Exploiting Non-Uniform Reuse for Cache Optimization
- 格式:pdf
- 大小:171.57 KB
- 文档页数:5

post-exploitation basics tryhackme -回复Post-Exploitation Basics: A Comprehensive Guide to TryHackMeIntroduction:Post-exploitation is a critical phase of cybersecurity and ethical hacking where an attacker gains access to a target system and then explores, analyzes, and exploits any vulnerabilities to maintain control or extract valuable information. In this article, we will delve into the basics of post-exploitation, focusing specifically on the TryHackMe platform, explaining the steps and techniques involved.What is TryHackMe?TryHackMe is an online platform designed for individuals interested in cybersecurity, specifically the field of ethical hacking. It offers a hands-on experience in a safe and controlled environment, enabling users to practice and refine their skills. TryHackMe consists of various virtual rooms or challenges, each offering a unique scenario or target system where users must exploit vulnerabilities and gain root access.1. The Post-Exploitation Phase:The post-exploitation phase occurs after initial access has been gained. It involves maintaining control, escalating privileges, exfiltrating data, and covering tracks. Let's explore the primary steps involved:a. Maintaining Access:Once you have access to a target system, you want to ensure you maintain control. This can be achieved by creating a backdoor, establishing persistence, or creating a new user account with administrative privileges. TryHackMe offers virtual machines with vulnerabilities that allow you to practice these techniques.b. Privilege Escalation:Privilege escalation involves elevating your privileges on the target system effectively. This can be accomplished through various methods, such as exploiting misconfigurations, unpatched software, or weak file permissions. Enumeration tools like LinEnum and WindowsExploitSuggester can aid in searching forvulnerabilities.c. Information Gathering:Collecting valuable data from the compromised system is often an essential part of post-exploitation. This can include passwords, sensitive files, or credentials stored in browser cookies. Tools like Mimikatz and Hashdump can aid in extracting credentials from memory or SAM databases.d. Lateral Movement:Lateral movement refers to the process of exploring and expanding your control within a network, moving from one compromised system to another. Tools like Bloodhound and Metasploit can help identify potential targets and exploit vulnerabilities to gain access to them.e. Data Exfiltration:Once you have gathered the desired information, you may want to exfiltrate it to your own system. This can be achieved by creatingcustom scripts or using tools like SCP or secure file transfer protocols.f. Covering Tracks:Leaving no traces behind is crucial in post-exploitation. Removing any logs, backdoors, or modifying timestamps can help hide your activities. Tools like LogCleaner and Shellerator can assist in these tasks.2. TryHackMe Platform:TryHackMe provides a hands-on experience for users to practice various post-exploitation techniques. The platform offers virtual machines and challenges, each with a specific goal in mind. Let's explore some common rooms to gain insight into thepost-exploitation basics.a. "Vulnversity" Room:The Vulnversity room in TryHackMe is an excellent starting point for understanding post-exploitation. By exploiting variousvulnerabilities, including remote code execution and command injection, users can gain root access to the system. The room offers practical experience in maintaining control, escalating privileges, and exfiltrating valuable data.b. "Bolt" Room:In the Bolt room, users have to exploit a vulnerable WordPress installation to gain access. This room focuses on exploiting weaknesses in web applications, gaining a foothold, and then pivoting within the network. Users will learn techniques like privilege escalation, WordPress enumeration, and lateral movement.c. "Relevant" Room:The Relevant room in TryHackMe focuses on advancedpost-exploitation techniques. Users will exploit vulnerabilities to gain access to a target system, escalate privileges, exfiltrate sensitive data, and perform lateral movement. This room provides hands-on experience with tools like Bloodhound, Metasploit, and Mimikatz.Conclusion:Understanding post-exploitation basics is crucial for cybersecurity professionals and ethical hackers. TryHackMe offers an immersive platform where users can practice and refine their skills, exploring real-world scenarios and gaining practical experience. Thepost-exploitation phase involves maintaining control, escalating privileges, extracting valuable information, and covering tracks. By mastering these steps and techniques, professionals can effectively assess and secure their systems against potential threats.。

垃圾分类保护环境英语作文倡议书Protect Our Planet by Sorting Waste!Hi friends! My name is Emily and I'm a 4th grader at Oakwood Elementary School. Today I want to talk to you about something really important – taking care of our amazing planet Earth!Have you ever thought about where our trash goes after we throw it away? A lot of it ends up in huge trash dumps called landfills. And those landfills are getting way too full! Plus, all that trash is really bad for the environment. It pollutes the air, land, and water around the landfills.But there's something we can all do to help – sort our waste properly so it can be recycled instead of just thrown away! Recycling is when we take old materials like plastics, glass, paper and metals and turn them into new products. That way, we don't have to keep cutting down trees and digging up the earth for brand new raw materials.My Class Recycling ProjectIn my class, we just finished a really cool project all about recycling. We learned that there are three main categories for sorting our waste:Recyclables - These are items like plastic bottles and containers, glass jars, aluminum cans, paper, and cardboard boxes. Instead of just throwing them in the trash, we need to put them in separate recycling bins so they can be turned into new products.Compostables - Food scraps like banana peels, egg shells, and leftover vegetables can be composted. Composting is like recycling for food and yard waste. The composter bin has special microorganisms that help break down the organic materials into a nutrient-rich soil called compost. We can then use that compost to help plants grow!Landfill - Finally, anything that can't be recycled or composted has to go into the regular trash bin to be sent to the landfill. Things like plastic wrappers, styrofoam, and waste with food stuck on it usually end up here.For our project, we had three different bins in our classroom - green for compostables, blue for recyclables, and black for landfill trash. We spent two weeks carefully sorting all of our waste into the right bins.At first, it was kind of confusing remembering what goes where. But by the end, we were pros! I was really surprised by how much of our waste could actually be recycled or compostedinstead of just thrown away. In just two weeks, our class only filled up one small black landfill bin, while the recycling and compost bins were completely stuffed!Why Bother Sorting Waste?I know what some of you might be thinking - "It's just a lot of extra work to sort the trash. Why does it even matter?" Well, here's why proper waste sorting is so important:It saves natural resources - By recycling items instead of just tossing them, we don't have to constantly chop down new trees for paper, mine for new metals, or drill for fresh plastic. Using recycled materials means we can conserve what's left of Earth's limited natural resources.It reduces pollution - Recycling and composting create way less air, water and land pollution compared to sending tons of trash to the landfills or burning it in incinerators. Those huge trash dumps and smouldering fires release toxic gases that are terrible for the environment.It saves energy - Did you know it takes way more energy to make products from brand new raw materials than from recycled items? Recycling aluminum cans saves 95% of the energy needed to create new ones from scratch!It fights climate change - Manufacturing with recycled materials cuts back on the greenhouse gas emissions that cause dangerous climate change and global warming. In fact, recycling just one aluminum can saves the same amount of greenhouse gas emissions as taking a car off the road for 20 minutes!It creates jobs - The whole recycling industry employs over 1 million people in jobs like manufacturing, collection, and processing. More recycling means more of those good green jobs!How You Can HelpNow that you know how important it is to sort our waste properly, I have a big favor to ask all of you. Will you join me in taking the Waste Sorting Challenge?The challenge is simple - for the next two weeks, I want you to be a Waste Sorting Warrior! Whenever you have any disposable item, whether it's an empty water bottle, a banana peel, a sheet of paper, or whatever, stop and think - can this be recycled or composted instead of just thrown away?At home, make sure you have separate bins for compost, recycling, and trash. Ask your parents to help you identify what can go in each one. At school, use the proper bins too. And ifyour school doesn't have recycling and compost bins yet, start a petition to get them!I know two weeks of carefully sorting everything seems like a long time. But I promise, if we all work together, it will become an easy habit before you know it. And just think about the huge difference we'll make for the planet by keeping tons of waste out of landfills!Once the two weeks are up, let me know how you did. Did you have a hard time remembering at first, or did it quickly become second nature? How much of your waste were you able to divert from the trash can? I'll collect everyone's results and share them to show what an impact we had as a community.A Greener FutureCaring for the environment has to start with small steps by each of us. But when we all work together, those little steps turn into big changes! By sorting our waste properly, we're not just reducing pollution and saving resources today. We're helping ensure a clean, healthy planet for generations to come.In the future, I hope that landfills are a thing of the past. I dream of a world where every recyclable item gets new life as something else, and Food scraps nourish gardens and farmsinstead of rotting in trash heaps. A world where instead of constantly exploiting the earth for new resources, we reuse what we've already extracted over and over in a sustainable, circular way. Doesn't that sound amazing?But it all starts with us developing better waste sorting habits now while we're young. Parents, teachers, community leaders - I'm asking you to please help guide us kids on the right path. Provide the resources and education we need to properly sort our waste. Make it the norm and the expectation in our schools, homes and neighborhoods.And to my fellow kids and students - let's be leaders in this important endeavor! Spread the word about waste sorting to your friends and families. Come up with creative ways to motivate people to recycle and compost more. We can truly make a difference.The planet is our home, and sorting our waste is one of the best ways we can take care of it. It's a simple habit, but it will have such a positive ripple effect on the environment. So what are we waiting for? Let's get sorting!。


starrocks 存算分离disable cache参数StarRocks(星环)的最新版本为 1.19,以下是关于存算分离(Storage-Compute Separation)以及禁用缓存(Disable Cache)的一些建议,注意这些信息可能随着版本的更新而变化,建议查看最新文档或源代码以获取准确的信息。
存算分离(Storage-Compute Separation):
在StarRocks中,存算分离是一种架构设计,其中存储层(存储引擎)和计算层(计算引擎)分离。
存储引擎负责数据存储和管理,而计算引擎负责执行查询操作。
这种分离可以提高系统的灵活性和可扩展性。
禁用缓存(Disable Cache):
如果你想禁用查询缓存,通常可以在执行查询时使用相应的查询选项。
在StarRocks中,可能会有一些参数或选项来控制查询缓存的行为。
请查看相关文档或查询引擎的配置选项。
在某些场景下,你可能想要禁用缓存来确保每次查询都是基于最新的数据执行的。
然而,需要注意禁用缓存可能会降低性能,特别是对于相同的查询请求。
具体的参数名称和用法可能会根据StarRocks的版本而有所不同。
以下是一些可能的示例:
-- 在查询中禁用缓存
SET disable_cache=1;
SELECT * FROM your_table;
-- 或者在整个会话期间禁用缓存
SET GLOBAL disable_cache=1;
请确保查阅最新的StarRocks文档或相关资源,以获取最准确的信息和配置选项。

IMSE_DONT_CATCH_=不良实践- 捕获可疑IllegalMonitorStateExceptionBX_BOXING_IMMEDIATELY_=性能- 基本类型包装之后立刻解包IJU_SETUP_NO_=使用错误- TestCase定义的setUp没有调用super.setUp()TQ_ALWAYS_VALUE_USED_WHERE_NEVER_=使用错误- 某个值使用了注解限制类型,但是这个限制永远不会发生TLW_TWO_LOCK_=多线程错误- 等待两个被持有的锁RV_01_TO_=使用错误- 0至1的随机数被当做整数0NP_PARAMETER_MUST_BE_NONNULL_BUT_MARKED_AS_=高危- 参数必须非null但是标记为可为nullRV_ABSOLUTE_VALUE_OF_RANDOM_=使用错误- 尝试计算32位随机整数的绝对值EC_INCOMPATIBLE_ARRAY_=使用错误- 使用equals()比较不兼容的数组UL_UNRELEASED_LOCK_EXCEPTION_=多线程错误- 方法没有在所有异常路径释放锁SE_NONSTATIC_=不良实践- serialVersionUID不是static的UCF_USELESS_CONTROL_=高危- 无用控制流BC_IMPOSSIBLE_=使用错误- 不可能的转换XSS_REQUEST_PARAMETER_TO_SEND_=安全风险- servlet的反射导致跨站脚本漏洞DM_NEW_FOR_=性能- 仅为了获得一个方法就创建了一个对象OBL_UNSATISFIED_=试验- 方法可能在清理流或资源时失败UW_UNCOND_=多线程错误- 无条件等待DLS_DEAD_LOCAL_STORE_OF_=高危- 把null设置给不会用到的局部变量NM_CLASS_NAMING_=类名应该以大写字母开头RC_REF_COMPARISON_BAD_PRACTICE_=使用错误- 怀疑对两个布尔值的引用进行比较MWN_MISMATCHED_=多线程错误- 不匹配的notify()NM_VERY_=错误- 非常容易迷惑的方法名FI_NULLIFY_=不良实践- 空Finalizer禁用了超类的finalizerMTIA_SUSPECT_STRUTS_INSTANCE_=高危- 继承了struts Action的类使用了实例变量DM_STRING_=性能- 方法调用了效率很低的new String(String)构造方法STCAL_INVOKE_ON_STATIC_DATE_FORMAT_=多线程错误- 调用静态DateFormatNP_NULL_PARAM_DEREF_=使用错误- 非虚拟方法调用向非空参数传入了nullFI_=不良实践- 应该删除空的finalizerCD_CIRCULAR_=试验- 类间存在循环引用EC_UNRELATED_=使用错误- 使用equals()比较不同类型EI_EXPOSE_STATIC_=恶意代码漏洞- 把可变对象保存到静态字段中可能会暴露内部静态状态DMI_INVOKING_TOSTRING_ON_ANONYMOUS_=错误- 对数组执行toStringSIC_INNER_SHOULD_BE_STATIC_=性能- 可以重构成一个静态内部类STI_INTERRUPTED_ON_=错误- 在thread实例上调用了静态Thread.interrupted()方法CN_IDIOM_NO_SUPER_=不良实践- clone方法没有调用super.clone()VA_FORMAT_STRING_BAD_=错误用法- 格式化字符串占位符与传入的参数不匹配EQ_DOESNT_OVERRIDE_=高危- 类没有覆盖父类的equals方法BC_IMPOSSIBLE_DOWNCAST_OF_=错误用法- 集合转换为数组元素时发生的类型转换错误SE_NO_SUITABLE_CONSTRUCTOR_FOR_=不良实践- 类是可扩展的,但是没有提供无参数的构造方法TQ_EXPLICIT_UNKNOWN_SOURCE_VALUE_REACHES_ALWAYS_=错误用法- 数值需要类型标示,但是却标记为未知SIC_INNER_SHOULD_BE_STATIC_NEEDS_=性能- 可以筹够成一个静态内部类EQ_CHECK_FOR_OPERAND_NOT_COMPATIBLE_WITH_=不良实践- equals检测不兼容的参数操作RV_RETURN_VALUE_OF_PUTIFABSENT_=错误用法- 忽略了putIfAbsent的返回值,传递给putIfAbsent的值被重用STCAL_INVOKE_ON_STATIC_CALENDAR_=多线程错误- 调用静态CalendarMS_CANNOT_BE_=恶意代码漏洞- 字段不是final的,不能防止恶意代码的攻击IS_INCONSISTENT_=多线程错误- 不一致的同步SE_NO_=不良实践- 类是可序列化的,但是没有定义serialVersionUIDEI_EXPOSE_=恶意代码漏洞- 可能暴露内部实现,通过与可变对象引用协作NM_METHOD_CONSTRUCTOR_=错误用法- 明显的方法/构造方法混淆ICAST_INTEGER_MULTIPLY_CAST_TO_=高危- 整形乘法的结果转换为long型QF_QUESTIONABLE_FOR_=高危- for循环中存在复杂,微妙或者错误的自增DLS_DEAD_STORE_OF_CLASS_=错误用法- 类中保存了无用字符NM_FUTURE_KEYWORD_USED_AS_MEMBER_=不良实践- 使用了未来java版本中成为关键字的标识BC_VACUOUS_=高危- instanceof会一直返回trueINT_VACUOUS_BIT_=高危- 在整形上进行位操作时有一些位上出现空洞NP_NULL_=错误用法- 一个已知的null值被检测它是否是一个类型的实例SIC_THREADLOCAL_DEADLY_=错误用法- 非静态内部类和ThreadLocal的致命结合EQ_=高危- 罕见的equals方法IJU_NO_=错误用法- TestCase没有任何测试EQ_OVERRIDING_EQUALS_NOT_=错误用法- equals方法覆盖了父类的equals可能功能不符XFB_XML_FACTORY_=高危- 方法直接调用了xml接口的一个具体实现SWL_SLEEP_WITH_LOCK_=多线程错误- 方法在获得锁时调用了Thread.sleep()CN_=不良实践- 类实现了Cloneable ,但是没有定义或使用clone方法WA_AWAIT_NOT_IN_=多线程错误- 未在循环中使用的Condition.await()DM_FP_NUMBER_=性能- 方法调用了低效的浮点书构造方法;应该使用静态的valueOf代替SF_SWITCH_NO_=Switch语句中没有包含defaultNP_NULL_ON_SOME_PATH_FROM_RETURN_=高危- 调用返回返回值可能出现null值NP_CLONE_COULD_RETURN_=不良实践- Clone方法可能返回nullMS_OOI_=恶意代码漏洞- 属性应该从接口中移除并将访问权限设置为包保护DM_BOXED_PRIMITIVE_=性能- 方法使用了装箱的基本类型只为了调用toStringEQ_ABSTRACT_=不良实践- 抽象类定义了协变的equals方法DM_STRING_=性能- 方法调用了String的toString()方法SE_METHOD_MUST_BE_=错误用法- 方法必须是private的为了让序列化正常工作DL_SYNCHRONIZATION_ON_=多线程错误- 在Boolean上使用同步可能导致死锁UWF_UNWRITTEN_=错误用法- 未赋值属性IS2_INCONSISTENT_=多线程错误- 不一致的同步IM_AVERAGE_COMPUTATION_COULD_=高危- 计算平均值可能溢出BIT_SIGNED_CHECK_HIGH_=错误用法- 检查位运算的符号FL_MATH_USING_FLOAT_=错误用法- 方法进行数学运算时使用了浮点数的精度WS_WRITEOBJECT_=多线程错误- 类的writeObject()方法是同步的,但是没有做其他事情RV_RETURN_VALUE_=错误用法- 方法忽略了返回值SQL_NONCONSTANT_STRING_PASSED_TO_=安全风险- 非常量的字符串传递给方法执行SQL语句JCIP_FIELD_ISNT_FINAL_IN_IMMUTABLE_=不良实践- 不可变的类的属性应该是finalAM_CREATES_EMPTY_ZIP_FILE_=不良实践- 创建了一个空的zip文件的入口DM_NEXTINT_VIA_=性能- 使用Random的nextInt方法来获得一个随机整数,而不是nextDouble UI_INHERITANCE_UNSAFE_=不良实践- 如果类被扩展,GetResource的使用可能就是不安全的SIO_SUPERFLUOUS_=错误用法- 不必要的类型检测使用instanceof操作符EQ_OTHER_NO_=错误用法- equals()方法定义,但是没有覆盖equals(Object)USM_USELESS_ABSTRACT_=试验- 抽象方法已经在实现的接口中定义了MTIA_SUSPECT_SERVLET_INSTANCE_=高危- 扩展Servlet的类使用了实例变量DM_USELESS_=多线程错误- 使用默认的空run方法创建了一个线程ML_SYNC_ON_UPDATED_=多线程错误- 方法在一个修改了的属性上进行了同步CO_SELF_NO_=不良实践- 协变的compareTo()定义BC_UNCONFIRMED_=高危- 未检查/未证实的类型转换FI_FINALIZER_NULLS_=不良实践- Finalizer空属性BIT_=错误用法- 不兼容的位掩码(BIT_AND)FE_FLOATING_POINT_=高危- 测试浮点数相等TQ_EXPLICIT_UNKNOWN_SOURCE_VALUE_REACHES_NEVER_=错误用法- 值不要求有类型标示,但是标记为未知NP_NULL_PARAM_=错误用法- 方法调用把null传递给一个非null参数FB_MISSING_EXPECTED_=试验- findbugs丢失了期待或需要的警告DMI_INVOKING_HASHCODE_ON_=错误用法- 在数组上调用了hashCodeQBA_QUESTIONABLE_BOOLEAN_=错误用法- 方法在布尔表达式中分配了boolean文字SA_FIELD_SELF_=错误用法- 属性自己与自己进行了比较UR_UNINIT_READ_CALLED_FROM_SUPER_=错误用法- 父类的构造方法调用未初始化属性的方法ES_COMPARING_PARAMETER_STRING_WITH_EQ.na me=不良实践- 比较字符串参数使用了== 或!=INT_BAD_COMPARISON_WITH_NONNEGATIVE_=错误用法- 错误比较非负值与负数INT_BAD_COMPARISON_WITH_SIGNED_=错误用法- 错误比较带符号的byteIO_APPENDING_TO_OBJECT_OUTPUT_=错误用法- 尝试向一个对象输出流添加信息FI_MISSING_SUPER_=不良实践- Finalizer没有调用父类的finalizerVA_FORMAT_STRING_EXTRA_ARGUMENTS_=错误用法- 传递了多余实际使用的格式化字符串的参数HE_EQUALS_USE_=不良实践- 类定义了equals(),但使用了Object.hashCode()IJU_BAD_SUITE_=错误用法- TestCase声明了一个错误的suite方法DMI_CONSTANT_DB_=安全风险- 硬编码了数据库密码REC_CATCH_=高危- 捕获了没有抛出的异常PS_PUBLIC_=高危- 类在公用接口中暴露了同步和信号EC_UNRELATED_=错误用法- 调用equals()比较不同的接口类型UCF_USELESS_CONTROL_FLOW_NEXT_=错误用法- 执行到下一行的无用流程控制LG_LOST_LOGGER_DUE_TO_WEAK_=试验- OpenJDK中存在潜在的丢失logger的风险,因为弱引用NP_UNWRITTEN_=错误用法- 读取未初始化的属性DMI_UNSUPPORTED_=高危- 调用不支持的方法RCN_REDUNDANT_COMPARISON_OF_NULL_AND_NONNULL_=高危- 重复比较非空值和nullEC_BAD_ARRAY_=错误用法- 调用equals(),与==效果一样EI_EXPOSE_=恶意代码漏洞- 可能通过返回一个可变对象的引用暴露了内部实现NP_DEREFERENCE_OF_READLINE_=高危- 没有判断readLine()的结果是否为空UPM_UNCALLED_PRIVATE_=性能- 从未用到的私有方法NP_NULL_ON_SOME_=错误用法- 可能出现空指针引用NP_EQUALS_SHOULD_HANDLE_NULL_=不良实践- equals()方法没有检测null参数EC_NULL_=错误用法- 使用空参数调用equals()SE_BAD_FIELD_=不良实践- 非序列化值保存在序列化类的实例变量中VO_VOLATILE_REFERENCE_TO_=多线程错误- 数组的volatile引用不会把数组元素也当做volatile来引用NP_SYNC_AND_NULL_CHECK_=多线程错误- 同步和空值检测发生在同一个属性上DM_=不良实践- 方法调用了System.exit(...)RC_REF_=不良实践- 怀疑进行了引用比较SE_NO_SUITABLE_=不良实践- 类是可序列化的,但是父类没有定义无参数构造方法DC_=多线程错误- 可能对属性进行了双重检测DMI_LONG_BITS_TO_DOUBLE_INVOKED_ON_=错误用法- 在int上调用了Double.longBitsToDouble RpC_REPEATED_CONDITIONAL_=错误用法- 重复判断条件WMI_WRONG_MAP_=性能- keySet迭代是低效的,使用entrySet代替DLS_DEAD_LOCAL_=高危- 未用的局部变量INT_BAD_REM_BY_=错误用法- 整数剩余模1RV_RETURN_VALUE_IGNORED_BAD_=不良实践- 方法忽略异常返回值SA_LOCAL_SELF_=高危- 局部变量的自我赋值MS_SHOULD_BE_=恶意代码漏洞- 属性不是final,但是应该设置成finalSIC_INNER_SHOULD_BE_=性能- 应该是一个静态内部类NP_GUARANTEED_=错误用法- null值一定会被调用SE_READ_RESOLVE_MUST_RETURN_=不良实践- readResolve方法必须返回ObjectNP_LOAD_OF_KNOWN_NULL_=高危- 加载了已知的null值BX_BOXING_IMMEDIATELY_UNBOXED_TO_PERFORM_=性能- 基本数据被装箱又被拆箱CN_IMPLEMENTS_CLONE_BUT_NOT_=不良实践- 类定义了clone()但没有实现CloneableCO_ABSTRACT_=不良实践- 抽象类定义了协变的compareTo()方法BAC_BAD_APPLET_=试验- 错误的Applet构造方法依赖未初始化的AppletStubEQ_GETCLASS_AND_CLASS_=不良实践- equals方法因为子类失败DB_DUPLICATE_SWITCH_=高危- 在两个switch语句中使用了相同的代码DB_DUPLICATE_=高危- 在两个分支中使用了相同的代码UOE_USE_OBJECT_=试验- 在final类上调用了equals,但是没有覆盖Object的equals方法FI_=不良实践- Finalizer除了调用父类的finalizer以外什么也没做NP_ALWAYS_=错误用法- 调用了null指针DMI_VACUOUS_SELF_COLLECTION_=错误用法- 集合的调用不能被感知DLS_DEAD_LOCAL_STORE_IN_=错误用法- 返回语句中的无用的赋值IJU_ASSERT_METHOD_INVOKED_FROM_RUN_=错误用法- 在run方法中的JUnit检验不能报告给JUnitDMI_EMPTY_DB_=安全风险- 空的数据库密码DM_BOOLEAN_=性能- 方法调用了低效的Boolean构造方法;使用Boolean.valueOf(...)代替BC_IMPOSSIBLE_=错误用法- 不可能转型BC_EQUALS_METHOD_SHOULD_WORK_FOR_ALL_=不良实践- Equals方法不应该假设任何有关参数类型的事宜RV_EXCEPTION_NOT_=错误用法- 异常创建后就丢弃了,没有抛出VA_PRIMITIVE_ARRAY_PASSED_TO_OBJECT_=错误用法- 基本类型数组传递给一个期待可变对象类型参数的方法LI_LAZY_INIT_UPDATE_=多线程错误- 错误的延迟初始化和更新静态属性SA_FIELD_SELF_=错误用法- 属性自身赋值EQ_ALWAYS_=错误用法- equals方法一直返回falseDMI_RANDOM_USED_ONLY_=不良实践- Random对象创建后只用了一次NM_CLASS_NOT_=不良实践- Class没有继承Exception,虽然名字像一个异常SA_LOCAL_DOUBLE_=高危- 给局部变量双重赋值NP_NULL_PARAM_DEREF_ALL_TARGETS_=错误用法- 方法调用传递null给非空参数(ALL_TARGETS_DANGEROUS)NP_TOSTRING_COULD_RETURN_=不良实践- toString方法可能返回nullBC_BAD_CAST_TO_ABSTRACT_=高危- 转换成抽象集合值得怀疑NM_LCASE_=类定义了hashcode(); 应该是hashCode()吧?RU_INVOKE_=多线程错误- 在线程中调用了run(你的意思是再启动一次么?)DMI_INVOKING_TOSTRING_ON_=错误用法- 调用了数组的toStringNM_METHOD_NAMING_=方法名应该以小写字母开头RCN_REDUNDANT_COMPARISON_TWO_NULL_=高危- 重复比较两个null值SA_LOCAL_SELF_=错误用法- 对一个变量进行无意义的自我计算(比如x & x)MS_MUTABLE_=恶意代码漏洞- 属性是可变的HashtableRV_DONT_JUST_NULL_CHECK_=高危- 方法丢掉了readLine的结果,在检测它是非空之后。

Error MessagesF9001 Error internal function call.F9002 Error internal RTOS function callF9003 WatchdogF9004 Hardware trapF8000 Fatal hardware errorF8010 Autom. commutation: Max. motion range when moving back F8011 Commutation offset could not be determinedF8012 Autom. commutation: Max. motion rangeF8013 Automatic commutation: Current too lowF8014 Automatic commutation: OvercurrentF8015 Automatic commutation: TimeoutF8016 Automatic commutation: Iteration without resultF8017 Automatic commutation: Incorrect commutation adjustment F8018 Device overtemperature shutdownF8022 Enc. 1: Enc. signals incorr. (can be cleared in ph. 2) F8023 Error mechanical link of encoder or motor connectionF8025 Overvoltage in power sectionF8027 Safe torque off while drive enabledF8028 Overcurrent in power sectionF8030 Safe stop 1 while drive enabledF8042 Encoder 2 error: Signal amplitude incorrectF8057 Device overload shutdownF8060 Overcurrent in power sectionF8064 Interruption of motor phaseF8067 Synchronization PWM-Timer wrongF8069 +/-15Volt DC errorF8070 +24Volt DC errorF8076 Error in error angle loopF8078 Speed loop error.F8079 Velocity limit value exceededF8091 Power section defectiveF8100 Error when initializing the parameter handlingF8102 Error when initializing power sectionF8118 Invalid power section/firmware combinationF8120 Invalid control section/firmware combinationF8122 Control section defectiveF8129 Incorrect optional module firmwareF8130 Firmware of option 2 of safety technology defectiveF8133 Error when checking interrupting circuitsF8134 SBS: Fatal errorF8135 SMD: Velocity exceededF8140 Fatal CCD error.F8201 Safety command for basic initialization incorrectF8203 Safety technology configuration parameter invalidF8813 Connection error mains chokeF8830 Power section errorF8838 Overcurrent external braking resistorF7010 Safely-limited increment exceededF7011 Safely-monitored position, exceeded in pos. DirectionF7012 Safely-monitored position, exceeded in neg. DirectionF7013 Safely-limited speed exceededF7020 Safe maximum speed exceededF7021 Safely-limited position exceededF7030 Position window Safe stop 2 exceededF7031 Incorrect direction of motionF7040 Validation error parameterized - effective thresholdF7041 Actual position value validation errorF7042 Validation error of safe operation modeF7043 Error of output stage interlockF7050 Time for stopping process exceeded8.3.15 F7051 Safely-monitored deceleration exceeded (159)8.4 Travel Range Errors (F6xxx) (161)8.4.1 Behavior in the Case of Travel Range Errors (161)8.4.2 F6010 PLC Runtime Error (162)8.4.3 F6024 Maximum braking time exceeded (163)8.4.4 F6028 Position limit value exceeded (overflow) (164)8.4.5 F6029 Positive position limit exceeded (164)8.4.6 F6030 Negative position limit exceeded (165)8.4.7 F6034 Emergency-Stop (166)8.4.8 F6042 Both travel range limit switches activated (167)8.4.9 F6043 Positive travel range limit switch activated (167)8.4.10 F6044 Negative travel range limit switch activated (168)8.4.11 F6140 CCD slave error (emergency halt) (169)8.5 Interface Errors (F4xxx) (169)8.5.1 Behavior in the Case of Interface Errors (169)8.5.2 F4001 Sync telegram failure (170)8.5.3 F4002 RTD telegram failure (171)8.5.4 F4003 Invalid communication phase shutdown (172)8.5.5 F4004 Error during phase progression (172)8.5.6 F4005 Error during phase regression (173)8.5.7 F4006 Phase switching without ready signal (173)8.5.8 F4009 Bus failure (173)8.5.9 F4012 Incorrect I/O length (175)8.5.10 F4016 PLC double real-time channel failure (176)8.5.11 F4017 S-III: Incorrect sequence during phase switch (176)8.5.12 F4034 Emergency-Stop (177)8.5.13 F4140 CCD communication error (178)8.6 Non-Fatal Safety Technology Errors (F3xxx) (178)8.6.1 Behavior in the Case of Non-Fatal Safety Technology Errors (178)8.6.2 F3111 Refer. missing when selecting safety related end pos (179)8.6.3 F3112 Safe reference missing (179)8.6.4 F3115 Brake check time interval exceeded (181)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand ControlsI Bosch Rexroth AG VII/XXIITable of ContentsPage8.6.5 F3116 Nominal load torque of holding system exceeded (182)8.6.6 F3117 Actual position values validation error (182)8.6.7 F3122 SBS: System error (183)8.6.8 F3123 SBS: Brake check missing (184)8.6.9 F3130 Error when checking input signals (185)8.6.10 F3131 Error when checking acknowledgment signal (185)8.6.11 F3132 Error when checking diagnostic output signal (186)8.6.12 F3133 Error when checking interrupting circuits (187)8.6.13 F3134 Dynamization time interval incorrect (188)8.6.14 F3135 Dynamization pulse width incorrect (189)8.6.15 F3140 Safety parameters validation error (192)8.6.16 F3141 Selection validation error (192)8.6.17 F3142 Activation time of enabling control exceeded (193)8.6.18 F3143 Safety command for clearing errors incorrect (194)8.6.19 F3144 Incorrect safety configuration (195)8.6.20 F3145 Error when unlocking the safety door (196)8.6.21 F3146 System error channel 2 (197)8.6.22 F3147 System error channel 1 (198)8.6.23 F3150 Safety command for system start incorrect (199)8.6.24 F3151 Safety command for system halt incorrect (200)8.6.25 F3152 Incorrect backup of safety technology data (201)8.6.26 F3160 Communication error of safe communication (202)8.7 Non-Fatal Errors (F2xxx) (202)8.7.1 Behavior in the Case of Non-Fatal Errors (202)8.7.2 F2002 Encoder assignment not allowed for synchronization (203)8.7.3 F2003 Motion step skipped (203)8.7.4 F2004 Error in MotionProfile (204)8.7.5 F2005 Cam table invalid (205)8.7.6 F2006 MMC was removed (206)8.7.7 F2007 Switching to non-initialized operation mode (206)8.7.8 F2008 RL The motor type has changed (207)8.7.9 F2009 PL Load parameter default values (208)8.7.10 F2010 Error when initializing digital I/O (-> S-0-0423) (209)8.7.11 F2011 PLC - Error no. 1 (210)8.7.12 F2012 PLC - Error no. 2 (210)8.7.13 F2013 PLC - Error no. 3 (211)8.7.14 F2014 PLC - Error no. 4 (211)8.7.15 F2018 Device overtemperature shutdown (211)8.7.16 F2019 Motor overtemperature shutdown (212)8.7.17 F2021 Motor temperature monitor defective (213)8.7.18 F2022 Device temperature monitor defective (214)8.7.19 F2025 Drive not ready for control (214)8.7.20 F2026 Undervoltage in power section (215)8.7.21 F2027 Excessive oscillation in DC bus (216)8.7.22 F2028 Excessive deviation (216)8.7.23 F2031 Encoder 1 error: Signal amplitude incorrect (217)VIII/XXII Bosch Rexroth AG | Electric Drivesand ControlsRexroth IndraDrive | Troubleshooting GuideTable of ContentsPage8.7.24 F2032 Validation error during commutation fine adjustment (217)8.7.25 F2033 External power supply X10 error (218)8.7.26 F2036 Excessive position feedback difference (219)8.7.27 F2037 Excessive position command difference (220)8.7.28 F2039 Maximum acceleration exceeded (220)8.7.29 F2040 Device overtemperature 2 shutdown (221)8.7.30 F2042 Encoder 2: Encoder signals incorrect (222)8.7.31 F2043 Measuring encoder: Encoder signals incorrect (222)8.7.32 F2044 External power supply X15 error (223)8.7.33 F2048 Low battery voltage (224)8.7.34 F2050 Overflow of target position preset memory (225)8.7.35 F2051 No sequential block in target position preset memory (225)8.7.36 F2053 Incr. encoder emulator: Pulse frequency too high (226)8.7.37 F2054 Incr. encoder emulator: Hardware error (226)8.7.38 F2055 External power supply dig. I/O error (227)8.7.39 F2057 Target position out of travel range (227)8.7.40 F2058 Internal overflow by positioning input (228)8.7.41 F2059 Incorrect command value direction when positioning (229)8.7.42 F2063 Internal overflow master axis generator (230)8.7.43 F2064 Incorrect cmd value direction master axis generator (230)8.7.44 F2067 Synchronization to master communication incorrect (231)8.7.45 F2068 Brake error (231)8.7.46 F2069 Error when releasing the motor holding brake (232)8.7.47 F2074 Actual pos. value 1 outside absolute encoder window (232)8.7.48 F2075 Actual pos. value 2 outside absolute encoder window (233)8.7.49 F2076 Actual pos. value 3 outside absolute encoder window (234)8.7.50 F2077 Current measurement trim wrong (235)8.7.51 F2086 Error supply module (236)8.7.52 F2087 Module group communication error (236)8.7.53 F2100 Incorrect access to command value memory (237)8.7.54 F2101 It was impossible to address MMC (237)8.7.55 F2102 It was impossible to address I2C memory (238)8.7.56 F2103 It was impossible to address EnDat memory (238)8.7.57 F2104 Commutation offset invalid (239)8.7.58 F2105 It was impossible to address Hiperface memory (239)8.7.59 F2110 Error in non-cyclical data communic. of power section (240)8.7.60 F2120 MMC: Defective or missing, replace (240)8.7.61 F2121 MMC: Incorrect data or file, create correctly (241)8.7.62 F2122 MMC: Incorrect IBF file, correct it (241)8.7.63 F2123 Retain data backup impossible (242)8.7.64 F2124 MMC: Saving too slowly, replace (243)8.7.65 F2130 Error comfort control panel (243)8.7.66 F2140 CCD slave error (243)8.7.67 F2150 MLD motion function block error (244)8.7.68 F2174 Loss of motor encoder reference (244)8.7.69 F2175 Loss of optional encoder reference (245)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand Controls| Bosch Rexroth AG IX/XXIITable of ContentsPage8.7.70 F2176 Loss of measuring encoder reference (246)8.7.71 F2177 Modulo limitation error of motor encoder (246)8.7.72 F2178 Modulo limitation error of optional encoder (247)8.7.73 F2179 Modulo limitation error of measuring encoder (247)8.7.74 F2190 Incorrect Ethernet configuration (248)8.7.75 F2260 Command current limit shutoff (249)8.7.76 F2270 Analog input 1 or 2, wire break (249)8.7.77 F2802 PLL is not synchronized (250)8.7.78 F2814 Undervoltage in mains (250)8.7.79 F2815 Overvoltage in mains (251)8.7.80 F2816 Softstart fault power supply unit (251)8.7.81 F2817 Overvoltage in power section (251)8.7.82 F2818 Phase failure (252)8.7.83 F2819 Mains failure (253)8.7.84 F2820 Braking resistor overload (253)8.7.85 F2821 Error in control of braking resistor (254)8.7.86 F2825 Switch-on threshold braking resistor too low (255)8.7.87 F2833 Ground fault in motor line (255)8.7.88 F2834 Contactor control error (256)8.7.89 F2835 Mains contactor wiring error (256)8.7.90 F2836 DC bus balancing monitor error (257)8.7.91 F2837 Contactor monitoring error (257)8.7.92 F2840 Error supply shutdown (257)8.7.93 F2860 Overcurrent in mains-side power section (258)8.7.94 F2890 Invalid device code (259)8.7.95 F2891 Incorrect interrupt timing (259)8.7.96 F2892 Hardware variant not supported (259)8.8 SERCOS Error Codes / Error Messages of Serial Communication (259)9 Warnings (Exxxx) (263)9.1 Fatal Warnings (E8xxx) (263)9.1.1 Behavior in the Case of Fatal Warnings (263)9.1.2 E8025 Overvoltage in power section (263)9.1.3 E8026 Undervoltage in power section (264)9.1.4 E8027 Safe torque off while drive enabled (265)9.1.5 E8028 Overcurrent in power section (265)9.1.6 E8029 Positive position limit exceeded (266)9.1.7 E8030 Negative position limit exceeded (267)9.1.8 E8034 Emergency-Stop (268)9.1.9 E8040 Torque/force actual value limit active (268)9.1.10 E8041 Current limit active (269)9.1.11 E8042 Both travel range limit switches activated (269)9.1.12 E8043 Positive travel range limit switch activated (270)9.1.13 E8044 Negative travel range limit switch activated (271)9.1.14 E8055 Motor overload, current limit active (271)9.1.15 E8057 Device overload, current limit active (272)X/XXII Bosch Rexroth AG | Electric Drivesand ControlsRexroth IndraDrive | Troubleshooting GuideTable of ContentsPage9.1.16 E8058 Drive system not ready for operation (273)9.1.17 E8260 Torque/force command value limit active (273)9.1.18 E8802 PLL is not synchronized (274)9.1.19 E8814 Undervoltage in mains (275)9.1.20 E8815 Overvoltage in mains (275)9.1.21 E8818 Phase failure (276)9.1.22 E8819 Mains failure (276)9.2 Warnings of Category E4xxx (277)9.2.1 E4001 Double MST failure shutdown (277)9.2.2 E4002 Double MDT failure shutdown (278)9.2.3 E4005 No command value input via master communication (279)9.2.4 E4007 SERCOS III: Consumer connection failed (280)9.2.5 E4008 Invalid addressing command value data container A (280)9.2.6 E4009 Invalid addressing actual value data container A (281)9.2.7 E4010 Slave not scanned or address 0 (281)9.2.8 E4012 Maximum number of CCD slaves exceeded (282)9.2.9 E4013 Incorrect CCD addressing (282)9.2.10 E4014 Incorrect phase switch of CCD slaves (283)9.3 Possible Warnings When Operating Safety Technology (E3xxx) (283)9.3.1 Behavior in Case a Safety Technology Warning Occurs (283)9.3.2 E3100 Error when checking input signals (284)9.3.3 E3101 Error when checking acknowledgment signal (284)9.3.4 E3102 Actual position values validation error (285)9.3.5 E3103 Dynamization failed (285)9.3.6 E3104 Safety parameters validation error (286)9.3.7 E3105 Validation error of safe operation mode (286)9.3.8 E3106 System error safety technology (287)9.3.9 E3107 Safe reference missing (287)9.3.10 E3108 Safely-monitored deceleration exceeded (288)9.3.11 E3110 Time interval of forced dynamization exceeded (289)9.3.12 E3115 Prewarning, end of brake check time interval (289)9.3.13 E3116 Nominal load torque of holding system reached (290)9.4 Non-Fatal Warnings (E2xxx) (290)9.4.1 Behavior in Case a Non-Fatal Warning Occurs (290)9.4.2 E2010 Position control with encoder 2 not possible (291)9.4.3 E2011 PLC - Warning no. 1 (291)9.4.4 E2012 PLC - Warning no. 2 (291)9.4.5 E2013 PLC - Warning no. 3 (292)9.4.6 E2014 PLC - Warning no. 4 (292)9.4.7 E2021 Motor temperature outside of measuring range (292)9.4.8 E2026 Undervoltage in power section (293)9.4.9 E2040 Device overtemperature 2 prewarning (294)9.4.10 E2047 Interpolation velocity = 0 (294)9.4.11 E2048 Interpolation acceleration = 0 (295)9.4.12 E2049 Positioning velocity >= limit value (296)9.4.13 E2050 Device overtemp. Prewarning (297)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand Controls| Bosch Rexroth AG XI/XXIITable of ContentsPage9.4.14 E2051 Motor overtemp. prewarning (298)9.4.15 E2053 Target position out of travel range (298)9.4.16 E2054 Not homed (300)9.4.17 E2055 Feedrate override S-0-0108 = 0 (300)9.4.18 E2056 Torque limit = 0 (301)9.4.19 E2058 Selected positioning block has not been programmed (302)9.4.20 E2059 Velocity command value limit active (302)9.4.21 E2061 Device overload prewarning (303)9.4.22 E2063 Velocity command value > limit value (304)9.4.23 E2064 Target position out of num. range (304)9.4.24 E2069 Holding brake torque too low (305)9.4.25 E2070 Acceleration limit active (306)9.4.26 E2074 Encoder 1: Encoder signals disturbed (306)9.4.27 E2075 Encoder 2: Encoder signals disturbed (307)9.4.28 E2076 Measuring encoder: Encoder signals disturbed (308)9.4.29 E2077 Absolute encoder monitoring, motor encoder (encoder alarm) (308)9.4.30 E2078 Absolute encoder monitoring, opt. encoder (encoder alarm) (309)9.4.31 E2079 Absolute enc. monitoring, measuring encoder (encoder alarm) (309)9.4.32 E2086 Prewarning supply module overload (310)9.4.33 E2092 Internal synchronization defective (310)9.4.34 E2100 Positioning velocity of master axis generator too high (311)9.4.35 E2101 Acceleration of master axis generator is zero (312)9.4.36 E2140 CCD error at node (312)9.4.37 E2270 Analog input 1 or 2, wire break (312)9.4.38 E2802 HW control of braking resistor (313)9.4.39 E2810 Drive system not ready for operation (314)9.4.40 E2814 Undervoltage in mains (314)9.4.41 E2816 Undervoltage in power section (314)9.4.42 E2818 Phase failure (315)9.4.43 E2819 Mains failure (315)9.4.44 E2820 Braking resistor overload prewarning (316)9.4.45 E2829 Not ready for power on (316)。
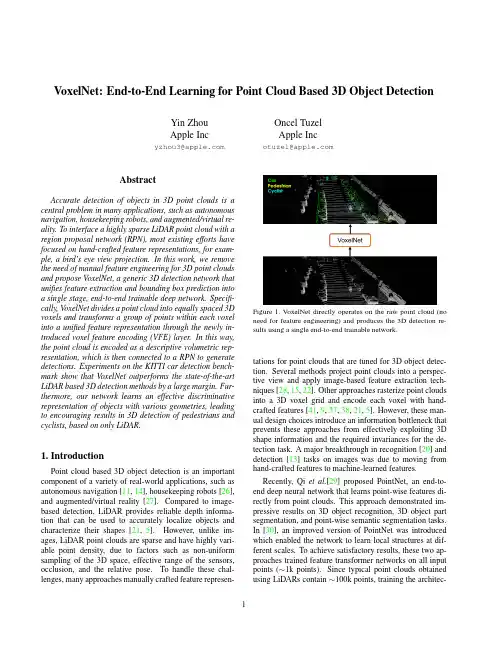
VoxelNet:End-to-End Learning for Point Cloud Based3D Object DetectionYin ZhouApple Inc****************Oncel TuzelApple Inc****************AbstractAccurate detection of objects in3D point clouds is a central problem in many applications,such as autonomous navigation,housekeeping robots,and augmented/virtual re-ality.To interface a highly sparse LiDAR point cloud with a region proposal network(RPN),most existing efforts have focused on hand-crafted feature representations,for exam-ple,a bird’s eye view projection.In this work,we remove the need of manual feature engineering for3D point clouds and propose VoxelNet,a generic3D detection network that unifies feature extraction and bounding box prediction into a single stage,end-to-end trainable deep network.Specifi-cally,VoxelNet divides a point cloud into equally spaced3D voxels and transforms a group of points within each voxel into a unified feature representation through the newly in-troduced voxel feature encoding(VFE)layer.In this way, the point cloud is encoded as a descriptive volumetric rep-resentation,which is then connected to a RPN to generate detections.Experiments on the KITTI car detection bench-mark show that VoxelNet outperforms the state-of-the-art LiDAR based3D detection methods by a large margin.Fur-thermore,our network learns an effective discriminative representation of objects with various geometries,leading to encouraging results in3D detection of pedestrians and cyclists,based on only LiDAR.1.IntroductionPoint cloud based3D object detection is an important component of a variety of real-world applications,such as autonomous navigation[11,14],housekeeping robots[26], and augmented/virtual reality[27].Compared to image-based detection,LiDAR provides reliable depth informa-tion that can be used to accurately localize objects and characterize their shapes[21,5].However,unlike im-ages,LiDAR point clouds are sparse and have highly vari-able point density,due to factors such as non-uniform sampling of the3D space,effective range of the sensors, occlusion,and the relative pose.To handle these chal-lenges,many approaches manually crafted featurerepresen-Figure1.V oxelNet directly operates on the raw point cloud(no need for feature engineering)and produces the3D detection re-sults using a single end-to-end trainable network.tations for point clouds that are tuned for3D object detec-tion.Several methods project point clouds into a perspec-tive view and apply image-based feature extraction tech-niques[28,15,22].Other approaches rasterize point clouds into a3D voxel grid and encode each voxel with hand-crafted features[41,9,37,38,21,5].However,these man-ual design choices introduce an information bottleneck that prevents these approaches from effectively exploiting3D shape information and the required invariances for the de-tection task.A major breakthrough in recognition[20]and detection[13]tasks on images was due to moving from hand-crafted features to machine-learned features.Recently,Qi et al.[29]proposed PointNet,an end-to-end deep neural network that learns point-wise features di-rectly from point clouds.This approach demonstrated im-pressive results on3D object recognition,3D object part segmentation,and point-wise semantic segmentation tasks.In[30],an improved version of PointNet was introduced which enabled the network to learn local structures at dif-ferent scales.To achieve satisfactory results,these two ap-proaches trained feature transformer networks on all input points(∼1k points).Since typical point clouds obtained using LiDARs contain∼100k points,training the architec-1Figure2.V oxelNet architecture.The feature learning network takes a raw point cloud as input,partitions the space into voxels,and transforms points within each voxel to a vector representation characterizing the shape information.The space is represented as a sparse 4D tensor.The convolutional middle layers processes the4D tensor to aggregate spatial context.Finally,a RPN generates the3D detection.tures as in[29,30]results in high computational and mem-ory requirements.Scaling up3D feature learning networks to orders of magnitude more points and to3D detection tasks are the main challenges that we address in this paper.Region proposal network(RPN)[32]is a highly opti-mized algorithm for efficient object detection[17,5,31, 24].However,this approach requires data to be dense and organized in a tensor structure(e.g.image,video)which is not the case for typical LiDAR point clouds.In this pa-per,we close the gap between point set feature learning and RPN for3D detection task.We present V oxelNet,a generic3D detection framework that simultaneously learns a discriminative feature represen-tation from point clouds and predicts accurate3D bounding boxes,in an end-to-end fashion,as shown in Figure2.We design a novel voxel feature encoding(VFE)layer,which enables inter-point interaction within a voxel,by combin-ing point-wise features with a locally aggregated feature. Stacking multiple VFE layers allows learning complex fea-tures for characterizing local3D shape information.Specif-ically,V oxelNet divides the point cloud into equally spaced 3D voxels,encodes each voxel via stacked VFE layers,and then3D convolution further aggregates local voxel features, transforming the point cloud into a high-dimensional volu-metric representation.Finally,a RPN consumes the vol-umetric representation and yields the detection result.This efficient algorithm benefits both from the sparse point struc-ture and efficient parallel processing on the voxel grid.We evaluate V oxelNet on the bird’s eye view detection and the full3D detection tasks,provided by the KITTI benchmark[11].Experimental results show that V oxelNet outperforms the state-of-the-art LiDAR based3D detection methods by a large margin.We also demonstrate that V oxel-Net achieves highly encouraging results in detecting pedes-trians and cyclists from LiDAR point cloud.1.1.Related WorkRapid development of3D sensor technology has moti-vated researchers to develop efficient representations to de-tect and localize objects in point clouds.Some of the earlier methods for feature representation are[39,8,7,19,40,33, 6,25,1,34,2].These hand-crafted features yield satisfac-tory results when rich and detailed3D shape information is available.However their inability to adapt to more complex shapes and scenes,and learn required invariances from data resulted in limited success for uncontrolled scenarios such as autonomous navigation.Given that images provide detailed texture information, many algorithms infered the3D bounding boxes from2D images[4,3,42,43,44,36].However,the accuracy of image-based3D detection approaches are bounded by the accuracy of the depth estimation.Several LIDAR based3D object detection techniques utilize a voxel grid representation.[41,9]encode each nonempty voxel with6statistical quantities that are de-rived from all the points contained within the voxel.[37] fuses multiple local statistics to represent each voxel.[38] computes the truncated signed distance on the voxel grid.[21]uses binary encoding for the3D voxel grid.[5]in-troduces a multi-view representation for a LiDAR point cloud by computing a multi-channel feature map in the bird’s eye view and the cylindral coordinates in the frontal view.Several other studies project point clouds onto a per-spective view and then use image-based feature encoding公众号DASOU-整理schemes[28,15,22].There are also several multi-modal fusion methods that combine images and LiDAR to improve detection accu-racy[10,16,5].These methods provide improved perfor-mance compared to LiDAR-only3D detection,particularly for small objects(pedestrians,cyclists)or when the objectsare far,since cameras provide an order of magnitude more measurements than LiDAR.However the need for an addi-tional camera that is time synchronized and calibrated with the LiDAR restricts their use and makes the solution more sensitive to sensor failure modes.In this work we focus on LiDAR-only detection.1.2.Contributions•We propose a novel end-to-end trainable deep archi-tecture for point-cloud-based3D detection,V oxelNet, that directly operates on sparse3D points and avoids information bottlenecks introduced by manual feature engineering.•We present an efficient method to implement V oxelNet which benefits both from the sparse point structure and efficient parallel processing on the voxel grid.•We conduct experiments on KITTI benchmark and show that V oxelNet produces state-of-the-art results in LiDAR-based car,pedestrian,and cyclist detection benchmarks.2.VoxelNetIn this section we explain the architecture of V oxelNet, the loss function used for training,and an efficient algo-rithm to implement the network.2.1.VoxelNet ArchitectureThe proposed V oxelNet consists of three functional blocks:(1)Feature learning network,(2)Convolutional middle layers,and(3)Region proposal network[32],as il-lustrated in Figure2.We provide a detailed introduction of V oxelNet in the following sections.2.1.1Feature Learning NetworkVoxel Partition Given a point cloud,we subdivide the3D space into equally spaced voxels as shown in Figure2.Sup-pose the point cloud encompasses3D space with range D, H,W along the Z,Y,X axes respectively.We define each voxel of size v D,v H,and v W accordingly.The resulting 3D voxel grid is of size D =D/v D,H =H/v H,W = W/v W.Here,for simplicity,we assume D,H,W are a multiple of v D,v H,v W.Grouping We group the points according to the voxel they reside in.Due to factors such as distance,occlusion,ob-ject’s relative pose,and non-uniform sampling,the LiDARFullyConnectedNeuralNetPoint-wiseInputPoint-wiseFeatureElement-wiseMaxpoolPoint-wiseConcatenateLocallyAggregatedFeaturePoint-wiseconcatenatedFeatureFigure3.V oxel feature encoding layer.point cloud is sparse and has highly variable point density throughout the space.Therefore,after grouping,a voxel will contain a variable number of points.An illustration is shown in Figure2,where V oxel-1has significantly more points than V oxel-2and V oxel-4,while V oxel-3contains no point.Random Sampling Typically a high-definition LiDAR point cloud is composed of∼100k points.Directly pro-cessing all the points not only imposes increased mem-ory/efficiency burdens on the computing platform,but also highly variable point density throughout the space might bias the detection.To this end,we randomly sample afixed number,T,of points from those voxels containing more than T points.This sampling strategy has two purposes,(1)computational savings(see Section2.3for details);and(2)decreases the imbalance of points between the voxels which reduces the sampling bias,and adds more variation to training.Stacked Voxel Feature Encoding The key innovation is the chain of VFE layers.For simplicity,Figure2illustrates the hierarchical feature encoding process for one voxel. Without loss of generality,we use VFE Layer-1to describe the details in the following paragraph.Figure3shows the architecture for VFE Layer-1.Denote V={p i=[x i,y i,z i,r i]T∈R4}i=1...t as a non-empty voxel containing t≤T LiDAR points,where p i contains XYZ coordinates for the i-th point and r i is the received reflectance.Wefirst compute the local mean as the centroid of all the points in V,denoted as(v x,v y,v z). Then we augment each point p i with the relative offset w.r.t. the centroid and obtain the input feature set V in={ˆp i= [x i,y i,z i,r i,x i−v x,y i−v y,z i−v z]T∈R7}i=1...t.Next, eachˆp i is transformed through the fully connected network (FCN)into a feature space,where we can aggregate in-formation from the point features f i∈R m to encode the shape of the surface contained within the voxel.The FCN is composed of a linear layer,a batch normalization(BN) layer,and a rectified linear unit(ReLU)layer.After obtain-ing point-wise feature representations,we use element-wise MaxPooling across all f i associated to V to get the locally aggregated feature˜f∈R m for V.Finally,we augmenteach f i with˜f to form the point-wise concatenated featureas f outi =[f T i,˜f T]T∈R2m.Thus we obtain the outputfeature set V out={f outi }i...t.All non-empty voxels areencoded in the same way and they share the same set of parameters in FCN.We use VFE-i(c in,c out)to represent the i-th VFE layer that transforms input features of dimension c in into output features of dimension c out.The linear layer learns a ma-trix of size c in×(c out/2),and the point-wise concatenation yields the output of dimension c out.Because the output feature combines both point-wise features and locally aggregated feature,stacking VFE lay-ers encodes point interactions within a voxel and enables thefinal feature representation to learn descriptive shape information.The voxel-wise feature is obtained by trans-forming the output of VFE-n into R C via FCN and apply-ing element-wise Maxpool where C is the dimension of the voxel-wise feature,as shown in Figure2.Sparse Tensor Representation By processing only the non-empty voxels,we obtain a list of voxel features,each uniquely associated to the spatial coordinates of a particu-lar non-empty voxel.The obtained list of voxel-wise fea-tures can be represented as a sparse4D tensor,of size C×D ×H ×W as shown in Figure2.Although the point cloud contains∼100k points,more than90%of vox-els typically are empty.Representing non-empty voxel fea-tures as a sparse tensor greatly reduces the memory usage and computation cost during backpropagation,and it is a critical step in our efficient implementation.2.1.2Convolutional Middle LayersWe use Conv M D(c in,c out,k,s,p)to represent an M-dimensional convolution operator where c in and c out are the number of input and output channels,k,s,and p are the M-dimensional vectors corresponding to kernel size,stride size and padding size respectively.When the size across the M-dimensions are the same,we use a scalar to represent the size e.g.k for k=(k,k,k).Each convolutional middle layer applies3D convolution,BN layer,and ReLU layer sequentially.The convolutional middle layers aggregate voxel-wise features within a pro-gressively expanding receptivefield,adding more context to the shape description.The detailed sizes of thefilters in the convolutional middle layers are explained in Section3.2.1.3Region Proposal NetworkRecently,region proposal networks[32]have become an important building block of top-performing object detec-tion frameworks[38,5,23].In this work,we make several key modifications to the RPN architecture proposed in[32], and combine it with the feature learning network and con-volutional middle layers to form an end-to-end trainable pipeline.The input to our RPN is the feature map provided by the convolutional middle layers.The architecture of this network is illustrated in Figure4.The network has three blocks of fully convolutional layers.Thefirst layer of each block downsamples the feature map by half via a convolu-tion with a stride size of2,followed by a sequence of con-volutions of stride1(×q means q applications of thefilter). After each convolution layer,BN and ReLU operations are applied.We then upsample the output of every block to a fixed size and concatanate to construct the high resolution feature map.Finally,this feature map is mapped to the de-sired learning targets:(1)a probability score map and(2)a regression map.2.2.Loss FunctionLet{a pos i}i=1...N pos be the set of N pos positive an-chors and{a neg j}j=1...N neg be the set of N neg negative anchors.We parameterize a3D ground truth box as (x g c,y g c,z g c,l g,w g,h g,θg),where x g c,y g c,z g c represent the center location,l g,w g,h g are length,width,height of the box,andθg is the yaw rotation around Z-axis.To re-trieve the ground truth box from a matching positive anchor parameterized as(x a c,y a c,z a c,l a,w a,h a,θa),we define the residual vector u∗∈R7containing the7regression tar-gets corresponding to center location∆x,∆y,∆z,three di-Voxel Input Feature BufferVoxel CoordinateBufferK T7Sparse TensorK31Voxel-wise FeatureK C 1Point CloudIndexingMemory CopyS t a c k e d V F EFigure 5.Illustration of efficient implementation.mensions ∆l,∆w,∆h ,and the rotation ∆θ,which are com-puted as:∆x =x g c −x a cd a ,∆y =y g c −y a c d a ,∆z =z gc −z a c h a ,∆l =log(l g l a ),∆w =log(w g w a ),∆h =log(h gh a ),(1)∆θ=θg −θawhere d a =(l a )2+(w a )2is the diagonal of the base of the anchor box.Here,we aim to directly estimate the oriented 3D box and normalize ∆x and ∆y homogeneously with the diagonal d a ,which is different from [32,38,22,21,4,3,5].We define the loss function as follows:L =α1N pos i L cls (p posi ,1)+β1N neg jL cls (p neg j ,0)+1N posiL reg (u i ,u ∗i )(2)where p pos i and p neg j represent the softmax output for posi-tive anchor a posi and negative anchor a neg j respectively,whileu i ∈R 7and u ∗i ∈R 7are the regression output and ground truth for positive anchor a pos i .The first two terms are the normalized classification loss for {a pos i }i =1...N pos and {a negj }j =1...N neg ,where the L cls stands for binary cross en-tropy loss and α,βare postive constants balancing the rel-ative importance.The last term L reg is the regression loss,where we use the SmoothL1function [12,32].2.3.Efficient ImplementationGPUs are optimized for processing dense tensor struc-tures.The problem with working directly with the point cloud is that the points are sparsely distributed across space and each voxel has a variable number of points.We devised a method that converts the point cloud into a dense tensor structure where stacked VFE operations can be processed in parallel across points and voxels.The method is summarized in Figure 5.We initialize aK ×T ×7dimensional tensor structure to store the voxel input feature buffer where K is the maximum number of non-empty voxels,T is the maximum number of points per voxel,and 7is the input encoding dimension for each point.The points are randomized before processing.For each point in the point cloud,we check if the corresponding voxel already exists.This lookup operation is done effi-ciently in O (1)using a hash table where the voxel coordi-nate is used as the hash key.If the voxel is already initial-ized we insert the point to the voxel location if there are less than T points,otherwise the point is ignored.If the voxel is not initialized,we initialize a new voxel,store its coordi-nate in the voxel coordinate buffer,and insert the point to this voxel location.The voxel input feature and coordinate buffers can be constructed via a single pass over the point list,therefore its complexity is O (n ).To further improve the memory/compute efficiency it is possible to only store a limited number of voxels (K )and ignore points coming from voxels with few points.After the voxel input buffer is constructed,the stacked VFE only involves point level and voxel level dense oper-ations which can be computed on a GPU in parallel.Note that,after concatenation operations in VFE,we reset the features corresponding to empty points to zero such that they do not affect the computed voxel features.Finally,using the stored coordinate buffer we reorganize the com-puted sparse voxel-wise structures to the dense voxel grid.The following convolutional middle layers and RPN oper-ations work on a dense voxel grid which can be efficiently implemented on a GPU.3.Training DetailsIn this section,we explain the implementation details of the V oxelNet and the training procedure.work DetailsOur experimental setup is based on the LiDAR specifi-cations of the KITTI dataset [11].Car Detection For this task,we consider point clouds within the range of [−3,1]×[−40,40]×[0,70.4]meters along Z,Y ,X axis respectively.Points that are projected outside of image boundaries are removed [5].We choose a voxel size of v D =0.4,v H =0.2,v W =0.2meters,which leads to D =10,H =400,W =352.We set T =35as the maximum number of randomly sam-pled points in each non-empty voxel.We use two VFE layers VFE-1(7,32)and VFE-2(32,128).The final FCN maps VFE-2output to R 128.Thus our feature learning net generates a sparse tensor of shape 128×10×400×352.To aggregate voxel-wise features,we employ three convo-lution middle layers sequentially as Conv3D(128,64,3,(2,1,1),(1,1,1)),Conv3D(64,64,3,(1,1,1),(0,1,1)),andConv3D(64,64,3,(2,1,1),(1,1,1)),which yields a4D ten-sor of size64×2×400×352.After reshaping,the input to RPN is a feature map of size128×400×352,where the dimensions correspond to channel,height,and width of the3D tensor.Figure4illustrates the detailed network ar-chitecture for this task.Unlike[5],we use only one anchor size,l a=3.9,w a=1.6,h a=1.56meters,centered at z a c=−1.0meters with two rotations,0and90degrees. Our anchor matching criteria is as follows:An anchor is considered as positive if it has the highest Intersection over Union(IoU)with a ground truth or its IoU with ground truth is above0.6(in bird’s eye view).An anchor is considered as negative if the IoU between it and all ground truth boxes is less than0.45.We treat anchors as don’t care if they have 0.45≤IoU≤0.6with any ground truth.We setα=1.5 andβ=1in Eqn.2.Pedestrian and Cyclist Detection The input range1is [−3,1]×[−20,20]×[0,48]meters along Z,Y,X axis re-spectively.We use the same voxel size as for car detection, which yields D=10,H=200,W=240.We set T=45 in order to obtain more LiDAR points for better capturing shape information.The feature learning network and con-volutional middle layers are identical to the networks used in the car detection task.For the RPN,we make one mod-ification to block1in Figure4by changing the stride size in thefirst2D convolution from2to1.This allowsfiner resolution in anchor matching,which is necessary for de-tecting pedestrians and cyclists.We use anchor size l a= 0.8,w a=0.6,h a=1.73meters centered at z a c=−0.6 meters with0and90degrees rotation for pedestrian detec-tion and use anchor size l a=1.76,w a=0.6,h a=1.73 meters centered at z a c=−0.6with0and90degrees rota-tion for cyclist detection.The specific anchor matching cri-teria is as follows:We assign an anchor as postive if it has the highest IoU with a ground truth,or its IoU with ground truth is above0.5.An anchor is considered as negative if its IoU with every ground truth is less than0.35.For anchors having0.35≤IoU≤0.5with any ground truth,we treat them as don’t care.During training,we use stochastic gradient descent (SGD)with learning rate0.01for thefirst150epochs and decrease the learning rate to0.001for the last10epochs. We use a batchsize of16point clouds.3.2.Data AugmentationWith less than4000training point clouds,training our network from scratch will inevitably suffer from overfitting. To reduce this issue,we introduce three different forms of data augmentation.The augmented training data are gener-ated on-the-fly without the need to be stored on disk[20].1Our empirical observation suggests that beyond this range,LiDAR returns from pedestrians and cyclists become very sparse and therefore detection results will be unreliable.Define set M={p i=[x i,y i,z i,r i]T∈R4}i=1,...,N as the whole point cloud,consisting of N points.We parame-terize a3D bouding box b i as(x c,y c,z c,l,w,h,θ),where x c,y c,z c are center locations,l,w,h are length,width, height,andθis the yaw rotation around Z-axis.We de-fineΩi={p|x∈[x c−l/2,x c+l/2],y∈[y c−w/2,y c+ w/2],z∈[z c−h/2,z c+h/2],p∈M}as the set con-taining all LiDAR points within b i,where p=[x,y,z,r] denotes a particular LiDAR point in the whole set M.Thefirst form of data augmentation applies perturbation independently to each ground truth3D bounding box to-gether with those LiDAR points within the box.Specifi-cally,around Z-axis we rotate b i and the associatedΩi with respect to(x c,y c,z c)by a uniformally distributed random variable∆θ∈[−π/10,+π/10].Then we add a translation (∆x,∆y,∆z)to the XYZ components of b i and to each point inΩi,where∆x,∆y,∆z are drawn independently from a Gaussian distribution with mean zero and standard deviation1.0.To avoid physically impossible outcomes,we perform a collision test between any two boxes after the per-turbation and revert to the original if a collision is detected. Since the perturbation is applied to each ground truth box and the associated LiDAR points independently,the net-work is able to learn from substantially more variations than from the original training data.Secondly,we apply global scaling to all ground truth boxes b i and to the whole point cloud M.Specifically, we multiply the XYZ coordinates and the three dimen-sions of each b i,and the XYZ coordinates of all points in M with a random variable drawn from uniform distri-bution[0.95,1.05].Introducing global scale augmentation improves robustness of the network for detecting objects with various sizes and distances as shown in image-based classification[35,18]and detection tasks[12,17].Finally,we apply global rotation to all ground truth boxes b i and to the whole point cloud M.The rotation is applied along Z-axis and around(0,0,0).The global ro-tation offset is determined by sampling from uniform dis-tribution[−π/4,+π/4].By rotating the entire point cloud, we simulate the vehicle making a turn.4.ExperimentsWe evaluate V oxelNet on the KITTI3D object detection benchmark[11]which contains7,481training images/point clouds and7,518test images/point clouds,covering three categories:Car,Pedestrian,and Cyclist.For each class, detection outcomes are evaluated based on three difficulty levels:easy,moderate,and hard,which are determined ac-cording to the object size,occlusion state,and truncation level.Since the ground truth for the test set is not avail-able and the access to the test server is limited,we con-duct comprehensive evaluation using the protocol described in[4,3,5]and subdivide the training data into a training setMethod ModalityCar Pedestrian CyclistEasy Moderate Hard Easy Moderate Hard Easy Moderate HardMono3D[3]Mono 5.22 5.19 4.13N/A N/A N/A N/A N/A N/A 3DOP[4]Stereo12.639.497.59N/A N/A N/A N/A N/A N/A VeloFCN[22]LiDAR40.1432.0830.47N/A N/A N/A N/A N/A N/A MV(BV+FV)[5]LiDAR86.1877.3276.33N/A N/A N/A N/A N/A N/A MV(BV+FV+RGB)[5]LiDAR+Mono86.5578.1076.67N/A N/A N/A N/A N/A N/A HC-baseline LiDAR88.2678.4277.6658.9653.7951.4763.6342.7541.06 V oxelNet LiDAR89.6084.8178.5765.9561.0556.9874.4152.1850.49 Table1.Performance comparison in bird’s eye view detection:average precision(in%)on KITTI validation set.Method ModalityCar Pedestrian CyclistEasy Moderate Hard Easy Moderate Hard Easy Moderate HardMono3D[3]Mono 2.53 2.31 2.31N/A N/A N/A N/A N/A N/A 3DOP[4]Stereo 6.55 5.07 4.10N/A N/A N/A N/A N/A N/A VeloFCN[22]LiDAR15.2013.6615.98N/A N/A N/A N/A N/A N/A MV(BV+FV)[5]LiDAR71.1956.6055.30N/A N/A N/A N/A N/A N/A MV(BV+FV+RGB)[5]LiDAR+Mono71.2962.6856.56N/A N/A N/A N/A N/A N/A HC-baseline LiDAR71.7359.7555.6943.9540.1837.4855.3536.0734.15 V oxelNet LiDAR81.9765.4662.8557.8653.4248.8767.1747.6545.11 Table2.Performance comparison in3D detection:average precision(in%)on KITTI validation set.and a validation set,which results in3,712data samples for training and3,769data samples for validation.The split avoids samples from the same sequence being included in both the training and the validation set[3].Finally we also present the test results using the KITTI server.For the Car category,we compare the proposed method with several top-performing algorithms,including image based approaches:Mono3D[3]and3DOP[4];LiDAR based approaches:VeloFCN[22]and3D-FCN[21];and a multi-modal approach MV[5].Mono3D[3],3DOP[4]and MV[5]use a pre-trained model for initialization whereas we train V oxelNet from scratch using only the LiDAR data provided in KITTI.To analyze the importance of end-to-end learning,we implement a strong baseline that is derived from the V ox-elNet architecture but uses hand-crafted features instead of the proposed feature learning network.We call this model the hand-crafted baseline(HC-baseline).HC-baseline uses the bird’s eye view features described in[5]which are computed at0.1m resolution.Different from[5],we in-crease the number of height channels from4to16to cap-ture more detailed shape information–further increasing the number of height channels did not lead to performance improvement.We replace the convolutional middle lay-ers of V oxelNet with similar size2D convolutional layers, which are Conv2D(16,32,3,1,1),Conv2D(32,64,3,2, 1),Conv2D(64,128,3,1,1).Finally RPN is identical in V oxelNet and HC-baseline.The total number of parame-ters in HC-baseline and V oxelNet are very similar.We train the HC-baseline using the same training procedure and data augmentation described in Section3.4.1.Evaluation on KITTI Validation SetMetrics We follow the official KITTI evaluation protocol, where the IoU threshold is0.7for class Car and is0.5for class Pedestrian and Cyclist.The IoU threshold is the same for both bird’s eye view and full3D evaluation.We compare the methods using the average precision(AP)metric. Evaluation in Bird’s Eye View The evaluation result is presented in Table1.V oxelNet consistently outperforms all the competing approaches across all three difficulty levels. HC-baseline also achieves satisfactory performance com-pared to the state-of-the-art[5],which shows that our base region proposal network(RPN)is effective.For Pedestrian and Cyclist detection tasks in bird’s eye view,we compare the proposed V oxelNet with HC-baseline.V oxelNet yields substantially higher AP than the HC-baseline for these more challenging categories,which shows that end-to-end learn-ing is essential for point-cloud based detection.We would like to note that[21]reported88.9%,77.3%, and72.7%for easy,moderate,and hard levels respectively, but these results are obtained based on a different split of 6,000training frames and∼1,500validation frames,and they are not directly comparable with algorithms in Table1. Therefore,we do not include these results in the table. Evaluation in3D Compared to the bird’s eye view de-tection,which requires only accurate localization of ob-jects in the2D plane,3D detection is a more challeng-ing task as it requiresfiner localization of shapes in3D space.Table2summarizes the comparison.For the class Car,V oxelNet significantly outperforms all other ap-proaches in AP across all difficulty levels.Specifically, using only LiDAR,V oxelNet significantly outperforms the。
carried out "practice line pioneer standard, and post spurs" "members concentrated service months", activities, education guide members always everywhere bearing in mind identity, based job post, active play role. To develop differentiated learning education guide party members in accordance with their own situation, target the problems to, based on the work done. Pay attention to the room and room for grass-roots party organizations, grass-roots party organizations have more autonomy in education, making education more ground, full of vitality, good effect. Finally, highlight the normal long-term. To highlight the characteristics of recurrent education, with long flowing, continuous line of perseverance the perseverance to promote educational efforts to realize the party's ideological and political construction of routine institutionalization. With the party branch as the base unit. Play the role of party branches should be, is the key to educational success. Each branch must take strict education and management responsibility of party members, education based on learning to make specific arrangements, fully mobilize the enthusiasm of party members involved in the education, ensure the Organization in place, measures in place, put in place. To the party organization as the basic form. In the standardized development of learning, make learning more effective efforts, and will adhere to the good party group, organized party, party members and the General Assembly, tell a good party lectures, can drive a good topic about, prevent showy without substance, Sham mules. To implement the education management system for basic support. Democratic mutual evaluation on party members in accordance with the regulations, the real performance criteria and order established, sound carefully dispose of unqualified party members, to further improve the dredge export team, pure self cleaning mechanism. Party leading cadres should adhere to and implement the central group learning system, to which branch of learning exchanges, participation in a dual organization with comrades. Focus on recurrent education, you also need to continue to strengthen the building of grass-roots party organizations. Now, the city also has 88 village party organizations are weak and lax, first Secretary of the village, but conversion requires a process. Recently, the city's party organization focused investigation, check out a total of "lost" members 4,507, "Pocket" members 1037, find there are 640 "lost" party members are not contacted 148 "Pocket" party members and implementation of organizational relationships. Educational management of party members into the Organization, there is a lot of work to do. Weak and lax party continued reorganization as an important task, finish perfect organization, with a good team, Good system. Special highlights of grass-roots party organizations, to be dealt with first in place, further education, reorganization, transformation and educational interaction. In short, through solid and effective work initiativesbroken problem, fill the short Board, so that the majority of party members and fully qualified, comprehensive skills of grass-roots party organizations, grass-roots party level upgrade. Comrades, do a "two" learning education is of great significance, responsibilities, carry significant implications. City levels party and general members cadres, to deep awareness "two learn a do" learning education of importance and need, to height of political consciously and full of political enthusiasm, put "two learn a do" learning education carried out good, for coordination advance "four a full" strategy layout, and achieved "Thirteen-Five" good start, and speed up construction more high ecological vitality happiness of City provides strong powerful guarantee. Two, starting from the revered Constitution respected the party Constitution was XI Jinping, General Secretary to the party's request, 18 six plenary session of the Central Commission for discipline inspection report "five experience" first. Full strictly administering the party, first of all, to exalt the party Constitution, and pipe the whole party, the ruling party of the party Constitution. Revered Constitution reflected in awe. Party a party of ideals and beliefs purpose, summed up the party's fine tradition and style; a clear party members and what can be done and what must be done, what cannot be done. Each Communist Party Constitution to awe and wary eye enhancing the sacred sense of responsibility and mission. Hearts filled with party Constitution, hold the party line, BA obligations unconditionally carry out party members, according to the Constitution of direction towards standards efforts. Respect reflected in the study the party Constitution means. Some party members joined the party Constitution on the shelf, not to learn, some long-term party according to the Constitution of the party's organization, the party is not required to pay membership dues, loose concept, party organizations of the party organization, and turned a blind eye on the tasks assigned by the Organization, were forgotten, forgotten vows performance the party Constitution. Constitution is the fundamental standard of our Communists are slim, the party Constitution to repeatedly learn, practice, thinking, learning and thinking, thinking and row, row, ever-spiraling increase in the learning process. Respect party lines reflected in practice. Two to learn a basic Constitution Party rules, series of speeches, the key to be qualified party members. To be qualified party members, standards are not high, but if he does take a ruler of the party Constitution to "card", truly it is not easy. Carry out study and education, every party must control the party's eight obligations, ask, look for gaps, identify problems, clear direction, work to solve specific problems. Actively practicing in the production life of the eight obligations, to play a vanguard and exemplary role, truly a party banner. "Two" fight to highlight grass-roots party organizationssudo sysctl -w kernel.randomize_va_space=0此外,为了进一步防范缓冲区溢出攻击及其它利用shell 程序的攻击,许多shell 程序在被调用时自动放弃它们的特权。

RSOFT 使用教程目录Rsoft 简介 ...............................................错误 ! 不决义书签。
Chapter 7 Tutorials第七章教程 . .........................错误 ! 不决义书签。
Tutorial 1: Ring Resonator教程 1:环形共振器 ...........错误 ! 不决义书签。
Device Layout:器件构造: . ...........................错误 ! 不决义书签。
Defining Variables定义变量 . .........................错误 ! 不决义书签。
Drawing the Structure画器件构造图 . ..................错误 ! 不决义书签。
Checking the Index Profile查对折射率散布 ............错误 ! 不决义书签。
Adding Time Monitors增添时间监督(探测)器 ..........错误 ! 不决义书签。
Simulation: Pulsed Excitation模拟:脉冲激发 .............错误 ! 不决义书签。
Launch Field 激发场 . .................................错误 ! 不决义书签。
Wavelength/Frequency Spectrum波长 / 频次光谱 ..........错误 ! 不决义书签。
Increasing the Resolution of the FFT提升 FFT 的分辨率错误 ! 不决义书签。
Simulation: CW Excitation模拟:连续激发 ................错误 ! 不决义书签。
Tutorial 2: PBG Crystal: Square Lattice教程2:PBG晶体:四方晶格错误!不决义书签。

disable function绕过原理disable function是一种绕过原理,用于绕过软件或者系统中的某个功能或者保护机制,以获取未授权的访问权限或者执行潜在的恶意操作。
这种技术常被黑客或者攻击者用于入侵系统、获取敏感信息、实施网络攻击等恶意活动。
下面将详细介绍disable function的原理和应对措施。
disable function的原理基于一些软件或者系统在运行过程中为了安全性考虑而实施的功能限制措施。
例如,一些网站或者应用程序可能为了防止用户执行恶意操作或者访问危险网站而对某些功能进行禁用。
这些功能可能包括文件上传、特定URL的访问、数据库访问等。
disable function的绕过常见的方法有以下几种:1. 代码注入:攻击者可以通过在输入数据中插入恶意代码,绕过对于某些功能的限制。
例如,一些应用程序可能会对用户输入的URL进行过滤,以防止访问危险网站。
攻击者可以通过在URL中插入一些特殊字符或者恶意代码来绕过过滤机制,从而访问被禁用的功能或者网站。
2. 文件上传漏洞:一些网站或者应用程序可能会禁用用户上传文件的功能,以防止上传恶意文件。
然而,存在一些文件上传漏洞可以被攻击者利用,绕过这个限制。
攻击者可以通过利用这些漏洞上传恶意文件,从而执行任意的恶意操作,例如执行系统命令、访问敏感文件等。
3. 绕过URL访问限制:某些应用程序可能会限制对某些URL的访问,以防止用户访问危险网站或者执行不安全的操作。
攻击者可以通过修改请求的参数或者其他手段绕过这些限制,从而访问被禁用的URL。
对于disable function的防御措施如下:1. 输入验证和过滤:对于用户输入的数据,应该进行严格的验证和过滤,以防止恶意代码的注入。
可以使用安全编码技术,例如输入验证、正则表达式匹配等,来确保输入数据的安全性。
2. 安全配置和设置:在配置和设置软件或者系统时,应该考虑到功能限制和保护机制的设置。
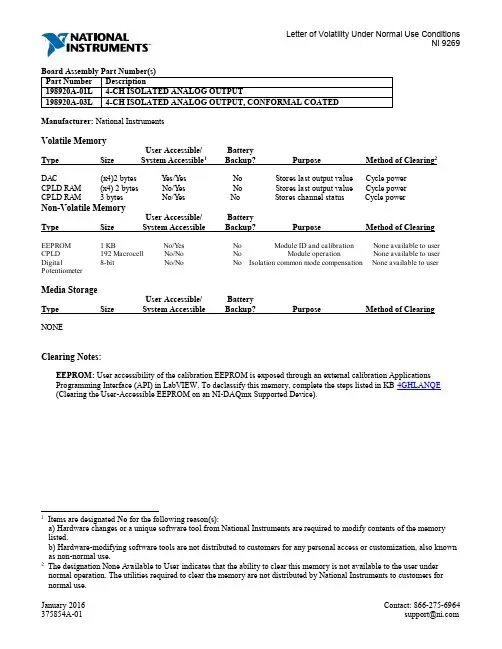
Manufacturer: National InstrumentsVolatile MemoryUser Accessible/ BatteryType Size System Accessible1Backup? Purpose Method of Clearing2DAC (x4)2 bytes Yes/Yes No Stores last output value Cycle powerCPLD RAM (x4) 2 bytes No/Yes No Stores last output value Cycle powerCPLD RAM 3 bytes No/Yes No Stores channel status Cycle powerNon-Volatile MemoryUser Accessible/ BatteryType Size System Accessible Backup? Purpose Method of ClearingEEPROM 1 KB No/Yes No Module ID and calibration None available to user CPLD 192 Macrocell No/No No Module operation None available to user Digital 8-bit No/No No Isolation common mode compensation None available to user PotentiometerMedia StorageUser Accessible/ BatteryType Size System Accessible Backup? Purpose Method of ClearingNONEClearing Notes:EEPROM: User accessibility of the calibration EEPROM is exposed through an external calibration Applications Programming Interface (API) in LabVIEW. To declassify this memory, complete the steps listed in KB 4GHLANQE (Clearing the User-Accessible EEPROM on an NI-DAQmx Supported Device).1 Items are designated No for the following reason(s):a) Hardware changes or a unique software tool from National Instruments are required to modify contents of the memory listed.b) Hardware-modifying software tools are not distributed to customers for any personal access or customization, also known as non-normal use.2 The designation None Available to User indicates that the ability to clear this memory is not available to the user under normal operation. The utilities required to clear the memory are not distributed by National Instruments to customers for normal use.Terms and DefinitionsUser Accessible Allows the user to directly write or modify the contents of the memory during normal instrument operation.System Accessible Does not allow the user to access or modify the memory during normal instrument operation. However, system accessible memory may be accessed or modified by background processes. This can be something that is not deliberate by the user and can be a background driver implementation, such as storing application information in RAM to increase speed of use.Cycle Power The process of completely removing power from the device and its components. This process includes a complete shutdown of the PC and/or chassis containing the device; a reboot is not sufficient for the completion of this process. Volatile Memory Requires power to maintain the stored information. When power is removed from this memory, its contents are lost.Non-Volatile Retains its contents when power is removed. This type of memory typically contains calibration or chip configuration information, such as power up states.。
exallocatepooluninitialized -回复题目:exallocatepooluninitialized:详解Windows内存管理中的常见错误引言:在Windows内存管理中,exallocatepooluninitialized是一个常见的错误,它通常发生在开发人员使用ExAllocatePool函数时未初始化分配的内存时。
本文将深入剖析exallocatepooluninitialized错误,探讨其原因和解决方案,以帮助开发人员更好地理解和处理这一问题。
第一部分:理解exallocatepooluninitialized错误1.1 exallocatepooluninitialized错误的定义和特点- exallocatepooluninitialized错误是在使用ExAllocatePool函数时,未对分配的内存进行初始化而产生的;- 该错误在操作系统内核中经常发生,但在应用程序也可能出现;- 错误会导致内存泄漏和未定义行为,严重时会导致系统崩溃。
1.2 错误原因的分析- 常见原因之一是开发人员对内存分配过程理解不够深入,忽略了初始化的重要性;- 另一个原因是在多线程或并发操作下,开发人员没有正确进行内存保护和同步操作。
第二部分:解决exallocatepooluninitialized错误的方法2.1 确保正确的内存分配和初始化- 在使用ExAllocatePool函数时,务必确保在分配内存之后立即进行初始化;- 可以使用RtlZeroMemory或KeZeroMemory等函数进行内存清零;- 对于复杂的数据结构,可以使用memset函数进行初始化。
2.2 同步和内存保护- 在多线程或并发操作中,通过使用锁或同步机制,确保在对同一内存区域进行读写时的同步;- 可以使用自旋锁、互斥锁、信号量等同步机制进行内存保护。
2.3 使用合适的内存管理技术- 可以考虑使用对象池或缓存池等技术,减少频繁的内存分配和释放;- 对于频繁分配和释放的小块内存,可以使用内存池技术进行高效管理。
B+K Precision ®models 9120A,9121A,9122A,9123A and 9124are laboratory grade Programmable DC Power Supplies providing great performance and features not found in other supplies in this price category.The 9120series are designed to meet the needs of today’s applications in R&D design verification,production testing or university labs that require clean and reliable power,high resolution and accuracy and fast transient response time.IExcellent display resolution I Low ripple and low noiseI Outstanding temperature stabilityI Fast transient response time (<150µs)I SCPI compatibleI Front and Rear Output T erminals I Closed case calibrationI Compact size for bench use or rack mountable (2U x 1/2U size)I List mode operation for increased throughput.Download and execute command sequences from non-volatile memory91244mm sheathed safety banana jacksOutput ON/OFF switchEncoder knob for quick analog style controlNumeric keys for direct entry of voltage and current valuesHigh resolution displayFront Panel OperationThe numeric keys and rotary knob provide a convenient interface for setting output levels quickly and precisely.Voltage and Current can be set to a maximum resolution of 0.5mV (2mV for 9124)and 0.1mA respectively.Up to 50parameters can be stored and recalled from internal memory.Data sheetTechnical data subject to change ©B&K Precision Corp.2008v031609Single Output Programmable DC Power SuppliesModels 9120A, 9121A, 9122A, 9123A & 9124DVM and m ΩmeterUser accessible fuseT emperature controlled cooling fan Serial interface connector for RS232 or USB communication.(USB communication cable is optional).Model 9123A also supports control via GPIB interface.Remote Sense and digital port functionalityThe 9120 series uses 4mm sheathed banana jacks that accept sheathed or shrouded banana plugs and meet the latest international safety standards.Extra FeaturesThe 9120 series’ digital port offers a variety of configurations. The port can operate in Digital I/O,external Trigger and DFI/RI (Discrete FaultIndicator/Remote Inhibit) mode. The RI feature can be used for turning several power supplies On/Off simultaneously. External triggering can be used in combination with List mode.The included Application Software supports front panel emulation and allows users to generate simple test sequences without the need to write source code.Additionally, the power supply comes with a built-in 51/2 digit DVM and high resolution milliohm meter supporting 4 wire measurements.Remote InterfaceThe power supplies can be remotely controlled from any PC with USB or RS232 interface, allowing the user to program and monitor all parameters through easy to use SCPI commands.The power supplies come with a RS232 to TTL serial converter cable. A USB to serial converter cable is available as option. Additionally, model 9123A can be controlled via GPIB interface and includes a GPIB to TTL conversion adapter cable.2Single Output Programmable DC Power Supplies Models 9120A, 9121A, 9122A, 9123A & 9124。
MySQL中的查询缓存无效和命中率优化引言在MySQL数据库中,查询缓存是一种用于提高数据库查询性能的重要机制。
它通过缓存查询的结果,避免了频繁执行相同查询的开销。
然而,在某些情况下,查询缓存可能会失效,并导致低命中率。
本文将探讨MySQL中查询缓存无效的原因,并提供一些优化命中率的方法。
一、查询缓存的工作原理MySQL查询缓存是基于内存的,允许存储查询和对应的结果集。
当一个查询被执行时,MySQL首先检查查询缓存是否已经存在该查询的结果。
如果结果已经缓存,则直接返回缓存的结果集,而不需要再次执行查询。
这种机制可以大大减少查询的响应时间,提高系统的吞吐量。
二、查询缓存无效的原因尽管查询缓存在提高性能方面有很大的潜力,但它也有一些限制,可能导致它无效化,包括以下几个方面:1. 数据表发生更改当数据表发生更新、插入或删除操作时,相关的查询缓存将被自动失效。
因为数据表的更改可能导致查询结果不再有效,所以MySQL会自动将查询缓存中的相关结果清除。
这也是为什么查询缓存在高写入负载的系统中效果不佳的原因之一。
2. 不同的连接权限MySQL查询缓存是基于每个连接的,也就是说,不同的用户连接具有不同的查询缓存。
因此,当不同连接执行相同的查询时,即使是相同的查询语句,也会被认为是不同的查询,从而无法利用查询缓存。
3. 查询不在缓存范围内MySQL查询缓存是基于完全匹配的查询,这意味着如果查询语句中包含任何不同的字符(包括空格和大小写),即使它们执行的是相同的查询,也会被认为是不同的查询,从而无法使用查询缓存。
因此,如果查询中存在动态参数或变量,查询缓存将无法生效。
三、提高查询缓存命中率的优化方法虽然MySQL查询缓存有时会无效,但我们可以通过一些优化方法来提高命中率,从而最大程度地利用查询缓存的优势。
1. 合理设置查询缓存大小在MySQL的配置文件中,有一个参数用于设置查询缓存的大小,即"query_cache_size"。
pgpool pgpool_authentication_method -回复题目:深入探究Pgpool的身份验证方法引言:Pgpool是一个流行的开源连接池和负载均衡工具,尤其为PostgreSQL数据库提供了高可用性和性能的增强功能。
其中的身份验证方法是确保用户安全访问数据库的重要组成部分。
在本文中,我们将一步一步地探讨Pgpool的身份验证方法,并深入了解如何在配置Pgpool时选择正确的身份验证方法,以满足用户的需求。
第一部分:了解Pgpool的身份验证方法1. "trust"身份验证方法:- 描述:此身份验证方法允许任何用户通过身份验证,并且不需要密码。
- 适用场景:仅在特定安全环境下使用,例如测试或内部网络,不建议在生产环境中使用。
2. "reject"身份验证方法:- 描述:该身份验证方法拒绝所有用户的登录尝试。
- 适用场景:在特殊情况下,如进行维护期间,防止用户对数据库进行访问。
3. "md5"身份验证方法:- 描述:当用户登录时,Pgpool将提取其提供的密码,并使用MD5算法对其进行哈希,然后与存储在配置文件中的哈希进行比较。
- 适用场景:在需要密码保护的生产环境中使用,提供适度的安全性。
4. "password"身份验证方法:- 描述:此身份验证方法要求用户在登录时输入密码。
Pgpool将检查输入的密码是否与存储在配置文件中的密码匹配。
- 适用场景:在需要更高安全性的生产环境中使用。
5. "pam"身份验证方法:- 描述:使用PAM(Pluggable Authentication Modules)机制对用户进行身份验证,以允许外部身份验证方法如LDAP或Active Directory。
- 适用场景:当需要与现有身份验证系统集成时使用。
第二部分:配置Pgpool验证方法1. 编辑pgpool.conf文件:- 在配置文件中,找到参数“authentication_method”。
content-security-policy nonce-规则-回复Content-Security-Policy Nonce规则是使用Nonce值来提供更强大的安全性和防御机制的一种策略。
在本篇文章中,我们将逐步解释什么是Nonce以及如何使用它来保护网站免受恶意攻击。
第一步:什么是Nonce?Nonce是一个随机生成的值,用于限制特定资源的加载和执行。
这个值只能由服务器生成并与响应一起发送给客户端。
因为Nonce是每次请求都不同的值,所以攻击者无法预测或伪造它。
第二步:义务和策略服务器使用Content-Security-Policy(CSP)头来传达网站的安全策略给浏览器。
CSP库里面的Nonce指令告诉浏览器,只有在匹配特定Nonce 值的script内联脚本才会被执行。
这个策略基于服务器和浏览器之间的互动,其中服务器为每个请求生成Nonce值,并将其放入相应的CSP头中。
第三步:生成和使用Nonce值生成Nonce值的方法因服务器配置和编程语言而异。
通常情况下,Nonce 值应该是随机且具有足够的复杂性,以避免被猜测或伪造。
服务器应该在生成Nonce值后,将其插入CSP头中并发送给浏览器。
第四步:配置服务器为了使用Nonce规则,服务器需要配置CSP头来包含Nonce值。
这可以通过添加"Content-Security-Policy" HTTP头,并在"script-src"指令中包含"nonce-{nonce_value}"来实现。
服务器将会在每次请求中动态生成Nonce值并将其插入"nonce-{nonce_value}"占位符中。
第五步:启用Nonce规则当客户端收到响应时,它会解析CSP头并检查服务器是否指定了Nonce 规则。
如果是的话,浏览器将只执行包含正确Nonce值的脚本。
这样,即使恶意代码被插入到网页中,浏览器也会拒绝执行,因为它们缺少正确的Nonce值。