........................................................................................................7-57.3 配置链路分片和交叉..........................................................................................................7-57.3.1 建立配置任务...........................................................................................................7-57.3.2 使能LFI..................................................................................................................7-67.3.3 配置LFI分片的最大时延........................................................................................7-67.3.4 配置MP绑定带宽....................................................................................................7-67.3.5 启动VT接口动态QoS的限速功能.........................................................................7-77.4 维护....................................................................................................................................7-77.4.1 调试IP头压缩.........................................................................................................7-77.4.2 清空压缩运行信息....................................................................................................7-8第8章帧中继QoS配置.........................................................................................................8-18.1 简介....................................................................................................................................8-18.1.1 帧中继class............................................................................................................8-28.1.2 实现的帧中继QoS...................................................................................................8-28.2 配置帧中继流量整形..........................................................................................................8-58.2.1 建立配置任务...........................................................................................................8-58.2.2 配置帧中继流量整形参数.........................................................................................8-68.2.3 将整形参数应用到接口............................................................................................8-78.2.4 使能帧中继流量整形................................................................................................8-78.3 配置帧中继流量监管..........................................................................................................8-88.3.1 建立配置任务...........................................................................................................8-88.3.2 配置帧中继流量监管参数.........................................................................................8-98.3.3 将流量监管参数应用到接口.....................................................................................8-98.3.4 使能帧中继流量监管................................................................................................8-98.4 配置帧中继接口的拥塞管理..............................................................................................8-108.4.1 建立配置任务.........................................................................................................8-108.4.2 配置帧中继接口的拥塞管理策略............................................................................8-108.5 配置帧中继虚电路的拥塞管理..........................................................................................8-118.5.1 建立配置任务.........................................................................................................8-118.5.2 配置帧中继虚电路的拥塞管理策略........................................................................8-128.5.3 配置虚电路的DE规则...........................................................................................8-128.5.4 将拥塞策略应用到虚电路.......................................................................................8-138.6 配置帧中继通用队列........................................................................................................8-138.6.1 建立配置任务.........................................................................................................8-138.6.2 配置帧中继通用队列..............................................................................................8-148.6.3 将通用队列应用到帧中继接口...............................................................................8-158.6.4 将通用队列应用到帧中继虚电路............................................................................8-158.6.5 检查配置结果.........................................................................................................8-158.7 配置帧中继PVC PQ队列................................................................................................8-168.7.1 建立配置任务.........................................................................................................8-168.7.2 配置帧中继接口的PVC PQ队列...........................................................................8-168.7.3 配置帧中继虚电路PVC PQ队列等级....................................................................8-178.8 配置帧中继分片................................................................................................................8-188.8.1 建立配置任务.........................................................................................................8-188.8.2 配置帧中继分片.....................................................................................................8-198.8.3 将帧中继分片应用到虚电路...................................................................................8-198.8.4 检查配置结果.........................................................................................................8-198.9 调试帧中继QoS...............................................................................................................8-208.10 配置举例.........................................................................................................................8-208.10.1 帧中继流量整形配置举例.....................................................................................8-208.10.2 帧中继分片配置举例............................................................................................8-22第9章 ATM QoS配置............................................................................................................9-19.1 简介....................................................................................................................................9-19.2 配置ATM PVC的拥塞管理................................................................................................9-29.2.1 建立配置任务...........................................................................................................9-29.2.2 配置ATM PVC的FIFO队列...................................................................................9-39.2.3 配置ATM PVC的CQ队列.....................................................................................9-49.2.4 配置ATM PVC的PQ队列......................................................................................9-49.2.5 配置ATM PVC的WFQ队列..................................................................................9-49.2.6 应用CBQ................................................................................................................9-49.2.7 配置ATM PVC的RTPQ队列.................................................................................9-59.2.8 配置ATM PVC的预留带宽.....................................................................................9-59.3 配置ATM PVC的拥塞避免................................................................................................9-59.3.1 建立配置任务...........................................................................................................9-59.3.2 配置ATM PVC的拥塞避免.....................................................................................9-69.4 配置ATM接口的流量监管.................................................................................................9-79.4.1 建立配置任务...........................................................................................................9-79.4.2 配置ATM接口的流量监管.......................................................................................9-79.5 配置ATM接口基于类的策略..............................................................................................9-89.5.1 建立配置任务...........................................................................................................9-89.5.2 配置ATM接口基于类的策略...................................................................................9-99.6 配置PVC业务映射............................................................................................................9-99.6.1 建立配置任务...........................................................................................................9-99.6.2 配置PVC-Group内PVC的IP优先级..................................................................9-109.6.3 为PVC-Group内创建的PVC配置流量参数.........................................................9-109.7 Multilink PPPoA QoS配置...............................................................................................9-119.7.1 建立配置任务.........................................................................................................9-119.7.2 创建Multilink PPPoA虚拟接口模板......................................................................9-129.7.3 创建PPPoA虚拟接口模板并绑定到Multilink PPPoA...........................................9-129.7.4 配置PPPoA应用...................................................................................................9-129.7.5 在Multilink PPPoA虚拟接口模板上应用QoS策略...............................................9-129.7.6 重启PVC...............................................................................................................9-139.8 配置举例...........................................................................................................................9-139.8.1 ATM PVC上的CBQ配置举例..............................................................................9-13。

问题描述:某局点反馈:部分iNode客户端无法打开EMO远程应用;定位思路:因为是部分iNode客户端无法打开远程应用(首先排除网络、用户权限问题),所以首先确认这部分无法使用的iNode客户端有某些共性,比如都是iOS系统,然后检查相关配置是否正确;重点检查:1:如果是iOS系统不能打开,安卓系统没有问题,这个很有可能是因为在VPN网关上配置的vAPP Server名称不符合规范,EMO要求:如果是v3 VPN网关,则Vapp Server的名称必须为“iES_IP:PORT”格式,EMO服务器侧同步保持一致,见下面截图配置2:如果是PC可以使用,手机iNode打不开则重点检查下面的勾是否去掉附:iNode EMO 远程应用配置指导(SSL VPN 方式)1.1 ssl vpn 接入方式iMC EMO 远程办公配置指导1.1.1 一.引入iMC EMO 移动办公管理组件定位于移动用户远程办公,使员工的办公模式摆脱了空间及时间的限制。
借助于iMC EMO 功能组件,员工可随时随地通过3G 或wifi 等公网网络接入VPN 网关,并通过SSL VPN 网关进行radius 认证,认证通过后就可以访问EMO 侧定义的网络资源,如lync 、notes 和IE 等,同时整个交互过程受RDP 协议保护,安全性也得到了保证,本文描述如何在SSL VPN 环境下进行EMO 配置。
1.1.2 二.组网图组网及流程说明:外网用户想要访问内网资源时,需要打开inode 客户端软件并选择SSL VPN 接入,然后通过3G 或者WIFI 环境接入位于公网的SSL VPN 网关并在认证信息输入框输入自己的账号信息,SSL VPN 网关将认证信息转发给iMC,iMC 完成用户认证后根据EMO配置将内网资源推送给VPNiNode客户端。
考虑实际组网,本文所有设备均位于同一局域网内手机终端:192.168.9.0/24 vlan9服务器端:172.16.0.0/24SSL VPN网关:172.16.0.13 型号:F1000-A Comware software, Version 3.40, Release 1662P21EIA:7.0 E0201;EMO:7.0E02021.1.3三.配置流程3.1:配置open wifi配置open wifi “ssl for emo”,终端用户连上该wifi后可以与SSL VPN网关正常通信,该wifi与vlan9绑定。

AWK-4131A SeriesOutdoor industrial IEEE 802.11a/b/g/n wireless AP/bridge/clientFeatures and Benefits•2x2MIMO 802.11a/b/g/n AP/bridge/client•Millisecond-level Client-based Turbo Roaming 1•Easy setup and deployment with AeroMag•Wireless redundancy with AeroLink Protection•Easy network setup with Network Address Translation (NAT)•Rugged industrial design with integrated antenna and power isolation•IP68-rated weatherproof housing designed for outdoor applications and -40to 75°C wide operating temperature range•Avoid wireless congestion with 5GHz DFS channel support CertificationsIntroductionThe AWK-4131A IP68outdoor industrial AP/bridge/client meets the growing need for faster data transmission speeds by supporting 802.11n technology and allowing 2X2MIMO communication with a net data rate of up to 300Mbps.The AWK-4131A is compliant with industrial standards and approvals covering operating temperature,power input voltage,surge,ESD,and vibration.The two redundant DC power inputs increase the reliability of the power supply,and the AWK-4131A can be powered via PoE to make deployment easier.The AWK-4131A can operate on either the2.4GHz or 5GHz bands and is backwards-compatible with existing 802.11a/b/g deployments to future-proof your wireless investments.Advanced 802.11n Industrial Wireless Solution•802.11a/b/g/n compliant AP/bridge/client for flexible deployment•Software-optimized for long-distance wireless communication with up to 1km line of sight and external high-gain antenna (available only on 5GHz)•Supports 60clients connected concurrently•DFS channel support allows a wider range of 5GHz channel selection to avoid interference from existing wireless infrastructure Advanced Wireless Technology for Mission-critical Applications•Seamless roaming with client-based Turbo Roaming 1for <150ms roaming recovery time between APs (Client mode)•AeroMag support for error-free setup of your industrial applications’basic WLAN settings•Supports AeroLink Protection for creating a redundant wireless link (<300ms recovery time)between APs and their clients Industrial Ruggedness•Integrated antenna and power isolation designed to provide 500V insulation protection against external electrical interference •IP68-rated metal casing for complete ingress protection for any outdoor weather•-40to 75°C wide operating temperature models available for smooth wireless communication in harsh environments SpecificationsWLAN InterfaceWLAN Standards 802.11a/b/g/n802.11i Wireless SecurityModulation TypeDSSSOFDM MIMO-OFDM 1.The Turbo Roaming recovery time indicated herein is an average of test results documented,in optimized conditions,across APs configured with interference-free 20-MHz RF channels,WPA2-PSK security,and default Turbo Roaming parameters.The clients are configured with 3-channel roaming at 100Kbps traffic load.Other conditions may also impact roaming performance.For more information about Turbo Roaming parameter settings,refer to the product manual.Frequency Band for US(20MHz operating channels) 2.412to2.462GHz(11channels)5.180to5.240GHz(4channels)5.260to5.320GHz(4channels)25.500to5.700GHz(11channels)25.745to5.825GHz(5channels)Frequency Band for EU(20MHz operating channels) 2.412to2.472GHz(13channels)5.180to5.240GHz(4channels)5.260to5.320GHz(4channels)25.500to5.700GHz(11channels)2Frequency Band for JP(20MHz operating channels) 2.412to2.484GHz(14channels)5.180to5.240GHz(4channels)5.260to5.240GHz(4channels)25.500to5.700GHz(11channels)2Wireless Security WEP encryption(64-bit and128-bit)WPA/WPA2-Enterprise(IEEE802.1X/RADIUS,TKIP,AES)WPA/WPA2-PersonalTransmission Rate802.11b:1to11Mbps802.11a/g:6to54Mbps802.11n:6.5to300MbpsTransmitter Power for802.11a23±1.5dBm@6to24Mbps21±1.5dBm@36Mbps20±1.5dBm@48Mbps18±1.5dBm@54MbpsTransmitter Power for802.11n(5GHz)23±1.5dBm@MCS0/820MHz18±1.5dBm@MCS7/1520MHz23±1.5dBm@MCS0/840MHz17±1.5dBm@MCS7/1540MHzTransmitter Power for802.11b26±1.5dBm@1Mbps26±1.5dBm@2Mbps26±1.5dBm@5.5Mbps25±1.5dBm@11MbpsTransmitter Power for802.11g23±1.5dBm@6to24Mbps21±1.5dBm@36Mbps19±1.5dBm@48Mbps18±1.5dBm@54MbpsTransmitter Power for802.11n(2.4GHz)23±1.5dBm@MCS0/820MHz18±1.5dBm@MCS7/1520MHz23±1.5dBm@MCS0/840MHz17±1.5dBm@MCS7/1540MHzTransmitter Power2.4GHz26dBm18dBm18dBm5GHz(UNII-1)23dBm21dBm21dBm5GHz(UNII-2)23dBm21dBm21dBm5GHz(UNII-2e)23dBm23dBm23dBm5GHz(UNII-3)23dBm––Note:Based on regional regulations,the maximum transmission power allowed onthe UNII bands is restricted in the firmware,as indicated above.Receiver Sensitivity for802.11a(measured at5.680 GHz)Typ.-90@6Mbps Typ.-88@9Mbps Typ.-88@12Mbps Typ.-85@18Mbps2.DFS(Dynamic Frequency Selection)channel support:In AP mode,when a radar signal is detected,the device will automatically switch to another channel.However,according to regulations,after switching channels,a60-second availability check period is required before starting the service.Typ.-81@24Mbps Typ.-78@36Mbps Typ.-74@48Mbps Typ.-72@54Mbps Note3Receiver Sensitivity for802.11n(5GHz;measured at 5.680GHz)Typ.-69dBm@MCS720MHz Typ.-71dBm@MCS1520MHz Typ.-63dBm@MCS740MHz Typ.-68dBm@MCS1540MHz Note3Receiver Sensitivity for802.11b(measured at2.437 GHz)Typ.-93dBm@1Mbps Typ.-93dBm@2Mbps Typ.-93dBm@5.5Mbps Typ.-88dBm@11MbpsReceiver Sensitivity for802.11g(measured at2.437 GHz)Typ.-88dBm@6Mbps Typ.-86dBm@9Mbps Typ.-85dBm@12Mbps Typ.-85dBm@18Mbps Typ.-85dBm@24Mbps Typ.-82dBm@36Mbps Typ.-78dBm@48Mbps Typ.-74dBm@54MbpsReceiver Sensitivity for802.11n(2.4GHz;measured at2.437GHz)Typ.-70dBm@MCS720MHz Typ.-69dBm@MCS1520MHz Typ.-67dBm@MCS740MHz Typ.-67dBm@MCS1540MHzWLAN Operation Mode Access point,Client,Client-Router,Master,Slave,SnifferAntenna External,3/6dBi,Omni-directionalWLAN Antenna Connector2N-type femaleEthernet InterfaceStandards IEEE802.3for10BaseTIEEE802.3u for100BaseT(X)IEEE802.3ab for1000BaseT(X)IEEE802.3af for PoEIEEE802.1D-2004for Spanning Tree ProtocolIEEE802.1w for Rapid Spanning Tree ProtocolIEEE802.1Q for VLAN TaggingPoE Ports(10/100/1000BaseT(X),RJ45connector)1Ethernet Software FeaturesManagement DHCP Server/Client,DNS,HTTP,IPv4,LLDP,Proxy ARP,SMTP,SNMPv1/v2c/v3,Syslog,TCP/IP,Telnet,UDP,VLAN,Wireless Search Utility,MXview,MXconfigRouting Static Route,NAT,Port forwardingRedundancy Protocols RSTP,STPSecurity HTTPS/SSL,RADIUS,SSHTime Management SNTP ClientFirewallFilter ICMP,MAC address,IP protocol,Port-basedSerial InterfaceConsole Port RS-232,8-pin RJ453.Due to a limitation in the receiver sensitivity performance for channels153and161,it is recommended to avoid using these channels in your critical applications.LED InterfaceLED Indicators PWR,FAULT,STATE,WLAN,LANInput/Output InterfaceAlarm Contact Channels Relay output with current carrying capacity of1A@24VDCButtons Reset buttonDigital Inputs+13to+30V for state1+3to-30V for state0Max.input current:8mAPhysical CharacteristicsHousing MetalIP Rating IP68Dimensions224x147.7x66.5mm(8.82x5.82x2.62in)Weight1,400g(3.09lb)Installation Wall mounting(standard),DIN-rail mounting(optional),Pole mounting(optional) Power ParametersInput Current0.64A@12VDC,0.16A@48VDCInput Voltage12to48VDC,Redundant dual inputs,48VDC Power-over-EthernetPower Connector M12A-coded5-pin male connectorPower Consumption7.68W(max.)Reverse Polarity Protection SupportedEnvironmental LimitsOperating Temperature-40to75°C(-40to167°F)Storage Temperature(package included)-40to85°C(-40to185°F)Ambient Relative Humidity5to95%(non-condensing)Standards and CertificationsEMC EN61000-6-2/-6-4EMI CISPR32,FCC Part15B Class BEMS IEC61000-4-2ESD:Contact:8kV;Air:15kVIEC61000-4-3RS:80MHz to1GHz:10V/mIEC61000-4-4EFT:Power:2kV;Signal:1kVIEC61000-4-5Surge:Power:2kV;Signal:2kVIEC61000-4-6CS:10VIEC61000-4-8PFMFRadio EN300328,EN301489-1/17,EN301893,FCC ID SLE-WAPN008,ANATEL,MIC,NCC,RCM,SRRC,WPC,KCSafety EN60950-1,UL60950-1Vibration IEC60068-2-6MTBFTime440,764hrsStandards Telcordia SR332WarrantyWarranty Period5yearsDetails See /warrantyPackage ContentsDevice1x AWK-4131A Series wireless AP/bridge/clientInstallation Kit1x cap,female,metal,for M12port1x cap,metal,for RJ45port1x field-installable power plug1x field-installable RJ45plug1x stick,transparent plastic,for field-installable plug2x wall-mounting kitAntenna2x2.4/5GHz antennaDocumentation1x quick installation guide1x warranty cardDimensionsOrdering InformationModel Name Band Standards Operating Temp. AWK-4131A-EU-T EU802.11a/b/g/n-40to75°C AWK-4131A-JP-T JP802.11a/b/g/n-40to75°C AWK-4131A-US-T US802.11a/b/g/n-40to75°CAccessories(sold separately)AntennasANT-WDB-ANF-0407 2.4/5GHz,omni-directional antenna,4/7dBi,N-type(male)ANT-WDB-ANF-0609 2.4/5GHz,omni-directional antenna,6/9dBi,N-type(female)ANT-WDB-ANM-0306 2.4/5GHz,omni-directional antenna,3/6dBi,N-type(male)ANT-WDB-ANM-0407 2.4/5GHz,dual-band omni-directional antenna,4/7dBi,N-type(male)ANT-WDB-ANM-0502 2.4/5GHz,omni-directional antenna,5/2dBi,N-type(male)ANT-WDB-ANM-0609 2.4/5GHz,omni-directional antenna,6/9dBi,N-type(male)ANT-WDB-ARM-02 2.4/5GHz,omni-directional rubber duck antenna,2dBi,RP-SMA(male)ANT-WDB-ARM-0202 2.4/5GHz,panel antenna,2/2dBi,RP-SMA(male)ANT-WDB-PNF-1518 2.4/5GHz,panel antenna,15/18dBi,N-type(female)MAT-WDB-CA-RM-2-0205 2.4/5GHz,ceiling antenna,2/5dBi,MIMO2x2,RP-SMA-type(male)MAT-WDB-DA-RM-2-0203-1m 2.4/5GHz,desktop antenna,2/3dBi,MIMO2x2,RP-SMA-type(male),1m cableMAT-WDB-PA-NF-2-0708 2.4/5GHz,panel antenna,7/8dBi,MIMO2x2,N-type(female)ANT-WSB5-ANF-125GHz,omni-directional antenna,12dBi,N-type(female)ANT-WSB5-PNF-185GHz,directional panel antenna,18dBi,N-type(female)ANT-WSB-ANF-09 2.4GHz,omni-directional antenna,9dBi,N-type(female)ANT-WSB-PNF-12 2.4GHz,directional panel antenna,12dBi,N-type(female)ANT-WSB-PNF-18 2.4GHz,directional panel antenna,18dBi,N-type(female)ANT-WSB-AHRM-05-1.5m 2.4GHz,omni-directional/dipole antenna,5dBi,RP-SMA(male),1.5m cableWireless Antenna CablesA-CRF-NMNM-LL4-300N-type(male)to N-type(male),LMR-400Lite cable,3mA-CRF-NMNM-LL4-600N-type(male)to N-type(male),LMR-400Lite cable,6mA-CRF-NMNM-LL4-900N-type(male)to N-type(male),LMR-400Lite cable,9mCRF-N0429N-3M N-type(male)to N-type(male),CFD400cable,3mWireless AP Connector CablesM12A-8PFF-IP68Field-installation A-coded M12screw-in8-pin connector,female connector female PINM12A-8PMM-IP68Field-installation A-coded screw-in Gigabit Ethernet connector,8-pin male M12connector,IP68-rated A-PLG-WPRJ Field-installation RJ-type plugWireless Connector CapsA-CAP-N-M Metal cap to cover N-type connectorA-CAP-WPRJ45-MC Metal cap with chain for RJ45connectorSurge ArrestorsA-SA-NMNF-01Surge arrester,N-type(female)to N-type(male)A-SA-NFNF-01Surge arrestor,N-type(female)to N-type(female)Wireless AdaptersA-ADP-RJ458P-DB9F-ABC01DB9female to RJ45connector for the ABC-01Wireless Terminating ResistorsA-TRM-50-NM Terminating Resistor,50ohm,RP-SMA MaleWall-Mounting KitsWK-51-01Wall-mounting kit,2plates,6screws,51.6x67x2mmWireless AP Mounting KitsWK-55Wall-mounting kit,55x34.5x2.5mm©Moxa Inc.All rights reserved.Updated Nov18,2019.This document and any portion thereof may not be reproduced or used in any manner whatsoever without the express written permission of Moxa Inc.Product specifications subject to change without notice.Visit our website for the most up-to-date product information.。

中国电信天翼网关3.0 入网测试要求2018年6月目录前言 (5)修订记录 (6)1.网关运行环境 (8)1.1.网关运行环境 (8)1.1.1.运行环境基本要求 (8)1.1.2.DBUS接口功能测试 (10)1.1.3.黑名单功能测试 (11)1.1.4.白名单功能测试 (13)1.1.5.DNS限速功能测试 (14)1.1.6.DNS过滤功能测试 (15)1.1.7.URL过滤功能测试 (16)1.1.8.VOIP连接仿真测试 (17)1.1.9.QoS测试 (18)1.1.10.多个Internet WAN连接测试 (21)1.1.11.面向应用管理平台的软件整体远程升级功能测试 (22)1.1.12.内存限制和磁盘缓存测试 (23)2.中间件 (25)2.1.中间件 (25)2.1.1.Framwork应用管理接口功能测试 (25)2.1.2.Framework CAPI接口功能测试 (26)2.1.3.接口交互及处理分发功能的模块升级 (27)2.1.4.插件优先级 (28)2.1.5.插件远程升级测试 (29)2.1.6.网关telnet超时退出的异常情况 (30)2.1.7.网关质量插件调用U01上报 (31)3.云客户端 (32)3.1.云客户端 (32)3.1.1.云客户端接口功能测试 (32)3.1.2.云客户端的模块升级 (34)3.1.3.云客户端扩展模块的升级卸载 (35)4.测速 (36)4.1.测速 (36)4.1.1.一键测速 (36)5.稳定性测试(入网试用阶段) (38)5.1.稳定性测试 (38)5.1.1.稳定性测试 (38)5.1.2.插件批量远程升级测试 (38)6.WEB UI (40)6.1.1.Web UI功能测试(登录) (40)6.1.2.Web UI功能测试(首页) (40)6.1.3.Web UI功能测试(终端设备) (41)6.1.4.Web UI功能测试(WiFi设置) (42)6.1.5.Web UI功能测试(存储管理) (43)6.1.6.Web UI功能测试(高级设置) (44)6.1.7.Web UI功能测试(更多应用) (45)7.平台 (46)7.1.平台 (46)7.1.1.网关向BSS平台注册异常流程1(地址不可达) (46)7.1.2.网关向能力平台注册异常流程2(注册失败) (47)7.1.3.网关首次向BSS平台注册的时效测试 (47)7.1.4.网关向能力平台心跳保活 (48)7.1.5.能力平台反向触发网关重新向BSS平台注册 (49)7.1.6.固件/中间件/插件/云客户端升级结果上报机制 (49)8.APP (51)8.1.APP (51)8.1.1.绑定网关 (51)8.1.2.我的WiFi (51)8.1.3.网关指示灯 (53)8.1.4.通过手机APP进行设备信息读取 (53)8.1.5.动态域名 (54)8.1.6.通过手机APP识别下挂设备 (55)8.1.7.绿色节能 (56)8.1.8.通过手机APP配置访客WiFi (57)8.1.9.通过手机APP配置定时重启 (58)8.1.10.通过手机APP配置网关休眠 (58)8.1.11.通过APP获取Wan侧速率 (59)9.插件 (61)9.1.插件通用性测试 (61)9.1.1.插件恢复出厂设置测试 (61)9.2.B01插件 (62)9.2.1.B01插件测试 (62)9.2.2.B01插件升降级 (64)9.2.3.B01插件接口测试 (64)9.2.4.B01插件运行测速影响 (66)9.2.5.B01插件流量接口测试 (67)9.3.U01插件 (69)9.3.1.u01插件测试 (69)9.3.2.U01插件接口测试 (70)9.3.3.U01插件运行测速影响 (70)9.4.1.智能组网插件测试 (72)9.4.2.智能组网插件强制漫游功能测试–从网关漫游到AP (73)9.4.3.智能组网插件强制漫游功能测试–从AP漫游到网关 (74)9.4.4.智能组网插件对网关性能影响测试 (76)9.5.网络质量诊断插件 (77)9.6.R01插件 (78)9.6.1.r01插件下发安装启动 (78)9.6.2.r01插件正常运行检测 (78)9.7.网关诊断插件 (80)10.家庭智能组网系统测试 (81)10.1.802.11K/V漫游功能测试 (81)10.1.1.网关支持802.11 k、802.11v 2.4G漫游切换功能 (81)10.1.2.网关支持802.11 k、802.11v 5G漫游切换功能 (82)10.2.快连配网功能测试 (84)10.2.1.基于固定SSID的快连配网功能测试 (84)10.2.2.基于Beacon/Probe帧扩展的快联配网功能测试 (86)前言本测试要求是根据中国电信开展智慧家庭宽带业务的实际需要而制定的,主要用于集采入围天翼网关产品的入网测试。

Anybus Wireless Bridge product FEATURES & BENEFITSWIRELESS LAN INTERFACE Anybus Wireless Bridge II – EthernetAnybus® Wireless Bridge enables you create an industrial wireless connection in anindustrial Ethernet network. This second generation of the proven and trusted Wireless Bridge can communicate via both Bluetooth and Wireless LAN and is ideal for communication throughhazardous areas or hard-to-reach locations where cables are not desirable. It provides an effectivewireless range of up to 400 meters.BRIDGING TCP/IP ETHERNET The Wireless Bridge makes it possible to operate leading TCP/IP based industrial Ethernetnetworks, such as BACnet/IP , PROFINET , EtherNet/IP and Modbus TCP , over Bluetooth andWireless LAN 2.4 / 5 GHz.POINT-TO-POINT OR MULTIPOINTPoint-to-point or multipoint Anybus Wireless Bridge is often used as an Ethernet cable replacement(point-to-point communication). But it can also be used as an access point for up to sevenWireless LAN/Bluetooth clients.Use with point-to-point wireless Industrial Ethernet installations through hazardous or hard-to-reach locationsUse as an Access Point for up to seven clientsSuitable for AGV’s (Automatic Guided Vehicle)Fast Roaming (IEEE 802.11r), High link speed (IEEE 802.11n), Robustness (three internal antennas, including MIMO)Eliminates the need for expensive or maintenance-heavy cablingBridges TCP/IP Ethernet and protocols such as: BACnet/IP , EtherNet/IP , Modbus-TCP and PROFINETMax range of up to 400 metersFull compatibility with Anybus Wireless Bolt — a wireless product for machine mountingEasy setup via push button or web interfaceAdvanced configuration with AT commandsCompatible with PROFIsafe requirementsRugged IP65 rated industrial designSecurity features for a secure industrial operationThree built in antennas for higher performance and better robustnessOperation with Wirelesss LAN, Bluetooth classic and Bluetooth Low Energy.CLI (Command Line Interface) for configuration and diagnosticsStarterkit availableWireless standards: WLAN 802.11 a, b, g, n, d.Operation modes: Access point or ClientWiFi channels: 2.4 GHz, channel 1-11 + 12-13 depending on regulatory domain scan.5 GHz Access Point: 36-48 (U-NII-1), 5 GHz Client: 100-116 + 132-140 and 120-128 depending on regulatory domain scan. (U-NII-1,U-NII-2, U-NII-2e).BLUETOOTH INTERFACE BLUETOOTH LOW ENERGY ETHERNET INTERFACECUSTOMER STORY1080 MOTION: ANYBUS WIRELESS TECHNOLOGY USED FOR ATHLETE TESTINGAnybus Wireless Bridge enables data from 1080 Motion’s neuromuscular testing machines tobe transferred wirelessly to a computer for immediate display.LOOKING FOR CAN TO BLUETOOTH? TAKE A LOOK AT OUR IXXAT® CANBLUE IICANblue IIWireless CAN Bridge for Bluetooth - range 200mProduct detailsTechnical specificationsRF output power: 18 dBm EIRP (including max antenna gain 3dBi)Max number of slaves for access point: 7Power consumption: 54mA@24VDCNet data throughput: 20 Mbps. Link speed: max 130 Mbps (802.11n 2x2 MIMO)Security: WEP 64/128, WPA, WPA-PSK and WPA2, TKIP and AES/CCMP , LEAP , PEAP .Wireless standards (profiles): PAN (PANU & NAP)Operation modes: Access point or ClientRF output power: 14 dBm EIRP (including max antenna gain 3dBi)Max number of slaves for access point: 7Power consumption: 36 mA@24VDCNet data throughput: ~1 MbpsBluetooth version support: Classic Bluetooth v2.1Security: Authentication & Authorization, Encryption & Data Protection, Privacy & Confidentiality, NIST Compliant, FIPS Approved Wireless standards (profiles): GATTOperation modes: Central or Peripheral (pending)RF output power: 10 dBm EIRP (including max antenna gain 3dBi)Max number of simultaneous connections for Central: 7Power consumption: 36 mA@24VDCNet data throughput: ~200 kbpsBluetooth Low Energy version: 4.0 dual-modeSecurity: AES-CCM cryptographySupports Ethernet protocols: IP , TCP , UDP , HTTP , LLDP , ARP , DHCP Client/ServerSupports wireless bridging of Industrial Ethernet protocols: BACnet/IP , EtherNet/IP , Modbus-TCP , PROFINETEthernet interface: 10/100BASE-T with automatic MDI/MDIX cross-over Wired interfaceEthernet 10/100 Mbit/s Dimensions (H•W•D)93 x 68 x 33mm Weight120g or 0,26 lbs Operating temperature-30 to +65 °C or -22 to +149 °F (Storage temp: -40 to +85 °C )Power supply9-30 VDC (-5% +20%), Cranking 12V (ISO 7637-2:2011 pulse 4). Reverse polarity protection.Power consumption0.7W idle, 1.7W max Enclosure material Plastic PC/ABS (Bayblend FR3010)Wired interface Ethernet 10/100 Mbit/sMechanical rating IP65Mounting Two screws (Ø 4 mm) on flat surface. DIN rail mount option available (optional accessory). Max range 400 metersConfiguration Three different methods:• Accessing the built-in web pages in the product• Using Easy Config modes (via push button or inside web interface)• Sending AT commandsConnectors1x M12 for Ethernet (4-pin, D-coded)1x M12 for Power 5-pin, A-coded)RP-SMA antenna connector for external antennaAntennas AWB3000Three internal antennas:1. 2.4 GHz2. 2,4GHz MIMO3. 5GHz AWB3010One external antenna: 1. 2,4/5GHz dual bandThe external antenna does not provide better range, but allows connectivity if the WirelessBridgeneeds to be placed inside a radio-secure environment such as a steel cabinet. When mountinginside a steel cabinet antenna cables with magnetic foot or screw mount should also beconsidered.CERTIFICATIONSEurope ATEX: ATEX Category 3, zone 2 according to EN60079-15, product marking: EX II 3 G nA IIC T4.2014/53/EURadio Equipment Directive (RED)USA FCC 47 CFR part 15, subpart B.UL: Ind. Cont. Eq. also Listed Ind. Cont. Eq. for Haz. Loc. CL1, DIV 2, GP A,B,C,D,T4. UL file:E203225Canada ICES 003Japan MICOther countries Australia, Colombia, Turkey, Malaysia, Peru, Mexico, Argentina.Brazil, India, Philippines, South Africa, Korea.WLAN Security WEP 64/128, WPA, WPA-PSK and WPA2, TKIP and AES/CCMP, LEAP, PEAP.Bluetooth Security Authentication & Authorization, Encryption & Data Protection, Privacy & Confidentiality, NISTCompliant, FIPS ApprovedFile Version Size Read onlineContent of deliveryAWB3000 (WITH INTERNAL ANTENNAS) / AWB3010 (WITH EXTERNAL ANTENNA)Quick start documentationPower supply not includedOptional AccessoriesOrder Code: 023040Accessory Pack – 1.5 meter Ethernet Cable with RJ45 connectorand World power supply with 1.5 meter cable and M12 connector.Order Code: 024700IP67 M12 connector kit for power and Ethernet,with screw terminalsOrder Code: 024701DIN clip with screwsOrder Code: 024702Replacement external antenna. Foldable, dual band.RPSMA connectorOrder Code: 024711Swivel Mount kit for Anybus Wireless BridgeIncluding 1x Swivel Mount bracket, 2x slim clamps and 2x mounting screws1.04.0085.00000Magnetic antenna foot with 1,5 m cable andRPSMA connector, excl. antenna.1.04.0085.00003Screw-mount antenna base with 1,5 m cableand RP-SMA connector, excl. antennaWireless bridge complete cable kit- All you need to make your Ethernet cable go wireless!Order code: AWB30032 pcs Anybus Wireless Bridge II (internal antennas)2 pcs Ethernet cables 2 meters, M12 + open leads2 pcs ”click mount” Ethernet RJ45 connectors2 pcs Power cables 2 meters M12 + open leadsWireless bridge starterkitOrder code: AWB3300Two Wireless Bridges with internal antennas,Two Power Supplies (world), cabling, Quick Start Guide(Limitation: Max one Starterkit per customer)Ordering InformationOrder code AWB3000 (WITH INTERNAL ANTENNAS)AWB3010 (WITH EXTERNAL ANTENNAS)Quick start documentation, USB configuration cable are included. Configuration software is available for download.Power supply is not included. 3 year guarantee. For purchasing instructions and terms and conditions, see: How to buyCopyright © 2020 HMS Industrial Networks - All rights reserved.。

H3C_iNode智能客户端_破解我们单位最新弄了套上网程序,叫什么H3C iNode智能客户端,对我们上网做了好多限制,令我最不爽的是有人竟然能看到我上网在看什么,好像被监控了的感觉,更令我郁闷的是U盘使用起来前所未有的麻烦,还经常不好使。
别提多憋屈了后来上网一顿神找资料,终于找到了这个程序的替代方案。
哈哈心里一下子就有了大海的感觉。
下面我跟大家做个分享哈哈:H3C iNode智能客户端采用的是802.1x 拨号协议,首先上网找一个802.1x替代拨号软件。
我这里用的是个叫xclient的软件来替代原来的拨号程序,在安装这个xclient之前要有个winpcap的驱动然后在装上这个xclient。
这样原有的那个H3C iNode智能客户端就没用了,你就可以把它卸载掉了。
哈哈【xclient 2.0】:【winpcap 4.0.2】:卸载了之后还有一个问题,就是U盘照样不能使用,因为涉及到一个认证的问题,那么如何才能恢复机器本来的面貌呢?重装系统当然可以,不过那是个笨方法,下面有个简单的方法嘿嘿:当你卸载掉了H3C iNode智能客户端的时候,其实有些他自带的服务还是没有被卸载掉的,那么就需要我们手动来关闭这些服务,这样你的U盘就象以前那样真正的即插即用了。
首先在运行里输入services.msc然后找到一个叫H3C DAM Agent的服务进程(他就是U盘不能即插即用的罪魁祸首)如图:把它禁用掉,在禁用的时候一定要先双击这个服务进程,在打开的页面里选择登陆分页然后在下面有个叫Profile1的硬件配置文件,先把它给禁用了,这样你才能真正禁用掉H3C DAM Agent这个进程,要不这么做这么进程在你禁掉后还会自动启用的。
呵呵 .这样你所有的事都大功告成了!!!尽享冲浪的乐趣吧。
注解:winpcap(windows packet capture)是windows平台下一个免费,公共的网络访问系统。

iNode客户端认证常见错误及处理办法提示信息:E63054::重复认证报文。
解决方法:出现这种错误时,应考虑可能是主-备服务器认证与记账报文发往的服务器不一致造成的,应注意观查一下接入交换机的配置中关于radius服务的配置项,是否会有不一致的情况发生。
处理的方法:1、重启接入交换机。
2、更改接入交换机的认证、记帐服务器的运行状态。
提示信息:IP地址与网络上的其他系统有冲突,连接被中断解决方法:请携带校园卡或学生证到科技楼3楼卡务中心报修。
提示信息:MAC地址绑定检查失败解决方法:请携带校园卡或学生证到科技楼3楼卡务中心解除MAC地址绑定。
提示信息:用户密码错误,加入黑名单解决方法:请携带校园卡或学生证到科技楼3楼卡务中心修改密码。
提示信息:您的网卡已被禁用或者网络电缆没有插好,这可能会影响您使用网络解决方法:a) 检查本地连接是否被禁用,如果被禁用改为启用b) 检查线路连接,网线是否插好c) 更换墙上端口,更换网线d) 检查自己的交换机,更换端口,重新启动,或直接用墙上的接口连接e) 检查网卡是否安装正确,检查驱动程序是否正常。
f)iNode客户端-〉属性-〉选择正确的网卡。
提示信息:静态IP地址绑定检查失败解决方法:a) 检查IP地址是否正确配置到本地连接当中(配置方法见问题9)。
b) 如果IP地址配置正确,卸载网络适配器驱动程序,重新启动电脑后重新配置IP地址。
卸载网络适配器方法:Xp系统:桌面我的电脑右键→属性→硬件→设备管理器→网络适配器→找到与本地连接相同的网卡(如图4)右键→卸载驱动Win7系统:桌面计算机右键→属性→(左侧)设备管理器→网络适配器→找到与本地连接相同的网卡右键→卸载驱动图4提示信息:未收到服务器回应,您的计算机可能只能访问隔离区的网络资源,请检查终端能否正常访问网络或者与管理员联系解决方法:a) 检查网关配置。
(将你的ip地址最后一组数字改成254就是你的网关)b) 如果网关配置正确,请到科技楼3楼卡务中心窗口报修。
TCP Performance in Coded Wireless MeshNetworksYong Huang∗,Majid Ghaderi†,Don Towsley†and Weibo Gong∗∗Department of Electrical and Computer Engineering†Department of Computer ScienceUniversity of Massachusetts AmherstTechnical Report:TR-07-CSE-02AbstractThis paper investigates the benefit of network coding for TCP traffic in a wireless mesh network.We implement network coding in a real wireless mesh network and measure TCP throughput in such a network.Unlike previous implementations of network coding in mesh networks,we use off-the-shelf hardware and software and do not modify TCP or the underlying MAC protocol.Therefore,our implementation can be easily exported to any operational wireless mesh network with minimal modifications.Furthermore,the TCP throughput improvement reported in this paper is due solely to network coding and is orthogonal to other improvements that can be achieved by optimizing other system components such as the MAC protocol.We conduct extensive measurements to understand the relation between TCP throughput and network coding in different mesh topologies.We show that network coding not only reduces the number of transmissions by sending multiple packets via a single transmission but also results in smaller loss probability due to reduced contention on the wireless medium.Unfortunately,due to asynchronous packet transmissions,there is often little opportunity to code resulting in small throughput gains.Coding opportunity can be increased by inducing small delays at intermediate nodes.However,this extra delay at intermediate nodes results in longer round-trip-times that adversely affect TCP throughput.Through experimentation,wefind a delay in the range of1ms to2ms to maximize TCP throughput.For the topologies considered in this paper,network coding improves TCP throughput by20%to70%.I.I NTRODUCTIONIn traditional networks,data packets are carried by store-and-forward mechanisms in which the in-termediate nodes(relays or routers)only repeat data packets that they have received.The concept of network coding was introduced for satellite communications in[1]and then fully developed in[2]for general networks.With network coding,a network node is allowed to combine several packets that it has generated or received into one or several outgoing packets.The original paper of Ahlswede et al.[2]showed the utility of network coding for multicast in wireline networks.Recently,network coding has been applied to wireless networks and received significant popularity as a means of improving network capacity and coping with unreliable wireless links[3]–[7]. In fact,the unreliability and broadcast nature of wireless links make wireless networks a natural setting for network coding.Moreover,network protocols in wireless networks,e.g.,wireless mesh networks and mobile ad hoc networks,are not fully developed yet and hence there is more freedom to apply network coding in such environments compared to wireline networks such as the Internet[5].In spite of many research papers on the application of network coding in wireless networks,unfortu-nately,there are not many real implementations.Because of the need for tractability,theoretical results on network coding do not account for the detailed behavior of a wireless network,e.g.,asynchronous transmissions due to random delays.Therefore,it is not well understood to what extent network coding improves the throughput capacity of a wireless network in a real implementation.This paper aims at characterizing and quantifying such throughput improvements in the context of wireless mesh networks (WMNs)employing network coding.We focus on TCP traffic,and hence TCP throughput improvement due to network coding,because TCP is expected to be the dominant transport protocol in WMNs.Surprisingly,TCP performance in coded wireless networks is a largely unknown area(in fact,network coding with multiple unicastflows has been just recently studied in[8]).A few papers that have implemented network coding in a wireless setting do not specifically con-sider TCP(see[3]for example).The only exception is the so-called COPE[6]which implements an opportunistic network coding scheme.In[6],the authors performed TCP experiments to understand how network coding impacts TCP throughput in a mesh setting.However,they did not fully explore the interactions between TCP and network coding.In this paper,we perform extensive experiments in our COTS1implementation to understand how network coding interacts with TCP and exploit these interactions to maximize TCP throughput.TCP traffic is naturally bidirectional,i.e.,data packets in one direction and ACK packets in the opposite direction,and hence network coding can be applied at intermediate nodes along the path even for a single TCPflow.Unfortunately,due to random delays in network,coding opportunities at intermediate nodes may be too small to benefit TCP.We show that inducing a small delay at each intermediate node can increase coding opportunity for TCP traffic,especially when there are only a few TCPflows in the network. However,there is a trade-off between increased coding opportunity and increased TCP round-trip-time by increasing delay at intermediate ing real measurements from our test-bed,we characterize the proper amount of delay in different mesh topologies and show how the induced delay affects coding opportunity,packet loss probability and round-trip-time.The contributions of this paper can be summarized as follows:1)It presents an implementation of network coding in a wireless mesh network using commercialoff-the-shelf hardware and software.2)It is thefirst paper that carefully studies interactions between network coding and TCP.3)It studies the impact of induced delay at intermediate nodes on coding opportunity,packet lossand TCP round-trip-time and empirically characterizes the best value of delay that maximizes TCP throughput.The rest of the paper is organized as follows.In Section II,we briefly describe network coding.We will focus on linear random coding and use simple examples to explain the concept of network coding. Section III is dedicated to network coding in wireless networks and reviews related work in the context of wireless mesh networks.In Section IV,we provide detailed description of our implementation of network coding in a WMN.We summarize our experiments in Section V.Our conclusions as well as future work are discussed in Section VI.II.N ETWORK C ODINGConsider a network composed of a set of source-destinations and a set of intermediate nodes acting as relays,e.g.,routers in Internet.Traditionally,relays simply repeat the packets they have received.With network coding,relays are allowed to combine packets that they have received into one or more packets before sending the packets over outgoing links.The concept of network coding is easiest explained using the famous butterfly example depicted in Figure1.All links have unit capacity,e.g.,one bit per time unit,and senders S1and S2want to send two bits X and Y to both receivers R1and R2.Clearly,link A-B is the bottleneck link,and hence,four units of time are required to transmit X and Y to R1and R2using a store-and-forward mechanism.However, using the transmissions outlined in thefigure,the multicast problem can be solved using only three units of time.In this example,node A XORs X and Y and transmits X⊕Y in a single transmission.In general, nodes can use different coding techniques to combine packets,however,Li et al.[9]showed that linear coding suffices to achieve the max-flow,i.e.,the optimum,in single source multicast networks.Then, the problem of network coding is how to select the linear combinations that each node of the network performs.In practice,most network coding approaches are based on the concept of random linear coding 1Commercial Off-The-Shelf hardware and software.Fig.1.Butterfly exampleproposed by Ho et al.[10].With random linear coding,each node in the network selects the linear coding coefficients uniformly at random over a finite field in a completely independent and decentralized manner.A brief description of random linear network coding is as follows:•At a sender node:Let {P 1,...,P n }denote the set of n original packets at a node.With linear network coding,the node generates a set {X 1,...,X k }of k (k ≥n )coded packets that are linear combinations of the original data packets and sends them over the outgoing links:X i =n j =1αij P j ,i =1,...,kwhere αijare the coding coefficients drawn uniformly from the field F 2q .In this approach,packets are treated as vectors over the field F 2q .The reason to use a linear code is that the encoding and decoding algorithms are well understood [11].Note that addition and multiplication are performed over the field F 2q .In random linear coding,each node in the network randomly chooses the coding coefficients from the field.By choosing a sufficiently large field,the probability of having linearly dependent combinations can be made arbitrarily close to zero.In random coding,the encoding vector ,whose components are the encoding coefficients,is sent in the packet header along with the actual packet information.•At an intermediate node:Consider an intermediate node that has received and stored a set {X 1,...,X m }of m coded packets.This node may generate new encoded packets {Y 1,...,Y l }by choosing anotherset of random coefficients βik from the field F 2q and computing a linear combination as followsY i =m j =1βi j X j ,i =1,...,lIn this case,a straightforward computation shows that the new encoding coefficients are given by g i j = m k =1βi k αkj for i =1,...,l .•At a receiver node:The receiver needs to decode the received packets in order to extract the original packets.Assume that the receiver has received the set {X 1,...,X k }of k coded packets.In order to decode the original packets,it needs to solve a system of k linear equations {X i = nj =1g ij P j },where g i j ’s are embedded in packet headers.There are efficient approaches based on Gaussian elimination to solve the system of linear equations.III.N ETWORK C ODING IN W IRELESS M ESH N ETWORKSIn wireless environments,network coding has been applied to various problems including broadcasting in ad hoc networks [7],data collection in sensor networks [7],file sharing in mesh networks [12]andreliability in lossy networks[4].In this section we review some related works on applying network coding in a WMN and refer interested readers to[5]and[7]for other applications.In the context of mesh networks,in particular,we review the application of network coding to bidirectional traffic proposed in[3] and opportunistic network coding proposed in[6].Wu et al.[3]investigated the use of network coding for the mutual exchange of independent information between two nodes in a wireless network.They showed that network coding can be used to increase the capacity of a wireless network with bidirectional traffic.Consider the network depicted in Figure2.Node A wants to send packet X to node C and node C wants to send packet Y to node A.With traditional store-and-forward routing,X and Y belong to two different unicastflows,one from A to C and the other from C to A.Hence,two routes are created to exchange packets between A and C.In this case,to exchange X and Y,four time slots are required.work coding for bidirectional trafficHowever,by using network coding and broadcasting,as shown in thefigure,the exchange can be performed in only three time slots.In thefirst two time slots X and Y are transmitted to node B,and then in the third time slot,node B broadcasts X⊕Y to nodes A and C.Upon receiving X⊕Y from B, node A(C)extracts Y(X)using its existing copy of X(Y).Therefore,one transmission is saved,which effectively increases the capacity by25%compared to traditional store-and-forward scheme.The authors also discussed a distributed implementation when transmissions are not synchronized and the wireless channel is lossy and with random delays.COPE[6]is thefirst implementation of network coding in a WMN.In COPE,each node uses local information to detect coding opportunities.The key idea is to use opportunistic listening,intrinsic to the wireless medium,to exploit network coding on thefly.All nodes opportunistically listen to all communications over the same wireless channel.Moreover,when a node transmits a packet,the node tells its neighbors what packets it already has in its storage by embedding a list of packet ids in the packet header.Each node then uses its knowledge of what packets its neighbors have to perform opportunistic coding by combining multiple packets in a single transmission as long as all the receivers have enough information to extract their intended packets.Next hopPacketP1 P2 P3 P4A C C D(a)Next hop information at node BP4P1P3P1 (b)Node B broadcasts P1⊕P3⊕P4Fig.3.Opportunistic network codingCOPE uses XOR operations to encode packets.Each node checks various packet combinations tofind the largest set of packets that can be coded together while all intended recipients are able to decode their respective packets.An example of opportunistic coding is illustrated in Figure3(b).Node B has four packets{P1,P2,P3,P4}in its queue with next hops given in Figure3(a).Because of opportunisticlistening,node B knows what packets are already stored in neighboring nodes A,C and D.Therefore, node B combines P1⊕P3⊕P4and sends it in a single transmission.Nodes A,C and D can then extract P1,P3and P4,respectively,using the packets already in their storage.IV.N ETWORK C ODING I MPLEMENTATIONIn our test-bed,the network coding module works between the link layer(layer2)and the network layer(layer3)based on Mesh Connectivity Layer(MCL)toolkit[13]and is transparent to other layers. MCL is a loadable Microsoft Windows driver that provides wireless mesh connectivity.It uses a modified Dynamic Source Routing(DSR)called Link Quality Source Routing(LQSR)to support link quality metrics.When it receives packets from layer3,MCL looks up its routing tables and encapsulates the source routing information into a LQSR header.Then the packet is passed to the link layer andfinally transmitted through the physical layer device.A.Unicast and Broadcast in IEEE802.11In our test-bed we use COTS IEEE802.11a network cards.As defined by802.11MAC,packets are transmitted either in unicast mode or broadcast mode.The unicast mode has some special properties compared the to the broadcast mode:•Link Layer Acknowledgement:In unicast mode,the receiver node immediately sends an acknowl-edgement packet for every packet it received at the link layer.•Link Layer Retransmission:Until the link layer acknowledgement is obtained,the sender assumes the packet is still in the air.The sender will retransmit the packet if a retransmission timer expires.Retransmission may be repeated until a maximum number of retransmissions has been reached.•Back-Off Window Adjustment:Before every retransmission,the sender doubles its back-off window.A node randomly sets a back-off counter between0and the current back-off window size before anytransmission.This counter is decremented by one slot time everytime if there is no medium activity during this period.The node sends the packet until this counter reduces to0.Hence,doubling the back-off window can reduce the retransmission collision probability.•Dedicated Receiver:In unicast mode,the destination is unique and its physical address is placed in the Ethernet header.If a node is not the receiver,it will drop the packet immediately at the physical layer unless it works in promiscuous mode.On the other hand,the broadcast mode provides a basic channel.The broadcast mode does not require a link layer acknowledgement.As a result,there is no link layer retransmission and no back-off window adjustment.A broadcast address is used to allow all nodes to receive the packet and the physical layer at receiver side passes the payload to upper layers for further processing.B.Pseudo-Broadcast or Pseudo-UnicastIn a WMN,network coded packets must be transmitted to multiple receivers to gain throughput im-provement.One way to do it is to put nodes into promiscuous mode;another way is to use broadcast mode to transmit coded packets.Katti et al.[6]use thefirst approach in their Linux-based implementation.In other words,COPE uses a pseudo-broadcast approach to send the coded packets using unicast functionality of802.11.The receivers work in promiscuous mode and can receive any packets in the air.In this way, a coded packet can be delivered to multiple receivers simultaneously.However,only a few COTS wireless cards support promiscuous mode.Even for those that support promiscuous mode,it is hard to switch them to promiscuous mode in Windows platform.Also,the pseudo-broadcast requires an intelligent and complicated broadcast operation.Our implementation simply uses the second approach,i.e.,the physical broadcasting method,to implement network coding.In our implementation,coded packets are always broadcasted.However,if non-coded packets are transmitted using the native unicast functionality of802.11,they take advantage of unicast mode andhave a better chance of delivery.It is unfair to compare network coding performance without the same link-layer functionality for coded and non-coded packets.Therefore,we implement pseudo-unicast in our test-bed.Under pseudo-unicast,unicast packets (non-coded packets)are transmitted using the broadcast function-ality of 802.11in the same way that broadcast packets (coded packets)are transmitted.Pseudo-unicast provides a worse channel than real unicast,but it provides a fair test-bed to illustrate the gain solely achieved by network coding.With pseudo-unicast,both network coding and non-coding work under the same MAC and link conditions.C.ImplementationNetwork coding module generates either pseudo-unicast packets or coded packets based on LQSR packets created by the MCL module.We first show the packet structures generated by different modules in Figure 4and then illustrate the operations of our implementation in Figure5.Pseudo-Unicast PacketCoded Packet (A xor B)LQSR PacketEhternet PacketFig.4.Packet structures generated by different modules.Ethernet packets are from layer 3.LQSR packets are generated by work coding module produces either pseudo-unicast packets or coded packets that are passed to layer 2.As shown in Figure 4,the MCL module generates LQSR packets by inserting an additional LQSR header into Ethernet packets received from the network pared to LQSR packets,a pseudo-unicast packet has an additional NC Header and its destination in the Ethernet header is set to the broadcast address (0xffffff).The NC header holds the packet identification information used in coding and decoding operations.The identification information includes the original destination address,the packet ID and the payload length.Figure 4also shows the structure of a coded packet consisting of packet A XORed with packet B.The destination of the coded packet is also set to the broadcast address.The NC header includes the triples (real destination address,ID and payload length)of both packet A and packet B.The rest of the coded packet consists of the LQSR headers of packets A and B and the XOR-ed payload.As shown in the figure,coded packets have a longer header than non-coded packets.A better design of the header,e.g.,XOR-ing the LQSR headers of both packet A and packet B,can reduce this overhead.Figure 5depicts the operations of our network coding implementation.The module consists of sending and receiving procedures.Two First-In-First-Out (FIFO)queues are used to store the packets.The first,called NC Cache,is used to keep copies of all outgoing and incoming packets for decoding purpose.Another FIFO queue is the NC Buffer.It holds the outgoing packets that have not found a coding opportunity yet.The sending procedure seeks coding opportunities for all outgoing packets.First,a local copy of an outgoing packet is stored in the NC Cache for decoding purpose.Then,if there is another packet in the NC buffer going in the opposite direction,the two packets are encoded immediately.Finally,the coded packet is passed to the link layer to be transmitted.If there is no coding opportunity when the packetFig.5.Operations of network coding implementationarrives,it waits in the NC Buffer for a future coding opportunity.Every packet in the NC Buffer has an associated timer with an initial value of NCBufTimeout.If this timer expires,the packet will be pseudo-unicasted.NCBufTimeout is an important parameter.As will be shown in the later part of the paper,NCBufTimeout may increase TCP throughput by creating more coding opportunity,but may decrease TCP throughput by increasing the round-trip-time.When receiving a packet,as shown in Figure5,a receiverfirst checks whether its address is included in the NC header of the received packet.If not,the packet is discarded immediately.Otherwise,if the packet is a coded packet,the receiver tries to decode it.To decode a packet,e.g.packet X from a coded packet X⊕Y,the receiver will look for packet Y in its NC Cache.If packet Y is found,packet X can be successfully decoded and a local copy of packet X will be stored in the NC Cache.Otherwise,packet X⊕Y is simply discarded.On the other hand,if the received packet is pseudo-unicasted(not coded),the receiver only needs to store a local copy of the received packet into its NC Cache.Finally,the processed packet is passed to the upper layer via the MCL module.V.TCP E XPERIMENT R ESULTSIn this section,we present TCP performance results in our test-bed with different topologies.Figure6(a) shows a simple line topology with7nodes and Figure6(b)depicts a mesh topology.All7nodes use the same Dell1450Dual-band802.11a/b/g wireless cards.To avoid interferences with existing802.11b/g networks,the test-bed uses802.11a.Static routing is used in all experiments.A.Performance MetricsWe are interested in the throughput gain achieved by network coding.Throughput gain is defined as:Gain=ThroughputCoding−ThroughputNoCodingThroughputNoCoding×100%(1)where ThroughputCoding and ThroughputNoCodingdenote average TCP throughput when network coding isturned on and off,respectively.S (R R 1(S 2)(a)Line topologyWireless NodeWireless LinkS 1R 21S 2S 3R 43S 4(b)Mesh topologyFig.6.Network topologies with 7nodes:S i and R i are the sender and receiver of TCP flow i ,respectively.The following observations are made with respect to TCP throughput:•Network coding may decrease loss probability,hence increase TCP throughput:TCP can achieve a higher throughput with a lower TCP loss work coding uses fewer transmissions to carry packets between a source-destination pair,and hence reduces the contention on wireless medium.Consequently,the overall packet loss probability is reduced and TCP throughput increases.TCP usually cannot fully utilize channel capacity.Hence the coding opportunity can be very low because the data and acknowledgement packets may not arrive at the same intermediate node ing timers at intermediate nodes can create more coding opportunity.•Network coding may increase round-trip-time,hence reduce TCP throughput:TCP has a lower throughput with larger round-trip-time.The extra waiting time at intermediate nodes caused by the use of timers increases the average round-trip-time.In particular,large value of NCBufTimeout results in longer round-trip-time and consequently decreases TCP throughput.Clearly,there is a trade-off between reduced loss probability and increased round-trip-time.We define the average coding ratio (CR)as the number of coded packet transmissions over the total number of packet transmissions.In our implementation,CR depends on the parameter NCBufTimeout .On one hand,larger NCBufTimeout increases CR,and hence reduces the loss probability.On the other hand,larger NCBufTimeout results in longer round-trip-time.In summary,our performance metrics include 1)TCP throughput gain,2)Average coding ratio (CR),3)Average TCP loss probability (p ),4)Average round-trip-time (RTT).In the next section,we show the throughput gain achieved by network coding and experimentally characterize the good values of NCBufTimeout in different topologies.B.Performance EvaluationThree experiments are conducted in our test-bed.The first experiment has one TCP flow in the line topology shown in Figure 6(a)from node A to G.Nodes B,C,D,E,and F act as relays.The second experiment has dual TCP flows in the same topology,from A to G and G to A,respectively with symmetric traffic.The last experiment has four TCP flows in the mesh topology depicted in Figure 6(b),from A to G,G to A,B to F,and F to B,respectively.Nodes C,D and E are relays.For each experiment we report the average of 10runs where each run lasts 90seconds.The variation between runs is negligible.Figure 7presents the TCP throughput 2gain achieved by network coding in different topologies with different values of NCBufTimeout .The figure shows that 1.5milliseconds is the best NCBufTimeout in all experiments.In the line topology with one TCP flow,the largest throughput gain is 70%.As the2The throughput computed in our experiments is based on the successfully received packets and hence can be interpreted as the goodput.10 20 30 40 50 60 70 80T h r o u g h p u t G a i n (%)NCBufTimeout (ms)Fig.7.TCP throughput gainnumber of TCP flows increases,the throughput gain decreases.The reason is that multiple TCP flows increase channel utilization with a consequent reduction of room for network coding improvement.As the number of flows increases,the improvement becomes less significant.5 10 15 20C o d i n g R a t i o (%)NCBufTimeout (ms)(a)Average coding ratio (CR)5 10 15 20p (%)NCBufTimeout (ms)(b)Average loss probability (p ) 01020 30 40 50 60 70 80T C P R T T (m s )NCBufTimeout (ms)(c)Average RTTFig.8.Average coding ratio,loss probability and RTT for the line topology with 1TCP flow.5 10 15 20C o d i n g R a t i o (%)NCBufTimeout (ms)(a)Average coding ratio (CR)5 10 15 20p (%)NCBufTimeout (ms)(b)Average loss probability (p ) 010 20 30 40 50 60 70 80T C P R T T (m s )NCBufTimeout (ms)(c)Average RTTFig.9.Average coding ratio,loss probability and RTT for the line topology with 2TCP flows.To have a better understanding of how NCBufTimeout affects TCP performance,Figures 8-10present CR,p and RTT for the three different experiments.Figure 8(a),9(a)and 10(a)show that CR at every relay increases as NCBufTimeout increases.Also different relays experience different values of CR.Figure 8(a)shows that the nodes (F and B)close to the source and destination have a higher CR than the other nodes.The node in the middle (D)has the lowest CR.Figure 9(a)shows a similar result.Because of the traffic symmetry,nodes B and F (C and E)have the same CR.The node in the middle (D)still has the worst coding opportunity.However,for the result of the mesh topology shown in Figure 10(a),5 10 15 20C o d i n g R a t i o (%)NCBufTimeout (ms)(a)Average coding ratio (CR)5 10 15 20p (%)NCBufTimeout (ms)(b)Average loss probability (p ) 010 2030 40 50 60 70 80T C P R T T (m s )NCBufTimeout (ms)(c)Average RTTFig.10.Average coding ratio,loss probability and RTT for the mesh topology with 4TCP flows.the middle node (D)has higher CR than node C and E as NCBufTimeout increases.The reason is that nodes C and E can only encode the packets of two flows but node D can encode packets of all four flows.Therefore,CR at a relay depends on not only the location of the relay but also the number of flows that the relay can encode.Although the maximum CR at the best NCBufTimeout is only around 5%,the network coding still achieves significant throughput gains.Figures 8(b),9(b)and 10(b)show how network coding reduces packet loss probability p in different experiments.As NCBufTimeout increases,CR increases and the number of transmissions decreases as well.Thus the average loss probability monotonically decreases as NCBufTimeout increases.Although larger NCBufTimeout results in smaller loss probability,Figures 8(c),9(c)and 10(c)show that RTT increases linearly as NCBufTimeout increases.The average RTT depends on the hop distance of TCP path.The first two experiments have similar average RTT but the third experiment has a smaller average RTT with a smaller hop distance.In summary,network coding achieves significant throughput gain even with a small CR.In our exper-iments,we observed throughput gains from 20%to 70%.VI.C ONCLUSIONSIn this paper,we presented an implementation of network coding in a wireless mesh network and studied TCP throughput using measurements from our implementation.The distinguishing feature of our implementation is that it uses off-the-shelf hardware and software components and does not need any modifications to TCP or the MAC layer protocol while still being able to achieve significant throughput improvements compared to non-coding scenarios.We argued that the main factor improving TCP through-put is reduced packet loss thanks to network coding.To further improve TCP throughput and combat time synchronization issues,we implemented a timer at intermediate nodes to postpone the immediate transmission of packets.We then presented measurement results characterizing the relation between the timeout value and throughput improvement.In the future,we hope to develop an analytical model to capture the impact of network coding on TCP throughput.Such a model can be used to characterize the throughput benefit of network coding and study the effect of various control parameters such as the timeout value at intermediate nodes.We also plan to explore the use of multi-path TCP in WMNs employing network coding.A CKNOWLEDGEMENTSY .Huang and W.Gong were supported in part by NSF contract CNS 0519922,DMI-0330171and ANI 0319871.M.Ghaderi and D.Towsley were supported in part by DARPA CBMANET program.This research is continuing through participation in the International Technology Alliance sponsored by the U.S.Army Research Laboratory and the U.K.Ministry of Defence and was accomplished under Agreement Number W911NF-06-3-0001.The views and conclusions contained in this document are。