NetworkManagementChapter5IPeBusinessManagement
- 格式:ppt
- 大小:1.65 MB
- 文档页数:94


UNDERSTANDING CANADIAN BUSINESSCHAPTER # 1 noteschater1MANAGING WITHIN THE DYNAMIC BUSINESS ENVIRONMENT动态商业环境下的管理Business and Entrepreneurship: Revenues, Profits, and Losses 事业和企业家能力:收益,利益和损失Business: Any activity that seeks to provide goods and services to others while operating at a profit.事业:寻求当在一笔利润操作时向其他人提供货物和服务的任何活动。
Profit: The amount a business earns beyond what it spends for salaries and other expenses.利益:一种商业在它为了薪金和其他话费所话费的以外赚的量Entrepreneur: A person who risks time and money to start and manage a business.企业家能力:冒险用时间和金钱开始和管理一种商业的一个人Revenue: The total amount of money a business takes in during a given period by selling goods and services. 收益:一种商业在一段特定的时间期间通过出售商品和服务获得的金钱Loss: When a business’s expenses are more then its revenue.失去:当一种商业的花费超过其收益时Risk: The chance an entrepreneur takes of losing time and money on a business that may not prove profitable.风险:一个企业家浪费了时间和金钱在事业上,却无利可图的机会Responding to the Various Business Stakeholders对各种各样的傻瓜也既得利益者作出反应Stakeholder:All the people who stand to gain or lose by the policies andactivities of a business.财产保管人:他通过政策和一种商业活动赢得或者失去的所有人- Investors; invest in the business投资者:在商业中的投资- Financial Institutions; lend money to the business 金融的社会公共机构:借钱给企业- Supplier; sell to the business供应商:向企业卖物品- Customers; buy goods and services from the business 消费者:从企业中购买商品和服务- Government; gets taxes from the business 政府:从企业中收税- Employees; get jobs from the business受雇者:从企业中得到工作- Dealers; buy and sell for the business经销商:为企业进行交易买卖- Environmentalists; protest the businesses pollution habits环境保护主义者:抗议商业污染习惯- Surrounding Community; get many positives and negatives from the business 周围的社区:从商业之中得到很多积极的和消极的影响Outsourcing: Assigning various functions, such as accounting, production, security, maintenance, and legal work, to outside organizations.外包:委托给外部单位的业务有很多,像审计,产品,安全,维护保养和政法工作.There is a major trend toward outsourcing in North Americanbusiness in an effort to cut costs and become more competitive. Much production has moved off shore, and many management functions are now sub contracted to external sources such as consulting firms.在北美的外包业务有一个大致的发展趋势:就是努力缩减成本提高竞争力.很多的产品现在已经转移到了沿海地区,许多管理职能现在订约与外部资源像咨询公司.Using Business Principles in Non-profit Organization非营利组织的商业原则的应用Non- profit Organization: An organization whose goals do not include making a personal profit for its owners or organization. 无利益组织:其目标不包括为其所有者或者组织赚取一笔个人的利润的一个组织。

System and Network Management Itineraries forMobile AgentsEmmanuel Reuter and Fran¸c oise BaudeOASIS Team,INRIA-CNRS-I3S2004route des Lucioles,BP9306902Sophia Antipolis cedex–France{st}@sophia.inria.frAbstract.The technology of mobile agents has proven its usefulness forsystem and network management.In order to be effective,the integrationof SNMP-based operations and the use of mobility should be effective.This paper presents a step forwards such an integration,by designingand implementing itineraries of mixed destination types:(1)a destina-tion type that represents a location where a mobile agent migrates(forreaching a remote network for performance purposes,or/and for man-aging the location using a pure Java function);(2)a destination typethat represents a location onto which the agent is not able to migrate,but for which an SNMP-based operation must be executed through aclassical client-server interaction.The mixed usage of both kinds of des-tinations is unified within our solution,and as such greatly simplifies theprogramming of new system and network management operations.1IntroductionFor several years now,the applicability and usefulness of mobile agent technolo-gies for distributed System and Network Management(SNM)have been recog-nized.One of the main point is to delegate to autonomous and possibly mobile agents the administration tasks.As such,the network and computation loads are distributed instead of centralized towards and on the manager host[BPW98]. The Java programming language is today the most adequate for building such SNM platforms,as it provides:(1)a total portability on all kind of operating systems(due to the Java Virtual Machine),(2)built-in distribution and mo-bility management mechanisms(RMI–Remote Method Invocation–,dynamic class loading,serialization,etc.),(3)built-in security management mechanisms (permissions,security policies).Moreover,for this specific application domain, SNMP operations[Sta93]can be invoked from Java programs,in particular,us-ing the AdventNet SNMP package[Adv98].Several academic research platforms have been recently built in order to prove the effectiveness of Java mobile-agents based SNM:Mole[BHSR98],MAMAS[BCS99],MAP[PT00],JAMES[SRS99], just to mention a few.One of the most tedious day-to-day task for a network and system manager is to keep the effective topology he/she has the responsability,in an up-to-date state,mainly in order to execute health monitoring.Fault diagnosis andnetwork configuration are other important tasks which can also have some effect on the effective topology of the managed whole ing any mobile agent based platform for system and network management implies tofirst deploy the infrastructure(daemons in order to host mobile agents).Secondly,be able to program itineraries composed of system or network elements,Java-compliant or not,that mobile agents must visit in order to execute their management tasks.The aim of our work is to introduce a transparent and easy-to-use mechanism such as to easily provide to mobile agents,up-to-date itineraries for executing their administrative task(on all or part of network elements of whatever type, Java or only SNMP compliant).Those itineraries will extend the common no-tion of what is an itineray for a mobile agent(i.e.,a list of computers running a platform-specific daemon onto which a mobile agent will move to),in the fol-lowing way:an itinerary for a SNM mobile agent will be considered as a list of elements to visit,not only locally after a move,but also remotely through a client-server interaction based on the classical SNMP protocol for instance.As such,we will provide a coherent,uniform and easy-to-use programming method-ology that solves the difficult programming problem of mixing in a same mobile agent pure Java-based and pure SNMP-based management operations.This programming facilities are made available into a system and manage-ment platform we are developing[RB02],using the ProActive library also devel-oped in our team and supported by ObjectWeb(),a consor-tium for open source middleware.ProActive(www.inria.fr/oasis/ProActive) is a100%Java library for parallel,distributed,concurrent computing with se-curity and mobility,implemented on top of RMI as the transport layer.Besides remote method invocation services,ProActive features transparent remote ac-tive objects,asynchronous two-way communications with transparent futures, high-level synchronisation mechanisms,migration of active objects with pend-ing calls and an automatic localisation mechanism to maintain connectivity for both“requests”and“replies”.ProActive is an open libray,whose behaviour can be modified or extended by the classical inheritance mechanisms found in object-oriented languages.For the present work,it has been possible to extend the way a mobile agent follows its itinerary for the case when this itinerary is not only a list of destinations where to migrate.In the following section,background on the model and usage of ProActive is given,followed by a quick overview of our SNM platform that is built upon this library for mobile code.Sections3and4detail how to build mixed itineraries and how their usage is already pre-programmed through the definition of a generic class.It remains only to programmers to extend this class in order to program a new specific mobile agent for a new management operation.Before concluding, we mention a few related works.2Background2.1The model of computation,remote invocation and migrationfeatured by ProActiveAs ProActive is built on top of standard Java APIs(Java RMI[Sun98b],the Reflection API[Sun98a],...).It does not require any modification to the stan-dard Java execution environment,nor does it make use of a special compiler, preprocessor or modified virtual machine.The model of distribution and activ-ity of ProActive is part of a larger effort to improve simplicity and reuse in the programming of distributed and concurrent object systems[Car93,CBR96]. Base model A distributed or concurrent application built using ProActive is composed of a number of medium-grained entities called active objects.Each active object has one distinguished element,the root,which is the only entry point to the active object.Each active object has its own thread of control and is granted the ability to decide in which order to serve the incoming method calls that are automatically stored in a queue of pending requests.Method calls (seefigure1)sent to active objects are always asynchronous with transpar-ent future objects and synchronization is handled by a mechanism known as wait-by-necessity[Car93].There is a short rendez-vous at the beginning of each asynchronous remote call,which blocks the caller until the call has reached the context of the callee(on Figure1,step1blocks until step2has completed).The ProActive library provides a way to migrate any active object from any JVM to any other one through the migrateTo(...)primitive which can either be called from the object itself or from another active object through a public method call,and which is put into the queue of pending requests in the same way as method calls.Mapping active objects to JVMs:Nodes Another extra service provided by ProActive(compared to Java RMI for instance)is the capability to re-motely create remotely accessible objects.For that reason,there is a need to identify JVMs,and to add a few services.Nodes provide those extra capabil-ities:a Node is an object defined in ProActive whose aim is to gather several active objects in a logical entity.It provides an abstraction for the physical location of a set of active objects.At any time,a JVM hosts one or several nodes.The traditional way to name and handle nodes in a simple manner is to associate them with a symbolic name,that is a URL giving their location,for in-stance:rmi://lo.inria.fr/Node1.As an active object is actually created on a Node we have instructions like:a=(A)ProActive.newActive("A",params, "rmi://lo.inria.fr/Node1").If the active object must be created on the same Node as the one hosting the object initiating the creation,then,a=(A)ProActive.newActive("A",params)is sufficient.Note that an active object can also be bound dynamically to a node as the result of a migration.Fig.1.Execution of a remote method call in ProActiveMigration of active objects from Nodes to Nodes The ProActive migra-tion mechanism[BCHV00]follows a classical weak migration model.That is, the migration is triggered at specific points only,in the present case,when the next element in the requests queue of the active object is a MigrateTo(...)call. The migration involves deactivating and serializing the active object on the lo-cal node,and then deserializing and reactivating the active object on the remote one.More sophisticated abstractions have been built on top of the migrateTo primitive in order to control the migration pattern with a higher level of abstrac-tion.An example of such an abstraction is static void onArrival(String s)which specifies as a string a method that will be executed upon arrival of the object at a node after its migration.Respectively,onDeparture allows us to declaratively specify code execution before migration.Finally,an itinerary abstraction allows us to specify a list of nodes to visit with various controls: add,requestFirst,migrationFirst,itineraryStop,itineraryRestart, etc.This is a migrationStrategyManager’s responsability to manage the travel of the active object according to its itinerary.For instance,if the requestFirst behaviour has been selected(it is the default one),then,in case the active ob-ject has pending remote method calls,then it will serve them before moving to the next location in its itinerary.Like all ProActive classes that configure the behaviour of an active object,the migrationStrategyManager can be extended such as to slightly modify the behaviour:it is exactly what we will done in order to build itineraries for System and Network Management.2.2Building and maintaining the effective topology of the network The SNM platform we have designed and implemented[RB02]is able to dynam-ically discover all system or network elements that are reachable on the network.To achieve this,one mobile DiscoveryAgent(itself programmed using ProActive) builds up a representation of the topology,by starting from an active equipment (a hub or switch for instance),and collecting and correlating SNMP variables of the various SNMP-enabled agents running on the current network.As such, it will discover all network elements,hosts and other devices and the way they are physically inter-connected.It gathers some information on each element,and registers all this in a specific server where this will be used for building itineraries for mobile agents as presented in the sequel.Such a server is called an Itinerary-Server.This discovery process is then periodically re-executed in background,in order to have an up-to-date vision of the effective topology of the network.For each element that is discovered,the following kind of information is recorded in the corresponding ItineraryServer:the state(alive or not);network parameters (IP and Ethernet addresses);interface types;if this element executes an SNMP agent(and all its associated parameters,target agent SNMP,read-mode com-munity name,UDP port number of the SNMP agent);if this element currently executes a ProActive Node,that is a specific daemon of our platform that could host a ProActive mobile object dedicated to a SNM task.As the administrative domain of the managed enterprise or institution may be composed of several networks,the topology discovery can be launched and executed in parallel for each network and one ItineraryServer per network main-tains the list of discovered elements on it.ItineraryServers are able to cooperate on demand in order to build itineraries that span several networks.Of course, the requirement is that elements belonging to a same network will appear close in an itinerary in order for a SNM mobile agent to avoid migrating more than once towards a given network.The next sections will show how to take advantage of those ItineraryServers in order to easily program mobile agents that will execute their task by travelling according to itineraries.3Design of itineraries for System and Network Management3.1Different kinds of DestinationsThe itinerary model for SNM we introduce is an extension of the basic itinerary concept provided by ProActive(a basic itinerary is a list of NodeDestinations, and for each,there is the ability to specify a method to execute on arrival).We have defined a new kind of destination,called an SnmpDestination,to which can also be associated a method to execute on arrival.An SnmpDestination collects all required information in order to execute a remote SNMP-based man-agement function(see2.2).Those various destination types are collected within a hierarchy(figure2).Simply extending the class Destination would enable to add a new kind of destination,such as for instance,one in order to support the version3of SNMP, or one to support the CMIP management[Sta93].Fig.2.Destination Class Hierarchy.3.2Itinerary managerThe purpose of an ItineraryManager is to factorize all code that is needed such as to build up an itinerary according to the type of travel and administrative tasks the mobile agent will be launched for:for instance,a mobile agent itineray specific for visiting all SNMP-compliant network elements,or all printers.All ItineraryServers will be asked to return the lists of elements or nodes they have collected during the topology discovery.Then,those lists will befil-tered such as to obtain the required itinerary type.One particular itinerary type consists in visiting only a given sub-network.In this case,only the lists maintained by the ItineraryServer of this given sub-network will be requested. In order to provide a set of pre-defined itinerary types,we have defined an ab-stract ItineraryManager class from which we have extended several sub-classes, one for each common itinerary type.Of course,new itinerary patterns may be obtained by sub-classing ItineraryManager.During this sub-classing process, only the method to effectivelyfilter the lists must be implemented by the pro-grammer.Below are listed the different pre-defined itinerary types and their purpose:–execute a complete management of the local network(i.e.,it is assumed that the mobile agent is started on a ProActive node belonging to this net-work):ItineraryManagerLocalNetwork will return an itinerary collecting all SNMP-compliant elements in this local network;ItineraryManagerLocalNodes will return an itinerary collecting all ProAc-tive nodes in this network,and it is assumed that all computers that must be visited must run a ProActive node such as to subsequently host the mobile agent,–execute a remote management in a specific sub-network:ItineraryManagerSubNetwork will return an itinerary collecting all SNMP-compliant and ProActive-compliant elements;and thefirst element in the itinerary is one of the ProActive remote nodes such as to host the mobile agent for performance purposes(instead of remotely executing the manage-ment of the subnetwork);–execute a remote management on all sub-networks:for obvious performance reasons,such an itineray will be built using ItineraryManagerWholeNetwork, as the result of concatenating itineraries for each sub-network,of the type ItineraryManagerSubNetwork.The purpose is that the mobile agent moves towards a remote sub-network only once.•ItineraryManagerAllNetwork is a restriction of the itinerary built withItineraryManagerWholeNetwork,to SNMP-compliant elements only;•ItineraryManagerAllNodes is a restriction of the itinerary built withItineraryManagerWholeNetwork,to ProActive-compliant elements only;–execute a remote management on all sub-networks restricted to specific types of devices(for instance,restricted to routers,printers,computers,etc): ItineraryManagerSpecificHosts.Figure3shows an example of a network that is built up with two sub-networks connecting elements that are only SNMP-compliant,Java-compliant or both.Suppose that we want to program a mobile agent such as to visit allwork diagram,showing the migration path and the SNMP traffic resulting from the itinerary built on table1,such as to be manage all elements.those elements,then,using the right sub-class of ItineraryManager,an SNM itinerary such as the one shown in table1will be built.Notice for instance that it might be the case that an itinerary element(Yate for instance)acts as a recipient for the mobile agent but gets also managed using SNMP operations (in which case,two Destinations in the itinerary will be present).Type of Action Element identification OS Type Type of Destination HomeNodeDestination YateMigration Koumac Linux NodeDestination Client-Server Koumac UCD-SNMP SnmpDestination Client-Server Server WinNt SnmpDestination Client-Server PC Win95SnmpDestination Client-Server Server WinNt SnmpDestination Client-Server Network Printer HP SnmpDestination Client-Server Server WinNt SnmpDestination Client-Server Router Cisco SnmpDestination Client-Server Server WinNt SnmpDestination Client-Server Print Server HP SnmpDestination Client-Server Server WinNt Term.Server SnmpDestination Client-Server Server Sco Openserver SnmpDestination Migration Yate Win XP NodeDestination Client-Server Yate SnmpDestination Client-Server Bourail Free BSD SnmpDestination End NodeDestination YateTable1.An Itinerary obtained with the ItineraryManagerWholeNetwork class for the network shown onfigure34A programming model for a mobile agent travelling according to a SNM itineraryThe purpose is to provide to end-users a framework that may them help to easily develop new agents for system and network management,under the plaform we provide built upon ProActive.The idea is to mask as much as possible the heterogeneity of elements that must be managed and the travelling from elements to elements.Moreover,while an agent is following its itinerary,any other object must be able to remotely communicate with it if required.In this perspective, we provide the definition of a generic Java class,called Agent(see code onfigure 4),from which active and mobile objects will be instanciated.As those objects are ProActive objects,they may execute pending remote method calls between considering any two Destinations in their itinerary.We will now detail those aspects.Automatic travel of the mobile agent following an itinerary.As soon as the itin-eray is built up,the mobile agent will automatically be able to travel according to it.The specific migrationStrategyManager that we have tuned,in order to be in charge of itineraries mixing NodeDestination and SnmpDestination, will be in charge of that:when the next Destination is not a ProActive com-pliant element,then,no migration arises;each time the mobile agent reaches a NodeDestination,a method named nodeOnArrival gets automatically ex-ecuted;each time it reaches a SnmpDestination,the method whose name is snmpOnArrival gets executed instead.This behaviour is automatically obtained through the fact that the mobile agent extends the generic SNM agent class we provide,named Agent(see code onfigure4).public class Agent implements java.io.Serializable{//the Destinationsprotected Destination dest;protected SnmpDestination snmpDest;protected NodeDestination nodeDest;private ItineraryManager itiManager;//my ItineraryManagerprivate ArrayList visitedNodes;//collected visited nodes//constructorpublic Agent(){}public ArrayList getVisitedNodes(){return visitedNodes;}public void setCurrentDestination(){//automatically called by the migrationStrategyManager,in order to//set the Destination to the appropriate variable,e.g.NodeDestination//or SnmpDestination,and record the Destination visiteddest=itiManager.getCurrentDestination();if(dest instanceof NodeDestination)nodeDest=(NodeDestination)dest;else snmpDest=(SnmpDestination)dest;visitedNodes.add(dest.toString());}public void nodeOnArrival(){};//what to do for a NodeDestinationpublic void snmpOnArrival(){};//what to do for a SnmpDestination//Prepare the itinerarypublic void prepareItinerary(String itineraryServerHome,ItineraryManager itiManager){//Record the ItineraryManager that must be usedthis.itiManager=itiManager;//ask it to build the required itineraryitiManager.prepareItinerary(itineraryServerHome);}//start to follow the itinerarypublic void startItinerary(){//start the travel}//add an urgent Destination to visitpublic void addUrgentDestination(Destination destination){//the next Destination will be the new oneitiManager.addUrgentDestination(destination);}//what to do at the end of the itinerary,if necessarypublic void atTheEnd(String methodName,Node homeNode){itiManager.setEndMethod(methodName,homeNode);}}//end of class AgentFig.4.Generic Class AgentRemote communication with a mobile agent.As already mentioned,as mobile agents implement the programming model featured by ProActive,which gener-alizes the usual Java RMI mechanism,then,it is possible to remotely commu-nicate with any travelling agent.For instance,it might be very useful to aska mobile agent to take into account an urgent destination(by calling for in-stance the addUrgentDestination(...)method predefined by the Agent class. As explained in section2.1,this method call will be executed before the next Destination in the itinerary gets visited.Easy programming of a new mobile agentThe only programming effort required for developing a new SNM agent(such as the one shown for instance on the code infigure5)is to extend Agent and overrides the implementation of either the nodeOnArrival(in standard Java)or textttsnmpOnArrival methods(using the AdventNet SNMP package),or both, if the agent may execute both kinds of management operations.On the given example,the class AgentMix enables to collect some memory usage information for ProActive-compliant hosts(generally,computers),and to collect some vari-ables stored in the SNMP MIB(here,ip.ipNetToMediaTable representing the MAC-IP table of the network element).public class AgentMix extends Agent implements java.io.Serializable{List AllMemInfo=new ArrayList();List AllArplTable=new ArrayList();public AgentMix(){}public void nodeOnArrival(){//implements Agent.nodeOnArrivalSystemResources sr=new SystemResources();//Gets TOTAL MEM,USED MEM,FREE MEM into a StringAllMemInfo.add(nodeDest.getURL()+sr.toString());}public void snmpOnArrival(){//implements Agent.snmpOnArrival//gets the SNMP MIB Table ip.ipNetToMediaTableAllArplTable.addAll(new IpMacTable(snmpDest).getArpTable());}//Display the collected Datapublic void displayData(){System.out.println("Data collected:"+AllMemInfo+"\n"+AllArplTable);}//return"partial"results,in the sense that the agent may not have terminated its travel public List getPartialResult(){return AllMemInfo;}}Fig.5.Scenario for an SNM agent extending Agent:it collects some Operating System Resources on each Java-compliant host and the ARP Table on each SNMP-compliant network elementFor launching a mobile agent executing this new management operation, then,the only requirement is to create this new active object,designate the required itineray type(by creating and passing an instance of the adequate ItineraryManager sub-class),and initiate the travel(see code onfigure6for instance).Notice that the same agent may be reused and given an other kind of itineray,by just passing it an other instance of a ItineraryManager sub-class.import org.objectweb.proactive.ProActive;import org.objectweb.proactive.core.node.NodeFactory;import mgt.agents.AgentMix;public class Launch{public static void main(String args[]){try{AgentMix mobileAgent=(AgentMix)ProActive.newActive("mgt.agents.AgentMix",null);mobileAgent.prepareItinerary(args[0],new mgt.itinerary.ItineraryManagerLocalNetwork());//NodeFactory.getDefaultNode is the ProActive Node onto the current JVMmobileAgent.atTheEnd("displayData",NodeFactory.getDefaultNode());mobileAgent.startItinerary();//do a job in parallel for instanceList partialResult=mobileAgent.getPartialResult();}catch(Exception e){e.printStackTrace();}}}Fig.6.How to launch a mobile agent:for instance here,an agent of the AgentMix class that will manage the local network5Related WorkIn none of the SNM platforms we have studied,the idea of how to build an itinerary that will sustain the travel of a mobile agent has been explored so deeply as here.Sometimes,the itinerary is manually given by the graphical user interface the manager is sitting in front of,or,read in a textfile.In other cases, such as in[OMDGG99],[GDM00],new elements are automatically recorded on the management workstation,such as to automatically build accurate itineraries for SNM mobile agents.But,it is restricted to locations able to host mobile agents,so the problem of visiting non-Java elements is not addressed at all. To our knowledge,the idea of mixing and uniformely use different types of destinations that trigger different kinds of management methods,in the same itinerary,is new.To our knowledge,only a few libraries for mobile agent programming in-troduce more structured itinerary patterns.For instance,the Ajanta library [TKA+02]features an itinerary description as a sequence of elements.Each ele-ment can either describe a single destination,or recursively a collection of des-tinations.The effective travel of a mobile agent will be structured in the same way.6ConclusionWe have introduced a new pattern for mobile agent itineraries,that proves to be particularily adapted to system and network management operations:indeed, in this kind of telecommunications application domain,the heterogeneity of ele-ments is important,even with the wide acceptance and usage of the SNMP pro-tocol.Our solution enables to mix several destinations into the same itinerary. If one would need to add an other kind of destination,such as CMIP for in-stance,only few classes should be extended or added:define a new adequatemigrationStrategyManager,define adequate new sub-classes of Destination and ItineraryManager.Of course,the topology discovery mechanism provided by our SNM platform should also be extended such as to register this new type of element.References[Adv98]AdventNet.AdventNet SNMP tools.,1998. [BCHV00] F.Baude,D.Caromel,F.Huet,and J.Vayssi`e municating Mobile Active Objects in Java.In proc.of the8th International Conference-HighPerformance Computing Networking’2000(HPCN Europe2000),LNCS vol.1823,pp633–643,2000.[BCS99]P.Bellavista,A.Corradi,and C.Stefanelli.An Open Secure Mobile Agent Framework for Systems Management.Journal of Network and Systems Man-agement,7(3),1999.[BHSR98]J.Baumann,F.Hohl,M.Straber,and K.Rothermel.Mole–Concepts ofa Mobile Agent System.World Wide Web1,3,1998.[BPW98] A.Bieszczad,B.Pagurek,and T.White.Mobile Agents for Network Man-agement.IEEE Communications Surveys1,1,1998.[Car93] D.Caromel.Towards a Method of Object-Oriented Concurrent Programming.Communications of the ACM,36(9):90–102,September1993.[CBR96] D.Caromel,F.Belloncle,and Y.Roudier.The C++//Language.In Parallel Programming using C++,pages257–296.MIT Press,1996.ISBN0-262-73118-5.[GDM00]Ghanbari M.Gavalas D.,Greenwood D.and O’Mahony M.Advanced network monitoring applications based on mobile/intelligent agent technol-puter Communications Journal,23(8):720–730,April2000.http:///268291.html.[OMDGG99] D.Greenwood O’Mahony M.J.D.Gavalas and M.Ghanbari.An infras-tructure for distributed and dynamic network management based on mobileagent technology.Proc.IEEE International Conference on Communications(ICC’99),2:1362–1366,June1999.[PT00] A.Puliafito and ing Mobile Agents to implementflexible Network Management puter Communication Journal,23(8),April2000.[RB02] E.Reuter and F.Baude.A mobile-agent and SNMP based management platform built with the Java ProActive library.submitted,2002.http://www.iufm.unice.fr/∼reuter/notes/submit02.ps.[SRS99]P.Sim˜o es,R.Reis,and L.Silva.Enabling mobile agent technology for legacy network management frameworks.In Proceedings of Softcom’99Conferenceon Software in Telecommunications and Computer Networks.IEEE Commu-nications Society,October1999.[Sta93]W.Stallings.SNMP,SNMPv2,and CMIP.Don Mills:Addison-Wesley,1993. [Sun98a]Sun Microsystems.Java Core Reflection,1998./ products/jdk/1.2/docs/guide/reflection/.[Sun98b]Sun Microsystems.Java Remote Method Invocation Specification,October 1998.ftp:///docs/jdk1.2/rmi-spec-JDK1.2.pdf. [TKA+02] A.Tripathi,N.Karnik,T.Ahmed,R.Singh, A.Prakash,V.Kakani, M.Vora,and M.Pathak.Design of the Ajanta System for Mobile AgentProgramming.Journal of Systems and Software,62(2):123–140,May2002.。


Network Management1 AbstractDECnet/OSI Phase V incorporates a new network management architecture based on Digital's Enterprise Management Architecture (EMA). The EMAentity model was developed to manage all entities in a consistent manner, structuring any manageable component regardless of its internal complexity. The DNA CMIP management protocol was developed in conjunction with the model to express the basic concepts in the entity model. Phase V network management is extensible; the Phase V management architecture transparently assimilates new devices and technologies. Phase V was designed to be an open architecture. Management of DECnet/OSI Phase V components is effective in a multivendor network.Network management has been an integral part of DECnet since 1976 when Phase II was developed.[1] Even at that early stage of the DECnet architecture, an effective management capability was recognized as an essential part of an organized approach to networking. Now in DECnetPhase V, the DECnet network management architecture has undergone a major revision based on Digital's Enterprise Management Architecture (EMA).This paper gives an overview of some of the key features and functionsof EMA and of DECnet Phase V network management. See the "Overview ofDigital's Open Networking" paper in this issue for an overview of the guiding principles, background, and architecture of DECnet Phase V.[2]Our initial work on Phase V indicated that changes were needed in the network management architecture to support the broad range of networking functions planned for Phase V. First, network managers would have to beable to manage all the Phase V components in a consistent manner. A method was needed to build Phase V management components that would give the same general look and feel and the same modeling approach to all components. Second, Phase V network management would have to be extensible. The PhaseV network architecture was being designed to allow the use of multiple modules that would provide the same or similar services at each layer andto simultaneously support multiple-layer protocols in a network. Therefore, we designed the Phase V management architecture to transparently assimilate new devices and technologies. Our management architecture had to become as extensible as the network architecture.Finally, since Phase V was designed to be an open architecture, management of Phase V components would have to be effective in a multivendor network. Our design had to ensure that the ability to provide effective managementof network components was independent of the vendors supplying them.Digital Technical Journal Vol. 5 No. 1, Winter 1993 1Network ManagementThe individual management mechanisms used in Phase IV could have been extended to accommodate all the changes planned for Phase V. However,we felt it was time to revisit the basic network management architectureto see if we could find a unified approach that would provide a superior solution.2 Enterprise Management ArchitectureWe began our Phase V development project by examining in detail the requirements for a new network management architecture. Our goal was to design an open architecture that allowed for consistent management of an extensible array of network components in a multivendor environment. Aswe identified the specific requirements that would have to be addressedto meet this goal, we realized that we had the opportunity to develop a architecture that went beyond management of Phase V networks. We realized that we could provide an architecture for the management of both networks and systems. The architecture eventually became known as the Enterprise Management Architecture or EMA.Early in the project, we recognized that the conceptual separationof manageable components from the software that manages them was a fundamental design principle. EMA therefore distinguished entities, the basic components of the network that had to be managed, from directors, the software systems and accompanying applications used by managers to manage the components, as shown in Figure 1.Formally, an entity was further split into a service element, a managed object, and an agent. The service element is the portion of the entitythat performs the primary function of the entity, e.g., a data linklayer protocol module whose primary purpose is communication with a peer protocol module on another machine. The managed object encapsulates the software that implements the functions supported by the entity for itsown management. For example, it responds to management requests for the current values of state variables or to requests for the values of certain configuration variables to be set to new values. The agent is the software that provides the interface between the director and the managed object. The agent encodes and decodes protocol messages it exchanges with the director and passes requests to and receives responses from the managed object.Informally, we generally equate the managed object and the entity because the managed object defines what the manager can monitor and control in the entity.A director was modeled as a layered software system that provides a management-specific environment to management applications. A directorwas split into a framework, a management information repository (MIR),and separate configurable software modules called management modules.The director kernel provides common routines useful for the layeredsoftware modules, including services such as dispatch (location-transparent exchange of management requests and responses with entities), encoding2 Digital Technical Journal Vol. 5 No. 1, Winter 1993Network Management /decoding, data access, data dictionary access, and event management. Taken together, the director kernel and the agent provide a framework for managed objects and management applications to interact. The framework provides an application programming interface (API) to managed object and management module developers. The MIR contains data about particular entities as well as information about the structure and other properties of entity classes, which the director software also knows.Management modules were distinguished as presentation, function, oraccess modules. Presentation modules implement user or software accessto the director management modules that is device independent and style dependent. Function modules provide value-added management functions that are partially or completely entity independent, such as network fault diagnosis, event or alarm handling, or historical data recording. Access modules provide a consistent interface to the basic management functions performed by entities. In addition, they include one portion that maps operations on entities into the appropriate protocol primitives and another portion that implements the protocol engine for the relevant management protocol. Figure 2 shows the components of a director and an entity. Although users can conveniently interact with systems through graphicaluser interfaces (GUIs), sophisticated users wished to preserve a command line interface (CLI) they could use to specify complex management requests quickly. Therefore, we developed a single, extensible command language that would allow human operators or software programs to communicate requeststo management modules and (ultimately) entities in a consistent fashion. This work developed into the network control language (NCL). An NCL command specifies an entity, an operation to be performed by the entity, a listof arguments (if any), and a list of qualifiers (for specifying users, passwords, paths, filtering values, etc.).Digital's DECmcc Management Director is an implementation of an EMAdirector.[3] The DECmcc product provides a platform for the developmentof new management capabilities and offers specific Phase V management capabilities as well as a number of generic network management tools. The DECmcc director supports both GUI and NCL CLI user interfaces.Entity ModelTo manage all entities in a consistent manner, we required a single, consistent method for structuring any manageable component (regardlessof its internal complexity) and for describing its management properties: the operations that it can perform, the variables it makes available forits management, the critical occurrences it can report to managers, etc. The EMA entity model was developed to answer these needs. The structure of a manageable component in this model is shown in Figure 3. Essentially, the entity model defines techniques for specifying an object-oriented view ofan entity. Each entity has the following properties:o A position within an entity hierarchy. To ease management of networkswith large numbers of complex components, entity classes are organizedinto logical structures that reflect the relationship of theirDigital Technical Journal Vol. 5 No. 1, Winter 1993 3Network Managementcorresponding components; individual entities are named in terms ofthat structure. The name of the top-level entity in each structure isglobally unique, and it is referred to as a global entity. All its child entities, however, have names that are unique only within the context of their level in the structure. Therefore, they are referred to as localentities.o A hierarchically structured name. An individual entity's local nameis constructed by concatenating its class name to its instanceidentifier. The class name is a keyword that uniquely identifies theclass (object type) of an entity. The instance identifier is the valueof an identifying attribute used for naming instances of the entity'sclass, for which each instance of the class has a unique value.A target entity's globally unique name is constructed by concatenatingits local name (a <class name, instance identifier> pair) to the localnames of each of its ancestors in turn, beginning with the containingglobal entity and ending with the target entity's immediate parent. The construction of an entity's name and the containment hierarchy are shown in Figure 4.o A collection of internal state variables, called attributes, that can be read and/or modified as a result of management operations. Attributeshave names unique within the context of the entity. Attributes have atype that defines the values the attribute can have.o A collection of operations that can be performed by the entity.Operations allow managers to read attributes, modify attributes, andperform actions supported by the entity. Actions are entity-specificoperations that result in changes of state in the entity or cause theentity to perform an operation that has a defined effect.o A collection of events that can be reported asynchronously by theentity. An event is some normal or abnormal condition within an entity, usually the result of a state transition observed by its service element or its agent. Event reports are sent asynchronously to the manager;they indicate the type of (entity-specific) event that occurred and may also contain arguments that further describe or qualify the event. Forexample, arguments could indicate the number of times the event occurred before a report was sent to announce that a threshold was reached, orgive the old and new states in an event that reports a state transition. o A specification of the behavior of the entity in relationship to thefunctions that the entity's service element provides. This is usuallyspecified as some abstract state machine, through pseudocode, or as aset of preconditions, postconditions, and invariants.The entity model provides specific requirements and recommendations about the way entities can be modeled in terms of these properties. These restrictions, placed on entity class definitions for purposes of both internal and global consistency, take several forms: (1) restrictionson the types and ranges of attributes that can be used for various purposes (e.g., as identifying or counter attributes); (2) constraints on 4 Digital Technical Journal Vol. 5 No. 1, Winter 1993Network Management operations (e.g., examine operations can have no side effects on the value of attributes whose values they report); or (3) restrictions on events(e.g., all events and event reports must have an associated time stamp and unique identifier).Readers familiar with open systems interconnection (OSI) managementwill find the entity model very similar to OSI's structure of management information (SMI) standard.[4,5] This is no coincidence. During the early development of Phase V and the entity model, we recognized the need foran open management architecture. Portions of the technology were therefore contributed to ISO/IEC JTC 1 SC21/WG4, a working group of the International Organization for Standardization (ISO) that is responsible for efforts to define standards for OSI management. Although some details of OSI SMI and the corresponding EMA features diverged slightly from each other duringtheir evolution, the EMA entity model and OSI SMI are still compatible. At this writing, work is under way to align certain parts of the EMA entity model with the final international standard (IS) versions of OSI SMI.EntitiesThe EMA entity model describes how to specify the management of an architected subsystem. However, for Phase V, we chose to make the management specification of a subsystem a part of the subsystem's specification. As described in the Modules section, that may have beenthe most important decision made in the network management architecture.As the entities for DECnet/OSI Phase V were defined, a collection offolklore grew on how typical design issues could or should be solved.As with any folklore, these guidelines were passed from one architectto another, either verbally, or as selected portions of the management specifications were copied from one subsystem to another. This folklore is continually changing, as new and better solutions are found. Much of the folklore has already been described.[6] Some other guidelines are described below.The Network Management Specification describes the central structure of Phase V network management, and in particular defines the node entityclass.[7] In the following sections, we describe the properties of the node entity class and, as a representative example, the OSI transport module entity class.3 Node Entity ClassA single computer system in the DECnet/OSI network is called a node. The bounds of that system depend on the system's architecture; a personal computer (PC), a single-processor workstation, a multiprocessor mainframe, a diskless system, even a VAXcluster system can be considered a singlenode. Nodes are modeled by the node entity class.Digital Technical Journal Vol. 5 No. 1, Winter 1993 5Network ManagementA node entity has only a few functions in management.o A node is a global entity that is the parent for many subsystems andprovides an agent for all of them.o A node has an identity, a name, and an address that allow it to bemanaged remotely.o A node plays a major role in system initialization and start-up.IdentityThe following attributes identify a node:o An address, the application layer address(es) of the node's agento A name, a DECdns fullname as defined by the DECnet/OSI distributed name server[8]o A synonym, a Phase IV-style node name for backward compatibilityo A spatially unique identifier (ID), a 48-bit quantity used as anInstitute of Electrical and Electronics Engineers (IEEE) 802 local area network (LAN) or Ethernet addresso A space- and time-unique valueA node's address is the application layer address(es) of the node'sagent. The DECnet/OSI network supports multiple protocols at any of the seven layers, and the agent can operate over multiple protocol stacks.Each protocol has its own addressing conventions. Thus a node's addressis actually a set of protocol towers. Each tower defines a sequence of protocols, each with its associated addressing information. A protocoltower provides all the information needed by a director to connect to the node's agent and to issue management directives to the node or any of its children.Users and network managers rarely refer to nodes by their addresses. First, it is difficult to remember the addresses and second, moving the nodefrom one place to another in the network generally changes its address. Thus each node has a name, a DECdns fullname. The node knows its nameand address. Each node's name is stored as a DECdns entry, and one of the entry's DECdns attributes holds the node's address. Thus, any director can look up the node's name in the DECdns and the address associated with it, and then use any one of the towers to connect to the node's agent.To ensure backward compatibility with DECnet Phase IV, a node also hasan attribute called its synonym, which is a six-character, Phase IV-style node name. If a node has a synonym name, that name is entered in a special directory in the DECdns name space as a soft link to the node's Phase V name. A soft link is a form of alias or indirect pointer, from one name to another, that allows an entry to be reached by more than one name.6 Digital Technical Journal Vol. 5 No. 1, Winter 1993Network Management Each network layer address of the node (a node can have more than one) is encoded in a standard way as a soft link to the node's name. This allows a manager (or director) to translate a node address into the equivalent node name, making many diagnostic problems much simpler.DECnet/OSI includes many features that allow most nodes to autoconfigure their addresses. Network layer addresses consist of an area address and a 48-bit ID. This ID can be obtained from an ID read-only memory (ROM) chip on many devices (for example, each Digital 802.3 LAN device has one). End nodes detect area addresses from messages sent by the routers adjacent to the end node. Higher-level addresses used by management are architecturally defined constants.Managers and users choose the name and synonym of a node. The manager uses the rename action to tell the node its name. Rename is an example of a situation in which an action is more appropriate than a set operation. Renaming a node is a fairly complicated operation. Not only is the name attribute changed, but also the information is stored in the DECdns name space. Although the operation can fail in many ways, actions allow errorsto be reported to the manager with enough detail on what went wrong toallow corrective action to be taken. This is not easily done with a set operation.One of the more difficult configuration problems to track down occurswhen two nodes in a network have either the same name or the same address. DECnet/OSI has several management features to prevent this from occurringor to detect the situation when it does occur.First, each node has a spatially unique 48-bit ID, i.e., no two nodes inthe enterprise have the same ID at the same time. The ID is usually derived from an ID ROM chip in a LAN adapter. Special manufacturing procedures ensure that no two ID ROMs hold the same ID. Nodes with multiple ID ROMs, for example a router with two Ethernet interfaces, choose one with a simple algorithm. Nodes without an ID ROM must be assigned an ID when the systemis first booted, and that ID must come from the locally administered IDs. However, an ID is not always tied to the same node. Hardware devices can be removed from one machine and inserted in another. Indeed, this is a common diagnostic procedure.Second, each node has a space- and time-unique value provided by theunique identifier (UID) service. UIDs combine a spatially unique ID witha time stamp in such a way that no two generated UIDs will ever have the same value.[9] The UID is stored in nonvolatile storage (if the node has some), so the UID remains constant across system reboots. Nodes without nonvolatile storage will generate a new UID on every reboot.Third, a change in the name, address, ID, or UID attributes is reportedby the node as an event, which aids in detecting duplicate node names and addresses. Two nodes can end up with the same name when the disk wherea node stores its system image, name, address, and UID is copied, andthen the copy is booted on another machine. When the disk is booted on the second machine, that machine would have a different ID ROM. The node would Digital Technical Journal Vol. 5 No. 1, Winter 1993 7Network Managementdetect that its ID is different, and thus an event would be generated. The event would not prevent the duplicate node from booting, but it would allow the manager to detect that a duplicate node may be on the network.Start-upA node is responsible for system start-up. We model start-up through four states.o Dead, when the node is down and requires manual intervention to start.o Booting, when the node is in the initial stages of software start-up.The booting process is highly system specific and may be initiated byhardware, by software, by a power failure, or by a manager's consolerequest. Booting loads a system image, starts it running, and bringsit to a known state. The system image can be loaded from a disk orequivalent storage, or it can be loaded over the network using themaintenance operations protocol (MOP) down-line load protocol.[10]MOP is layered directly over the data link protocols. In Digital'scommunications devices, MOP is generally implemented in the hardwareor firmware and does not require a working operating system.o Off, when the node is initializing itself and its internalconfiguration. When booting completes, the node changes to theoff state. This transition is called the "big bang." In the firstinstant after the big bang, the node has at least the following thingsavailable, as shown in Figure 5:- A working clock and time service used to time stamp events.- A UID generator used to give entities and events a unique identifier. - The node entity (and possibly some of the node's child entities)together with its agent (which includes both the directive dispatcher and event logging).- An initialization script, a series of management commands toconfigure the system. This can be in the form of a text NCL commandfile (described later in the section on NCL), or it can be a compiled script, one that has been encoded as a series of common managementinformation protocol (CMIP) requests. MOP can be used to down-lineload an initialization script.- An initialization director, which reads the script and invokesthe directives in the order given. Errors and other output may bedisplayed on a console (if the system has one) and/or reported asevents.o On, when the node has "completed" initialization to the extent thatit can be managed remotely. Somewhere in the initialization script(probably near the end), the node is enabled, which changes its state to on, i.e., it can be managed remotely.8 Digital Technical Journal Vol. 5 No. 1, Winter 1993Network Management ModulesA node has many subsystems, called modules in DECnet/OSI. Each module mayor may not be configured within any particular node. Within the modules are the various subsystems that make up DECnet/OSI. A node never has more than one instance of a module contained within it. A general-purpose node allows the manager to flexibly configure a node to serve a particular purpose by creating and deleting the appropriate modules.In the DECnet/OSI Phase V network, the specification of the managementof each module is an integral part of the architecture of the subsystem. Moving responsibility for the management of a subsystem from a central network management architecture to the subsystem architecture has madethe specifications clearer and more complete. In Phase IV, a great deal of effort was spent coordinating the subsystem specifications and the network management specification. Placing responsibility in one person's hands made writing an internally consistent subsystem much easier. Besides, the sheer size of DECnet/OSI Phase V management would have made it impossible for a single person to design the management of the whole system.The development of the OSI management standards in ISO/CCITT (ComitéConsultatif Internationale de Télégraphique et Téléphonique) has been done in a similar way and for the same reasons. ISO/IEC JTC1 SC21/WG4 is the group that has developed the OSI management information model, management specification language, and guidelines for module developers. While SC21/WG4 has itself also developed the management of specific subsystems (e.g., for event forwarding and logging), typically, the job of doing this has been left to other groups more expert in particular areas. For example, Working Groups 1, 2, and 4 of ISO/IEC JTC1 SC6 have developed management standards for the ISO data link, network, and transport layers, based on Digital's contributions derived from the DECnet/OSI Phase V work in these areas.In DECnet/OSI, the transport, network, and data link subsystems were among the first to have the EMA concepts applied to their management. Others quickly followed and, presently, more than 50 modules have been specified, with others being added as new subsystems are designed. Not surprisingly, during the early days considerable interaction took place between the architects responsible for the central network management architecture and those responsible for developing the management of specific subsystems. The EMA evolved and was refined based on the experiences of the many subsystem architects using it.In almost all cases, modules contain one or more entities, eachrepresenting some management aspect of the subsystem. These entities inturn may contain other entities (subentities). This nesting can occur toan arbitrary depth, reflecting the management complexity of the subsystem.Note that modules themselves are entities, albeit with the restriction that a node never has more than one instance of a module contained within it.An entity is formally described using Digital's Management Specification Language (MSL).[11]Digital Technical Journal Vol. 5 No. 1, Winter 1993 9Network ManagementWe next consider in more detail the structure and contents of the DECnet/OSI Phase V OSI transport module. Complete descriptions of this and other Phase V subsystems can be found in the Digital Network Architecture (Phase V) Documentation Kits.[12,13,14,15]4 OSI Transport ModuleIn DECnet/OSI Phase V, the OSI transport module contains port, template, local network service access point (NSAP) address, and manufacturing automation protocol (MAP) entities. A local NSAP entity contains remote NSAP entities. The containment hierarchy is shown in Figure 6.The OSI transport module has characteristic attributes. A manager can change the configuration of the module by modifying its characteristic attributes. This is done for several reasons, includingo To limit the maximum permissible number of active transport connections at any one timeo To control the maximum credit window that may be granted on anindividual transport connectiono To control the maximum number of transport connections that can bemultiplexed on any single network connection, when the OSI transportprotocol is operating over the connection-mode network serviceModification of these attributes is needed only if the manager requires anything other than a standard configuration; working default values are defined for all characteristic attributes.Status attributes show the current operating state of the module, e.g.,the number of transport connections currently active. Status attributes cannot be modified directly by a manager. To start the operation of the OSI transport module, the manager uses the enable action. If successful, the state attribute changes from off to on.In the DECnet/OSI Phase V architecture, a port entity represents the interface between layers, making visible to a manager how one layer (a client) is using the services of a lower layer. Ports are not created by a manager; they are created when a client of the service requests use of the service (by "opening a port"). The exact information held in a port entity varies for each subsystem. In general, a port entity contains attributes that identify the client and the service being used, and how that serviceis being used (e.g., as usage counters). The port entity is an exampleof how the EMA evolved through feedback from the subsystem architects. Before being adopted as a general mechanism in the overall management architecture, the concept was first developed and used in subsystem。

对外经济贸易大学管理学原理考点精华 UIBECHAPTER 1•Manager(管理者)➢Someone who works with and through otherpeople by coordinating and integrating theirwork activities in order to accomplishorganizational goals•First-line Managers(基层管理者)➢Are at the lowest level of management andmanage the work of non-managerial employees. •Middle Managers(中层管理者)➢Manage the work of first-line managers.•Top Managers(高层管理者)➢Are responsible for making organization-widedecisions and establishing plans and goals thataffect the entire organization.What Is Management?(什么是管理)•Coordinating working activities (协调)•Managerial Concerns➢Efficiency(效率)❖“Doing things right”–G etting the most output for the leastinputs➢Effectiveness(效果)❖“Doing the right things”–A ttaining organizational goals•Functional Approach(管理职能)➢Planning (计划)❖D efining goals, establishing strategies toachieve goals, developing plans to integrateand coordinate activities.➢Organizing (组织)❖A rranging work to accomplishorganizational goals.➢Leading (领导)❖W orking with and through people toaccomplish goals.➢Controlling (控制)❖M onitoring, comparing, and correcting thework.•Management Roles Approach (管理角色)➢Interpersonal roles(人际)❖F igurehead, leader, liaison➢Informational roles (信息)❖M onitor, disseminator, spokesperson ➢Decisional roles (决策)❖E ntrepreneur, Disturbance handler,resource allocator, negotiator•Skills Approach(管理技能)➢Technical skills (技术技能)❖K nowledge and proficiency in a specificfield➢Human skills (人际技能)❖T he ability to work well with other people ➢Conceptual skills (概念技能)❖T he ability to think and conceptualizeabout abstract and complex situationsconcerning the organization••An Organization Defined➢A deliberate arrangement of people toaccomplish some specific purpose•Common Characteristics of Organizations➢Have a distinct purpose (goal)➢Composed of people➢Have a deliberate structureCHAPTER 2Scientific ManagementTaylor’s Four Principles of Management1.Develop a science for each element of anindividual’s work, which will replace the old rule-of-thumb method. 科学方法2.Scientifically select and then train, teach, anddevelop the worker. 科学培训3.Heartily cooperate with the workers so as to ensurethat all work is done in accordance with the principles of the science that has been developed.忠心合作4.Divide work and responsibility almost equallybetween management and workers. 职责平等5.Frank and Lillian Gilbreth 吉尔布雷斯夫妇1.Focused on increasing worker productivitythrough the reduction of wasted motion2.Developed the microchronometer to timeworker motions and optimize performance6.Henri Fayol 亨利.法约尔1.Believed that the practice of management wasdistinct from other organizational functions2.Developed fourteen principles of managementthat applied to all organizational situations Division of work.Authority.Discipline.Unity of command.Unity of direction.Subordination of individual interest to the interests of the organization. Remuneration.Centralization.Scalar chain.Order.Equity.Stability of tenure of personnel.Initiative.Esprit de corps.7.Max Weber 马克斯.韦伯1.Developed a theory of authority based on anideal type of organization (bureaucracy•Organizational Behavior (OB)➢The study of the actions of people at work;people are the most important asset of anorganizationThe Hawthorne Studies (霍桑实验•A series of productivity experiments conducted at Western Electric from 1927 to 1932.•Experimental findings➢Productivity unexpectedly increased underimposed adverse working conditions.➢The effect of incentive plans was less thanexpected.•Research conclusion➢Social norms, group standards and attitudesmore strongly influence individual output andwork behavior than do monetary incentivesCHAPER 3The Manager: Omnipotent or Symbolic? •Omnipotent View of Management (管理万能论)➢管理者应该直接对组织的成败负责➢不同组织间效能或效率的差异,是由于管理者的决策与行动差异所致➢组织的绩效好坏难以归咎是管理者的直接影响,但管理者仍要为组织绩效负起大部分责任•Symbolic View of Management (管理象征论)•组织的成败大部分是由于管理者无法掌握的外力所造成•管理者对成果的掌握能力,会受到外部因素的影响和束缚•这些因素包括经济、市场(顾客)的变化、政府政策、竞争者行为、特定产业状况、专利技术的控制以及前任管理者的决策等•管理者透过行动,象征性地控制和影响组织的运作•Organizational Culture➢A system of shared meanings and commonbeliefs held by organizational members thatdetermines, in a large degree, how they acttowards each other.➢“The way we do things around here.”•Values, symbols, rituals, myths, andpractices➢Implications:•Culture is a perception.•Culture is shared.•Culture is descriptive.The source of an organization’s culture and how that culture continues 看书上How Employees Learn Culture•Stories (故事)➢Narratives of significant events or actions ofpeople that convey the spirit of the organization •Rituals (仪式)➢Repetitive sequences of activities that expressand reinforce the values of the organization •Material Symbols➢Physical assets distinguishing the organization •Language➢Acronyms and jargon of terms, phrases, andword meanings specific to an organizationCHAPER 6The Decision-Making Process•The Decision-Making Process (决策制定过程)➢Identifying a problem and decision criteria andallocating weights to the criteria. (界定问题,设立决策的准则,分配准则的权重)➢Developing, analyzing, and selecting analternative that can resolve the problem. (发展、分析、选择能解决问题之方案)➢Implementing the selected alternative. (执行方案)➢Evaluating the decision’s effectiveness. (评估决策的效能)Step 1: Identifying the Problem•Problem (问题)➢A discrepancy between an existing and desiredstate of affairs. (理想情况与现实状况之间存在了某种差距)•Characteristics of Problems (问题的特性)➢A problem becomes a problem when a managerbecomes aware of it. (管理者察觉问题所在)➢There is pressure to solve the problem. (压力——解决问题的动机)➢The manager must have the authority,information, or resources needed to solve theproblem. (管理者必须有解决问题所需之职权、信息和各项资源)Step 2: Identifying Decision Criteria•Decision criteria are factors that are important (relevant) to resolving the problem.Step 3: Allocating Weights to the Criteria•Decision criteria are not of equal importance:•各个决策准则,其重要性并不完全一致Step 4: Developing Alternatives 步骤四:开发备择方案•Identifying viable alternatives 确认可行的方案➢Alternatives are listed (without evaluation) thatcan resolve the problem. 列出解决问题的各种可行方案(但不予以评估)Step 5: Analyzing Alternatives•Appraising each alternative’s strengths and weaknesses评估每个方案的优劣➢An alternative’s appraisal is based on its abilityto resolve the issues identified in steps 2 and 3. 方案的评估是根据第二、三步骤所发展的准则,透过这样的分析,每个方案的优劣即可清楚呈现Step 6: Selecting an Alternative 步骤六:选择方案•Choosing the best alternative (选出最佳方案)➢The alternative with the highest total weight ischosen.选出得分最高的方案Step 7: Implementing the Decision 步骤七:执行•Putting the chosen alternative into action.•将决策付诸行动➢Conveying the decision to and gainingcommitment from those who will carry out thedecision.将方案有关的讯息传给执行决策者,并获得他们的认同与承诺Step 8: Evaluating the Decision’s Effectiveness 步骤八:评估决策的效能•The soundness of the decision is judged by its outcomes.决策正确与否,可由决策的结果加以检视Making Decisions (决策模式)•Rationality (理性)➢Managers make consistent, value-maximizingchoices with specified constraints.➢Assumptions are that decision makers: (理性假设)❖A re perfectly rational, fully objective, andlogical.❖H ave carefully defined the problem andidentified all viable alternatives.❖H ave a clear and specific goal❖W ill select the alternative that maximizesoutcomes in the organization’s interestsrather than in their personal interests. •Bounded Rationality (有限理性)➢Managers make decisions rationally, but arelimited (bounded) by their ability to processinformation.➢Assumptions are that decision makers: (有限理性假设)❖W ill not seek out or have knowledge of allalternatives❖W ill satisfice—choose the first alternativeencountered that satisfactorily solves theproblem—rather than maximize theoutcome of their decision by considering allalternatives and choosing the best. •Escalation of Commitment (承诺升级)➢Increasing or continuing a commitment toprevious decision despite mounting evidencethat the decision may have been wrong.What is Intuition? (何谓直觉)•Structured Problems (结构化问题)➢Involve goals that clear.➢Are familiar (have occurred before).➢Are easily and completely defined—informationabout the problem is available and complete.Programmed Decision (程序化决策)➢A repetitive decision that can be handled by aroutine approach.•Unstructured Problems (非结构化问题)•Problems that are new or unusual and for which information is ambiguous or incomplete. •Problems that will require custom-made solutions •Nonprogrammed Decisions (非程序化决策)➢Decisions that are unique and nonrecurring.➢Decisions that generate unique responses. Decision-Making Conditions•Certainty (确定性决策)➢管理者得以作出准确决策的最理想状况,因为所有可能方案的结果都是已知•Risk (风险决策)➢在风险情况下,决策者可依据个人经验或资料,预估各方案成败与结果的机率•Uncertainty (不确定性决策)➢当管理者对可能的结果与机率一无所知时,将迫使他们靠直觉、创意、征兆观察和胆识来作决策•Uncertainty (不确定性)➢Limited or information prevents estimation ofoutcome probabilities for alternativesassociated with the problem and may forcemanagers to rely on intuition, hunches, and“gut feelings”.•Maximax: the optimistic manager’s choiceto maximize the maximum payoff (最大收益最大化)找出每种可能决策的最好结果,选择其中具有最大报酬的决策Maximin: the pessimistic manager’s choice to maximize the minimumpayoff (最小收益最大化)找出每种决策的最差结果,选择其中最大报酬的决策•Minimax: the manager’s choice tominimize his maximum regret. (最大遗憾最小化)找出每种决策的最大潜在遗憾,选择其中最小的决策。



Agents in Network ManagementOsman Ertugay Micheal Hicks Jessica KornblumJonathan Smith26th February 2000AbstractThe ubiquity and complexity of modern networks require automated management and control. With increases in scale, automated solutions based on simple data access models such as SNMP will give way to more distributed and algorithmic techniques. This article outlines present and near-term solutions based on the ideas of active networks and mobile agents, which permit sophisticated programmable control and management of ultra large scale networks.1IntroductionAlthough the widely accepted definition of “Network Management” has not changed in over a decade, the importance of managing a network has increased dramatically. Networks have become embedded in almost everything we do from placing a phone call or sending an email to running a business. What was initially a few computers connected together has now become a vast array of specialized devices connected by phone lines, optical cable, satellites, and microwave dishes. The number of network services has also dramatically increased. The telecommunications industry has recently created many “value added services” such as caller identification, call waiting, and call forwarding. They also offer customers a diverse range of network resources such as Plain Old Telephone Service (POTS), Integrated Services Digital Network (ISDN), Digital Subscriber Lines (DSL), T1 and T3 lines. The Internet service base has also expanded, with demand for quality of service (QoS) guarantees, mobile computing, and secure communications. And of course, new services in the network engender the proliferation of new software applications and specialized hardware devices.As networks and their services and applications become larger in scale and more complex, the need for network management increases. Informally, network management seeks to configure, diagnose, and otherwise control the network and its services. However, traditional models of network management have not evolved at the same rate as the networks they manage. For example, the Simple Network Management Protocol (SNMP)1is still the de facto standard in the Internet community, even though it was developed over ten years ago when IP-based networks presented a much different landscape. Most network managers find that an ad-hoc collection of scripts is their most valuable management tool, rather than a well-defined approach involving automation, simply because the network is too complex.Distributed systems and distributed algorithms, have arisen as a way to deal with scale, complexity and diversity in networks. Distributed algorithms are used in current networks in an ad-hoc way; routing algorithms in the Internet are a conspicuous example. While other approaches exist, the two best-known approaches that provide a platform for implementing distributed algorithms are agent-based systems and active networks. In both cases, systems across the network are augmented with some level of programmability. In the case of agents, this usually occurs at the application layer, while in active networks the entire network itself becomes programmable, including the network layer using “active packets.”In this paper, we propose to enhance the existing client-server model of network management with an agent-based model that allows distributed computation. In doing so, we aim to reduce the complexity of implementing management tasks, and improve the agility with which these tasks can be deployed to react to new network services and infrastructures. By providing a uniform model for distributed programmability, we believe network management tasks may be implemented with greaterautomation. While our thinking has been informed by our experiences with active networking, in this paper we will adopt the mobile agent perspective.In the following section, we introduce and discuss agents, and the advantages of agents as compared with the client/server model. Section 3 examines the current practice of network management and highlights areas that need improving. In section 4, we present a number of approaches to network management using agents, describing work we have already done in the active networking context, as well as work to be done in other agent models. We briefly describe various related efforts in Section 5. We present conclusions in Section 6.2AgentsThough many definitions abound, we minimally define an agent to be a program that performs a task on behalf of some other entity (like a person or larger program). Expanding on this definition, agents may have a number of characteristics. A stationary agent runs locally, perhaps sending messages across the network, while a mobile agent may move (both its code and its state) across the network during its computation. An agent may be persistent, waiting for events to occur and then responding to them, or it may be ephemeral, simply performing its task and then terminating. If agents may communicate with one another, they may be composed into larger applications.2.1Benefits of AgentsAn agent is used to offload some of the computation that would normally be required of its client. If the client is a human user, then the agent simply automates a common task. For example, in ssh2, a user may use an ssh-agent to hold his ssh-key’s passphrase and automatically supply that phrase whenever the user makes connections through the agent, obviating the need of the user to repeatedly type the passphrase. However, if the client is a program, then the end result is to decompose and distribute the program into autonomous pieces. For example, consider the client-server model of communication as illustrated in Figure 1.Figure 1: Client-server modelPrograms are depicted as circles, and computers are depicted as squares. In this example, a client program wishes to obtain some information located at a server elsewhere on the network. The client then sends a number of request messages to the server, and the server replies with the information. This is a common paradigm in network management: the client is the NOC (Network Operations Center), and the server is a network host or router being managed. The request messages correspond to SNMP GET messages and the responses are SNMP RESP messages.Figure 2: Agent modelThe agent model is depicted in Figure 2. Here, an agent of the client program is co-located with the server. Upon receipt of the client message, the agent initiates a number of local messages to the server,and responds to the client based on the server’s responses and some computation. This approach has a number of benefits:•reduced network trafficCommunication between client (via the agent) and server is local until the final result is calculated and returned. This especially important if the management action is to diagnose and respond to an already congested network.•distributed computationSome of the client’s computation is offloaded to the agent running on the server. This has two benefits. First, this reduces the load and resource consumption on the client application. In the case of network management, we could imagine a single NOC administering hundreds of nodes.By offloading a small computation to each node, we barely disturb the node, but we greatly benefit the client. Second, the resulting distributed computation is more modular and easier tounderstand.•low latencyBy localizing communication between agent and server, related information is more accuratebecause of reduced latency. Consider n queries made to the server for related information. In the client-server model, each query is separated by a potentially large gap during message transit, such that a (relatively) large amount of time may pass between the first and (n-1)th message, diluting the relationship between the information contained in the messages. In contrast, the agent model reduces the latency between each server message, as well as the latency of the overall macro-operation.•fault toleranceThe agent model is more fault tolerant in two ways. First, messages between the server and the agent are local, and thus essentially reliable, in contrast to messages across the network. Second, both the code and data relevant to pieces of a distributed computation are condensed into a single entity: the agent. In the client-server case, there is often data duplicated between client and server, which can become inconsistent during partial failures.•secure communicationIf messages between client and server are to be authenticated and/or encrypted, the benefit of the agent paradigm is magnified, simply because the number of messages that traverse the untrusted network, and thus the number of messages to encrypt/sign, is reduced. Assuming that the agent is authenticated when it is spawned at the server, all of its communications with the server mayoccur without authentication because they are local.There are additional benefits if agents are persistent; that is, they reside on the server for an extended period, reacting to events. Two relevant kinds of events are timeouts and server notifications. If agents may wake up at periodic intervals, they may poll the server and assess current conditions, obviating potential network traffic due to client polling. Additionally, they may react directly to server notifications. In the traditional SNMP model, the server may notify the client of events by sending a TRAP message. In the agent model, the TRAP could instead notify the agent, which may react locally or forward the information to the client. In the former case, we reduce the load on the client and the latency of the response.Finally, if agents may communicate among themselves, then the client application need be involved even less often. We could imagine an application structured hierarchically, such that certain agents defer to others in coordinating events.2.2Challenges of AgentsAgents are not a panacea, however. By increasing the “vocabulary” of the server with agent computation, we increase the potential for malicious or inadvertent damage to the server. In an untrusted setting, we must provide security commensurate with the flexibility available in an agent environment. Fortunately, most researchers in agent technology consider security a solved problem for special-purpose environments3 by employing cryptographic techniques; more general solutions, such as resource control4,5 are also possible.Perhaps more problematic is designing an agent environment amenable to non-experts. In principle, the agent paradigm should allow most anyone to write small bits of computation to act on their behalf, but this is difficult for non-experts in current agent implementations3. However, in the area of network management, this issue is less problematic because network managers are not “non-experts.” Our experience within the active network context has borne out both of these conclusions, as we describe in more detail in Section 4. In the next section we shall discuss standard network management models to place some context for our proposed solutions.3 Network ManagementNetwork Management broadly describes all activities needed to insure a network is behaving as expected. OSI spent a considerable amount of time in the early 1990’s defining “Network Management.” The following five functional areas have since been accepted as the de facto definitions in both the Telecommunication and Internet management communities6: fault, performance, accounting, security, and configuration and name management. Each functional area requires extracting information from managed devices. For example, fault management tasks must gather information about the topology of the system such as if an interface or gateway is alive, p erformance management tasks are interested in statistical metrics such as interface load or average queue length and c on figuration and name management might query device MAC or IP addresses. In the following section, we will describe two popular approaches to managing networks: ad-hoc and centralized.3.1Popular approachNetwork management is a constant cycle of monitoring, analyzing and controlling different components of the network. There are two popular approaches to building network management applications. Both approaches use the client/server model.The first approach, ad-hoc management, uses a set of customized, independent scripts. Scripts are usually written to focus on a very small, discrete task such as calculating the load for a given interface or checking configuration parameters for a device. The manager typically runs the script by manually sending it to a managed device. This is a very ad-hoc and popular approach to network management because it is simple. However, ad-hoc management is very costly and inefficient because it places the complexity of managing the network on the manager; manually monitoring and fixing erroneous behavior is very time consuming and inefficient. The positive aspect to ad-hoc scripts is that management tasks are divided up into modular components. Modularity allows the manager to write flexible management applications that can easily be extended as the network evolves.The second approach to network management is a centralize approach. In a centralized approach, one application is developed to handle all five areas of network management. This tactic isdepicted in Figure 3.Figure 3: Centralized Network Management modelIn the depicted network, we have a centralized NOC with three different managed devices. Each device exports some local information. Traditionally, the local information is formatted as a Management Information Base (MIB). It is not necessary that each device supports the same API to access local information and hence the shapes in the figure are different. For example, our application in Figure 3 could query Device A using SNMP, but query Device B and C using CLI (Command Line Interface). Our example shows one large application with five management tasks. Each task is responsible for polling the devices for information, making a centralized decision on the network’s health and then possibly initiating a control mechanism to change the device’s state.The centralized management model is complex and inextensible. If a new device is added to the managed set or a known device extends its set of exported local information (new MIB or device OS), the NOC must halt management applications and recompile to include new information. It is not an acceptable solution to halt network management software applications for a critical network system. This model also suffers from a limited or unsafe API between the NOC and its managed devices. For example, the SNMP API only allows three types of functions: get, set and trap. Get and its various forms are used for querying the managed device. Set is used as a control mechanism to change state. It is important to note that not all variables are write enabled. Trap is used by the SNMP agent (server) to notify the NOC. An SNMP agent is capable of monitoring individual variables for some condition then notifying the NOC once the condition becomes true1. Such limited API methods force the NOC to use a polling mechanism to determine the health of the network, which may cause network congestion. A positive aspect to the centralized model is that it naturally provides a global view of the network.By combining the positive aspects of both the ad-hoc and centralized management models, we can create a management infrastructure that is modular, extensible and capable of managing a network from a global view. Agent technology provides us with the best of both worlds.4Agents and Network ManagementIn this section, we examine more closely how the agent model can be applied to improve automation and address the complexity problem in network management.A common characteristic for all agent-based models is extensibility. Agents can be deployed and removed dynamically over the network, hence the computation required for a management task can be changed in a flexible manner. Agents nicely accommodate the diversity and dynamism of requirements from network management.Much of our recent research has examined applying ephemeral, mobile agents to the task of network management. This work has been done in the context of an active, or programmable, network, called PLANet7. In PLANet, packets consist not of the header and data fields of traditional packets, but instead, of packet programs, not unlike mobile agents. Packet programs are written in a small, script-like language called PLAN, the Packet Language for Active Networks4. PLAN provides simple primitives for data aggregation, control-flow, and computation, but is expression-limited so that all PLAN programs are guaranteed to terminate. In particular, there is no way in the language to express infinite loops or recursive function calls.In previous work we used PLAN to write small diagnostic programs useful for network management. For example, a simple ping program implemented in PLAN is depicted below:fun ping (src:host, dest:host) : unit =if (not thisHostIs(dest)) thenOnRemote(|ping|(src,dest), dest, getRB(), defaultRoute)elseOnRemote(|ack|(), src, getRB(), defaultRoute)The program works as follows. In the case that the packet has not reached its destination, the first case applies, as the call to thisHostIs(dest) fails, and so the packet is resent towards its destinationusing the OnRemote primitive. The details of OnRemote are unimportant; the key elements to notice are the first and second arguments: |ping|(src,dest) indicates that the function ping, with argumentssrc and dest, should be evaluated at the destination dest, the second argument. Once the destination is reached, the second case will execute, causing a packet to be sent back to the source, and invoking a small acknowledgement function ack (not shown).PLAN can express more interesting programs as well. For example, we can write traceroute, which aggregates the list of nodes traversed between a source and a destination, and even trace-net, in which packets fan out and discover the topology of the network, within certain parameters (such as hop distance from the source). Both are useful for discovering inconsistencies in routing tables, and for diagnosing downed nodes and/or links. The interested reader is referred to8 for a more thorough treatment of PLAN programming.We have also used PLANet as the basis for more complicated service management functions, such as device queue management (perhaps to implement QoS)6, and packet filtering9. In both cases, we can take advantage of PLANet’s extensibility, which allows network nodes to be augmented with new, persistent functionality available to PLAN programs, termed services. For example, we can load a new queuing service, and allow it to be initiated, configured, and/or terminated by a PLAN management packet. To make sure that arbitrary packets cannot change node parameters, PLAN is augmented with security services8 that allow authenticated packets to access services commensurate with their level of privilege. For example, a user’s packet would not be privileged enough to access the service that allows a node to be extended, whereas a management packet would authenticate itself with the node, and thus gain access to additional services.We are currently examining how PLAN may be used as a mobile agent technology for management outside of the active network context.4.1Management ModelsPLANet uses one sort of agent model in implementing network management. Various other models exist based on agent characteristics. These characteristics can be examined along three discrete dimensions: mobility, persistence and cooperation. This classification is a good starting point for analyzing agent-based models in a more structured manner.Figure 4: Agent CharacteristicsPersistent agents run indefinitely to perform long-term computations. Ephemeral agents, on the other hand, perform relatively shorter computations and terminate. Although the distinction may seem vague, one can think of persistent agents as executing in an infinite loop where termination depends on special conditions while ephemeral agents are designed to terminate and loops are bounded. Management tasks that depend on long-term system state are candidates for persistent agents. Ephemeral agents can handle tasks that depend on instantaneous state or no state at all.Stationary agents perform their computation at a single node. Mobile agents, on the other hand, may move from node to node during their computation. Tasks local to a node may be performed by stationary agents while tasks with topological dependencies may be performed by mobile agents. Stationary agents may also perform global tasks if they are persistent and able to cooperate withremote agents. Hence, the choice between stationary and mobile models depends on the agent characteristics in other dimensions as well as the requirements of the particular management task.Finally, cooperative agents communicate with peer agents at other nodes to perform their computation. Non-cooperative agents act alone. Note that in both cases agents may communicate with higher-level management applications. Tasks that require a global view to make local decisions are handled by cooperative agents while tasks that have only local dependencies are handled by non-cooperative agents.4.2ApplicationsThere are eight possible models based on the classification in Figure 4. Choice of a model depends on the properties of particular management tasks. The PLANet model described above used themobile/ephemeral/non-cooperative model. In this section, we focus on two other models with potential applications: the stationary/persistent/non-cooperative and stationary/persistent/cooperative models. We also examine how agents can be used to introduce new network services in the context of the stationary/persistent/cooperative model.Stationary/Persistent/Non-cooperative modelConsider the task of monitoring the running mean and variance of the amount of traffic going out from each interface of each router in our network. This is an informational management task, i.e. agents do not change any operational properties on the routers. The computed information may be used for future system planning, or for (figuring out) load distribution over the network.This task is best suited by a stationary/persistent/non-cooperative model. Agents need to be persistent to periodically get the number of bytes sent out from each interface, update the mean and variance values by using an appropriate algorithm, and log the computed values periodically (much less often than the sampling frequency) to an external application. Mobility and cooperation of agents, furthermore, do not provide any additional benefits. This model has all the benefits described in Section 2 over the traditional management model based on centralized polling.Stationary/Persistent/Cooperative modelConsider the logging task performed by the agents in the above example. Rather than each agent logging to a central application, in a cooperative model, agents can form a hierarchy by using a distributed spanning tree algorithm, and log to their parent agents. In general, the cooperative model allows the agents to choose and form the right communication topology for efficiency in terms of bandwidth, delay, and scalability.Agents can be used not only as watchers of the network, but as implementers of its services, as proposed by active networks. The stationary/persistent/cooperative agent model is well-suited to this task for three reasons. First, because agents are long-lived, they can react to network events, such as timeouts and user- or network-requests. Second, because agents cooperate, large services can be broken down into smaller modular components that are easier to understand. Furthermore, communication may occur with agents at other nodes without loss of abstraction. Finally, services may be easily evolved by deploying new agents or upgrading old ones.Consider the example of providing guaranteed quality of service (QoS) to network clients. Many routers and switches provide low-level mechanisms (packet filters, priority queues, traffic counters, etc.) for supporting QoS, and higher level protocols, such as IntServ10 and DiffServ11 , are built on top of these mechanisms. We believe that agents can be used to implement these services in a modular and extensible manner. Persistent agents at QoS-capable nodes can monitor and control the filtering, classification, queuing and other mechanisms that the underlying device exports. Network wide QoS objectives can be achieved by communicating the QoS state between node agents. Furthermore, the algorithms and policies that govern the allocation of resources can be changed dynamically. Implementing DiffServ with this agent model is especially appealing because the domain can tailor its implementation based on its own constraints and objectives, and can update the system dynamically to accommodate new requirements. We are currently working on the design and implementation of anagent-based QoS management model on commercial network devices that allow dynamic loading and execution of mobile programs.5 Related WorkThe research community has recognized some of the problems that we have mentioned, and a number of different approaches have been proposed. RMON 1 and 2 (Remote Network Monitoring)5 were developed to relieve the NOC from load incurred during monitoring. RMON is a specification that presents a higher-level MIB that combines lower-level functions into single entities so as to reduce the load on the NOC, offsetting some monitoring responsibility to the managed device. However, this monitoring ability is fundamentally fixed; the manager could not, for example, specify new filters at runtime.AgentX12 was developed with goals similar to ours: to reduce the complexity of management software, and to allow it to change at runtime. These goals are achieved by allowing traditional SNMP agents to be programmed in a modular, extensible manner. AgentX logically splits the traditional SNMP agent in two; a master and one or more subagents. The master agent handles all NOC SNMP requests and passes the information on to the appropriate subagent. Each subagent manages a MIB. If a device or system wants to support new MIB or extend an existing MIB, a new subagent can be loaded and initialized to support the new information. This approach is still fundamentally data-driven, however, and therefore does not offset the complexity of the management application.Agents have been a popular research topic during the last decade, and a number of agent systems already exist3. Several agent systems cite network management as an applicable domain, but none that we know of have developed such applications to an appreciable degree.6 ConclusionAs networks filter into more aspects of our lives, the importance of the network management system in watching, configuring, and protecting network functions increases dramatically. Current network management models place little burden on the managed device but tremendous burden on the management applications, dramatically increasing their complexity. Furthermore, standard models are fairly rigid, making it difficult to accommodate new services and advances in networking technology. To solve these problems of high complexity and rigidity, and therefore scalability, we have presented new models of network management that move some computational ability to managed devices through the use of agents, or more generally, active networks. Our classification of agent models in this context serves as a means for examining the tradeoffs of various approaches. In particular, within this context we have described prior work in the active network system, PLANet7, as well as presented two other feasible agent models for network management along with example applications.。


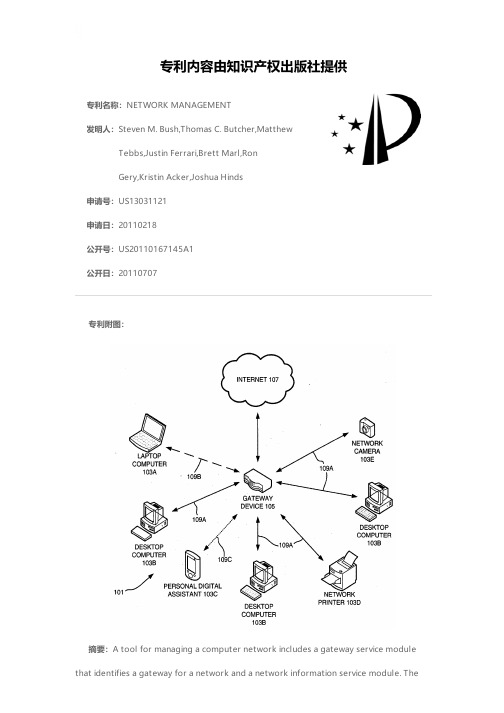
专利名称:NETWORK MANAGEMENT发明人:Steven M. Bush,Thomas C. Butcher,MatthewTebbs,Justin Ferrari,Brett Marl,RonGery,Kristin Acker,Joshua Hinds申请号:US13031121申请日:20110218公开号:US20110167145A1公开日:20110707专利内容由知识产权出版社提供专利附图:摘要:A tool for managing a computer network includes a gateway service module that identifies a gateway for a network and a network information service module. Thenetwork information service module identifies devices in the network, determines at least one property for each of the identified devices, and creates a network information data structure for storing device properties. A communication agent service module transmits at least one determined device property to other agent service modules associated with the network, receives at least one device property from another agent service module associated with the network, and provides the received at least one property device to the network information service module. A method of monitoring a computer network is also provided. The method includes identifying devices in a network, determining at least one property for each of the identified devices, receiving at least one determined device property from another device the network, and creating a network information data structure for storing the determined device properties.申请人:Steven M. Bush,Thomas C. Butcher,Matthew Tebbs,Justin Ferrari,Brett Marl,Ron Gery,Kristin Acker,Joshua Hinds地址:Redmond WA US,Seattle WA US,Seattle WA US,Seattle WA US,Seattle WA US,Kirkland WA US,Seattle WA US,Duvall WA US国籍:US,US,US,US,US,US,US,US更多信息请下载全文后查看。

专利名称:NETWORK MANAGEMENT SYSTEM 发明人:KOMIYA, Noriyuki申请号:EP01917631.2申请日:20010329公开号:EP1376941B1公开日:20091111专利内容由知识产权出版社提供摘要:The present invention provides a network management system where as setup processing of a target network can be done at other network, it is possible to perform a network setup from a remote place. The network management system according to the present invention includes a plurality of networks to which equipment is connected and a management node connected between the plurality of networks, for exchanging setup information on equipment between different networks through the management node. The management node includes: first transmission/reception means which performs data communications with one network, second transmission/reception means which performs data communications with another network, setup information store means which stores setup information on the above-mentioned another network, setup information frame analysis means which analyzes a setup information frame received from the above-mentioned one network and making the setup information store means store the setup information on the above-mentioned another network, setup means which sets up the above-mentioned another network by using the setup information on the above-mentioned another network, setup state acquisition means which acquires a setup state of the above-mentioned another network from equipment which is connected to the above-mentioned another network and making the setup information store means storethe setup state as the setup information on the above-mentioned another network, and setup information frame forming means which forms a setup information frame in order to transmit the setup information on the above-mentioned another network to the above-mentioned one network and transmitting to above-mentioned one network.申请人:MITSUBISHI ELECTRIC CORP地址:JP国籍:JP代理机构:Gleiter, Hermann更多信息请下载全文后查看。


(DRAFT)Architectural and Engineering Issues for Building an Optical InternetTing Wo ChungBell CanadaTWChung@on.bell.caJohn CoulterBell CanadaJcoulter@on.bell.caJeff FitchettStentor Canadian Network ManagementFitchettjw@Stentor.caSam MokbelONet Networking IncSmokbel@enfm.utcc.utoronto.caBill St. ArnaudCANARIE IncBill.st.arnaud@canarie.caLast Revised 09/22/98, 1998This document will be continually updated as the network deployment and design evolves. The latest version of this document can be found atAbstractThis document describes the architectural and engineering issues of building a wide area optical Internet network as part of the CANARIE advanced networks program. Recent developments in high density Wave Division Multiplexing fiber systems allows for the deployment of a dedicated optical Internet network for large volume backbone pipes that does not require an underlying multi-service SONET/SDH and ATM transport protocol. Some intrinsic characteristics of Internet traffic such as its self similar nature, server bound congestion, routing and data asymmetry allow for highly optimized traffic engineered networks using individual wavelengths. By transmitting GigaBit Ethernet or SONET/SDH frames natively over WDM wavelengths that directly interconnect high performance routers the original concept of the Internet as an intrinsically survivable datagram network is possible. Traffic engineering, restoral, protection and bandwidth management of the network must now be carried out at the IP layer and so new routing or switching protocols such as MPLS that allow for uni-directional paths with fast restoral and protection at the IP layer become essential for a reliable production network. The deployment of high density WDM municipal and campus networks also gives carriers and ISPs the flexibility to offer customers an integrated and seamless set of network services: IP directly over WDM for large volume IP networks and regional local loops, IP over ATM for VPNs and small bandwidth networks and IP over SONET for multiplexing with traditional TDM services. The cost of such a network may also prove to be several orders of magnitude less expensive than today's current Internet architecture.Table of Contents1.0 What is an optical Internet?41.1 High Density Wave Division Multiplexing41.2 Why build an optical Internet?61.3 Internet Traffic growth71.4Internet Applications and Data Types81.5Definition of bandwidth92.0 Internet traffic characteristics112.1 Fractal nature of data 112.2 Asymmetric Tx/Rx122.3 Server Bound Congestion143.0 Transport Options -WDM, SONET/SDH or ATM?163.1 Optical Internet versus Optical ATM163.2 Optical Internet versus Packet over SONET/SDH183.3 WDM Switched Circuits vs WDM datagrams193.4 Framing - SONET/SDH, Gigabit Ethernet, Frame Relay204.0 Fundamentals of Optical Networking234.1 Fiber types23 4.2 Lasers 244.3 EFDAs244.4 Optical Couplers254.5 Electrical Repeaters254.6 Transponders264.7 Optical Add Drop Mux, Cross Connects and Switches264.8 WDM standards and interoperability 275.0 Possible Optical Internet architectures285.1 Basic Architecture of an Optical Internet285.2 WAN versus MAN optical Internet networks315.3 Hybrid Optical Network32 5.4 Using both sides of a fiber ring355.5 Optical IP municipal area network375.6 Optical Internet Exchange396.0 Traffic Engineering, Restoral, QoS and Network Management416.1 Traffic Engineering416.2 Layer 3 Restoral 416.3 QoS issues436.4 Network Management Issues447.0 Future costing and marketing scenarios457.1 Long Haul IP over WDM Costing457.2 Municipal IP over WDM costs488.0 CA*net 3 – Canada’s National Optical Internet Project499.0 Conclusions521.0 What is an Optical Internet?For the purposes of this document an optical Internet is defined as any Internet network where the network link layer connections are "dedicated" wavelengths on an Wave Division Multiplexed (WDM) optical fiber directly connected to a high performance network router. The high performance network router replaces traditional ATM and SONET/SDH switching and multiplexing equipment in that it is the essential statistical multiplexing device that controls wavelength access, switching, routing and protection. SONET/SDH and ATM technology are based on the circuit switched paradigm that has been the fundamental underlying concept of telecommunications design from the days of Graham Bell. The CANARIE National Optical Internet Project for the first time, is designed to be a true link layer datagram network as envisaged twenty years ago by the early Internet pioneers Vint Cerf an Bob Kahn [CERF74]. By this minimum definition for an Optical Internet, the architectural and design issues are really not that much different from building a leased line Internet network or one made with ATM Permanent Virtual Circuits. However, traffic engineering of the network can now be only accomplished at the IP layer as there is no underlying transport layer and so protocols like Multi Protocol Label Switching (MPLS) become essential for the effective management and engineering of the network.However, with an optical network using dedicated wavelengths, or lambdas, there is considerable more flexibility in architectural topology and the potential to eventually move to an optical switching and all optical routing architecture as these technologies mature.1.1 High Density Wave Division MultiplexingIn the past carriers multiplexed different network services into a single transport stream. The most common the underlying transport mechanism was SONET/SDH time division multiplexing systems. More recently ATM has taken on a larger role, particularly in the broadband carrier market as a "cell" or "packet based" multiplexing schema. However with the advent of high density WDM networks it is possible to conceive of "optical" multiplexed telecommunication services where different wavelengths can support different "electrical" multiplexed services. For example, a number of wavelengths can be dedicated to a high bandwidth optical IP network as further described in this document, while others can be dedicated to optical ATM networks and finally other wavelengths can be dedicated to traditional SONET/SDH services that support a number of overlay network protocols including IP and ATM.The attraction of "optical" multiplexed networks is that carriers can now offer a suite of services and protocols to customers based on the customer's own specific requirements and needs. This suite of services can range from simple dark fiber through to broadbandoptical IP networks to high end quality of service virtual private networks running on ATM over SONET or WDM.It is conceivable that future Internet networks may be a seamless composite of a variety of transport protocols, each on their own dedicated wavelength. The following diagram illustrates a possible future network Internet architecture that integrates IP over WDM with ATM and SONET services. The IP over WDM might be used for high volume, best efforts computer to computer traffic, while IP over ATM might be used to support VPNs and mission critical IP networks while IP over SONET would be used to aggregate and deliver traditional IP network services that are delivered via T1s and DS3s .Figure 1.1 Integrated Optical InternetCurrently carriers are deploying up to 16 wavelength, or "lambda" WDM systems. A number of manufacturer's have announced 32 and 96 wavelength systems and researchers in various laboratories are working on 200 and 1000 wavelength systems.In the next few years network bandwidth will dramatically increase as these very high density WDM systems are deployed. In fact it is quite likely that the growth of network bandwidth will far exceed the growth of computing power as stipulated by Moore's law. This will have a profound impact on the future architecture of future computer data networks, as the computer and not the network may be the controlling element for network design, quality of service and advanced network applications.Figure 1.2 Growth of Bandwidth versus CPU1.2 Why Build an Optical Internet?There is considerable debate in the telecommunications industry about the best technology for transporting IP services. Carriers are generally more committed to ATM as the common network technology. On the other hand there are many in the Internet community who believe that soon, just about everything will ride over IP and a network optimized to carry IP is the most appropriate direction. While there are compelling arguments for both sides of the debate the most likely outcome is that IP over ATM and optical IP services will exist in parallel to meet the spectrum of customer requirements for IP networking. This will be particularly true with the advent high density WDM systems which can support a multitude of transport service delivery mechanisms from traditional SONET/SDH services to the new optical ATM and IP architectures.The case therefore for an optical Internet essentially rests on the predicted volumes for Internet traffic growth and the expected predominant types of Internet applications. If Internet traffic continues to grow exponentially and for the bulk of traffic all that is required is a "best efforts" or an "ensured" delivery service then high volume IP pipes would seem to be the most appropriate technology.In additional to accommodating the huge anticipated capacity requirements of the Internet, an Optical Internet would be more efficient. As modern network overlays become increasingly survivable and robust, the fault tolerance built into the core transport network may becoming increasingly redundant, particularly for IP networks. Efficiencies and cost savings can be gained from single layer management of survivability. Fault tolerant features are largely inherent in IP.There is little doubt that there will always be a demand for network solutions that provide guaranteed qualities of service and well managed traffic engineering solutions, particularly for mission critical applications. If an IP network is capable of delivering such end to end service is a matter of debate and it is quite possible that ATM or othernetwork technologies are best suited for that type of requirement. However, if the volume of "best efforts" or "ensured" IP traffic is the overwhelmingly predominant traffic type then it perhaps make sense to build a network that, first and foremost, can support that type of traffic. This does not mean that one network technology will displace another. The power of WDM is that both network solutions can be accommodated in a modern network infrastructure.With high density WDM neither the "bell heads" or the "net heads" are losers in the protocol wars. The winner is the customer in terms of increased choice in network offerings, services and cost savings.1.3 Internet Traffic GrowthInternet traffic volumes continue to grow exponentially. Current predictions indicate thatFigure 1.3 Growth of Date Traffic versus Voice TrafficA conservative estimate of Internet traffic growth is that it will double every 6 months. With this growth rate the aggregate bandwidth required for the Internet in the US will be about 35 Tbps (Terabits per second) by 2001-2002 [OLDY98]. As such a number of carriers are already planning to deploy OC-48 ATM and SONET/SDH networks for the sole purpose of delivering Internet data.With the advent of IP telephony, high speed connections to the home via cable modems or ADSL, fiber to the curb and the advanced applications that are being developed on Internet 2 and CA*net II there is every reason to believe that Internet traffic will continue on its exponential growth for the foreseeable future.Given this increasing demand for high bandwidth Internet in the coming years a large part of the debate has centered around the appropriate transport technology that will be used for delivering such bandwidth - ATM, SONET/SDH or WDM optical networks.The appropriate technology choice will be driven largely by the characteristics of future applications. Many people feel that interactive real time multimedia will be the driving application for high bandwidth networks. Such things as tele-immersive virtual reality,3D interactive gaming, distance education and tele-medicine are cited as examples of the future applications that will drive the demand for increased bandwidth. If these do become the dominant IP applications then there is no question there will be requirement for large bandwidth networks. But in addition there are some early indications that existing data applications may grow significantly in size as well and will also drive the demand for large IP pipes.1.4 Classification of Internet Applications and Data TypesApplications on the Internet can be divided into three broad categories based on their unique traffic profiles and network requirements: human to human, human to computer and computer to computer applications.Human to human communications are considered to be those services where a live human being is required at both ends to complete the communications connection. Such applications include voice telephony and video conferencing, but also include the more futuristic applications such as tele-immersive virtual reality and Internet gaming. Human to human communications are the most demanding application of any network technology as the usual human I/O devices, the eyeball and the ear drum, have the limited buffering capability and hence are the least tolerant of delay and jitter in a communications channel.Most human to human communications are also sensitive to the speed of light delay in a network particularly those dependant on a high real time interactivity factor such as Internet gaming and tele-immersive virtual reality. However, when these applications mature in the next 15-20 years there will be an additional bandwidth explosion. Although major network upgrades will be needed to support voice and video on the Internet these services are in fact probably the slowest growing of all communication services. Traditional voice telephony has experienced very little growth in the past few years and video conferencing growth despite all its promises, remains anemic. And ultimately these applications are limited in growth by the number of human beings on the planet and their peculiar habit of requiring sleep approximately 8 hours (depending on life style) every day.Human to computer communications on the other hand has been the success story of the decade. Human to computer communications include the obvious things like the Web,but it also includes such things as voice and video playback services that are just starting to come on line. These applications can be delivered quite effectively over a "best efforts network" as long as there is sufficient buffering at the end points to smooth out the network induced jitter. There is every reason to believe that the exponential growth experienced by this type of communications connection particularly driven by the web should continue, if not accelerate over the coming years,Computer to computer communications may however, be the real driver for advanced networks and bandwidth. Computer to computer communication occurs when no human is required to initiate or terminate the communication. Such things as distributed web caching, multicast feeds, news feeds, batch processing, and database synchronization are typical of computer to computer communication. E-mail and voice mail are also considered to be computer to computer communications because they usually use a store and forward server and don't require relatively immediate connectivity across a network.A best efforts, high bandwidth IP network is generally all that is required to support most computer applications traffic. This type of traffic is in the early stages of growth. New applications being developed in the Next Generation Internet (NGI), Internet 2 andCA*net II programs in such areas distributed human genome sequencing, geo-spatial database mapping, astronomy imaging and database mining promise an even greater growth in this type of traffic.One of the fundamental assumptions for future advanced networks is that real time interactive human to human communications will be the predominant traffic type. Distance education, medical collaboration and tele-immersive virtual reality are cited as common examples of the future telecommunications traffic profile. However, if future networks turn out to be principally used for computer to computer and/or human to computer to communications then this will have a significant impact on the requirements for either a WDM or ATM networks as the network requirements for these applications can be generally best satisfied with a high bandwidth big pipe "best efforts" network. 1.5 Definition of BandwidthOne of the more confusing terms of reference between the traditional telecommunications versus data view of the world is the interpretation and definition of bandwidth.In high speed networks it is common to use the SONET/STM designations for bandwidth or capacity based on the OC-x (Optical Connection) or the international variation of STM-x. These designations for bandwidth are based on the assumption that all Tx/Rx circuits are full duplex balanced symmetrical so the bandwidth ascribed to these designations is for data transmission in one direction. They also do not include any protection bandwidth that may be associated with a given circuit.The data networking world evolved from definitions of bandwidth based on LAN technology. The first widespread LAN technology was based on the ethernet standard which was referred to as a half duplex "broadcast" medium where the Tx/Rx data shared the same link. The bandwidth given in "megabits per second" truly described the total available bandwidth in all directions.As wide area network data becomes increasingly asymmetrical and unbalanced it is important to distinguish the overall capacity of a network versus its nominal capacity as given by the more familiar OC-x or STM-x designations. As such we will try to endeavor to use the data definition of bandwidth throughout this document by stating the unidirectional bandwidth in Gbps.Table 1.0 illustrates the differences in network capacity assuming that both the protection and working fibers of a fiber ring are available for the transmission of data.Designation Nominal Bandwidth Ethernet EquivalentBandwidth Ethernet Equivalent using working and protection fiber 1:1OC-48 2.4 Gbps 4.8 Gbps9.6 GbpsOC-1929.6 Gbps19.2 Gbps38.4 GbpsOC-76838.4 Gbps76.8 Gbps153.6 Gbps Table 1.0 Ethernet Equivalents of Bandwidth on Fiber SystemsIn this document all bandwidth capacities describe the actual physical one way capacity of a given link. Hence a “nominal” OC-48 (2.4 Gbps) bi-directional link would be described as an aggregate bi-directional link capacity of 4.8 Gbps. This is important because in a future traffic engineered DWDM network the bi-directional link may be converted in 2 uni-directional wavelengths. Hence an accurate and common semantic for the underlying bandwidth capacity is critical to the design of future IP/DWDM networks.1.0 Internet Traffic CharacterizationsThe understanding of Internet traffic characterizations is crucial to the design of future networks. In the past there has been little work in this area, but thanks to recent developments at CAIDA (Cooperative Association for Internet Data Analysis) and the IETF IPPM WG ( Internet Protocol Performance Metrics /csg-ippm/) tools and test suites are being developed that will allow network engineers fully understand the unique traffic profile of Internet networks. Early measurements and analysis by these groups point to some intriguing network characteristics that could have a profound effect on the design of Terabit Internet networks.2.1 Fractal Nature of Internet TrafficThere have been several studies [PAXS95] indicating that Internet traffic is fractal or self-similar in nature. Self similar means that traffic on Internet networks exhibits the same characteristics regardless of the number of simultaneous sessions on a given physical link.Traditionally in the telecommunications world traffic volumes aggregate with the number of users on any given link. There are a number of network traffic models [STUC85], based on well established queuing models for predicting traffic loads on voice telephony networks.The fundamental reason why traffic aggregation is well understood on voice networks is that voice traffic aggregates in 64 kbps steps with each phone call, and once a link is saturated no more callers are admitted to the network. However, on the Internet any single computer can use as much bandwidth that is available, and there is no limit on the number of computers that can access the network at any given time. In the event of congestion, all the computers back off and transmit less data until the congestion clears. This saturation and back off results in waves of data on most Internet links for which it is very difficult to predict or model.The consequences of this fractal nature of the Internet is that in order to minimize congestion IP networks must operate at a higher average peak to average load than in a traditional telecommunications network [COFF98]. A possible solution for network operators is to increase the buffer size at admission points into the network to smooth out the bumps and valleys. However, large buffering results in throughput delays of the data.Figure 2.1 Fractal Internet Traffic versus Poisson Voice TrafficThe Internet Performance and Practices Measurement (IPPM) Group have confirmed this fractal nature of the Internet via direct measurement [PAXS96]. Members of IPPM have installed devices called "Surveyors" at several network nodes throughout the US. These nodes collect data from a source node and time stamp the departure and arrival of the data with Global Positioning System (GPS) timers.The IPPM web site /surveyor/support provides a real world example of the "self similar" nature of Internet traffic. As can be seen by these diagrams on that web site the bursty nature of Internet traffic means that even though a data link may have relatively low traffic volumes packet loss and delay can still occur. Conversely, on a heavily loaded link with severe packet loss there can be many instances of short periods of idle time.2.2 Asymmetric Tx/Rx DataAnother unusual characteristic of Internet data is the extreme imbalances that exist between the transmit and receive paths on most Internet links. This characteristic has been observed for some time on Canadian US Internet links where it is quite common 1:10 ratio between outbound traffic to the US and inbound traffic to Canada. The common explanation for this phenomenon is the large number of users who are pulling down web pages from US servers. This phenomena, however has also been observed on other international links and links within the US.The asymmetric data flows are attributed to larger server farms sending out large amounts of data in response to small requests and to the preponderance of users who download web pages. Web server farms tend to be clustered near large Internet service points while users are randomly distributed around the edges of the network. As a result near large interconnection points where web servers are located there is a large asymmetry in Tx/Rx data flows in favour of the Tx path exiting the servers. As the data is distributed to second tier regional networks and from there to local networks and eventually the end user the asymmetry proportionally increases to the receive side in the direction of the user retrieving the web data.Figure 2.3 Examples of Asymmetric Data Flows on the InternetIt is presumed that web caching and mirroring will minimize the Tx/Rx asymmetry in the core of the network, but there will still remain large asymmetries that will vary throughout the day. Time zone changes introduce diurnal asymmetry as parts of the world are logging onto the Internet and accessing web servers on the opposite side of the planet. This diurnal shift in Internet Tx/Rx data is well illustrated by studies done by MCI Engineering on their commercial Internet links [MILL97]/presentations/papers/index.htmlThe consequence of asymmetric is that considerable amount of Internet bandwidth, sometimes close to 50% sits idle, paradoxically at the same time as the bandwidth on the other side of a Tx/Rx pair is totally congested.This condition exists because the telecommunication systems of today are still designed to support primarily voice traffic. The diurnal asymmetry is amplified by the spatialasymmetry of Internet traffic, which is not present in voice network. Even with the latest WDM and SONET/SDH and ATM technologies most networks that are being deployed right now assume that voice will be the dominant traffic type.2.3 Server Bound CongestionThere is increasing evidence that traffic flow on the Internet is limited not by the network itself but by the servers providing data to requests from users. A recent analysis by Christian Huitema of Bellcore [HUIT98] indicates that over 50% of web congestion is due to server related issues.The server congestion is made up of 3 major components: the HTTP session initiation, the DNS lookup request and the actual system specific components such as CPU load, memory and I/O response of the server to the user requests. The HTTP session initiation involves opening the socket up on the server and other related activities. The DNS lookup request is the traditional process of resolving the web DNS name into an IP address.Typically on most Internet links a TCP congestion avoidance window is the controlling factor on Internet throughput [JACO88]. The server specified flow control window, in most cases, is larger than the TCP congestion avoidance window. Congestion avoidance in TCP sessions is a very complex subject and the reader is referred to the following web site for more detail /networking/tcp.htmlThe predominance of the congestion avoidance window being the controlling factor in most TCP sessions may actually, in many cases, be a flow control window bound session, but it is being masked by the silly window syndrome (SWS) in most TCP kernels. If the SWS were not present then there may even be a greater number of TCP sessions that are server bound then is being actually measured by Christian Huitema and others.In the presence of large bandwidth it is increasingly likely that the server flow control window will be the dominant control element in traffic throughput rather than today's congestion window. As a consequence with larger pipes, the Internet throughput will be increasingly server bound, even beyond the 52% server bound congestion experienced today.Unfortunately to the user the Internet will probably always appear largely congested. But there will be little that the network operator can do to obviate the situation except to install mirroring and caching.Undoubtedly servers will increase their flow control window size as they increase in CPU power. But will overall network capacity increase faster than the average CPU performance of most servers, particularly as the number of user connected to the Internet continues to grow unabated?。

第2章网络管理技术概述1.网络管理的目标是什么?答:提高通信网络的运行效率和可靠性。
2.网络管理的内容有哪些?OAM&P(运行、控制、维护、提供)①运行(operation):针对向用户提供的服务而进行的、面向网络整体进行的管理,如用户流量管理、对用户的计费等。
②控制(Administration):针对向用户提供有效的服务、为满足服务质量要求而进行的管理活动。
如对整个网络的管理和网络流量的管理。
③维护(Maintance):针对保障网络及其设备的正常、可靠、连续运行而进行的管理活动,如故障的检测、定位和恢复,对设备单元的测试。
又分为预防性维护和修正性维护。
④提供(Provision):针对电信资源的服务准备而进行的管理活动,如安装设备/软件、配置参数等。
为实现某个服务而提供资源、向用户提供某个服务等属于这个范畴。
3.网络管理的内容可以分为哪些层次?①网元管理层(Network Element Management Layer)提供的管理功能服务实现对一个或多个网元的操作,如交换机、传输设备等的远程操作,设备的软件、硬件管理。
该层管理功能通常就足对网络设备的远稃操作维护功能。
②网络管理层(Network Management Layer)提供的管理功能服务实现对网络的操作控制,主要虑网络中各设备之间的关系、网络的性能、网络的调整和控制、涉及整个网络的事件和日志,如对传输和交换的综合操作控制、网络话务的监视与控制和不同网兀告警的综台分析等。
通常是网络组织和运行管理人员使用该层功能服务。
③服务管理层(Service Management Layer)提供的管理功能服务主要针对网络所提供的服务进行监视和操作控制,管理网络服务的质量和相互关系。
如智能网业务、专线租用业务等的管理。
通常是运行管理部门使用该层功能服务。
④商务管理层(Business Management Layer)提供的服务为网络运行的决策管理提供支持,如网络运行总体目标的确定。