Mifare s50时序手册
- 格式:doc
- 大小:86.50 KB
- 文档页数:5


2002/01/10版本目录第一章RC500系统描述MIFARE 系统简介RC500系统结构及功能说明RC500系统安装用户系统开发步骤第二章RC500系统通信协议通信接口定义通信方式标准RS232通信协议TTL电平RS232通信协议LD自定义格式通信协议通信命令传输:两次握手协议第三章RC500系统操作命令模块操作命令卡片操作基础命令集卡片操作高级命令集第四章Advic32 函数动态链接库运行环境说明ADVIC32 动态库说明ADVIC32 常量定义ADVIC32 函数定义ADVIC32 函数详解附录一 RC500命令代码速查表附录二 RC500命令返回码表第一章RC500系统描述RC500系列MIFARE卡读写器/读写模块是本公司研制生产的智能卡读写器/读写模块系列产品之一。
它独立完成对MIFARE系列非接触卡的读写及控制操作,广泛应用于需以MIFARE卡作为存贮媒体的系统中。
它可以作为用户系统中的一部份,受控于主控制器,完成用户系统设定的对MIFARE卡片的所有操作。
用户应用本模块,能够简便地构成自己的智能卡应用产品。
1.1MIFARE系统简介近几年来,IC智能卡中的非接触式射频卡的安全保密、使用简便等特点使其在各领域的应用中异军突起,特别在民用系统(自动电表抄表系统、公交/地铁自动售票系统、企业“一卡通”、巡更保安系统等)中得到广泛的应用。
人们己愈来愈多开始接收和使用智能卡。
相信该领域的发展将越来越大。
MIFARE智能卡系统的核心是PHILIPS公司的MIFARE 1 S50系列晶片,该技术己被制定为国际标准:ISO/IEC 14443 TYPE A。
目前许多较大的IC卡卡片制造商的非接触卡制造均以MIFARE技术为标准。
MIFARE卡中包含一块ASIC微晶片和一个高频天线,其工作原理是:读写器中的MIFARE基站向MIFARE卡发一组固定频率()的电磁波,卡片内有一个LC串联谐振电路,其频率与基站发射的频率相同,在电磁波的激励下,LC谐振电路产生共振,从而使卡片内具有电荷,当所积累的电荷达到2V时,卡片中芯片将卡内数据发射出去或接收基站对卡片的操作。
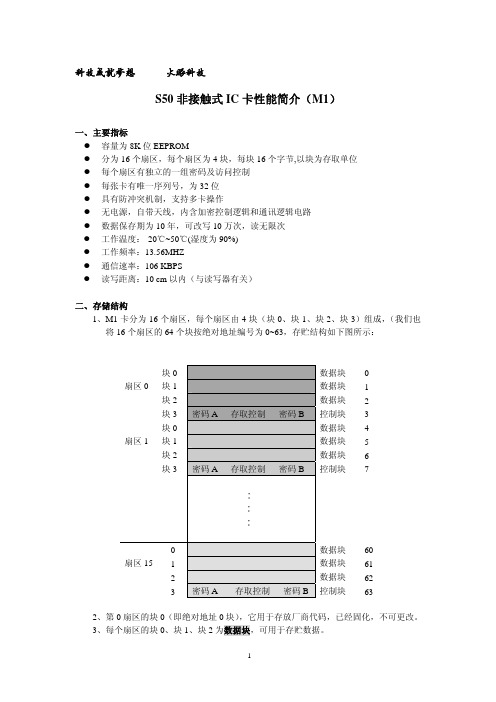
科技成就梦想 火眼科技S50非接触式IC卡性能简介(M1)一、 主要指标容量为8K位EEPROM分为16个扇区,每个扇区为4块,每块16个字节,以块为存取单位每个扇区有独立的一组密码及访问控制每张卡有唯一序列号,为32位具有防冲突机制,支持多卡操作无电源,自带天线,内含加密控制逻辑和通讯逻辑电路数据保存期为10年,可改写10万次,读无限次工作温度:-20℃~50℃(湿度为90%)工作频率:13.56MHZ通信速率:106 KBPS读写距离:10 cm以内(与读写器有关)二、 存储结构1、M1卡分为16个扇区,每个扇区由4块(块0、块1、块2、块3)组成,(我们也将16个扇区的64个块按绝对地址编号为0~63,存贮结构如下图所示:块0 数据块0扇区0 块1 数据块 1块2 数据块 2块3 密码A 存取控制密码B 控制块 3块0 数据块 4扇区1 块1 数据块 5块2 数据块 6块3 密码A 存取控制密码B 控制块7∶∶∶0 数据块60扇区15 1 数据块612 数据块623 密码A 存取控制密码B控制块632、第0扇区的块0(即绝对地址0块),它用于存放厂商代码,已经固化,不可更改。
3、每个扇区的块0、块1、块2为数据块,可用于存贮数据。
数据块可作两种应用:★ 用作一般的数据保存,可以进行读、写操作。
★ 用作数据值,可以进行初始化值、加值、减值、读值操作。
4、每个扇区的块3为控制块,包括了密码A、存取控制、密码B。
具体结构如下:密码A(6字节)存取控制(4字节)密码B(6字节)5、每个扇区的密码和存取控制都是独立的,可以根据实际需要设定各自的密码及存取控制。
存取控制为4个字节,共32位,扇区中的每个块(包括数据块和控制块)的存取条件是由密码和存取控制共同决定的,在存取控制中每个块都有相应的三个控制位,定义如下:块0: C10 C20 C30块1: C11 C21 C31块2: C12 C22 C32块3: C13 C23 C33三个控制位以正和反两种形式存在于存取控制字节中,决定了该块的访问权限(如进行减值操作必须验证KEY A,进行加值操作必须验证KEY B,等等)。
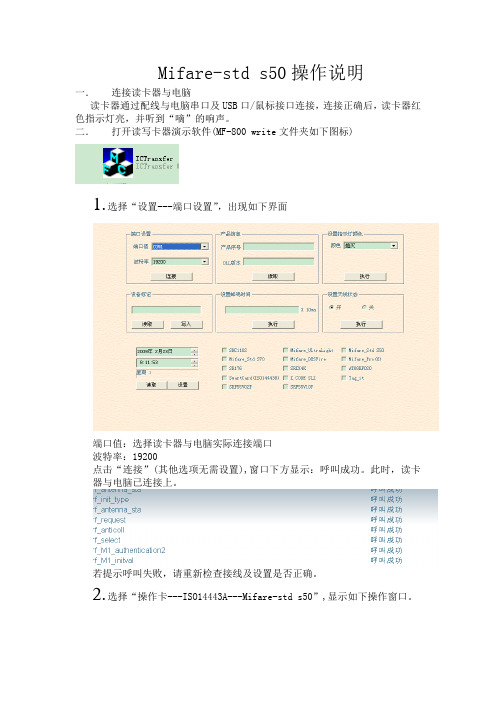
Mifare-std s50操作说明
一.连接读卡器与电脑
读卡器通过配线与电脑串口及USB口/鼠标接口连接,连接正确后,读卡器红色指示灯亮,并听到“嘀”的响声。
二.打开读写卡器演示软件(MF-800 write文件夹如下图标)
1.选择“设置---端口设置”,出现如下界面
端口值:选择读卡器与电脑实际连接端口
波特率:19200
点击“连接”(其他选项无需设置),窗口下方显示:呼叫成功。
此时,读卡器与电脑已连接上。
若提示呼叫失败,请重新检查接线及设置是否正确。
2.选择“操作卡---ISO14443A---Mifare-std s50”,显示如下操作窗口。
将IC卡置于读卡器,选择“寻卡.ALL”,窗口下方提示“呼叫成功”。
设置钱包功能:在钱包功能窗口进行如下设置:扇区号:0;块号:2;A.密匙:ffffffffffff ;
初始化钱包操作(IC卡首次使用时需要进行此操作):金额(十进制):0,点击“初始化”,提示:初始化钱包操作成功。
初始化成功后可对IC卡进行“充值” “扣款” “读余额”的操作。
“充值”操作
金额(十进制):填写要充值的数目(IC卡可用次数),点击“充值“,对IC卡进行充值,窗口下方提示:呼叫成功,已成功充值。
充值成功后,可点击“读余额“,查看卡内余额。
操作窗口操作
操作窗口进行如下设置:扇区号:0;块号:1;A.密匙:ffffffffffff ;点击“读卡”,然后把第二个栏里的数据改成0902********后面全是0,然后点击“写卡”提示:“写卡成功”即完成操作。

文军维修 Mifare1卡及其读写器ASIC 模块之“密码操作”研究与其应用程序开发作者: 张敏2001-8-4关键字: 非接触式智能卡 ASIC 模块1、序言 非接触式智能卡已经广泛地应用于各类门禁控制系统,公共交通支付系统,e -purse 系统,高速公路不停车收费系统,IBMS (智能大楼管理系统),海关过境身份识别,以及医疗保险系统等等。
非接触式智能卡以其高度安全保密性,通信高速性,使用方便性,成本日渐低廉等而受到广泛使用,给我们的生活质量带来了很大的提高。
因此,如何认识、理解智能卡,特别是带有非常神秘色彩的非接触式智能卡,已引起很多智能卡的使用者,包括智能卡专业研发的IT 科研人员的极大的兴趣和爱好。
笔者在此很愿意将自己多年来在智能卡(接触式智能卡及非接触式智能卡)方面的研究及其软硬件应用开发的经验与大家一同交流和分享,以取得我国金卡工程事业的更进一步的发展。
在此,笔者将以符合ISO/IEC14443TYPEA 标准的Mifare1S50系列非接触式智能卡及其读写设备专用IC (ASIC )RC150/170模块为对象,与大家一起就“关于非接触式智能卡及其读写器ASIC 模块之‘密码操作’”作一些研究与探讨,并将用标准的Intel -51系列微处理器汇编语言进行实际的应用程序的开发。
在笔者曾设计和开发的众多智能卡项目中,本文所给出的应用程序都有着良好的运行效果。
2、非接触式智能卡及其读写器ASIC 模块RC150/170 Mifare1S50非接触式智能卡片有着16个Sector(扇区);每个Sector 包含4个Block (块);每个Block 具有16个byte 的存储容量。
Sector 被定义为Sector0至Sector15;Block 被分为Block0至Block3;整个Mifare1S50非接触式智能卡共有64个Block 。
Sector0中的Block0记录了该张智能卡的序列号(SerialNumber )以及生产厂商的标志信息等,这些信息已在卡片出厂时固化,不能更改。

非接触式IC卡Mifare S50卡详细介绍一、何谓RFID与非接触式IC卡(Contactless Samrt Card)RFID (Radio Frequency Identification)常称为感应式电子晶片或近接卡、感应卡、非接触智能卡、非接触IC卡等等。
一套完整RFID系统由Reader 与Transponder两部分组成,其动作原理为由Re ader发射一特定频率之无线电波能量给Transponder,用以驱动Transponder 电路将内部之ID Code送出,此时Reader便接收此ID Code。
Transponder的特殊在于免用电池、免接触、免刷卡故不怕脏污,且晶片密码为世界唯一无法复制COPY,安全性高、长寿命。
RFID的产品有电容式(Capacatine)、微波式(Microwave)、无线电频率RF(R adioFrequency),因电容式在使用时须与CSC验票机几乎贴近才能感应,而微波式则须与CSC验票机直线对准,只有无线电频率式则无此限制,所以目前CSC 的主流卡片是飞利浦的MIFAER卡片,其材质采用无线电频率式;而以无线电频率不含电池之CSC,其动作原理是经由内部RF天线接收由读写器所发送出来之电波,感应出一微小电源电压来供应内部电路及读写器所需之电力,亦藉由此感应电压来读写、运算、储存卡片内记忆体资料或藉由读写器和外界接触,并进行卡片和读写器彼此间之资料之交换;其卡片特性概述如下:1、尺寸:信用卡尺寸86mm*54mm*0.76mm。
2、外型:坚固、防潮、不易弯曲变形。
3、电池:无内部电池。
4、读写距离:与读写单元间距离2-10CM内均可正确读写资料。
5、读写角度:与读写单元上方半球幅度内均可正确读写资料。
6、运输方式:无线电调频通信方式。
7、内部构造:固态电子装置(Solid-state Electric Device),有内藏记忆体、微处理器晶片两种形式。


科技成就梦想 火眼科技S50非接触式IC 卡性能简介(M1)一、 主要指标容量为8K 位EEPROM分为16个扇区,每个扇区为4块,每块16个字节,以块为存取单位 每个扇区有独立的一组密码及访问控制 每张卡有唯一序列号,为32位 具有防冲突机制,支持多卡操作无电源,自带天线,内含加密控制逻辑和通讯逻辑电路 数据保存期为10年,可改写10万次,读无限次 工作温度:-20℃~50℃(湿度为90%) 工作频率:13.56MHZ 通信速率:106 KBPS读写距离:10 cm 以内(与读写器有关)二、 存储结构1、M1卡分为16个扇区,每个扇区由4块(块0、块1、块2、块3)组成,(我们也将16个扇区的64个块按绝对地址编号为0~63,存贮结构如下图所示:块0 数据块 0 扇区0 块1数据块 1 块2数据块 2 块3 密码A 存取控制 密码B 控制块 3 块0 数据块 4 扇区1 块1 数据块 5 块2数据块 6 块3 密码A 存取控制 密码B 控制块 7∶ ∶ ∶0 数据块 60 扇区15 1数据块 61 2数据块 623密码A 存取控制 密码B控制块632、第0扇区的块0(即绝对地址0块),它用于存放厂商代码,已经固化,不可更改。
3、每个扇区的块0、块1、块2为数据块,可用于存贮数据。
Edited by Foxit ReaderCopyright(C) by Foxit Software Company,2005-2008For Evaluation Only.数据块可作两种应用:★ 用作一般的数据保存,可以进行读、写操作。
★ 用作数据值,可以进行初始化值、加值、减值、读值操作。
4、每个扇区的块3为控制块,包括了密码A、存取控制、密码B。
具体结构如下:密码A(6字节)存取控制(4字节)密码B(6字节)5、每个扇区的密码和存取控制都是独立的,可以根据实际需要设定各自的密码及存取控制。
存取控制为4个字节,共32位,扇区中的每个块(包括数据块和控制块)的存取条件是由密码和存取控制共同决定的,在存取控制中每个块都有相应的三个控制位,定义如下:块0: C10 C20 C30块1: C11 C21 C31块2: C12 C22 C32块3: C13 C23 C33三个控制位以正和反两种形式存在于存取控制字节中,决定了该块的访问权限(如进行减值操作必须验证KEY A,进行加值操作必须验证KEY B,等等)。

非接触式IC卡Mifare S50卡详细介绍一、何谓RFID与非接触式IC卡(Contactless Samrt Card)RFID (Radio Frequency Identification)常称为感应式电子晶片或近接卡、感应卡、非接触智能卡、非接触IC卡等等。
一套完整RFID系统由Reader 与Transponder两部分组成,其动作原理为由Re ader发射一特定频率之无线电波能量给Transponder,用以驱动Transponder 电路将内部之ID Code送出,此时Reader便接收此ID Code。
Transponder的特殊在于免用电池、免接触、免刷卡故不怕脏污,且晶片密码为世界唯一无法复制COPY,安全性高、长寿命。
RFID的产品有电容式(Capacatine)、微波式(Microwave)、无线电频率RF(R adioFrequency),因电容式在使用时须与CSC验票机几乎贴近才能感应,而微波式则须与CSC验票机直线对准,只有无线电频率式则无此限制,所以目前CSC 的主流卡片是飞利浦的MIFAER卡片,其材质采用无线电频率式;而以无线电频率不含电池之CSC,其动作原理是经由内部RF天线接收由读写器所发送出来之电波,感应出一微小电源电压来供应内部电路及读写器所需之电力,亦藉由此感应电压来读写、运算、储存卡片内记忆体资料或藉由读写器和外界接触,并进行卡片和读写器彼此间之资料之交换;其卡片特性概述如下:1、尺寸:信用卡尺寸86mm*54mm*0.76mm。
2、外型:坚固、防潮、不易弯曲变形。
3、电池:无内部电池。
4、读写距离:与读写单元间距离2-10CM内均可正确读写资料。
5、读写角度:与读写单元上方半球幅度内均可正确读写资料。
6、运输方式:无线电调频通信方式。
7、内部构造:固态电子装置(Solid-state Electric Device),有内藏记忆体、微处理器晶片两种形式。

MF1ICS50Functional specificationRev. 5.3 — 29 January 2008Product data sheet001053PUBLIC 1.General descriptionNXP has developed the MIFARE MF1ICS50 to be used in a contactless smart cardaccording to ISO/IEC 14443 Type A.The MIFARE MF1ICS50 IC is used in applications like public transport ticketing wheremajor cities have adopted MIFARE as their e-ticketing solution of choice.1.1Key applications•Public transportation•Access control•Event ticketing•Gaming & identity1.2AnticollisionAn intelligent anticollision function allows to operate more than one card in the fieldsimultaneously. The anticollision algorithm selects each card individually and ensures thatthe execution of a transaction with a selected card is performed correctly without datacorruption resulting from other cards in the field.MIFARE card reader1.3Simple integration and user convenienceThe MF1ICS50 is designed for simple integration and user convenience. Which couldallow complete ticketing transactions to be handled in less than 100 ms. Thus, theMF1ICS50card user is not forced to stop at the reader leading to a high throughput atgates and reduced boarding times onto busses. The MIFARE card may also remain in thewallet during the transaction, even if there are coins in it.1.4SecuritySeveral security measures like mutual challenge and response authentication, dataciphering and message authentication checks support the protection of the systemagainst various attack scenarios. The UID of the IC as a base of key diversificationsupports the security concept.1.5Delivery options•Die on wafer•Bumped die on wafer•MOA4 or MOA2 contactless card module•Flip chip package2.Features2.1MIFARE‚ RF Interface (ISO/IEC 14443 A)Contactless transmission of data and supply energy (no battery needed)Operating distance: Up to 100mm (depending on antenna geometry)Operating frequency: 13.56 MHzData transfer: 106 kbit/sData integrity: 16 Bit CRC, parity, bit coding, bit countingAnticollisionTypical ticketing transaction: < 100 ms (including backup management)2.2EEPROM1 Kbyte, organized in 16 sectors with 4 blocks of 16 bytes each (one block consists of16 byte)User definable access conditions for each memory blockData retention of 10 years.Write endurance 100.000 cycles2.3SecurityMutual three pass authentication (ISO/IEC DIS 9798-2)Individual set of two keys per sector (per application) to support multi-application with key hierarchyUnique serial number for each device3.Ordering informationSee Delivery Type Addendum of Device 4.Block diagram5.Pinning information5.1PinningSee Delivery Type Addendum of Device6.Functional description6.1Block descriptionThe MF1ICS50 chip consists of the 1 Kbyte EEPROM, the RF-Interface and the DigitalControl Unit. Energy and data are transferred via an antenna, which consists of a coil witha few turns directly connected to the MF1ICS50. No further external components arenecessary. (For details on antenna design please refer to the document MIFARE‚ Card ICCoil Design Guide.)•RF-Interface:–Modulator/Demodulator–Rectifier–Clock Regenerator–Power On Reset–Voltage Regulator•Anticollision: Several cards in the field may be selected and operated in sequence•Authentication: Preceding any memory operation the authentication procedureensures that access to a block is only possible via the two keys specified for eachblock•Control & Arithmetic Logic Unit: Values are stored in a special redundant format and can be incremented and decremented•EEPROM-Interface•Crypto unit: The CRYPTO1 stream cipher of the MF1ICS50 is used for authentication and enchryption of data exchange.•EEPROM: 1 Kbyte is organized in 16 sectors with 4 blocks each. A block contains16bytes. The last block of each sector is called “trailer”, which contains two secretkeys and programmable access conditions for each block in this sector.6.2Communication principleThe commands are initiated by the reader and controlled by the Digital Control Unit of theMF1ICS50 according to the access conditions valid for the corresponding sector.6.2.1Request standard/ allAfter Power On Reset (POR) of a card it can answer to a request command - sent by thereader to all cards in the antenna field - by sending the answer to request code (ATQAaccording to ISO/IEC 14443A).6.2.2Anticollision loopIn the anticollision loop the serial number of a card is read. If there are several cards in theoperating range of the reader, they can be distinguished by their unique serial numbersand one can be selected (select card) for further transactions. The unselected cardsreturn to the standby mode and wait for a new request command.6.2.3Select cardWith the select card command the reader selects one individual card for authenticationand memory related operations. The card returns the Answer To Select (ATS) code(= 08h), which determines the type of the selected card. Please refer to the documentMIFARE‚Standardized Card Type Identification Procedure for further details.6.2.4Three pass authenticationAfter selection of a card the reader specifies the memory location of the following memory access and uses the corresponding key for the three pass authentication procedure. Aftera successful authentication all memory operations are encrypted.6.2.5Memory operationsAfter authentication any of the following operations may be performed:•Read block•Write block•Decrement: Decrements the contents of a block and stores the result in a temporary internal data-register•Increment: Increments the contents of a block and stores the result in the data-register•Restore: Moves the contents of a block into the data-register•Transfer: Writes the contents of the temporary internal data-register to a value block6.3Data integrityFollowing mechanisms are implemented in the contactless communication link between reader and card to ensure very reliable data transmission:•16 bits CRC per block•Parity bits for each byte•Bit count checking•Bit coding to distinguish between "1", "0", and no information•Channel monitoring (protocol sequence and bit stream analysis)6.4Three pass authentication sequence1.The reader specifies the sector to be accessed and chooses key A or B.2.The card reads the secret key and the access conditions from the sector trailer. Thenthe card sends a random number as the challenge to the reader (pass one).3.The reader calculates the response using the secret key and additional input. Theresponse, together with a random challenge from the reader, is then transmitted to thecard (pass two).4.The card verifies the response of the reader by comparing it with its own challengeand then it calculates the response to the challenge and transmits it (pass three).5.The reader verifies the response of the card by comparing it to its own challenge.After transmission of the first random challenge the communication between card andreader is encrypted.6.5RF interfaceThe RF-interface is according to the standard for contactless smart cardsISO/IEC14443A.The carrier field from the reader is always present (with short pauses when transmitting), because it is used for the power supply of the card.For both directions of data communication there is only one start bit at the beginning of each frame. Each byte is transmitted with a parity bit (odd parity) at the end. The LSB of the byte with the lowest address of the selected block is transmitted first. The maximum frame length is 163 bits (16 data bytes + 2 CRC bytes = 16 * 9 + 2 * 9 + 1 start bit).6.6Memory organizationThe 1024 x 8 bit EEPROM memory is organized in 16 sectors with 4 blocks of 16 bytes each. In the erased state the EEPROM cells are read as a logical “0”, in the written state as a logical “1”.6.6.1Manufacturer blockThis is the first data block (block 0) of the first sector (sector 0). It contains the ICmanufacturer data. Due to security and system requirements this block is write protected after having been programmed by the IC manufacturer at production.6.6.2Data blocksAll sectors contain 3 blocks of 16 bytes for storing data (Sector 0 contains only two datablocks and the read-only manufacturer block).The data blocks can be configured by the access bits as•read/write blocks for e.g. contactless access control or•value blocks for e.g. electronic purse applications, where additional commands like increment and decrement for direct control of the stored value are provided.An authentication command has to be carried out before any memory operation in order to allow further commands.6.6.2.1Value BlocksThe value blocks allow to perform electronic purse functions (valid commands: read, write, increment, decrement, restore, transfer).The value blocks have a fixed data format which permits error detection and correction and a backup management.A value block can only be generated through a write operation in the value block format:•Value: Signifies a signed 4-byte value. The lowest significant byte of a value is stored in the lowest address byte. Negative values are stored in standard 2´s complementformat. For reasons of data integrity and security, a value is stored three times, twicenon-inverted and once inverted.•Adr: Signifies a 1-byte address, which can be used to save the storage address of a block, when implementing a powerful backup management. The address byte isstored four times, twice inverted and non-inverted. During increment, decrement,restore and transfer operations the address remains unchanged. It can only bealtered via a write command.6.6.3Sector trailer (block 3)Each sector has a sector trailer containing the•secret keys A and B (optional), which return logical “0”s when read and•the access conditions for the four blocks of that sector, which are stored in bytes 6...9.The access bits also specify the type (read/write or value) of the data blocks.If key B is not needed, the last 6 bytes of block 3 can be used as data bytes.Byte 9 of the sector trailer is available for user data. For this byte apply the same access rights as for byte 6, 7 and 8.6.7Memory accessBefore any memory operation can be carried out, the card has to be selected andauthenticated as described previously.The possible memory operations for an addressed block depend on the key used and the access conditions stored in the associated sector trailer.Table 1.Memory operationsOperation Description Valid for Block TypeRead reads one memory block read/write, value and sectortrailerWrite writes one memory block read/write, value and sectortrailervalueIncrement increments the contents of ablock and stores the result inthe internal data registervalueDecrement decrements the contents of ablock and stores the result inthe internal data registervalueTransfer writes the contents of theinternal data register to a blockRestore reads the contents of a blockvalueinto the internal data register6.7.1Access conditionsThe access conditions for every data block and sector trailer are defined by 3 bits, whichare stored non-inverted and inverted in the sector trailer of the specified sector.The access bits control the rights of memory access using the secret keys A and B. Theaccess conditions may be altered, provided one knows the relevant key and the currentaccess condition allows this operation.Remark: With each memory access the internal logic verifies the format of the accessconditions. If it detects a format violation the whole sector is irreversible blocked.Remark: In the following description the access bits are mentioned in the non-invertedmode only.The internal logic of the MF1ICS50 ensures that the commands are executed only after anauthentication procedure or never.Table 2.Access conditionsAccess Bits Valid Commands Block DescriptionC13 C23 C33read, write→3sector trailer→2data blockC12 C22 C32read, write, increment, decrement,transfer, restore→1data blockC11 C21 C31read, write, increment, decrement,transfer, restoreC10 C20 C30read, write, increment, decrement,→0data blocktransfer, restoreFig 9.Access conditions6.7.2Access conditions for the sector trailerDepending on the access bits for the sector trailer (block 3) the read/write access to the keys and the access bits is specified as ‘never’, ‘key A’, ‘key B’ or key A|B’ (key A or key B).On chip delivery the access conditions for the sector trailers and key A are predefined as transport configuration. Since key B may be read in transport configuration, new cards must be authenticated with key A. Since the access bits themselves can also be blocked, special care should be taken during personalization of cards.Remark: the grey marked lines are access conditions where key B is readable and may be used for data.Table 3.Access conditions for the sector trailerAccess bits Access condition for RemarkKEYAAccess bitsKEYB C1C2C3read write read write read write 000never key A key A never key A key A Key B may be read 010never never key A never key A never Key B may be read100never key B key A|B never never key B 110never never key A|B never never never 001never key A key A key A key A key A Key B may be read,transport configuration 011never key B key A|B key B never key B 101never never key A|B key B never never 111neverneverkey A|Bnevernevernever6.7.3Access conditions for data blocksDepending on the access bits for data blocks (blocks 0...2) the read/write access isspecified as ‘never’, ‘key A’, ‘key B’ or ‘key A|B’ (key A or key B). The setting of therelevant access bits defines the application and the corresponding applicable commands.•Read/write block: The operations read and write are allowed.•Value block: Allows the additional value operations increment, decrement, transfer and restore. In one case (‘001’) only read and decrement are possible for anon-rechargeable card. In the other case (‘110’) recharging is possible by using key B.•Manufacturer block: The read-only condition is not affected by the access bits setting!•Key management: In transport configuration key A must be used for authentication1Table 4.Access conditions for data blocksAccess bits Access condition for ApplicationC1C2C3read write increment decrement,transfer,restore000key A|B[1]key A|B1key A|B1key A|B1transportconfiguration 010key A|B[1]never never never read/write block100key A|B[1]key B1never never read/write block110key A|B[1]key B1key B1key A|B1value block001key A|B[1]never never key A|B1value block011key B[1]key B1never never read/write block101key B[1]never never never read/write block111never never never never read/write block[1]if Key B may be read in the corresponding Sector Trailer it cannot serve for authentication (all grey markedlines in previous table). Consequences: If the reader tries to authenticate any block of a sector with key Busing grey marked access conditions, the card will refuse any subsequent memory access afterauthentication.1.If Key B may be read in the corresponding Sector Trailer it cannot serve for authentication (all grey marked lines in previous table). Consequences: If the RDW tries to authenticate any block of a sector with key B using grey marked access conditions, the card will refuse any subsequent access after authentication.7.Limiting valuesSee Delivery Type Addendum of Device 8.Recommended operating conditionsSee Delivery Type Addendum of Device 9.CharacteristicsSee Delivery Type Addendum of Device 10.Support informationFor additional information, please visit: 11.Package outlineSee Delivery Type Addendum of Device12.Revision historyTable 5.Revision historyDocument ID Release date Data sheet status Change notice Supersedes 00105329 January 2008Product data sheet 5.2 Modifications:•Update•General rewording of MIFARE designation and commercialconditions00105215 January 2007Product data sheet 5.1 Modifications:•The format of this data sheet has been redesigned to comply with the new identityguidelines of NXP Semiconductors.•Legal texts have been adapted to the new company name.13.Legal information13.1Data sheet status[1]Please consult the most recently issued document before initiating or completing a design. [2]The term ‘short data sheet’ is explained in section “Definitions”.[3]The product status of device(s) described in this document may have changed since this document was published and may differ in case of multiple devices. The latest product status information is available on the Internet at URL .13.2DefinitionsDraft — The document is a draft version only. The content is still under internal review and subject to formal approval, which may result in modifications or additions. NXP Semiconductors does not give any representations or warranties as to the accuracy or completeness ofinformation included herein and shall have no liability for the consequences of use of such information.Short data sheet — A short data sheet is an extract from a full data sheet with the same product type number(s) and title. A short data sheet is intended for quick reference only and should not be relied upon to contain detailed and full information. For detailed and full information see the relevant full data sheet, which is available on request via the local NXP Semiconductors sales office. In case of any inconsistency or conflict with the short data sheet, the full data sheet shall prevail.13.3DisclaimersGeneral — Information in this document is believed to be accurate andreliable. However, NXP Semiconductors does not give any representations or warranties, expressed or implied, as to the accuracy or completeness of such information and shall have no liability for the consequences of use of such information.Right to make changes — NXP Semiconductors reserves the right to make changes to information published in this document, including withoutlimitation specifications and product descriptions, at any time and without notice. This document supersedes and replaces all information supplied prior to the publication hereof.Suitability for use — NXP Semiconductors products are not designed, authorized or warranted to be suitable for use in medical, military, aircraft, space or life support equipment, nor in applications where failure ormalfunction of a NXP Semiconductors product can reasonably be expected toresult in personal injury, death or severe property or environmental damage. NXP Semiconductors accepts no liability for inclusion and/or use of NXP Semiconductors products in such equipment or applications and therefore such inclusion and/or use is at the customer’s own risk.Applications — Applications that are described herein for any of these products are for illustrative purposes only. NXP Semiconductors makes no representation or warranty that such applications will be suitable for the specified use without further testing or modification.Limiting values — Stress above one or more limiting values (as defined in the Absolute Maximum Ratings System of IEC 60134) may cause permanent damage to the device. Limiting values are stress ratings only and operation of the device at these or any other conditions above those given in theCharacteristics sections of this document is not implied. Exposure to limiting values for extended periods may affect device reliability.Terms and conditions of sale — NXP Semiconductors products are sold subject to the general terms and conditions of commercial sale, as published at /profile/terms , including those pertaining to warranty, intellectual property rights infringement and limitation of liability, unlessexplicitly otherwise agreed to in writing by NXP Semiconductors. In case of any inconsistency or conflict between information in this document and such terms and conditions, the latter will prevail.No offer to sell or license — Nothing in this document may be interpreted or construed as an offer to sell products that is open for acceptance or the grant, conveyance or implication of any license under any copyrights, patents or other industrial or intellectual property rights.13.4TrademarksNotice: All referenced brands, product names, service names and trademarks are the property of their respective owners.MIFARE — is a trademark of NXP B.V.14.Contact informationFor additional information, please visit: For sales office addresses, send an email to: salesaddresses@Document status [1][2]Product status [3]DefinitionObjective [short] data sheet Development This document contains data from the objective specification for product development. Preliminary [short] data sheet Qualification This document contains data from the preliminary specification. Product [short] data sheetProductionThis document contains the product specification.15.TablesTable 1.Memory operations. . . . . . . . . . . . . . . . . . . . . .11 Table 2.Access conditions. . . . . . . . . . . . . . . . . . . . . . .12 Table 3.Access conditions for the sector trailer. . . . . .13Table 4.Access conditions for data blocks . . . . . . . . . .14 Table 5.Revision history. . . . . . . . . . . . . . . . . . . . . . . .1616.FiguresFig 1.MIFARE card reader . . . . . . . . . . . . . . . . . . . . . . .1Fig 2.Block diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . .3Fig 3.Three pass authentication . . . . . . . . . . . . . . . . . . .5Fig 4.Memory organization. . . . . . . . . . . . . . . . . . . . . . .7Fig 5.Manufacturer block . . . . . . . . . . . . . . . . . . . . . . . .8Fig 6.Value blocks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9Fig 7.Sector trailer . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9Fig 8.Memory access . . . . . . . . . . . . . . . . . . . . . . . . . .10Fig 9.Access conditions . . . . . . . . . . . . . . . . . . . . . . . .12continued >>© NXP B.V.2008.All rights reserved.For more information, please visit: For sales office addresses, please send an email to: salesaddresses@Please be aware that important notices concerning this document and the product(s)described herein, have been included in section ‘Legal information’.17.Contents1General description. . . . . . . . . . . . . . . . . . . . . . 11.1Key applications . . . . . . . . . . . . . . . . . . . . . . . . 11.2Anticollision. . . . . . . . . . . . . . . . . . . . . . . . . . . . 11.3Simple integration and user convenience. . . . . 21.4Security. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21.5Delivery options . . . . . . . . . . . . . . . . . . . . . . . . 22Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22.1MIFARE‚ RF Interface (ISO/IEC 14443 A) . . . . 22.2EEPROM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22.3Security. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23Ordering information. . . . . . . . . . . . . . . . . . . . . 34Block diagram . . . . . . . . . . . . . . . . . . . . . . . . . . 35Pinning information. . . . . . . . . . . . . . . . . . . . . . 35.1Pinning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36Functional description . . . . . . . . . . . . . . . . . . . 46.1Block description . . . . . . . . . . . . . . . . . . . . . . . 46.2Communication principle . . . . . . . . . . . . . . . . . 46.2.1Request standard/ all . . . . . . . . . . . . . . . . . . . . 46.2.2Anticollision loop. . . . . . . . . . . . . . . . . . . . . . . . 46.2.3Select card . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56.2.4Three pass authentication . . . . . . . . . . . . . . . . 56.2.5Memory operations. . . . . . . . . . . . . . . . . . . . . . 66.3Data integrity. . . . . . . . . . . . . . . . . . . . . . . . . . . 66.4Three pass authentication sequence . . . . . . . . 66.5RF interface . . . . . . . . . . . . . . . . . . . . . . . . . . . 76.6Memory organization . . . . . . . . . . . . . . . . . . . . 76.6.1Manufacturer block. . . . . . . . . . . . . . . . . . . . . . 86.6.2Data blocks. . . . . . . . . . . . . . . . . . . . . . . . . . . . 86.6.2.1Value Blocks. . . . . . . . . . . . . . . . . . . . . . . . . . . 86.6.3Sector trailer (block 3) . . . . . . . . . . . . . . . . . . . 96.7Memory access . . . . . . . . . . . . . . . . . . . . . . . 106.7.1Access conditions. . . . . . . . . . . . . . . . . . . . . . 126.7.2Access conditions for the sector trailer. . . . . . 136.7.3Access conditions for data blocks. . . . . . . . . . 147Limiting values. . . . . . . . . . . . . . . . . . . . . . . . . 158Recommended operating conditions. . . . . . . 159Characteristics. . . . . . . . . . . . . . . . . . . . . . . . . 1510Support information . . . . . . . . . . . . . . . . . . . . 1511Package outline . . . . . . . . . . . . . . . . . . . . . . . . 1512Revision history. . . . . . . . . . . . . . . . . . . . . . . . 1613Legal information. . . . . . . . . . . . . . . . . . . . . . . 1713.1Data sheet status . . . . . . . . . . . . . . . . . . . . . . 1713.2Definitions. . . . . . . . . . . . . . . . . . . . . . . . . . . . 1713.3Disclaimers. . . . . . . . . . . . . . . . . . . . . . . . . . . 1713.4Trademarks. . . . . . . . . . . . . . . . . . . . . . . . . . . 1714Contact information . . . . . . . . . . . . . . . . . . . . 1715Tables. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1816Figures. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1817Contents. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19。



1. Mifare_Std 卡片的密钥属性取决于控制字。
控制字的默认值是“FF078069”,此时A密钥:不可被读出,有全部权限 B密钥:可被读出,没有任何权限2. Philips/NXP在2001年对S50芯片有重要更新:当B密钥可以被读出时,B密钥失效。
关于这一点请仔细阅读关于这一点请仔细阅读S50 DATASHEET S50 DATASHEET 的第的第151515页页2000年以前的卡片以及大陆地区仿制的卡片不具备此功能 3. 如果使用的是PHILIPS原始芯片的卡片,且控制字 = FF078069时,通过某台读卡器进行B密钥验证后可读写卡片,说明这台读卡器有BUG。
最大的可能性是这个读卡器并不区分AB密钥。
我们可以做个简单的实验,将AB密钥设为不同的值,例如首先将密钥BLOCK改写为如下:111111111111 FF078069222222222222 此时KeyA = 111111111111, KeyB = 222222222222然后用您所说的可以通过B密钥读写的读卡器进行操作,就会发现问题所在4. 在大多数使用B密钥的系统中,控制字 = 08778F00,此时A密钥:不可被读出,有读取数据可扣款权限 B密钥:不可被读出,有全部权限1.裝原的Philps S50廠廠廠個區塊晶片在出置每分的的第四A 鑰密是:“FFFFFFFFFFFF”,控制字是:“FF078069”,B 鑰密是:“FFFFFFFFFFFF”,A 鑰戶戶戶密是供用操作的,利用A 鑰對對密可除0區區塊區戶戶外其它所有扇行操作。
B 鑰這密不可操作,些用的都是邏邏鑰見們戶廠加密算法加密,而且密都是不可,我在能看到的A密鑰顯為都是示“000000000000”,B 鑰顯密示:“FFFFFFFFFFFF”, 這廠廠廠廠認些都是出家定的默值。
2.戶如果用要使用B 鑰間密,如“公交一卡通的公交卡”,那先要把中控制改錯個區沒了,如果改那所改的那分就被加密用了。

卡片系列介绍之——M1(S50、S70)卡片卡片简介S50、S70属于NXP 的MF1系列卡片,是NXP 公司生产的一种大容量逻辑存储标签芯片。
该系列标签存储容量有1K 和4K 两种,且卡片有密码保护功能,所以较M0系列卡片而言安全性更高。
存储结构S50卡内部为1Kbtyes 存储空间,而S70卡则为4Kbytes 。
其中S50卡的存储结构如图 1所示卡片内部以扇区为单位,卡片共有16个扇区,每个扇区共有4个块,每块有16字节。
所以卡片共有16x4x16=1024字节,总容量1K 。
S70卡则与S50卡略微有些不同,在S70卡中,共有40个扇区,其中前32个扇区与S50卡的结构完全相同都是一个扇区4块,而后8个扇区则是每个扇区16个块,所以S70卡的总容量为32x4x16+8x16x16=4096(4Kbytes )。
如图 2所示每个扇区都有一个独立的访问密钥,在对扇区的块进行读写前需要先验证密钥,验证通过后才能开启读写权限。
图 2 扇区结构图 1 S50卡片结构扇区0是卡片中最特殊的一个扇区,因为此扇区的第0块是卡片厂商固化的一些信息,不可更改,其中就包括了卡片的UID,如图3所示SN0~SN3则为卡片的4字节ID号。
依据ISO/IEC14443-3, 其校验位BCC 计算如下:BCC=SN0 ⊕SN1 ⊕SN2⊕SN3 。
图 3 厂商块定义应用实例M1卡因为其容量大、价格便宜的特点在市场中有着广泛的应用,如门禁、考勤、物流、校园卡、会员卡、公交卡、电子门票等多种场合。
卡片操作流程以我公司ZLG600SP/T为例操作S50卡的流程如下:数据读写操作:1、发送:08 02 4D 02 00 26 9C 03(卡激活命令)模块回应:0E 02 00 08 04 00 08 04 1C1C DD A6 88 03解释:参看ZLG600SP/T模块用户手册对该命令的说明可知卡片返回的ATQ=0x0004;而SAK=0x08,卡片的UID=0xA6DD1C1C。




MiFare_one卡介绍MiFare one卡介绍⼀、Mifare one IC S50 主要指标●容量为8K位EEPROM●分为16个扇区,每个扇区为4块,每块16个字节,以块为存取单位●每个扇区有独⽴的⼀组密码及访问控制●每张卡有唯⼀序列号,为32位●具有防冲突机制,⽀持多卡操作●⽆电源,⾃带天线,内含加密控制逻辑和通讯逻辑电路●数据保存期为10年,可改写10万次,读⽆限次●⼯作温度:-20℃~50℃(湿度为90%)●⼯作频率:13.56MHZ●通信速率:106 KBPS●读写距离:10 cm以内(与读写器有关)⼆、Mifare one IC S70 主要指标●容量为32K位EEPROM●分为40个扇区,其中32个扇区中每个扇区存储容量为64个字节,分为4块,每块16个字节;8个扇区中每个扇区存储容量为256个字节,分为16块,每块16个字节;以块为存取单位●每个扇区有独⽴的⼀组密码及访问控制●每张卡有唯⼀序列号,为32位●具有防冲突机制,⽀持多卡操作●⽆电源,⾃带天线,内含加密控制逻辑和通讯逻辑电路●数据保存期为10年,可改写10万次,读⽆限次●⼯作温度:-20℃~50℃(湿度为90%)●⼯作频率:13.56MHZ●通信速率:106 KBPS●读写距离:10 cm以内(与读写器有关)三、M1射频卡与读写器的通讯见下图⽰:四、⼯作原理卡⽚的电⽓部分只由⼀个天线和ASIC组成。
天线:卡⽚的天线是只有⼏组绕线的线圈,很适于封装到IS0卡⽚中。
ASIC:卡⽚的ASIC由⼀个⾼速(106KB波特率)的RF接⼝,⼀个控制单元和⼀个8K位EEPROM组成。
⼯作原理:读写器向M1卡发⼀组固定频率的电磁波,卡⽚内有⼀个LC串联谐振电路,其频率与讯写器发射的频率相同,在电磁波的激励下,LC谐振电路产⽣共振,从⽽使电容内有了电荷,在这个电容的另⼀端,接有⼀个单向导通的电⼦泵,将电容内的电荷送到另⼀个电容内储存,当所积累的电荷达到2V时,此电容可做为电源为其它电路提供⼯作电压,将卡内数据发射出去或接取读写器的数据。
非接触式IC卡性能简介(M1)
一、主要指标
●容量为8K位EEPROM
●分为16个扇区,每个扇区为4块,每块16个字节,以块为存取单位
●每个扇区有独立的一组密码及访问控制
●每张卡有唯一序列号,为32位
●具有防冲突机制,支持多卡操作
●无电源,自带天线,内含加密控制逻辑和通讯逻辑电路
●数据保存期为10年,可改写10万次,读无限次
●工作温度:-20℃~50℃(温度为90%)
●工作频率:13.56MHZ
●通信速率:106KBPS
●读写距离:10mm以内(与读写器有关)
二、存储结构
1、M1卡分为16个扇区,每个扇区由4块(块0、块1、块
2、块3)组成,(我们也
将16个扇区的64个块按绝对地址编号为0~63,存贮结构如下图所示:
数据块0
数据块 1
数据块 2
控制块 3
数据块 4
数据块 5
数据块 6
控制块7
数据块60
数据块61
数据块62
控制块63
2、第0扇区的块0(即绝对地址0块),它用于存放厂商代码,已经固化,不可更改。
3、每个扇区的块0、块1、块2为数据块,可用于存贮数据。
数据块可作两种应用:
★ 用作一般的数据保存,可以进行读、写操作。
★ 用作数据值,可以进行初始化值、加值、减值、读值操作。
4、每个扇区的块3为控制块,包括了密码A 、存取控制、密码B 。
具体结构如下:
密码A (6字节) 存取控制(4字节) 密码B (6字节)
5、每个扇区的密码和存取控制都是独立的,可以根据实际需要设定各自的密码及存取控制。
存取控制为4个字节,共32位,扇区中的每个块(包括数据块和控制块)的存取条件是由密码和存取控制共同决定的,在存取控制中每个块都有相应的三个控制位,定义如下:
块0: C10 C20 C30 块1: C11 C21 C31 块2: C12 C22 C32 块3: C13 C23 C33
三个控制位以正和反两种形式存在于存取控制字节中,决定了该块的访问权限(如 进行减值操作必须验证KEY A ,进行加值操作必须验证KEY B ,等等)。
三个控制 位在存取控制字节中的位置,以块0为例:
对块0的控制:
字节6 字节7 字节8 字节9
( 注: C10_b 表示C10取反 )
存取控制(4字节,其中字节9为备用字节)结构如下所示:
字节6 字节7 字节8 字节9
( 注: _b 表示取反 )
6、数据块(块0、块1、块2)的存取控制如下:
例如:当块0的存取控制位C10 C20 C30=1 0 0时,验证密码A或密码B正确后可读;
验证密码B正确后可写;不能进行加值、减值操作。
7、控制块块3的存取控制与数据块(块0、1、2)不同,它的存取控制如下:
例如:当块3的存取控制位C13 C23 C33=1 0 0时,表示:
密码A:不可读,验证KEYA或KEYB正确后,可写(更改)。
存取控制:验证KEYA或KEYB正确后,可读、可写。
密码B:验证KEYA或KEYB正确后,可读、可写。
三、工作原理
卡片的电气部分只由一个天线和ASIC组成。
天线:卡片的天线是只有几组绕线的线圈,很适于封装到IS0卡片中。
ASIC:卡片的ASIC由一个高速(106KB波特率)的RF接口,一个控制单元和一个8K位EEPROM组成。
工作原理:读写器向M1卡发一组固定频率的电磁波,卡片内有一个LC串联谐振电路,其频率与读写器发射的频率相同,在电磁波的激励下,LC谐振电路产生共振,从而使电容内有了电荷,在这个电容的另一端,接有一个单向导通的电子泵,将电容内的电荷送到另一个电容内储存,当所积累的电荷达到2V时,此电容可做为电源为其它电路提供工作电压,将卡内数据发射出去或接取读写器的数据。
四、M1射频卡与读写器的通讯
复位应答(Answer to request)
M1射频卡的通讯协议和通讯波特率是定义好的,当有卡片进入读写器的操作范围时,读写器以特定的协议与它通讯,从而确定该卡是否为M1射频卡,即验证卡片的卡型。
防冲突机制(Anticollision Loop)
当有多张卡进入读写器操作范围时,防冲突机制会从其中选择一张进行操作,未选中的则处于空闲模式等待下一次选卡,该过程会返回被选卡的序列号。
选择卡片(Select Tag)
选择被选中的卡的序列号,并同时返回卡的容量代码。
三次互相确认(3 Pass Authentication)
选定要处理的卡片之后,读写器就确定要访问的扇区号,并对该扇区密码进行密码校验,在三次相互认证之后就可以通过加密流进行通讯。
(在选择另一扇区时,则必须进行另一扇区密码校验。
)
对数据块的操作
读(Read):读一个块;
写(Write):写一个块;
加(Increment):对数值块进行加值;
减(Decrement):对数值块进行减值;
存储(Restore):将块中的内容存到数据寄存器中;
传输(Transfer):将数据寄存器中的内容写入块中;
中止(Halt):将卡置于暂停工作状态;。