Iptables L7使用方法
- 格式:doc
- 大小:1.02 MB
- 文档页数:13

ptables简介iptables是基于内核的防火墙,功能非常强大,iptables内置了filter,nat和mangle三张表。
filter负责过滤数据包,包括的规则链有,input,output和forward;nat则涉及到网络地址转换,包括的规则链有,prerouting,postrouting和output;mangle表则主要应用在修改数据包内容上,用来做流量整形的,默认的规则链有:INPUT,OUTPUT,NAT,POSTROUTING,PREROUTING;input匹配目的IP是本机的数据包,forward匹配流经本机的数据包,prerouting用来修改目的地址用来做DNAT,post routing用来修改源地址用来做SNAT。
iptables主要参数-A 向规则链中添加一条规则,默认被添加到末尾-T指定要操作的表,默认是filt er-D从规则链中删除规则,可以指定序号或者匹配的规则来删除-R进行规则替换-I插入一条规则,默认被插入到首部-F清空所选的链,重启后恢复-N新建用户自定义的规则链-X删除用户自定义的规则链-p用来指定协议可以是tcp,udp,icmp等也可以是数字的协议号,-s指定源地址-d指定目的地址-i进入接口-o流出接口-j采取的动作,accept,drop,snat,dnat,masquerade--sport源端口--dport目的端口,端口必须和协议一起来配合使用注意:所有链名必须大写,表明必须小写,动作必须大写,匹配必须小写iptable配置实例iptable基本操作iptables -L 列出iptables规则iptables -F 清除iptables内置规则iptables -X 清除iptables自定义规则设定默认规则在iptables规则中没有匹配到规则则使用默认规则进行处理iptables -P INPUT DROPiptables -P OUTPUT ACCEPTiptables -P FORWARD DROP配置SSH规则iptables -A INPUT -p t cp --dport 22 -j ACCEPTiptables -A OUTPUT -p tcp --sport 22 -j ACCEPT 如果你把OUTPUT 设置成DROP,就需要加上这个规则,否则SSH还是不能登录,因为SSH服务职能进不能出。

1iptables与firewalld的关系RHEL7.0以后,使用firewalld服务取代了iptables服务,但是依然可以使用iptables服务,只是默认不开启了,iptables和firewalld都不是真正的防火墙,它们都只是用来定义防火墙策略的防火墙管理工具,是操作系统上的一种服务,将定义好的规则交给内核中的netfilter(网络过滤器)来读取,从而实现防火墙的功能,firewalld和iptables除了可以可以在inbond和outbond方向做策略限制以外,还能实现snat和dnat功能。
注意:firewalld和iptables同时只能运行一种服务,否则会出现不可预知的情况2iptables安装RHEL7.0以后,iptables默认不开启,需要安装iptables服务安装完成后3实验场景3.1源地址转换需求:源地址1(172.16.202.15)需要访问公网目的地址(192.168.111.245),源地址2(172.16.202.16)不需要访问公网。
内网两台服务器,分别为源地址1(172.16.202.15)和源地址2(172.16.202.16),公网出口处有一台centos 7.1的双网卡服务器,一个接口接内网(172.16.202.14),一个接口接外网(192.168.111.63)。
源地址1上首先需要保证和iptables服务器能够互通,并且有去往192.168.111.245的路由,路由下一跳需要指向iptables内网接口(172.16.202.14),由iptables服务器做源nat,把源地址(172.16.202.15)nat成公网接口地址(192.168.111.63),从而可以访问目的地址(192.168.111.245)。
一、首先在源地址1服务器上配置去往192.168.111.245的路由ip route add 192.168.111.245 via 172.16.202.14 //临时添加路由,重启网卡或者系统后,路由会丢失,建议做路由固化路由固化:在/etc/sysconfig/network-scripts目录下,新建一个route配置文件,vi route-eth0,新增一条路由,192.168.111.245/32 via 172.16.202.14,重启网卡即可生效二、iptables服务器上,配置snat策略iptables -t nat -A POSTROUTING -s 172.16.202.15/32 -d 192.168.111.245/32 -j SNAT --to 192.168.111.63注释:-t table table to manipulate (default: `filter') //这个选项指定命令要操作的匹配包的表。

使用iptables命令在Linux中配置和管理防火墙规则防火墙是计算机网络安全的重要组成部分,用于保护计算机免受恶意攻击和未经授权的访问。
在Linux系统中,可以使用iptables命令进行防火墙的配置和管理。
本文将介绍如何使用iptables命令来配置和管理防火墙规则。
一、iptables概述iptables是Linux系统中的一个用于配置和管理防火墙规则的命令行工具。
它可以通过定义规则集来限制、修改和重定向进出系统的网络数据流量。
二、iptables命令基本用法1. 查看当前的iptables规则使用以下命令可以查看当前系统上的iptables规则:```bashiptables -L```该命令将显示当前系统上的所有iptables规则,包括过滤规则、NAT规则和Mangle规则。
2. 清除所有的iptables规则使用以下命令可以清除当前系统上的所有iptables规则:```bashiptables -F```该命令会将所有的iptables规则删除,恢复到默认的配置。
3. 添加一条iptables规则使用以下命令可以添加一条iptables规则:```bashiptables -A [chain] -p [protocol] [--dport] [port] -j [target]```其中,[chain]是要添加规则的链的名称,常见的链包括INPUT、OUTPUT和FORWARD;[protocol]是要过滤的协议,如TCP、UDP或ICMP;[--dport]和[port]用于指定要过滤的端口;[target]是规则的动作,如ACCEPT、DROP或REJECT。
4. 删除一条iptables规则使用以下命令可以删除一条iptables规则:```bashiptables -D [chain] [rule number]```其中,[chain]是要删除规则的链的名称,[rule number]是要删除的规则的序号。

iptables的用法iptables是Linux系统中防火墙工具,用于配置、管理和过滤网络流量。
它可以用于设置各种规则,以控制网络传输,过滤入站和出站流量,并允许或拒绝特定的网络连接。
以下是iptables的常见用法:1. 查看当前的iptables规则:```iptables -L```2. 清除当前的iptables规则:```iptables -F```3. 允许特定IP地址的访问:```iptables -A INPUT -s <IP_ADDRESS> -j ACCEPT```4. 禁止特定IP地址的访问:```iptables -A INPUT -s <IP_ADDRESS> -j DROP```5. 允许特定端口的访问:```iptables -A INPUT -p tcp --dport <PORT_NUMBER> -j ACCEPT```6. 允许特定协议的访问:```iptables -A INPUT -p <PROTOCOL> -j ACCEPT```7. 配置端口转发:```iptables -t nat -A PREROUTING -p tcp --dport <SOURCE_PORT> -j DNAT --to-destination<DESTINATION_IP>:<DESTINATION_PORT>```8. 配置端口映射:```iptables -t nat -A POSTROUTING -p tcp -d <DESTINATION_IP> --dport<DESTINATION_PORT> -j SNAT --to-source <SOURCE_IP>```以上只是iptables的一些常见用法,它还提供了更多高级功能和选项,可以根据具体需求进行配置和使用。

步骤:一,下载所需要的软件包:1,下载新内核linux-2.6.19.7wget [url]/pub/linux/kernel/v2.6/linux-2.6.19.7.tar.bz2[/ur l]2,下载iptables1.3.7wget [url]/projects/iptables/files/iptables-1.3.7.tar.bz2[/ url]3,下载Layer-7补丁,模块协议:[url]/project/showfiles.php?group_id=80085[/url]l7-protocols-2007-01-14.tar.gznetfilter-layer7-v2.9.tar.gz二,配置好内核选项:1.把源码都放在/usr/src下tar jvf linux-2.6.19.7.tar.bz2 #解压cd linux-2.6.19.72.配置内核源码:make m enuconfig(内核配置参照2.6内核编译的说明文档,论坛很多的)3.新内核加进了Proxy Server经常用到几个功能:Core Netfilter configuration(2.6.19.7内核netfilter的string,comment,quota,iprange等模块已集成了)ppp (point-to-point protocol) supportPPP MPPE compression (encryption) #微软加密协议支持,做pptp vpn用得着哦三,L7补丁:1,安装l7协议:tar -zxvf l7-protocols-2007-01-14.tar.gzcd l7-protocols-2007-01-14make install2.L7内核支持补丁:cd /usr/src/linux-2.6.19.7patch -p1 </usr/src/netfilter-layer7-v2.9/kernel-2.6.18-2.6.19-layer7-2.9.patch 3,m ake menuconfig进去把Layer 7 m atch support选上四,编译内核:makemake modules_installmake installreboot选2.6.19.7内核启动五,升级iptables:cd /usr/src/iptables-1.3.7#打上iptables的Layer7补丁patch -p1 < ../netfilter-layer7-v2.9/iptables-layer7-2.9.patchchm od +x extensions/.layer7-testexport KERNEL_DIR=/usr/src/linux-2.6.19.7export IPTABLES_DIR=/usr/src/iptables-1.3.7make BINDIR=/sbin LIBDIR=/lib MANDIR=/usr/share/man install六,测试iptables -I FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT1,用string模块封QQ的DNS:#封tencentiptables -I FORWARD -p udp --dport 53 -m string --string "tencent" --algo bm -j Drop#封,717103636F6D这段数据包特征可用嗅探器获取,#如果直接用string封,但是String模块不支持(估计是字符串匹配的问题)#封qq的话很多wqq,qqxx这样的域名都不能用了所以封是最佳做法iptables -I FORWARD -p udp --dport 53 -m string --hex-string "|717103636F6 D|" --algo bm-j Drop此方法可以使用hosts文件和代理的方式绕过。

Linux命令技巧使用iptables进行高级网络防火墙配置使用iptables进行高级网络防火墙配置在Linux系统中,iptables是一个非常强大的工具,它可以用于配置和管理网络防火墙。
通过使用iptables,我们可以实现高级的网络防火墙配置,以保护我们的计算机和网络资源免受潜在的安全威胁。
本文将介绍一些常用的Linux命令技巧,以帮助你更好地使用iptables进行高级网络防火墙配置。
1. 检查当前iptables规则使用以下命令可以查看当前的iptables规则:```shelliptables -L```该命令将显示当前生效的iptables规则列表,包括输入、输出和转发规则。
通过查看这些规则,可以了解当前系统的网络访问策略。
2. 添加规则可以使用以下命令添加iptables规则:```shelliptables -A <chain> <rule>```其中,`<chain>`表示规则要添加到的链,可以是输入链(INPUT)、输出链(OUTPUT)或转发链(FORWARD)等。
`<rule>`表示要添加的规则内容。
例如,如果要允许来自特定IP地址的HTTP访问,可以使用以下命令:```shelliptables -A INPUT -s <IP地址> -p tcp --dport 80 -j ACCEPT```该命令将添加一个在输入链中生效的规则,允许源IP地址为`<IP地址>`,目标端口为80的TCP连接。
3. 删除规则如果需要删除已添加的规则,可以使用以下命令:```shelliptables -D <chain> <rule_number>```其中,`<chain>`表示规则所在的链,`<rule_number>`表示规则在该链中的序号。
例如,如果要删除输入链中的第一条规则,可以使用以下命令:```shelliptables -D INPUT 1```该命令将删除输入链中的第一条规则。

如何使用iptables命令在Linux中配置防火墙和网络转发由于网络安全的重要性日益凸显,配置防火墙和网络转发成为Linux系统管理员必备的技能之一。
在Linux系统中,iptables命令提供了灵活的方式来配置防火墙规则和网络转发设置。
本文将介绍如何使用iptables命令来完成这些任务。
一、什么是iptables命令iptables是Linux操作系统中一个非常强大的防火墙工具,它可以通过管理网络数据包的流动来控制网络访问权限。
iptables命令可以根据预先定义的规则集过滤网络数据包,拒绝无效或危险的连接,从而保护系统的安全性。
二、基本概念与术语在开始使用iptables命令之前,我们需要了解一些基本的概念和术语。
1. 表(Table):iptables命令使用表来组织和管理规则。
常用的表有:filter、nat和mangle等。
2. 链(Chain):每个表都包含多个链,链是规则的组合。
常用的链有:INPUT、FORWARD和OUTPUT等。
3. 规则(Rule):规则是iptables命令的基本单位,它定义了针对网络数据包的动作和匹配条件。
4. 动作(Action):动作定义了对匹配到的数据包的处理方式,常见的动作有:ACCEPT、DROP和REJECT等。
5. 匹配条件(Match):匹配条件定义了规则在应用到数据包时需要满足的条件。
常见的匹配条件有:source、destination和protocol等。
三、配置防火墙规则配置防火墙规则是保护系统安全的第一步。
使用iptables命令可以轻松地添加、修改和删除防火墙规则。
1. 查看当前防火墙规则首先,我们需要查看当前的防火墙规则,可以使用以下命令:```iptables -L```该命令将列出当前的防火墙规则,包括表、链、规则和动作等信息。
2. 添加规则要添加一个防火墙规则,可以使用以下命令:```iptables -A INPUT -s 192.168.0.0/24 -p tcp --dport 22 -j ACCEPT```该命令将允许来自192.168.0.0/24网段的TCP连接访问本地的SSH 服务。

Iptables的使用各位iptalbes是广泛的使用在linux下的一种防火墙软件,它的主要功能是完成封包过滤,封包重定向,和网络地址转换NA T等功能并且该软件是免费的能够代替昂贵的商业防火墙的功能并且能够用一条命令来控制开启与关闭这是我最喜欢的一点比windows强多了。
首先,现在的LINUX大多都自带了IPTABLES这个软件包了如果没有请大家去这里下载一个吧安装起来也比较方便。
我们先来说说在linux下如何开启和关闭这个防火墙吧。
1如何开启默认情况下如果您安装了LINUX 它都会要求您配置防火墙在启动的时候会有该防火墙的启动项。
也可以手工开启命令[root@localhost /]# service iptables start会出现如下提示Flushing all current rules and user defined chains:[ OK ]Clearing all current rules and user defined chains:[ OK ]Applying iptables firewall rules: [ OK ]也可以用这个方法[root@localhost init.d]# /etc/init.d/iptables startFlushing all current rules and user defined chains:[ OK ]Clearing all current rules and user defined chains:[ OK ]Applying iptables firewall rules: [ OK ]2关闭执行命令:[root@localhost /]# service iptables startFlushing all current rules and user defined chains:[ OK ]Clearing all current rules and user defined chains:[ OK ]Applying iptables firewall rules: [ OK ]也可以用这个方法[root@localhost init.d]# /etc/init.d/iptables stopFlushing all chains:[ OK ]Removing user defined chains:[ OK ]Resetting built-in chains to the default ACCEPT policy:[ OK ]3如何看IPT ABLES里的配置情况这里是我找的一台实验的机器里的配置如下:[root@localhost /]# iptables -LChain INPUT (policy ACCEPT)target prot opt source destinationRH-Lokkit-0-50-INPUT all -- anywhere anywhereChain FORWARD (policy ACCEPT)target prot opt source destinationRH-Lokkit-0-50-INPUT all -- anywhere anywhereChain OUTPUT (policy ACCEPT)target prot opt source destinationChain RH-Lokkit-0-50-INPUT (2 references)target prot opt source destinationACCEPT tcp -- anywhere anywhere tcp dpt:smtp flags:SYN,RST,ACK/SYNACCEPT tcp -- anywhere anywhere tcp dpt:http flags:SYN,RST,ACK/SYNACCEPT tcp -- anywhere anywhere tcp dpt:ftp flags:SYN,RST,ACK/SYNACCEPT tcp -- anywhere anywhere tcp dpt:ssh flags:SYN,RST,ACK/SYNACCEPT tcp -- anywhere anywhere tcp dpt:telnet flags:SYN,RST,ACK/SYNACCEPT udp -- anywhere anywhere udp spts:bootps:bootpc dpts:bootps:bootpcACCEPT udp -- anywhere anywhere udp spts:bootps:bootpc dpts:bootps:bootpcACCEPT all -- anywhere anywhereREJECT tcp -- anywhere anywhere tcp dpts:0:1023 flags:SYN,RST,ACK/SYN reject-with icmp-port-unreachableREJECT tcp -- anywhere anywhere tcp dpt:nfs flags:SYN,RST,ACK/SYN reject-with icmp-port-unreachableREJECT udp -- anywhere anywhere udp dpts:0:1023 reject-with icmp-port-unreachableREJECT udp -- anywhere anywhere udp dpt:nfs reject-with icmp-port-unreachableREJECT tcp -- anywhere anywhere tcp dpts:x11:6009 flags:SYN,RST,ACK/SYN reject-with icmp-port-unreachableREJECT tcp -- anywhere anywhere tcp dpt:xfs flags:SYN,RST,ACK/SYN reject-with icmp-port-unreachable4配置文件存放的位置它的程序文件存在/etc/init.d/iptables里。

iptables 命令参数iptables 命令参数是 Linux 系统中一个非常强大的网络管理工具,可以用来配置和管理网络安全防护、流量的分配和限制等。
本文将分步骤介绍 iptables 命令的用法和一些常见的参数。
第一步:启动和停止 iptables 服务在 Linux 系统中, iptables 服务默认是启动的。
如果需要手动停止或启动 iptables 服务,可以使用如下命令:systemctl start iptables # 启动 iptables 服务systemctl stop iptables # 停止 iptables 服务第二步:查看 iptables 规则我们可以使用以下命令来查看当前系统中的 iptables 规则:iptables -L # 查看所有防火墙规则iptables -L -n -v # 显示更详细的信息其中 -n 参数用于显示 IP 地址而不是 DNS 名称,-v 参数用于显示详细的防火墙规则。
第三步:添加 iptables 规则添加 iptables 规则主要使用 -A 参数,它表示在当前防火墙规则下添加一个新规则。
例如,我们要允许来自 192.168.0.1 的 IP 访问我们的 Web 服务器(例如使用 80 端口),可以使用以下命令:iptables -A INPUT -p tcp -s 192.168.0.1 --dport 80 -j ACCEPT其中,-A INPUT 表示添加一个新规则到 INPUT 防火墙链中,-p tcp 表示限制TCP协议流量,-s 参数指定来源 IP 地址,--dport 参数指定目标端口号,-j ACCEPT 表示允许流量通过。
第四步:删除或清空 iptables 规则如果需要删除或清空 iptables 规则,可以使用如下命令:iptables -D INPUT 1 # 删除第一条 INPUT 规则iptables -F # 清空所有的规则其中 -D 参数用于删除指定的规则,-F 参数用于清空所有的规则。

Linux命令iptables的用法概述i p ta bl es是L in ux操作系统中的一个重要工具,它用于配置L in ux 内核中的网络过滤规则。
通过使用ip ta bl e s,我们可以控制网络数据包的流向和访问权限,实现网络安全的管理和控制。
本文将详细介绍i p ta bl es的用法和常见操作。
一、iptable s简介i p ta bl es是一个内核空间的防火墙工具,用于过滤、修改、传递数据包,提供网络安全的策略控制。
它基于N et fi lt er框架,能够实时监控网络数据包,并根据预先定义的规则进行处理。
ip ta bl es可以在L i nu x终端上运行,并可以通过配置文件持久化规则。
二、iptable s的基本用法1.查看当前i p t a bl e s规则要查看当前i pt ab le s规则,可以使用以下命令:i p ta bl es-L该命令将显示当前的i pt ab le s规则表和链的信息。
2.添加规则要添加一条i pt ab le s规则,可以使用以下命令:i p ta bl es-A<链名><匹配条件><动作>其中,`链名`表示ip t ab le s中的链,如I NP UT、O UT PU T、F OR WA RD 等;`匹配条件`用于对数据包进行匹配,如源I P、目标IP、协议等;`动作`表示对匹配的数据包采取的操作,如A CC EP T、DR OP等。
3.删除规则要删除一条i pt ab le s规则,可以使用以下命令:i p ta bl es-D<链名><规则序号>其中,`链名`表示要删除规则的链,`规则序号`表示要删除的规则在链中的位置。
4.修改规则要修改一条i pt ab le s规则,可以先删除旧规则,再添加新规则。
三、iptable s常用命令示例1.允许所有本地流量i p ta bl es-A IN PU T-i l o-jA CC EP T该命令允许所有本地流量通过IN PU T链。

Linux命令高级技巧使用iptables命令进行网络流量控制iptables是Linux系统中最常用的网络过滤工具之一。
它允许系统管理员通过定义规则来控制网络流量的进出。
使用iptables命令可以有效地防止恶意攻击、保护网络安全和进行流量控制。
本文将介绍一些高级技巧,以帮助读者更好地使用iptables命令进行网络流量控制。
一、iptables概述及基本用法iptables是一款由Linux内核提供的,用于配置Linux内核的防火墙的工具。
它可以允许或拒绝数据包通过系统,同时也可以修改数据包的各种属性。
iptables具有很好的灵活性,在网络安全和流量控制中扮演着重要的角色。
基本的iptables命令用法如下:1. 开启或关闭iptables服务systemctl start iptables # 开启iptables服务systemctl stop iptables # 关闭iptables服务2. 清空已有规则iptables -F # 清空过滤规则iptables -X # 清空用户自定义链3. 默认规则设置iptables -P INPUT DROP # 设置INPUT链的默认规则为拒绝iptables -P OUTPUT ACCEPT # 设置OUTPUT链的默认规则为允许二、高级技巧之网络流量控制1. 限制特定IP地址访问iptables -A INPUT -s 192.168.1.2 -j DROP # 拒绝指定IP地址访问2. 限制特定端口的访问iptables -A INPUT -p tcp --dport 22 -j DROP # 拒绝SSH端口访问3. 允许指定IP地址访问特定端口iptables -A INPUT -s 192.168.1.2 -p tcp --dport 80 -j ACCEPT # 允许指定IP地址访问HTTP端口4. 放行特定MAC地址的流量iptables -A INPUT -m mac --mac-source 00:11:22:33:44:55 -j ACCEPT # 允许指定MAC地址的流量通过5. 源地址伪装iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -j MASQUERADE # 对指定网段的源地址进行伪装6. 限制请求频率iptables -I INPUT -p tcp --dport 80 -m limit --limit 25/minute --limit-burst 100 -j ACCEPT # 限制HTTP请求频率7. 根据连接状态控制流量iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT # 允许已建立或相关的连接通过8. 防止SYN Flood攻击iptables -A INPUT -p tcp --syn -m connlimit --connlimit-above 10 -j DROP # 拒绝连接数超过10个的SYN请求9. 使用IP集合进行流量控制iptables -A INPUT -m set --match-set allowed_ips src -j ACCEPT # 允许IP集合中的地址通过10. 使用日志功能iptables -A INPUT -p tcp --dport 22 -j LOG --log-prefix "SSH:" # 对SSH连接进行日志记录三、总结本文介绍了Linux系统中使用iptables命令进行网络流量控制的高级技巧。

高级技巧使用iptables进行网络流量控制与限速高级技巧:使用iptables进行网络流量控制与限速近年来,随着互联网的迅猛发展,网络流量的控制与限速变得越来越重要。
为了满足不同用户的需求,并保持网络的稳定性,管理员们需要掌握一些高级技巧来进行网络流量的控制与限速。
本文将介绍一种常见而有效的方法,即使用iptables。
一、iptables简介iptables是一个在Linux操作系统中用于管理网络流量的工具。
它允许管理员设置规则来过滤、控制和限制传入和传出的网络流量。
通过定义规则,可以实现网络流量的分类、转发、丢弃等操作,从而帮助管理员控制网络的负载和带宽分配。
二、设置基本的流量控制规则首先,我们需要了解如何设置基本的流量控制规则。
以下是一个示例,展示了如何使用iptables来限制每台主机的上传和下载速度。
1. 设置上传速度限制要限制某台主机的上传速度,可以使用以下命令:iptables -A OUTPUT -m limit --limit 100kb/s -j ACCEPT该命令将限制上传速度为每秒不超过100KB。
2. 设置下载速度限制要限制某台主机的下载速度,可以使用以下命令:iptables -A INPUT -m limit --limit 1mb/s -j ACCEPT该命令将限制下载速度为每秒不超过1MB。
三、设置高级的流量控制规则除了基本的限速功能,iptables还提供了一些高级的流量控制功能,使管理员能够更加精细地控制网络流量。
以下是一些常见的高级技巧。
1. 使用QoS(Quality of Service)进行流量控制QoS是一种网络流量管理机制,通过对不同类型的流量分配不同的优先级,以保证网络的服务质量。
使用iptables,我们可以配置QoS来实现流量的分类和优先级控制。
2. 使用连接跟踪进行应用层的流量控制iptables提供了连接跟踪机制,可以识别并跟踪不同的连接。

IPTABLES(8) iptables 1.4.7 IPTABLES(8)NAMEiptables — administration tool for IPv4 packet filtering and NATSYNOPSISiptables [-t table] {-A|-D} chain rule-specificationiptables [-t table] -I chain [rulenum] rule-specificationiptables [-t table] -R chain rulenum rule-specificationiptables [-t table] -D chain rulenumiptables [-t table] -S [chain [rulenum]]iptables [-t table] {-F|-L|-Z} [chain [rulenum]] [options...]iptables [-t table] -N chainiptables [-t table] -X [chain]iptables [-t table] -P chain targetiptables [-t table] -E old-chain-name new-chain-namerule-specification = [matches...] [target]match = -m matchname [per-match-options]target = -j targetname [per-target-options]DESCRIPTIONIptables is used to set up, maintain, and inspect the tables of IPv4 packet filter rules in the Linux kernel. Several different tables may be defined. Each table contains a number of built-in chains and may also contain user-defined chains.Each chain is a list of rules which can match a set of packets. Each rule specifies what to do with a packet that matches. This is called a ‘target’, which may be a jump to a user-defined chain in the same ta- ble.TARGETSA firewall rule specifies criteria for a packet and a target. If the packet does not match, the next rule in the chain is the examined; if it does match, then the next rule is specified by the value of the tar- get, which can be the name of a user-defined chain or one of the spe- cial values ACCEPT, DROP, QUEUE or RETURN.ACCEPT means to let the packet through. DROP means to drop the packet on the floor. QUEUE means to pass the packet to userspace. (How the packet can be received by a userspace process differs by the particular queue handler. 2.4.x and 2.6.x kernels up to 2.6.13 include the ip_queue queue handler. Kernels 2.6.14 and later additionally include the nfnetlink_queue queue handler. Packets with a target of QUEUE will be sent to queue number ’0’ in this case. Please also see the NFQUEUE target as described later in this man page.) RETURN means stop traversing this chain and resume at the next rule in the previous (calling) chain. If the end of a built-in chain is reached or a rule in a built-in chain with target RETURN is matched, the target specified by the chain policy determines the fate of the packet.TABLESThere are currently three independent tables (which tables are present at any time depends on the kernel configuration options and which modules are present).-t, --table tableThis option specifies the packet matching table which the com-mand should operate on. If the kernel is configured with auto-matic module loading, an attempt will be made to load the appro-priate module for that table if it is not already there.The tables are as follows:filter:This is the default table (if no -t option is passed). Itcontains the built-in chains INPUT (for packets destined tolocal sockets), FORWARD (for packets being routed throughthe box), and OUTPUT (for locally-generated packets).nat:This table is consulted when a packet that creates a newconnection is encountered. It consists of three built-ins:PREROUTING (for altering packets as soon as they come in),OUTPUT (for altering locally-generated packets before rout-ing), and POSTROUTING (for altering packets as they areabout to go out).mangle:This table is used for specialized packet alteration. Untilkernel 2.4.17 it had two built-in chains: PREROUTING (foraltering incoming packets before routing) and OUTPUT (foraltering locally-generated packets before routing). Sincekernel 2.4.18, three other built-in chains are also sup-ported: INPUT (for packets coming into the box itself), FOR-WARD (for altering packets being routed through the box),and POSTROUTING (for altering packets as they are about togo out).raw:This table is used mainly for configuring exemptions fromconnection tracking in combination with the NOTRACK target.It registers at the netfilter hooks with higher priority andis thus called before ip_conntrack, or any other IP tables.It provides the following built-in chains: PREROUTING (forpackets arriving via any network interface) OUTPUT (forpackets generated by local processes)OPTIONSThe options that are recognized by iptables can be divided into several different groups.COMMANDSThese options specify the desired action to perform. Only one of them can be specified on the command line unless otherwise stated below. For long versions of the command and option names, you need to use only enough letters to ensure that iptables can differentiate it from all other options.-A, --append chain rule-specificationAppend one or more rules to the end of the selected chain. Whenthe source and/or destination names resolve to more than oneaddress, a rule will be added for each possible address combina-tion.-D, --delete chain rule-specification-D, --delete chain rulenumDelete one or more rules from the selected chain. There are twoversions of this command: the rule can be specified as a number in the chain (starting at 1 for the first rule) or a rule to match.-I, --insert chain [rulenum] rule-specificationInsert one or more rules in the selected chain as the given rule number. So, if the rule number is 1, the rule or rules are inserted at the head of the chain. This is also the default if no rule number is specified.-R, --replace chain rulenum rule-specificationReplace a rule in the selected chain. If the source and/or des- tination names resolve to multiple addresses, the command will fail. Rules are numbered starting at 1.-L, --list [chain]List all rules in the selected chain. If no chain is selected, all chains are listed. Like every other iptables command, it applies to the specified table (filter is the default), so NAT rules get listed byiptables -t nat -n -LPlease note that it is often used with the -n option, in order to avoid long reverse DNS lookups. It is legal to specify the -Z (zero) option as well, in which case the chain(s) will be atomically listed and zeroed. The exact output is affected by the other arguments given. The exact rules are suppressed until you useiptables -L -v-S, --list-rules [chain]Print all rules in the selected chain. If no chain is selected, all chains are printed like iptables-save. Like every other ipt- ables command, it applies to the specified table (filter is the default).-F, --flush [chain]Flush the selected chain (all the chains in the table if none is given). This is equivalent to deleting all the rules one by one.-Z, --zero [chain [rulenum]]Zero the packet and byte counters in all chains, or only the given chain, or only the given rule in a chain. It is legal to specify the -L, --list (list) option as well, to see the coun-ters immediately before they are cleared. (See above.)-N, --new-chain chainCreate a new user-defined chain by the given name. There mustbe no target of that name already.-X, --delete-chain [chain]Delete the optional user-defined chain specified. There must beno references to the chain. If there are, you must delete orreplace the referring rules before the chain can be deleted.The chain must be empty, i.e. not contain any rules. If noargument is given, it will attempt to delete every non-builtinchain in the table.-P, --policy chain targetSet the policy for the chain to the given target. See the sec-tion TARGETS for the legal targets. Only built-in (non-user-defined) chains can have policies, and neither built-in noruser-defined chains can be policy targets.-E, --rename-chain old-chain new-chainRename the user specified chain to the user supplied name. Thisis cosmetic, and has no effect on the structure of the table.-h Help. Give a (currently very brief) description of the command syntax.PARAMETERSThe following parameters make up a rule specification (as used in the add, delete, insert, replace and append commands).[!] -p, --protocol protocolThe protocol of the rule or of the packet to check. The speci-fied protocol can be one of tcp, udp, udplite, icmp, esp, ah,sctp or all, or it can be a numeric value, representing one ofthese protocols or a different one. A protocol name from/etc/protocols is also allowed. A "!" argument before the pro-tocol inverts the test. The number zero is equivalent to all.Protocol all will match with all protocols and is taken asdefault when this option is omitted.[!] -s, --source address[/mask][,...]Source specification. Address can be either a network name, ahostname, a network IP address (with /mask), or a plain IPaddress. Hostnames will be resolved once only, before the rule is submitted to the kernel. Please note that specifying any name to be resolved with a remote query such as DNS is a really bad idea. The mask can be either a network mask or a plain num- ber, specifying the number of 1’s at the left side of the net- work mask. Thus, a mask of 24 is equivalent to 255.255.255.0.A "!" argument before the address specification inverts thesense of the address. The flag --src is an alias for this option. Multiple addresses can be specified, but this will expand to multiple rules (when adding with -A), or will cause multiple rules to be deleted (with -D).[!] -d, --destination address[/mask][,...]Destination specification. See the description of the -s (source) flag for a detailed description of the syntax. The flag --dst is an alias for this option.-j, --jump targetThis specifies the target of the rule; i.e., what to do if the packet matches it. The target can be a user-defined chain (other than the one this rule is in), one of the special builtin targets which decide the fate of the packet immediately, or an extension (see EXTENSIONS below). If this option is omitted ina rule (and -g is not used), then matching the rule will have noeffect on the packet’s fate, but the counters on the rule will be incremented.-g, --goto chainThis specifies that the processing should continue in a user specified chain. Unlike the --jump option return will not con- tinue processing in this chain but instead in the chain that called us via --jump.[!] -i, --in-interface nameName of an interface via which a packet was received (only for packets entering the INPUT, FORWARD and PREROUTING chains).When the "!" argument is used before the interface name, the sense is inverted. If the interface name ends in a "+", then any interface which begins with this name will match. If this option is omitted, any interface name will match.[!] -o, --out-interface nameName of an interface via which a packet is going to be sent (for packets entering the FORWARD, OUTPUT and POSTROUTING chains).When the "!" argument is used before the interface name, thesense is inverted. If the interface name ends in a "+", thenany interface which begins with this name will match. If thisoption is omitted, any interface name will match.[!] -f, --fragmentThis means that the rule only refers to second and further frag-ments of fragmented packets. Since there is no way to tell thesource or destination ports of such a packet (or ICMP type),such a packet will not match any rules which specify them. Whenthe "!" argument precedes the "-f" flag, the rule will onlymatch head fragments, or unfragmented packets.-c, --set-counters packets bytesThis enables the administrator to initialize the packet and bytecounters of a rule (during INSERT, APPEND, REPLACE operations).OTHER OPTIONSThe following additional options can be specified:-v, --verboseVerbose output. This option makes the list command show theinterface name, the rule options (if any), and the TOS masks.The packet and byte counters are also listed, with the suffix ’K’, ’M’ or ’G’ for 1000, 1,000,000 and 1,000,000,000 multipli- ers respectively (but see the -x flag to change this). Forappending, insertion, deletion and replacement, this causesdetailed information on the rule or rules to be printed.-n, --numericNumeric output. IP addresses and port numbers will be printedin numeric format. By default, the program will try to displaythem as host names, network names, or services (whenever appli-cable).-x, --exactExpand numbers. Display the exact value of the packet and bytecounters, instead of only the rounded number in K’s (multiples of 1000) M’s (multiples of 1000K) or G’s (multiples of 1000M).This option is only relevant for the -L command.--line-numbersWhen listing rules, add line numbers to the beginning of eachrule, corresponding to that rule’s position in the chain.--modprobe=commandWhen adding or inserting rules into a chain, use command to loadany necessary modules (targets, match extensions, etc).MATCH EXTENSIONSiptables can use extended packet matching modules. These are loaded in two ways: implicitly, when -p or --protocol is specified, or with the -m or --match options, followed by the matching module name; after these, various extra command line options become available, depending on the specific module. You can specify multiple extended match mod- ules in one line, and you can use the -h or --help options after the module has been specified to receive help specific to that module.The following are included in the base package, and most of these can be preceded by a "!" to invert the sense of the match.addrtypeThis module matches packets based on their address type. Address types are used within the kernel networking stack and categorize addresses into various groups. The exact definition of that group depends on the specific layer three protocol.The following address types are possible:UNSPEC an unspecified address (i.e. 0.0.0.0)UNICASTan unicast addressLOCAL a local addressBROADCASTa broadcast addressANYCASTan anycast packetMULTICASTa multicast addressBLACKHOLEa blackhole addressUNREACHABLEan unreachable addressPROHIBITa prohibited addressTHROW FIXMENAT FIXMEXRESOLVE[!] --src-type typeMatches if the source address is of given type[!] --dst-type typeMatches if the destination address is of given type--limit-iface-inThe address type checking can be limited to the interface thepacket is coming in. This option is only valid in the PREROUT-ING, INPUT and FORWARD chains. It cannot be specified with the--limit-iface-out option.--limit-iface-outThe address type checking can be limited to the interface thepacket is going out. This option is only valid in the POSTROUT-ING, OUTPUT and FORWARD chains. It cannot be specified with the--limit-iface-in option.ahThis module matches the SPIs in Authentication header of IPsec packets.[!] --ahspi spi[:spi]clusterAllows you to deploy gateway and back-end load-sharing clusters without the need of load-balancers.This match requires that all the nodes see the same packets. Thus, the cluster match decides if this node has to handle a packet given the following options:--cluster-total-nodes numSet number of total nodes in cluster.[!] --cluster-local-node numSet the local node number ID.[!] --cluster-local-nodemask maskSet the local node number ID mask. You can use this option instead of --cluster-local-node.--cluster-hash-seed valueSet seed value of the Jenkins hash.Example:iptables -A PREROUTING -t mangle -i eth1 -m cluster --clus- ter-total-nodes 2 --cluster-local-node 1 --cluster-hash-seed 0xdeadbeef -j MARK --set-mark 0xffffiptables -A PREROUTING -t mangle -i eth2 -m cluster --clus- ter-total-nodes 2 --cluster-local-node 1 --cluster-hash-seed 0xdeadbeef -j MARK --set-mark 0xffffiptables -A PREROUTING -t mangle -i eth1 -m mark ! --mark 0xffff -j DROPiptables -A PREROUTING -t mangle -i eth2 -m mark ! --mark 0xffff -j DROPAnd the following commands to make all nodes see the same packets:ip maddr add 01:00:5e:00:01:01 dev eth1ip maddr add 01:00:5e:00:01:02 dev eth2arptables -A OUTPUT -o eth1 --h-length 6 -j mangle --mangle-mac- s 01:00:5e:00:01:01arptables -A INPUT -i eth1 --h-length 6 --destination-mac 01:00:5e:00:01:01 -j mangle --mangle-mac-d 00:zz:yy:xx:5a:27arptables -A OUTPUT -o eth2 --h-length 6 -j mangle --man- gle-mac-s 01:00:5e:00:01:02arptables -A INPUT -i eth2 --h-length 6 --destination-mac01:00:5e:00:01:02 -j mangle --mangle-mac-d 00:zz:yy:xx:5a:27In the case of TCP connections, pickup facility has to be disabled to avoid marking TCP ACK packets coming in the reply direction as valid.echo 0 > /proc/sys/net/netfilter/nf_conntrack_tcp_loosecommentAllows you to add comments (up to 256 characters) to any rule.--comment commentExample:iptables -A INPUT -s 192.168.0.0/16 -m comment --comment "A pri-vatized IP block"connbytesMatch by how many bytes or packets a connection (or one of the two flows constituting the connection) has transferred so far, or by aver- age bytes per packet.The counters are 64-bit and are thus not expected to overflow ;)The primary use is to detect long-lived downloads and mark them to be scheduled using a lower priority band in traffic control.The transferred bytes per connection can also be viewed through ‘con- ntrack -L‘ and accessed via ctnetlink.NOTE that for connections which have no accounting information, the match will always return false. The "filter.nf_conntrack_acct" sysctl flag controls whether new connections will be byte/packet counted. Existing connection flows will not be gaining/losing a/the accounting structure when be sysctl flag is flipped.[!] --connbytes from[:to]match packets from a connection whose packets/bytes/averagepacket size is more than FROM and less than TO bytes/packets. ifTO is omitted only FROM check is done. "!" is used to matchpackets not falling in the range.--connbytes-dir {original|reply|both}which packets to consider--connbytes-mode {packets|bytes|avgpkt}whether to check the amount of packets, number of bytes trans-ferred or the average size (in bytes) of all packets received sofar. Note that when "both" is used together with "avgpkt", anddata is going (mainly) only in one direction (for example HTTP),the average packet size will be about half of the actual datapackets.Example:iptables .. -m connbytes --connbytes 10000:100000--connbytes-dir both --connbytes-mode bytes ...connlimitAllows you to restrict the number of parallel connections to a server per client IP address (or client address block).[!] --connlimit-above nMatch if the number of existing connections is (not) above n.--connlimit-mask prefix_lengthGroup hosts using the prefix length. For IPv4, this must be anumber between (including) 0 and 32. For IPv6, between 0 and128.Examples:# allow 2 telnet connections per client hostiptables -A INPUT -p tcp --syn --dport 23 -m connlimit--connlimit-above 2 -j REJECT# you can also match the other way around:iptables -A INPUT -p tcp --syn --dport 23 -m connlimit !--connlimit-above 2 -j ACCEPT# limit the number of parallel HTTP requests to 16 per class C sized network (24 bit netmask)iptables -p tcp --syn --dport 80 -m connlimit --connlimit-above16 --connlimit-mask 24 -j REJECT# limit the number of parallel HTTP requests to 16 for the link local network(ipv6) ip6tables -p tcp --syn --dport 80 -s fe80::/64 -mconnlimit --connlimit-above 16 --connlimit-mask 64 -j REJECTconnmarkThis module matches the netfilter mark field associated with a connec- tion (which can be set using the CONNMARK target below).[!] --mark value[/mask]Matches packets in connections with the given mark value (if amask is specified, this is logically ANDed with the mark beforethe comparison).conntrackThis module, when combined with connection tracking, allows access to the connection tracking state for this packet/connection.[!] --ctstate stateliststatelist is a comma separated list of the connection states tomatch. Possible states are listed below.[!] --ctproto l4protoLayer-4 protocol to match (by number or name)[!] --ctorigsrc address[/mask][!] --ctorigdst address[/mask][!] --ctreplsrc address[/mask][!] --ctrepldst address[/mask]Match against original/reply source/destination address[!] --ctorigsrcport port[!] --ctorigdstport port[!] --ctreplsrcport port[!] --ctrepldstport portMatch against original/reply source/destination port(TCP/UDP/etc.) or GRE key.[!] --ctstatus stateliststatuslist is a comma separated list of the connection statusesto match. Possible statuses are listed below.[!] --ctexpire time[:time]Match remaining lifetime in seconds against given value or rangeof values (inclusive)--ctdir {ORIGINAL|REPLY}Match packets that are flowing in the specified direction. Ifthis flag is not specified at all, matches packets in bothdirections.States for --ctstate:INVALIDmeaning that the packet is associated with no known connectionNEW meaning that the packet has started a new connection, or other- wise associated with a connection which has not seen packets inboth directions, andESTABLISHEDmeaning that the packet is associated with a connection whichhas seen packets in both directions,RELATEDmeaning that the packet is starting a new connection, but isassociated with an existing connection, such as an FTP datatransfer, or an ICMP error.SNAT A virtual state, matching if the original source address differs from the reply destination.DNAT A virtual state, matching if the original destination differs from the reply source.Statuses for --ctstatus:NONE None of the below.EXPECTEDThis is an expected connection (i.e. a conntrack helper set itup)SEEN_REPLYConntrack has seen packets in both directions.ASSUREDConntrack entry should never be early-expired.CONFIRMEDConnection is confirmed: originating packet has left box.dccp[!] --source-port,--sport port[:port][!] --destination-port,--dport port[:port][!] --dccp-types maskMatch when the DCCP packet type is one of ’mask’.’mask’ is acomma-separated list of packet types. Packet types are: REQUESTRESPONSE DATA ACK DATAACK CLOSEREQ CLOSE RESET SYNC SYNCACKINVALID.[!] --dccp-option numberMatch if DCP option set.dscpThis module matches the 6 bit DSCP field within the TOS field in the IP header. DSCP has superseded TOS within the IETF.[!] --dscp valueMatch against a numeric (decimal or hex) value [0-63].[!] --dscp-class classMatch the DiffServ class. This value may be any of the BE, EF,AFxx or CSx classes. It will then be converted into itsaccording numeric value.ecnThis allows you to match the ECN bits of the IPv4 and TCP header. ECN is the Explicit Congestion Notification mechanism as specified in RFC3168[!] --ecn-tcp-cwrThis matches if the TCP ECN CWR (Congestion Window Received) bitis set.[!] --ecn-tcp-eceThis matches if the TCP ECN ECE (ECN Echo) bit is set.[!] --ecn-ip-ect numThis matches a particular IPv4 ECT (ECN-Capable Transport). You have to specify a number between ‘0’ and ‘3’.espThis module matches the SPIs in ESP header of IPsec packets.[!] --espspi spi[:spi]hashlimithashlimit uses hash buckets to express a rate limiting match (like the limit match) for a group of connections using a single iptables rule. Grouping can be done per-hostgroup (source and/or destination address) and/or per-port. It gives you the ability to express "N packets per time quantum per group":matching on source host"1000 packets per second for every host in 192.168.0.0/16"matching on source prot"100 packets per second for every service of 192.168.1.1"matching on subnet"10000 packets per minute for every /28 subnet in 10.0.0.0/8"A hash limit option (--hashlimit-upto, --hashlimit-above) and --hash- limit-name are required.--hashlimit-upto amount[/second|/minute|/hour|/day]Match if the rate is below or equal to amount/quantum. It isspecified as a number, with an optional time quantum suffix; thedefault is 3/hour.--hashlimit-above amount[/second|/minute|/hour|/day]Match if the rate is above amount/quantum.--hashlimit-burst amountMaximum initial number of packets to match: this number getsrecharged by one every time the limit specified above is notreached, up to this number; the default is 5.--hashlimit-mode {srcip|srcport|dstip|dstport},...A comma-separated list of objects to take into consideration. Ifno --hashlimit-mode option is given, hashlimit acts like limit,but at the expensive of doing the hash housekeeping.--hashlimit-srcmask prefixWhen --hashlimit-mode srcip is used, all source addressesencountered will be grouped according to the given prefix lengthand the so-created subnet will be subject to hashlimit. prefixmust be between (inclusive) 0 and 32. Note that --hashlimit-src-mask 0 is basically doing the same thing as not specifying srcipfor --hashlimit-mode, but is technically more expensive.--hashlimit-dstmask prefixLike --hashlimit-srcmask, but for destination addresses.--hashlimit-name fooThe name for the /proc/net/ipt_hashlimit/foo entry.--hashlimit-htable-size bucketsThe number of buckets of the hash table--hashlimit-htable-max entriesMaximum entries in the hash.--hashlimit-htable-expire msecAfter how many milliseconds do hash entries expire.--hashlimit-htable-gcinterval msecHow many milliseconds between garbage collection intervals.helperThis module matches packets related to a specific conntrack-helper.[!] --helper stringMatches packets related to the specified conntrack-helper.string can be "ftp" for packets related to a ftp-session ondefault port. For other ports append -portnr to the value, ie."ftp-2121".Same rules apply for other conntrack-helpers.icmpThis extension can be used if ‘--protocol icmp’ is specified. It pro- vides the following option:[!] --icmp-type {type[/code]|typename}This allows specification of the ICMP type, which can be anumeric ICMP type, type/code pair, or one of the ICMP type namesshown by the commandiptables -p icmp -hiprangeThis matches on a given arbitrary range of IP addresses.[!] --src-range from[-to]Match source IP in the specified range.[!] --dst-range from[-to]Match destination IP in the specified range.lengthThis module matches the length of the layer-3 payload (e.g. layer-4packet) of a packet against a specific value or range of values.[!] --length length[:length]limitThis module matches at a limited rate using a token bucket filter. Arule using this extension will match until this limit is reached (unless the ‘!’ flag is used). It can be used in combination with the LOG target to give limited logging, for example.--limit rate[/second|/minute|/hour|/day]Maximum average matching rate: specified as a number, with an optional ‘/second’, ‘/minute’, ‘/hour’, or ‘/day’ suffix; thedefault is 3/hour.--limit-burst numberMaximum initial number of packets to match: this number getsrecharged by one every time the limit specified above is notreached, up to this number; the default is 5.mac[!] --mac-source addressMatch source MAC address. It must be of the formXX:XX:XX:XX:XX:XX. Note that this only makes sense for packetscoming from an Ethernet device and entering the PREROUTING, FOR-WARD or INPUT chains.。
然后保存退出内核配置模式。
# make dep @@@链接程序代码和函数库首先我们查看一下l7filter支持的封禁列表:# ls /etc/l7-protocols/protocols/100bao.pat gkrellm.pat ncp.pat ssdp.pataim.pat gnucleuslan.pat netbios.pat ssh.pat aimwebcontent.pat gnutella.pat nntp.pat ssl.pat applejuice.pat goboogy.pat ntp.pat stun.patares.pat gopher.pat openft.pat subspace.pat armagetron.pat guildwars.pat pcanywhere.pat subversion.pat battlefield1942.pat h323.pat poco.pat teamfortress2.pat battlefield2142.pat halflife2-deathmatch.pat pop3.pat teamspeak.pat battlefield2.pat hddtemp.pat pplive.pat telnet.patbgp.pat hotline.pat qq.pat tesla.patbiff.pat http.pat quake1.pat tftp.patbittorrent.pat http-rtsp.pat quake-halflife.pat thecircle.pat chikka.pat ident.pat radmin.pat tor.patcimd.pat imap.pat rdp.pat tsp.patciscovpn.pat imesh.pat replaytv-ivs.pat unknown.patcitrix.pat ipp.pat rlogin.pat unset.patcounterstrike-source.pat irc.pat rtp.pat uucp.patcvs.pat jabber.pat rtsp.pat validcertssl.pat dayofdefeat-source.pat kugoo.pat shoutcast.pat ventrilo.pat dhcp.pat live365.pat sip.pat vnc.pat directconnect.pat liveforspeed.pat skypeout.pat whois.patdns.pat lpd.pat skypetoskype.pat worldofwarcraft.pat doom3.pat mohaa.pat smb.pat x11.patedonkey.pat msn-filetransfer.pat smtp.pat xboxlive.pat fasttrack.pat msnmessenger.pat snmp.pat xunlei.pat finger.pat mute.pat socks.pat yahoo.pat网友评论内容:现在出了一个新的MSN客户端米鼠MSN。

iptables⽤法和介绍参考视频:/video/BV12f4y1q73o?from=search&seid=11667345261719018642&spm_id_from=333.337.0.01.阿⾥云故障案例搭建keepalived推出havip,19年⽆法使⽤只能使⽤阿⾥云⾃⼰推出的slb负载均衡2.阿⾥云的iptables防⽕墙屏蔽/放⾏端⼝ IP 都可以正常使⽤ iptables共享上⽹端⼝转发/映射⽆法使⽤阿⾥云NAT⽹关,可以实现iptables共享上⽹端⼝转发/映射⽆法使⽤3.阿⾥云云盾故障导致⽤户使⽤什么命令,云盾就删除什么命令时刻备份好数据防⽕墙⼀些名词容器:存放东西表(table):存放链的容器链(chain):存放规则的容器规则(policy):准许或拒绝规则Netfilter 表(tables)链(chain)规则(policy)⼀栋楼楼⾥的房⼦房⼦⾥的柜⼦柜⼦⾥的⾐服,摆放规则⼀:iptables1.iptables⼯作流程1).防⽕墙是层层过滤的,实际是按照配置规则的顺序从上⽽下,从前到后进⾏过滤的2).如果匹配上规则,即明确表⽰是阻⽌还是通过,数据包就不再向下匹配新的规则3).如果规则中没有明确表明是阻⽌还是通过,也就是没有匹配规则,向下进⾏匹配,直到匹配默认规则得到明确的阻⽌还是通过4).防⽕墙的默认规则是所有规则执⾏完才执⾏的注意:屏蔽规则都是放在最上⾯2.表与链简介:iptables 是 4表五链4表: filter表 nat表 raw表 mangle表filter表:负责过滤功能,防⽕墙;内核模块:iptables_filternat表: network address translation,⽹络地址转换功能;内核模块:iptable_natmangle表拆解报⽂,做出修改,并重新封装的功能;iptable_mangleraw表:关闭nat表上启⽤的连接追踪机制;iptable_raw1)filter表防⽕墙:屏蔽或允许端⼝ IPfilter表强调:主要和主机⾃⾝有关,真正负责主机防⽕墙功能的(过滤流⼊流出的数据包) filter表⽰iptanles默认使⽤的表,这个表定义了三个链(chains)企业⼯作场景:主机防⽕墙INPUT 负责过滤所有⽬标地址是本机地址的数据包通俗来说:就是过滤主机的数据包FORWARD 负责转发流经主机的数据包,起转发的作⽤,和NAT关系很⼤ LVS NAT模式,net.ipv4.ip_forward=0OUTPU 处理所有源地址是本机地址的数据包通俗讲:就是处理从主机发出去的数据包2)nat表实现nat功能实现共享上⽹(内⽹服务器上外⽹)端⼝映射ip映射nat 负责⽹络地址转换的,即来源与⽬的IP地址和port的转换应⽤:和主机本⾝⽆关,⼀般⽤于局域⽹共享上⽹或者特殊的端⼝转换服务相关⼯作场景:1.⽤于企业路由(zebra)或⽹关(iptables),共享上⽹(POSTROUTING)2.做内部外部IP地址⼀对⼀映射(dmz),硬件防⽕墙映射IP到内部服务器,ftp服务(PREROUTING)3.WEB,单个端⼝的映射,直接映射80端⼝(PREROUTING)这个表定义了3个链,nat功能相当于⽹络的acl控制,和⽹络交换机acl类似OUTPUT 和主机放出去的数据包有关,改变主机发出数据包的⽬的地址PREROUTING 在数据包到达防⽕墙时,进⾏路由判断之前执⾏的规则,作⽤是改变数据包的⽬的地址,⽬的端⼝等(端⼝转发)PORTROUTING 在数据包离开防⽕墙时,进⾏路由判断之后执⾏的规则,作⽤是改变数据包的⽬的地址,⽬的端⼝等⽣产应⽤:局域⽹共享上⽹查看是否加载iptables相关模块到内核[root@node1 ~]# lsmod | egrep 'filter|nat|ipt'iptable_filter 16384 1iptable_nat 16384 1nf_nat 40960 2 iptable_nat,xt_MASQUERADEnf_conntrack 147456 4 xt_conntrack,nf_nat,nf_conntrack_netlink,xt_MASQUERADEip_tables 28672 2 iptable_filter,iptable_natlibcrc32c 16384 3 nf_conntrack,nf_nat,xfs其中iptables_filter和iptables_nat为核⼼,缺少就⽆法使⽤[root@node1 ~]# systemctl stop firewalld[root@node1 ~]# systemctl disable firewalld然后开启iptables[root@node1 ~]# systemctl start iptables[root@node1 ~]# systemctl enable iptables[root@node1 ~]# iptables -nL 说明:-n是把服务名字转换为端⼝,-L是列出,iptables默认是filter表Chain INPUT (policy ACCEPT)target prot opt source destinationACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHEDACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0ACCEPT all -- 0.0.0.0/0 0.0.0.0/0ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)target prot opt source destinationREJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)target prot opt source destination3.iptables命令参数参数含义-L 显⽰表中的所有规则-n 不要把端⼝或ip反向解析为名字-t 指定表不指定默认为filter表-A append追加,加⼊准许类规则-D delete删除 -D INPUT 1-I insert拒绝类规则放在所有规则最上⾯拒绝类参数含义-p 协议protocal tcp/udp/icmp/all--dport ⽬标端⼝ dest destination 指定端⼝加上协议-p tcp--sport 源端⼝ source 源-s --source 源ip-d --destination ⽬标ip-m 指定模块 multiport(指定多个端⼝)-i input 输⼊的时候从哪个⽹卡进来-o ouput 输出的时候从那个⽹卡出去参数含义-j 满⾜条件后的动作:DROP/ACCEPT/REJECTDROP PEJECT 都是拒绝DROP 会把数据丢掉,不会返回信息给⽤户PEJECT 拒绝返回拒绝信息参数含义-F flush 清除所有规则,不会处理默认规则-X 删除⽤户⾃定义的链-Z 链的计数器清零(数据包计数器与数据包字节计数器)4.配置filter表规则正式配置之前先备份,再清空规则[root@node1 ~]# iptables -F 清除所有规则,不会处理默认规则[root@node1 ~]# iptables -X 删除⽤户⾃定义的链[root@node1 ~]# iptables -Z 链的计数器清零(数据包计数器与数据包字节计数器)[root@node1 ~]# iptables -nL 清空之后的样⼦,然后再进⾏配置Chain INPUT (policy ACCEPT)target prot opt source destinationChain FORWARD (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destination案例:禁⽌访问22端⼝[root@node1 ~]# iptables -A INPUT -p tcp --dport 22 -j DROP说明:-A 后⾯写链名(追加,允许类规则⽤A) INPUT是链名 -p是添加tcp协议 --dport是⽬标端⼝ -j就是说明后⾯是允许还是拒绝-p 协议tcp/udp/icmp(ping命令拒绝访问)/all--dport ⽬标端⼝,指定端⼝加上协议 -p tcp--sport 源端⼝查看iptables表的顺序[root@node1 ~]# iptables -nL --line-number[root@node1 ~]# iptables -D INPUT 1说明:-D 后⾯写链名(删除类规则⽤D) 1是规则表的序号5.屏蔽某个ip[root@node1 ~]# iptables -I INPUT -s 192.168.20.22 -j DROP说明:-I -s 后⾯加IP 由于禁⽌的是IP所以不需要加端⼝[root@node1 ~]# iptables -nLChain INPUT (policy ACCEPT)target prot opt source destinationDROP all -- 192.168.20.22 0.0.0.0/0Chain FORWARD (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destination[root@node1 ~]# iptables -D INPUT 1 删除规则表的禁⽌192.168.20.21的这⾏6.禁⽌某个⽹段连⼊(禁⽌192.168.20.0/24⽹段访问8888端⼝)iptables -I INPUT -s 192.168.20.0/24 -p tcp --dport 8888 -j DROP7.只允许某个⽹段连⼊(允许192.168.20.0⽹段)allow 192.168.20.0/24;deny all;⽅法1:利⽤!进⾏排除iptables -I INPUT ! -s 192.168.20.0/24 -j DROP⽅法2:修改链默认规则,修改为拒绝"添加准许"先配置好规则准许规则再修改默认规则[root@node1 ~]# iptables -A INPUT -s 192.168.20.0/24 -j ACCEPT说明:-A 后⾯写链名(追加,允许类规则⽤A)INPUT是链名 ACCEPT(允许的意思)意思是说:防⽕墙规则允许192.168.20.0⽹段访问然后再修改默认规则[root@node1 ~]# iptables -P INPUT DROP说明:-P是修改默认规则的参数,INPUT链内容就改为DROP[root@node1 ~]# iptables -nLChain INPUT (policy DROP)target prot opt source destinationACCEPT all -- 192.168.20.0/24 0.0.0.0/0ACCEPT all -- 192.168.10.0/24 0.0.0.0/0Chain FORWARD (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destination8.匹配⽹络连接状态(TCP/IP连接状态)-m state --stateNEW:已经或将启动新的连接ESTABLISHED:已经建⽴的连接RELATED:正在启动的新连接INVALID:⾮法或⽆法识别的连接UNTRACKED:表⽰报⽂未被追踪,⽆法找到[root@node1 ~]# iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT[root@node1 ~]# iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT9.拒绝多个端⼝访问[root@node1 ~]# iptables -I INPUT -p tcp -m multiport --dport 2222,12306 -j DROP说明:-m是指定模块 multiport是指定多个端⼝ 2222,12306是指两个端⼝[root@node1 ~]# iptables -I INPUT -p tcp -m multiport --dport 1024:2048 -j DROP说明:1024:2048是指从1024端⼝到2048端⼝都拒绝访问10.匹配ICMPICMP:控制报⽂协议 ping⼀般⽤于禁ping虽然被禁ping但不影响访问⽅法1):通过防⽕墙禁ping[root@node1 ~]# iptables -I INPUT -p icmp --icmp-type 8 -j DROP说明:--icmp-type 8 icmp有很多类型禁ping是第8个⽅法2):通过修改内核禁ping[root@node1 ~]# echo 1 > /proc/sys/net/ipv4/icmp_echo_ignore_all 临时修改[root@node1 ~]# echo 0 > /proc/sys/net/ipv4/icmp_echo_ignore_all 恢复修改将net.ipv4.icmp_echo_ignore_all=1 写⼊到/etc/sysctl.conf 永久修改然后输⼊[root@node1 ~]# sysclt -p 使其⽣效11.限制并发及速率-m limit 限制模块-m ;limt --limt 10/minute #每分钟只能有10个数据包,每秒6个-m ;limt --limt n/{second/minute/hour}说明:指定时间内的请求速率 'n'为速率,后⾯为时间分别为:秒分时-m limit --limit 10/minute --limit-burst 5 #每6秒释放⼯牌给别⼈使⽤--limit-burst[n]说明:在同⼀时间内允许通过的请求'n'为数字,不指定默认为5案例:[root@node1 ~]# iptables -A INPUT -p tcp --dport 22 -j ACCEPT 先允许22端⼝[root@node1 ~]# iptables -A INPUT -p icmp -m limit --limit 10/minute --limit-burst 5 -j ACCEPT[root@node1 ~]# iptables -P INPUT DROP12.防⽕墙规则的保护与恢复iptables-save 默认输出到屏幕iptables-restore写⼊到/etc/sysconfig/iptables案例:iptables-save > /etc/sysconfig/iptables 保存到⽂件中iptables-restore < /etc/sysconfig/iptables 恢复防⽕墙策略filter表⼩结封IP 端⼝⽹段禁⽌ping限制速度和并发iptables filter表所有功能可以在云服务器中使⽤13.实际⽣产⽤法iptables 配置⽅式可以远程访问22端⼝[root@node1 ~]# iptables -A INPUT -p tcp --dport 22 -j ACCEPT[root@node1 ~]# iptables -A INPUT -p tcp -m multiport --dport 443,80 -j ACCEPT[root@node1 ~]# iptables -A INPUT -s 192.168.20.0/24 -j ACCEPT说明:这⾥还可以添加vpn⽹段例:172.16.1.0/241)设置允许本机lo 通讯规则允许本机回环lo接⼝数据流量流出与流⼊[root@node1 ~]# iptables -A INPUT -i lo -j ACCEPT[root@node1 ~]# iptables -I OUTPUT -o lo -j ACCEPT[root@node1 ~]# iptables -P INPUT DROP[root@node1 ~]# iptables -P FORWARD DROP[root@node1 ~]# iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT[root@node1 ~]# iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT⼆:nat1:1)共享上⽹[root@node1 ~]# iptables -t nat -A POSTROUTING -s 192.1683.20.0/24 -j SNAT --to-source 10.0.0.50(公⽹)说明:修改的是POSTROUTING(数据包离开防⽕墙时)链源地址为192.168.20.0/24 经过防⽕墙处理修改为10.0.0.50(公⽹)[root@node1 ~]# echo 'net.ipv4.icmp_echo_ignore_all = 0' >> /etc/sysctl.conf[root@node1 ~]# echo 'net.ipv4.ip_forward = 1' >> /etc/sysctl.conf2)端⼝映射/转发[root@node1 ~]# iptables -t nat -A PREROUTING -d 10.0.0.50 -p tcp --dport 9001 -j DNAT --to-destination 192.168.20.21:22 3)IP转发[root@node1 ~]# iptables -t nat -A PREROUTING -d 10.0.0.50 -p tcp -j DNAT --to-destination 192.168.20.212.nat故障排查1)先看⼀下防⽕墙规则iptables -t nat -nL2)ip⽹关配置查询⽹关ip r或者route -n3)内核转发是否配置在/etc/sysctl.conf⽂件中net.ipv4.ip_forward = 1echo '1' > /proc/sys/net/ipv4/ip_forward4)nat表总结实现共享上⽹(内⽹服务器上外⽹)端⼝转发/映射nat功能在云服务器上⽆法使⽤替代品叫:NAT⽹关三:总结1.禁⽌来⾃10.0.0.188 IP地址访问80端⼝请求iptables -I INPUT -s 10.0.0.188 -p tcp --dport 80 -j DROP2.如何使命令在执⾏的时候永久⽣效?iptables-save/etc/sysconfig/iptables3.实现把访问10.0.0.3:80的请求转到192.168.20.21:80iptables -t nat -A PREROUTING -d 10.0.0.3 -P tcp --dport 80 -j DNAT --to-destination 192.168.20.21:80 4.实现192.168.20.0/24段所有主机通过1xx.3x.5x.2xx外⽹IP共享上⽹iptables -t nat -A POSTROUTING -s 192.168.20.0/24 -j SNAT --to-destination 1xx.3x.5x.2xxiptables -t nat -A PORTROUTING -s 192.168.20.0/24 -j SNAT MASQUERADE。

IPTables 使用手册:iptables 的基本架构图:netfilter iptables(table) chain rulerulefilter OUTPUTPREROUTINGnetfilter iptables nat POSTROUTINGOUTPUTPREROUTINGmangle对链操作:建立一个新的链( -N)删除一个链( -X)改变一个内建(默认)规则链( -P)列出链中的所有规则( -L)清除一个链中的所有规则( -F)对规则的基本操作:-A 在链尾加一条规则-I 插入规则-D 删除规则-R 替代一条已存在的规则-L 列出所有规则对链与规则的目标动作:ACCEPT 接收该数据报DROP 丢弃该数据报REJECT 拒绝该数据报对规则的基本匹配条件:-p 指定协议(tcp / udp/ icmp)-s 源地址(IP Address / mask Len)-d 目的地址(IP Address / mask Len)-i 数据报输入接口-o 数据报输出接口--sport 源端口协议(tcp / upd / icmp)--dport 目的端口协议(tcp / upd / icmp)附:PREROUTING 用于DNA T 只能选择进入接口( -i ) POSTROUTING用于SNA T 只能选择送出接口( -o ) 在使用iptables 前装载NA T 模块modprobe iptable_nat (主要模块)modprobe ip_contrackmodprobe ip_contrack_ftpmodprobe ip_nat_ftp基本语法:iptables -t table -Operation chain -j target例:允许所有IP到本机的SMTP port 的连接iptables -t filter -A INPUT -p tcp --dport smtp -j ACCEPT删除一个规则:iptables -t filter/nat/mangle -D INPUT/OUTPUT/FORWARD/… 1/2/3/…删除所有规则:iptables -t filter/nat/mangle -F删除一个外加的链:iptables -t filter/nat/mangle -X (外加的链)检查当前链状态:iptables -L -t filter/nat/mangle or iptables -L (只对filter有效)改变一个链的规则:iptables -t filter/nat/mangle -P INPUT/OUTPUT/FORWARD/…不允许所有电脑ping my server:iptables -A INPUT -p icmp -j DROP允许内网ssh连server:iptables -A INPUT -s 192.168.0.0/24 -p tcp --dport ssh -j ACCEPT阻塞外网对内网server的ssh连接:iptables -A INPUT -s ! 192.168.0.0/24 -p tcp --dport ssh -j DROP阻塞向外网的的telnet连接iptables -A OUTPUT -p tcp --dport telnet -j DROP禁止192.168.0.4的IP访问所有www:iptables -A FORWARD -s 192.168.0.4 -p tcp --dport www -j REJECT禁止某NIC's Address 不能访问所有的www:iptables -A FORW ARD -p tcp -m mac -- mac-source <mac adderss> -d 0.0.0.0 - --dport www -j DROP在NAT(-nat)表中加入一条规则,在路由之前(-A PREROUTING) 指向1.2.3.4(-d 1.2.3.4)8080 port (-dport 8080)的tcp包(-p tcp)目标地址(-j DNAT)被重定向到192.168.0.4的80port(--to 192.168.0.4:80)iptables -t nat -A PREROUTING -p tcp -d 1.2.3.4 - - dprot 8080 -j DNAT - - to 192.168.0.4:80 SNAT的特例为伪装(MASQUERADE)只用于动态分配IP地址的情况(静态IP地址请用SNAT)伪装所有ppp0送出的东西:iptables -t nat -A POSTROUTING -o ppp0 -j MASQUERADE伪装来源为192.168.0.4的www协议到ppp0送出到202.64.164.247的80端口:iptables -t nat -A POSTROUTING -s 192.168.0.4 -p tcp --sport www -o ppp0 -j MASQUERADE --to 202.64.164.247附内核的编辑:/usr/src/kernel's version/make menuconfig/usr/src/kernel's version/make xconfig/usr/src/kernel's version/make config内核配置完后运行:make bzImagemake modulesmake modules_install。

iptables⽤法及常⽤模块总结iptables传输数据包的过程: 1. 当⼀个数据包进⼊⽹卡时,它⾸先进⼊PREROUTING链,内核根据数据包⽬的IP判断是否需要转送出去。
2. 如果数据包就是进⼊本机的,它就会沿着图向下移动,到达INPUT链。
数据包到了INPUT链后,任何进程都会收到它。
本机上运⾏的程序可以发送数据包,这些数据包会经过OUTPUT链,然后到达POSTROUTING链输出。
3. 如果数据包是要转发出去的,且内核允许转发,数据包就会如图所⽰向右移动,经过FORWARD链,然后到达POSTROUTING链输出。
第⼀部分:常⽤显⽰模块介绍注意:本⽂所有实例都是在默认规则为DROP下。
# 开放ssh服务端⼝iptables -A INPUT -p tcp --dport 22 -j ACCEPTiptables -A INPUT -p tcp --sport 22 -j ACCEPT# 修改默认规则为DROPiptables -P INPUT DROPiptables -P OUTPUT DROP1. multiport: 多端⼝匹配可⽤于匹配⾮连续或连续端⼝;最多指定15个端⼝;实例iptables -A INPUT -p tcp -m multiport --dport 22,80 -j ACCEPTiptables -A OUTPUT -p tcp -m multiport --sport 22,80 -j ACCEPT2. iprange: 匹配指定范围内的地址匹配⼀段连续的地址⽽⾮整个⽹络时有⽤实例:iptables -A INPUT -p tcp -m iprange --src-range 192.168.118.0-192.168.118.60 --dport 22 -j ACCEPTiptables -A OUTPUT -p tcp -m iprange --dst-range 192.168.118.0-192.168.118.60 --sport 22 -j ACCEPT3. string: 字符串匹配,能够检测报⽂应⽤层中的字符串字符匹配检查⾼效算法:kmp, bm能够屏蔽⾮法字符实例:# 注意该条规则需要添加到OUTPUT链,当服务端返回数据报⽂检查到有关键字"sex"时,则丢弃该报⽂,可⽤于web敏感词过滤iptables -A OUTPUT -p tcp --dport 80 -m string --algo kmp --string"sex" -j DROP4. connlimit: 连接数限制,对每IP所能够发起并发连接数做限制;实例:# 默认INPUT 为 DROP. 每个ip对ssh服务的访问最⼤为3个并发连接,超过则丢弃iptables -A INPUT -p tcp --dport 22 -m connlimit ! --connlimit-above 3 -j ACCEPT5. limit: 速率限制limit-burst: 设置默认阀值# 默认放⾏10个,当到达limit-burst阀值后,平均6秒放⾏1个iptables -A INPUT -p icmp -m limit --limit 10/minute --limit-burst 10 -j ACCEPT6. state: 状态检查连接追踪中的状态:NEW: 新建⽴⼀个会话ESTABLISHED:已建⽴的连接RELATED: 有关联关系的连接INVALID: ⽆法识别的连接# 放⾏ssh的⾸次连接状态iptables -A INPUT -p tcp --dport 22 -m state --state NEW -j ACCEPT第⼆部分:编写常⽤规则编写iptables注意:做默认规则drop的时候⼀定要先开放ssh端⼝,否则就杯具了。
iptables也叫netfilter,是Linux下自带的一款免费且优秀的基于包过滤的防火墙工具,他的功能十分强大,使用也非常灵活,可以对流入、流出、流经服务器的数据包进行精细的控制。
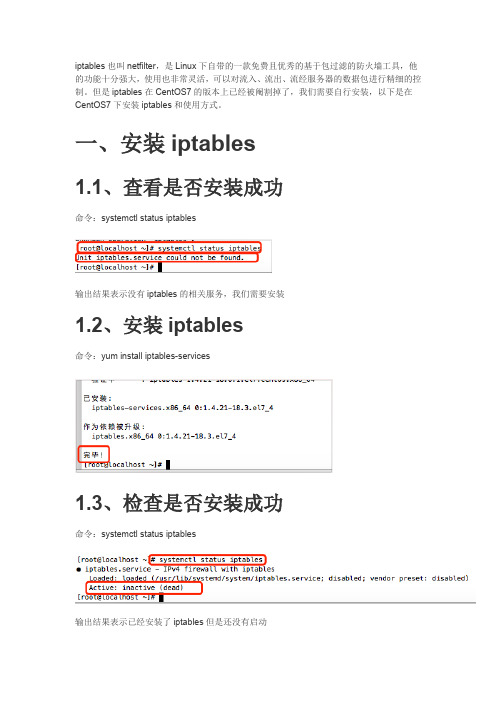
但是iptables在CentOS7的版本上已经被阉割掉了,我们需要自行安装,以下是在CentOS7下安装iptables和使用方式。
一、安装iptables1.1、查看是否安装成功命令:systemctl status iptables输出结果表示没有iptables的相关服务,我们需要安装1.2、安装iptables命令:yum install iptables-services1.3、检查是否安装成功命令:systemctl status iptables输出结果表示已经安装了iptables但是还没有启动1.4、启动iptables命令:systemctl start iptables.service再次查看状态,输出结果表示已经成功启动iptables1.5、关闭SELINUX这里需要关闭SELINUX,因为当SELINUX不关闭时,iptables不读取配置文件,二、命令2.1、系统命令systemctl start iptables #启动systemctl status iptables #查看运行状态systemctl restart iptables.service #重启systemctl stop iptables.service #停止systemctl enable iptables.service #设置开机启动systemctl disable iptables.service #禁止开机启动2.2、常用命令iptables -h #查询帮助iptables -L -n #列出(filter表)所有规则iptables -L -n --line-number #列出(filter表)所有规则,带编号iptables -L -n -t nat #列出(nat表)所有规则iptables -F #清除(filter表)中所有规则iptables -F -t nat #清除(nat表)中所有规则service iptables save #保存配置(保存配置后必须重启iptables)systemctl restart iptables.service #重启三、语法3.1、filter表解析filter表是iptables默认使用的表,负责对流入、流出本机的数据包进行过滤,该表中定义了3个链,分别是:INPUT、OUTPUT、FORWARDINPUT:过滤进入主机的数据包OUTPUT:处理从本机出去的数据包FORWARD:负责转发流经本机但不进入本机的数据包,起到转发作用3.2、iptables常用语法-A:追加到规则的最后一条-D:删除记录-I:添加到规则的第一条-p:(proto)规定通信协议,常见的协议有:tcp、udp、icmp、all-j:(jump)指定要跳转的目标,常见的目标有:ACCEPT(接收数据包)、DROP(丢弃数据包)、REJECT(重定向)三种,但是一般不适用重定向,会带来安全隐患四、常见案例4.1、IP过滤4.1.1、禁止192.168.1.3 IP地址的所有类型数据接入iptables -A INPUT ! -s 192.168.1.3 -j DROP4.2、开放端口4.2.1、开放端口iptables -A INPUT -p tcp --dport 80 -j ACCEPT #开放80端口4.2.2、开放端口范围iptables -I INPUT -p tcp --dport 22:80 -j ACCEPT #开发22-80范围的端口4.2.3、不允许80端口流出iptables -I OUTPUT -p tcp --dport 80 -j DROP。

iptables 用法iptables是Linux系统上的一个强大的防火墙工具。
它可以检查、过滤、转发和修改来自网络的数据包,同时保护Linux主机免受网络攻击。
iptables的工作原理是将来自网络的数据包与预先定义的规则进行匹配,并根据规则对其进行处理。
规则可以定义对来自特定IP地址、端口号或协议的数据包的处理方式。
使用iptables需要一定的专业知识和经验,下面将分步骤介绍iptables的用法和一些常用操作。
要查看当前iptables规则,可以使用以下命令:```bashiptables -L```这将显示当前iptables中所有规则。
默认情况下,iptables不进行任何防火墙过滤,并允许所有数据包通过。
2. 添加规则要添加一个新的规则,需要指定规则的类型、动作和匹配条件。
例如,如果想要阻止所有来自IP地址为192.168.0.2的主机的传入数据包,可以使用以下命令:```bashiptables -A INPUT -s 192.168.0.2 -j DROP```该命令将在“INPUT”链中添加一条规则,该规则匹配所有源IP地址为192.168.0.2的数据包,并将其动作设置为“DROP”,即完全拒绝该数据包。
3. 删除规则要删除特定的iptables规则,需要知道该规则的编号。
可以使用以下命令列出每个规则的编号:一旦知道规则的编号,就可以使用以下命令删除规则:比如,要删除第2条INPUT链规则,可以使用以下命令:4. 允许或拒绝所有数据包要允许或拒绝所有数据包,可以使用以下命令:如果要还原默认策略,可以使用以下命令:5. 修改特定规则6. 保存当前规则为了在每次系统重启后,保留设置的iptables规则,需要将其保存。
可以使用以下命令将iptables规则保存到文件中:```bashiptables-save > /etc/sysconfig/iptables```现在,即使重启系统,iptables的规则也会被保留。
然后保存退出内核配置模式。
# make dep @@@链接程序代码和函数库
首先我们查看一下l7filter支持的封禁列表:
# ls /etc/l7-protocols/protocols/
100bao.pat gkrellm.pat ncp.pat ssdp.pat
aim.pat gnucleuslan.pat netbios.pat ssh.pat aimwebcontent.pat gnutella.pat nntp.pat ssl.pat applejuice.pat goboogy.pat ntp.pat stun.pat
ares.pat gopher.pat openft.pat subspace.pat armagetron.pat guildwars.pat pcanywhere.pat subversion.pat battlefield1942.pat h323.pat poco.pat teamfortress2.pat battlefield2142.pat halflife2-deathmatch.pat pop3.pat teamspeak.pat battlefield2.pat hddtemp.pat pplive.pat telnet.pat
bgp.pat hotline.pat qq.pat tesla.pat
biff.pat http.pat quake1.pat tftp.pat
bittorrent.pat http-rtsp.pat quake-halflife.pat thecircle.pat chikka.pat ident.pat radmin.pat tor.pat
cimd.pat imap.pat rdp.pat tsp.pat
ciscovpn.pat imesh.pat replaytv-ivs.pat unknown.pat
citrix.pat ipp.pat rlogin.pat unset.pat
counterstrike-source.pat irc.pat rtp.pat uucp.pat
cvs.pat jabber.pat rtsp.pat validcertssl.pat dayofdefeat-source.pat kugoo.pat shoutcast.pat ventrilo.pat dhcp.pat live365.pat sip.pat vnc.pat directconnect.pat liveforspeed.pat skypeout.pat whois.pat
dns.pat lpd.pat skypetoskype.pat worldofwarcraft.pat doom3.pat mohaa.pat smb.pat x11.pat
edonkey.pat msn-filetransfer.pat smtp.pat xboxlive.pat fasttrack.pat msnmessenger.pat snmp.pat xunlei.pat finger.pat mute.pat socks.pat yahoo.pat
网友评论
内容:现在出了一个新的MSN客户端米鼠MSN。
我用的感觉还不错,东西很小,MSN有的功能它基本上都有了。
在linux系统上操作也和windows系统上
一样方便。
关键是不用配协议,我比较菜,呵呵
华军啊,天空啊,各个大下载站都有下载的
本站网友评论于:2009-03-18 14:11:25 (218.81.140.★)
内容:现在出了一个新的MSN客户端米鼠MSN。
我用的感觉还不错,东西很小,MSN有的功能它基本上都有了。
在linux系统上操作也和windows系统上
一样方便。
关键是不用配协议,我比较菜,呵呵
华军啊,天空啊,各个大下载站都有下载的
本站网友评论于:2009-03-18 14:12:27 (218.81.140.★)
内容:现在新浪,PChome或官网上有米鼠MSN最新版本供下载
本站网友评论于:2009-03-23 11:29:04 (218.81.140.★)
内容:楼主:
迅雷使用 TCP/80 BitComet 默认使用 TCP/80(这些软件都太狠了)和自己的加密协议电驴也支持了协议迷惑现在Layer7在很多情况下都用不了了。
本站网友评论于:2009-04-07 15:00:01 (124.193.95.★)
内容:是的,软件级别的防火墙还是有一定限制的。
硬件防火墙是第一选择
zmouc评论于:2009-04-07 18:02:24 (125.122.29.★)。