2009级吉林大学计算机学院-计算机导论试题B卷
- 格式:doc
- 大小:72.50 KB
- 文档页数:3

河南省2009年普通高等学校对口招收中等职业学校毕业生考试计算机类专业课试题卷一、选择题(数据库应用基础-Visual Foxpro6.0 1-10;计算机网络基础11-23)1.用二维表格来表示数据集合以及它们之间联系的数据模型是A.层次模型B.关系模型C.网状模型D.面向对象模型2.在Visual Foxpro 6.0主界面中,显示已隐藏的命令窗口,应使用的组合键是A.ALT+Q B.CTRL+Q C.CTRL+F2D.CTRL+F43.Visual Foxpro 6.0的PACK命令用来清除当前数据表文件的A.全部记录B.有删除标记的记录C.满足条件的字段D.满足条件的记录4.要修改当前数据表文件的“姓名”字段,应使用的命令是A.MODIFY COMMAND B.MODIFY QUERYC.MODIFY STRUCTURE D.MODIFY FORM5.非空数据表文件及其索引文件都已经打开,确保记录指针定位在记录号为1的记录,应使用的命令是A.GOTO TOP B.GOTO BOF C.SKIP 1 D.GOTO 16.下列命令中,只能关闭当前数据库的是A.CLOSE ALL B.USE C.CLOSE D.CLOSE DA TABASE 7.使用报表向导创建报表的过程中,进行到“定义报表布局”步骤时的选项有A.列数、方向、字段布局B.列数、行数、字段布局C.行数、方向、字段布局D.列数、行数、方向8.Visual Foxpro 6.0中,视图不能单独存在,它依赖于A.表B.数据库C.查询D.表单9.表达式V AL(SUBSTR("5.12汶川大地震",1,4))的运算结果是A.5.12B."5.12" C..T. D.出错10.以下有关索引的说法中正确的是A.建立主索引的主关键字值不能为空,但可以有重复数值B.主索引既可在自由表中创建,也可以在数据库表中创建C.侯选索引既可在自由表中创建,也可以在数据库表中创建D.建立唯一索引的索引关键字值不能有重复值11.建立计算机网络的目的是实现计算机资源共享。

计算机导论》试卷1注意事项:1)本试卷适用于计算机相关专业本科学生使用。
2)本试卷共7页,满分100分。
考试时间120分钟。
一)单项选择题(1分×70=70分)1C234B)RAM是一种半导体存储器C)RAM中的信息不能长期保存D)RAM用来存放计算机本身的监控程序5、ASCII码值由小到大的一般顺序是。
A)特殊符号、控制符、数字、大写字母、小写字母B)控制符、特殊符号、数字、大写字母、小写字母C)大写字母、小写字母、数字、特殊符号、控制符D)数字、特殊符号、控制符、小写字母、大写字母6、扩展名为COM类文件为。
A)命令解释文件B)C语言源程序文件7891011、批处理操作系统是一个操作系统。
A)交互式B)分时C)非交互式D)网络式12、把高级语言的源程序变为目标程序要经过。
A)汇编B)编译C)编辑D)解释13、微机的性能指标中的内部存储器的容量是指。
A)RAM的容量B)ROM的容量C)硬盘的容量D)RAM和ROM的容量14、现代计算机之所以能自动连续进行数据处理,主要因为。
15、16171819、计算机一旦断电后中的信息会丢失。
A)硬盘B)软盘C)RAM D)ROM20、系统软件中最重要的是A)操作系统B)语言处理程序C)工具软件D)数据库管理系统21、总线是连接计算机各部分的一镞公共信号线,它是计算机中传送信息的公共通道,总线是由地址总线)数据总线和控制总线组成,其中地址总线是_在微机各部分之间传送的线路。
A)数据信号B)控制信号22AC23AC24AC2526、TCP/IP协议的含义是。
A)局域网传输协议B)拨号入网传输协议C)传输控制协议和网际协议D)OSI协议集27、Internet的域名结构中,顶级域名为Edu的代表。
A)商业机构B)政府部门C)教育机构D)军事部门28、电子邮件是A)网络信息检索服务。
B)通过Web网页发布的公告信息C)通过网络实时交互的信息传递方式29A)C)3031、A)C)32A)C)BitsPerSecondD)BillionPerSecond33、在因特网(Internet)中,电子公告板的缩写是。
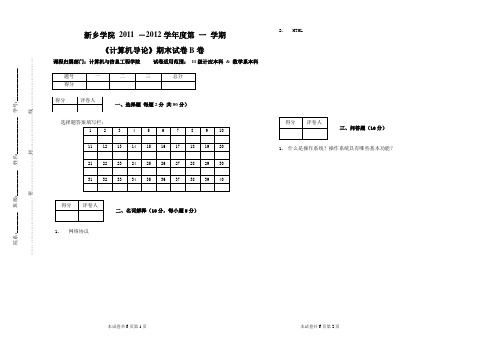
新乡学院2011 ―2012学年度第一学期《计算机导论》期末试卷B卷课程归属部门:计算机与信息工程学院试卷适用范围:11级计应本科& 数学系本科选择题答案填写栏:二、名词解释(10分,每小题5分)1.网络协议2.HTML三、问答题(10分)1.什么是操作系统?操作系统具有哪些基本功能?一、选择题每题2分共80分)院系:________班级:__________姓名:______________学号:_____________…….……………………….密…………………封…………………线…………………………新乡学院2011 ―2012学年度第一学期《计算机导论》期末试卷B卷课程归属部门:计算机与信息工程学院试卷适用范围:11级计应本科& 数学系本科一、选择题每题2分共80分)1.商业企业进销存管理系统属于。
A.科学计算方面的计算机应用B.数据处理方面的计算机应用C.过程控制方面的计算机应用D.人工智能方面的计算机应用2.下列数中最大的数是。
A.(1000101)2B.(107)8C.(73)10D.(4B)163.假设某计算机的字长为8位,则十进制数(+67)10的反码表示为。
A.01000011B.00111100C.00111101D.101111004.已知:“B”的ASCII码值是66,则码值为1000100的字符为。
A.“C”B.“D”C.“E”D.“F”5.下面的输入设备中,不属于定点输入设备?A. 鼠标B. 触摸屏C. 光笔D. 键盘6..在逻辑运算中有Y=A+B,则表示逻辑变量A和B进行。
A.与运算B.或运算C.非运算D.与非运算7.计算机的内存储器比外存储器。
A.更便宜B.存储速度快C.存储容量大D.虽贵但能存储更多信息8.计算机工作时,内存储器用来存储。
A.程序和指令B.程序与数据C.数据和信号D.ASCII码和汉字编码9.CPU中临时存放数据的部件是。
A.算术逻辑单元B.存储器C.寄存器D.控制器10.为了解决CPU与主存的速度匹配问题,可采用。

一、选择题(每小题 2分,共50分)1、现在的计算机是基于()模型。
A. 莱布尼茨B. 冯.洛伊曼C. 帕斯卡D. 查尔斯.巴比奇2、目前人们常说“IT人才”,其中IT是指()。
A. 交互技术B. 信息技术C. 制造技术D. 控制技术3、下列不同数制的数值中,最大的一个是()。
A.(1001)2 B.(70)8 C.(70)10 D.(70)164、目前硬盘与内存相比,具有()的特点。
A. 存储容量小,工作速度快B. 存储容量大,工作速度快C. 存储容量小,工作速度慢D. 存储容量大,工作速度慢5、为了提高计算机中CPU的性能,可以采用多种措施,但以下措施中()是基本无效的。
A. 使用多个算术逻辑部件B. 提高中央处理器的主频C. 增加中央处理器的字长D. 增大辅助存储器的容量6、存储器容量是1KB,实际包含()字节。
A. 1000B. 1024C. 1024GD. 1000M7、()是可以存放临时数据的独立存储单元。
A.ALUB. 寄存器C. 控制单元D. 磁带驱动器8、在“资源管理器”中进行文件操作时,为了选择多个不连续的文件,必须首先按住()健。
A. AltB. ShiftC. INSD. Ctrl9、( ) 键是大写字母锁定键,主要用于连续输入若干大写字母。
A. Shift B. Alt C. Ctrl D. CapsLock10、启动Windows后,出现在屏幕的整个区域称为( )。
A.工作区域 B.桌面 C.文件管理器 D.程序管理器11、在Windows中移动窗口时,鼠标光标要停留在()处拖拽。
A. 菜单栏B. 状态栏C. 标题栏D. 工具栏12、在使用Word文本编辑软件时,插入点位置是很重要的,因为文字的增删都将在此处进行,现在要删除一个字,当插入点在该字的前面时,应该按()键。
A. 退格键B. 删除键C. 空格键D. 回车键13、在Word文档中插入图形的第1步操作是()。
A. 执行“插入”菜单中的“图片”命令B.将插入点置于图形预期出现的位置C.在图片对话框中选择要输入的图片文件名D.单击“确定”按钮,插入图片14、某Excel工作表的单元格区域A2:C4输入数值均为10,若在C1单元格内输入公式“=Sum(A2:C4)”,则C1单元格的显示结果是()。

计算机导论习题(答案)一、单项选择题1. 问题逐步解决的方案被称为 D 。
A. 硬件B. 操作系统C. 计算机语言D. 算法2、十进制整数A要转换为二进制数据,需要用的方法是 A 。
A.反复“以2除A并取其商的余数”B.反复“以10除A并取其商的余数”C.反复“以2乘A并取其积的整数”D.反复“以10乘A并取其积的整数”3. 把十进制数转换成8进制,需要不断用 C 来除这个数。
A. 2B. 4C. 8D. 104、6位无符号二进制整数所能表示的最大十进制整数是 B 。
A.64 B.63C.62 D.615.如果计算机断电,那么下列 A 中的数据将被擦除。
A. RAMB. ROMC. 磁带驱动器D. CD-ROM6、依据冯·诺依曼模型, C 将被存储在存储器之中。
A.仅有数据B.仅有程序C.程序及其所处理的数据D.以上都不是7. 16千兆的字节是 C 字节。
A. 2^16B. 2^40C. 2^34D. 2^568、冯·诺依曼模型中的控制单元用于对 D 子系统的操作进行控制。
A.算数逻辑单元B.存储器C.输入输出D.以上都是9. 子算法又称为 C 。
A. 函数B. 子例程C. 模块D. 过程10、十六进制数CE2所对应的位模式是 D 。
A.001100011101 B.101100011101C.010********* D.11001110001011. C、C++可归类于 C 语言:A.机器; B.符号;C.高级; D.自然。
12. 包括行和列的数组可能是 B 数组:A.一维; B.二维;C.三维; D.多维。
13、十进制数 -124表示在计算机内的8位二进制补码形式是 D 。
A.01111100 B.10000011C.01111011 D.1000010014. C 是有交换功能的多道程序技术A.分区调度;B.分页调度;C.请求分页调度;D.队列。
15、下列各项中 C 的程序是属于操作系统进程管理概念中的进程。

计算机导论考试题库大全(word版可编辑修改)编辑整理:尊敬的读者朋友们:这里是精品文档编辑中心,本文档内容是由我和我的同事精心编辑整理后发布的,发布之前我们对文中内容进行仔细校对,但是难免会有疏漏的地方,但是任然希望(计算机导论考试题库大全(word 版可编辑修改))的内容能够给您的工作和学习带来便利。
同时也真诚的希望收到您的建议和反馈,这将是我们进步的源泉,前进的动力。
本文可编辑可修改,如果觉得对您有帮助请收藏以便随时查阅,最后祝您生活愉快业绩进步,以下为计算机导论考试题库大全(word版可编辑修改)的全部内容。
《计算机导论》模拟试题一一、单选题(每小题1分,共80分)1.客机、火车订票系统属于。
A.科学计算方面的计算机应用B.数据处理方面的计算机应用C.过程控制方面的计算机应用 D。
人工智能方面的计算机应用2。
按照计算机用途分类,可将计算机分为。
A。
通用计算机、个人计算机 B.数字计算机、模拟计算机C.数字计算机、混合计算机 D。
通用计算机、专用计算机3.下列数中最大的数是。
A.(1000101)2B.(107)8 C。
(73)10 D。
(4B)164。
已知:3×4=10,则5×6= .A.24 B。
26 C.30 D.365。
假设某计算机的字长为8位,则十进制数(+67)10的反码表示为。
A。
01000011 B。
00111100 C.00111101 D。
101111006.假设某计算机的字长为8位,则十进制数(—75)10的补码表示为。
A.01001011B.11001011C.10110100 D。
101101017。
已知:“B”的ASCII码值是66,则码值为1000100的字符为。
A。
“C” B。
“D” C.“E" D。
“F”8.在计算机系统内部,汉字的表示方法是采用。
A.ASCII码B.机内码C.国标码D.区位码9。
汉字“办”的区位码是1676,其国标码是。

吉林大学软件学院《数据库原理》期末试题B卷(答案)2009-2010学年第2学期2007级《数据库系统》考试题(B)考试时间:2010年6月班级:学号:姓名:请将答案写在答题纸上,写明题号,不必抄题,字迹工整、清晰;请在答题纸和试题纸上都写上你的班级,学号和姓名,交卷时请将试题纸、答题纸和草纸一并交上来。
一、[20分]用英文解释下列名词:1.Schema:the logical structure of the database2.Instance:the actual content of the database at a particular point in time3.Entity:a “thing” or “object” in the enterprise that is distinguishable from otherobjects4.1NF:A relational schema R is in 1NF if the domains of all attributes of R areatomic5.Super Key:A super key of an entity set is a set of one or more attributes whosevalues uniquely determine each entity.6.RAID:Redundant Arrays of Independent Disks,disk organization techniquesthat manage a large numbers of disks, providing a view of a single disk7.Clustering index:in a sequentially ordered file, the index whose search keyspecifies the sequential order of the file8.Query Optimization:Amongst all equivalent evaluationplans choose the onewith lowest cost.9.Specialization:T op-down design process; we designate subgroupings within anentity set that are distinctive from other entities in the set10.Conflict serializable:We say that a schedule S is conflict serializable if it isconflict equivalent to a serial schedule二、[15分]以下是某健身俱乐部的会员管理数据库,其保存的信息有:·置业顾问(adviser)的编号Ano,姓名Aname,性别Asex,电话Atel;·客户(customer)的身份证号码Cid,姓名Cname,年龄Cage,联系电话Ctel ;·每个客户有且仅有一个置业顾问,一个置业顾问可以为多个客户提供咨询服务;·每个客户可以进行多次卖房或买房业务,在一次交易过程中,买方与卖方是一一对应的;·试画出E-R图,并将其转换为符合3NF规范的关系模型1.画出上述关系的E-R模型[10分]2.将E-R模型转换为符合3NF规范的关系模型[5分]Members = (cid, cname, cage, csex, phone, cdate, type, discount)Adviser = (ano, aname, asex, atel, level)Alevel = (Level, salary, awards)MA = (Cid, Ano, MAtime)三、[15分] 设有关系数据库e ( e#, en, ea, ex, d# ) p ( p#, pn, pt, pb )ep ( e#, p#, b ) d ( d#, dn, dl )其中,e#, en, ea, ex依次分别表示工程师编号、姓名、年龄、性别;p#, pn, pt, pb依次分别表示工程项目编号、名称、类别、预算;ep示工程师参加工程项目,b 表示奖金;d#, dn, dl依次分别表示部门编号、部门名称、部门地址;试用关系代数表达:1. 查询年龄大于40的工程师的编号和姓名∏e#,en (σea > 40(e))2. 查询所有参加了A项目,但没有参加B项目的工程师编号∏e#(σp# = 'A'(e ∞ ep))- ∏e#(σp# = 'B'(e ∞ ep))3. 查询参加所有pb大于100000的工程项目的工程师的编号和姓名∏e#,en (σpb > 100000(e ∞ ep ∞ p))4. 查询pb最大的工程项目的编号和工程名称∏p#,pn (p#gmax(pb)(p))5. 假设有一部分工程师没有参与任何项目,查询该单位所有的工程师的名字以及其所参与的项目编号∏e#,p#(e =∞ p)四、[20分] 题设与第三题相同。

2008级吉林大学软件学院-计算机导论试题A卷2007-2008学年第1学期2008级《计算机导论》考试试题A卷考试时间:2008年12月28班级学号姓名请将答案写在答题纸上,写明题号,不必抄题,字迹工整、清晰;请在答题纸和试题纸上都写上你的班级,学号和姓名,交卷时请将试题纸、答题纸和草纸一并交上来。
Ⅰ.Choice Questions(30 questions, 1 score for each question)1. The step by step solution that expresses the logical solution to a particular problem of interest is called a(n) ________.A. programB. answerC. algorithmD. process2. The ASCII character set includes ________ characters.A. 4,294967296B. 256C. 65536D. 1273. The most common way to represent signed integers today is ________.A. two’s complementB. one’s complementC. sign-and magnitudeD. unsigned integers4.What is -31 in Excess_127 notation? ________A. 01100001B. 01100000C. 10011111D. 111000015.To subtract two binary numbers, take the ________ of the second number, and then add.A. inverseB. one's complementC. two's complementD. square root6. Every computer today is based on the ________ model..A. IntelB. MicrosoftC. von NeumannD. input/output7. The place where programs and data are stored during processing is ________..A. displayB. hard diskC. floppy diskD. memory8. A computer stores data as a ________ pattern.A. binaryB. hexadecimalC. unaryD. numeric9. An 8-bit pattern can represent up to ________ symbols.A. 128B. 256C. 16D. 810. A byte consists of ______ bits.A. 2B. 4C. 8D. 111. If the memory address space is 32MB and the word size is 8 bits, then ______bits are needed to access each word.A.25B. 16C. 8D. 3212. The three steps in the running of a program on a computer are performed ______in this specific order.a. fetch, execute, and decodeb. fetch, decode, and executec. decode, fetch, and executed. decode, execute, and fetch13.A ______is a device that can route a packet based on its network layer address.A. bridgeB. repeaterC. routerD. all of the above14.In the ______method to synchronize the operation of the CPU with the I/O device, the I/O device informs the CPU when it is ready for data transfer.A. programmed I/OB. DMAC. isolated I/OD. interrupt-driven I/O15. A(n) ________ search is used if the list being searched is not ordered.A. heapB. binaryC. 8. selectionD. sequential16. Using the XOR (exclusive OR) operator, if more than one input is 1, the output is ________.A. 0B. 1C. indeterminateD. equal to the number of inputs that are 117.If you make a mask of all 0s and then AND the bit pattern and the mask, you will _______.A. set all the bits of the patternB. unset all the bits of the patternC. randomize the bits of the patternD. complement the bits of the pattern18. The ______ is a computer subsystem that performs operations on data.A. memoryB. I/O hardwareC. CPUD. RAM19.Memory addresses are defined using ________.A. signed binary integersB. two's complement representationC. floating point numbersD. unsigned binary integers20. The ________ moves a process from one state to another.A. control unitB. job schedulerC. system administratorD. process scheduler21.The idea of a sorting algorithm is to ________.A. determine if a particular item is present or notB. arrange data according to their valueC. compute the sum of all the items in an arrayD. output the items in an array22. A binary search starts the process ________ of a list.A. at the beginningB. at a random locationC. in the middleD. at the end23. What needs to be added to the simple black box model of a data processing device to make it more applicable to a computer?A. BIOSB. Power supplyC. Operating systemD. Program24. A program is comprised of a finite number of ________.A. instructionsB. memory cellsC. i/o devicesD. hard drives25.A(n) ________ operates ate the first three layers of the OSI model.A. hubB. repeaterC. routerD. bridge26. Machine language is ________.A. written in LinuxB. the only language understood by a computerC. the same as assembly languageD. variant of BASIC27.Recursion is a process by which an algorithm calls ________.A. a sorting algorithmB. a search algorithmC. itselfD. a subalgorithm28. The transport layer protocol of TCP/IP is called _______.A. TCPB. UDPC. IPD. a and b29. ______ is a program that facilitates the execution of other programs.A. An operating systemB. A queueC. An application programD. Hardware30. A process in the ready state goes to the running state when _________.A. it finishes runningB. it enters memoryC. it gets access to the CPUD. it requests I/OⅡ.Questions( 5 questions,4 scores for each question)1. What‘s the function of the ALU?/doc/6f3549947.html, the layers of the OSI model..3. What is the formal definition of an algorithm?4. What are the components of an operating system?5. What are the subsystems of the von Neumann computer model?Ⅲ.Calculation( 5 subjects, 6 scores for each subject)1. Change the following 8-bit two’s complement numbers to decimal.(1). 11111111 (2). 01100011 (3). 10000000 (4). 11001110 (5).11010000 (6)000100112.Change the following decimal numbers to 8-bit two’s complement integers.(1). 142 (2). -13 (3). -128 (4). 100 (5). -56 (6) -13. Using an 8-bit allocation, first convert each of the following numbers to two’s complement, do the operation, and then convert the result to decimal.(1) 18+22 (2) 18-22 (3) -18 +22 (4) -18-22 (5) 22-1 (6)-128-14. Show the result of the following operations in hexadecimal format.(1) NOT x55 (2) x AA AND x55 (3) x99 OR x66 (4) 100 AND 255(5) xFF XOR x33 (6) x40 OR (x8F AND xF7)5.Change the -7.125 decimal numbers to binary numbers, and show in 32-bit IEEE format, then changed to hexadecimal.Ⅳ. Analyzing and Design (4 subjects, 5 scores for each subject)1. An imaginary computer has eight data registers Rx(R0 toR7), 16M words in memory, the address can address words in the 16M words memory, and have 32 different instructions (ADD, SUB, etc.). A typical instruction of the computer uses the following format: SUB address, Rx(1) What is the minimum size of an instruction in bits?(2) If the instruction is in the minimum size and the computer uses the same size of word for data and instructions, what is the size of the data bus?(3) What is the size of the program counter?(4) What is the size of the address bus?(5) What is the minimum size of the control bus?2. Imaging a power plant that pumps water to a city using eight pumps. The states of the pumps (on oroff) can be represented by 8-bit pattern. For example, the pattern 10001111 shows that pumps 1 to 4(from right), and 8 are on(running) while pumps 5, 6, and 7 are off(shut down). How can you shut down all pumps, after a while, and then let the pump 5 ,7 running?3. Using the Insertion sort algorithm, manually sort the following list and show your work in each pass:12, 5, 23, 31, 40, 56, 78, 9, 2, 11, 984. A list contains the following elements. Using the binary search algorithm, trace the steps followed to find 58. At each step, show the values of first, last, and mid.5,12, 16, 26, 33, 51, 58, 80。

计算机科学导论试卷B卷答案一、单选题1.—5. ACCAC ;2. —10. CCAAA ;11.—15. CCBDB ;16. —20. ACDBC ;21.—25. C CCDD ;26. —30. BDBDB ;二、多选题1. 对2. 错3. 错4. 错5. 对6. 错7. 错8. 错9. 对10. 错三、判断题1. 表示、传播2. 采样、量化、编码3. 位图4. 系统软件、支撑软件、应用软件5. 局域网、城域网、广域网6. 总线型、环型、星型7. 用户名和邮件服务器主机名8. 设计视、过程视、实现视9. 网络层、应用层10 确定性、有穷性、可行性四、简答题1. 计算机病毒的基本特征是什么?答:计算机病毒是一小段程序或指令集合,它能进行自身拷贝或覆盖在其它较大的宿主程序上,并取得程序执行时的控制权。
当宿主程序执行时,病毒便被启动并继续其传染工作,当某些特定条件符合时,病毒便会发作,破坏数据和资料,危害计算机系统。
2. 什么是计算机网络?答:计算机网络是指把若干台地理位置不同,且具有独立功能的计算机,通过通信设备和线路相互联接起来,在网络操作系统、网络管理系统软件及网络通信协议的管理和协调下,实现信息传输和资源共享的一种计算机系统。
3. 什么是总线?常用的总线有哪几种?答:总线是计算机中连接多个部件和信息传输线,是各部件共享的传输介质。
在单CPU系统中,总线可分为三类:内部总线、系统总线和I/O总线。
4. 什么是计算机语言?计算机语言都有哪几类?答:计算机语言是指编写计算机程序所用的语言,是人与计算机之间交换信息的工具。
计算机语言可以分为:机器语言、汇编语言和高级语言三大类。
五、列出下列函数的真值表。
ABC+ABC (BC + BC)六、画出下列逻辑表达式对应的逻辑图。
F=AB+AB七、写出计算F=1+2+3+……+n的流程图。

2009级吉林大学计算机学院-计算机导论试题A卷2009-2010学年第1学期2009 级《计算机导论》考试试题A卷考试时间:2009年月班级学号姓名请将答案写在答题纸上,写明题号,不必抄题,字迹工整、清晰;请在答题纸和试题纸上都写上你的班级,学号和姓名,交卷时请将试题纸、答题纸和草纸一并交上来。
I、Choice Questions(20 questions, 1 score for each question)1. Every computer today is based on the _____ model.a. von Neumannb. Microsoftc. Inteld. input/output2. The CPU includes a small number of storage buffers that hold data temporarily, called ________.a. cacheb. registersc. memoryd. disk drives3. To store a byte, you need ______ electronic switches.a. 1b. 4c. 8d. 164. According to the von Neumann model, _________ are stored in memory.a. datab. programsc. algorithmd. a and b5. Computer scientists have defined three constructs for a structures program or algorithm, assertingthat a program must be made of a combination of them. Which of the following is NOT among them?a. Decisionb. Sequencec. Flowchartingd. Repetition6. The output data depend on the combination of the ________ and the program.a. memory sizeb. input datac. processor modeld. processor speed7. In ______ number representation, there are two representations for 0a. sign-and-magnitude .b. one’s complementc. two’s complementd. a and b8. The uniform representation for storing data is called ________.a. textb. a bit patternc. a switchd. ISO9. To unset (force to 0) all the bits of a bit pattern, make amask of all 0s and then ______the bitpattern and the mask.a. ORb. NOTc. XORd. AND10. A bit pattern of three bits can take on how many different states?a. sixteenb. eightc. fourd. three11. A program is a set of ________ written in a(n) ________ language.a. directions, humanb. mathematical operations, mathematicalc. codes, binaryd. instructions, computer12. A ______ bus connects the CPU and memory.a. controlb. addressc. datad. all of the above13. A router operates at ______ layer of the OSI model.a. all layersb. the first four layersc. the first three layersd. application14. The ______ scheduler creates a process from a job and changes a process back to a job.a. processb. queuec. jobd. virtual15. ______ is a protocol for mail services.a. FTPb. SMTPc. TELNETd. HTTP16. ______ is a memory type with capacitors that need to be refreshed periodically.a. SRAMb. DRAMc. ROMd. a tape drive17. When you try to store a number that is not within the range defined by the allocation, what happens?a. The system automatically allocates more space.b. The processor halts.c. Nothing; the processor just drops the extra bitsd. You get an overflow error.18. In a linked list, each element contains ______.a. a link and a recordb. data and a recordc. data and a linkd. all of the above19. A process in the running state goes to ready state when _______.a. get access to CPUb. Time slot exhaustedc. I/O requestedd. it finishes running20. The bit pattern 11000111 _________ to flip the leftmost bit.a. XOR 10000000b. OR 11111000c. NOTd. AND 11111000II、Questions( 5 questions, 5 scores for each question)1. What’s the definition of an operating system?2. What are the subsystems of the von Neumann computer model?3. Name four types of network connecting devices.4. Name the layers of the OSI model?5. What’s the f ormal definition of an algorithm?III、Calculation( 5 subjects, 5 scores for each subject)1. Change the following 8-bit two’s complement numbers to decimal.(1). 10000000 (2). 01100100 (3). 11001000 (4). 11000011 (5).110101012. Change the following decimal numbers to 8-bit two’s complement integers, and then convert the result to hexadecimal.(1). -48 (2). 25 (3). -127 (4). 98 (5). -553. Using an 8-bit allocation, first convert each of the following numbers to two’s complement, do the operation, and then convert the result to hexadecimal.(1) 35+63 (2) 35-63 (3) -35 +63 (4) -35-63 (5) 63-14. Show the result of the following operations, and then convert the result to hexadecimal.(1) NOT 129 (2) 15 AND 10 (3) x55 OR xAA (4) 100 AND 255(5) (xFF XOR xBB) AND (xFF OR xBB)5. Change the +12.625 decimal numbers to binary numbers, and show it in 32-bit IEEE format, and then convert the result to hexadecimal.IV. Analyzing and Design (5 subjects, 6 scores for each subject)1. Using the insertion sort algorithm, manually sort the following list and show your work in each pass:12, 6, 78, 31, 50, 46, 99, 2, 20, 442. A list contains the following elements. Using the binary search algorithm, trace the steps followed to find 66. At each step, show the values of first,last and mid.2, 5, 18, 28, 30, 40, 66, 1003 Write an algorithm in pseudocode to find the smallest of a set of 10000 numbers (the biggest data is 255 among the numbers).4. Write a recursive algorithm to find the combination of n objects taken k at a time using following definition.C(n,k)=1 , if k=0 or n=kC(n,k)=C(n-1,k)+C(n-1,k-1) , if n>k>05. Imaging a power plant that pumps water to a city using eight pumps(P8, P7, P6, P5, P4, P3, P2, and P1). The states of the pumps (on or off) can be represented by 8-bit pattern. For example, the pattern 10001111 shows that pumps 1 to 4(from right), and 8 are on (running) while pumps 5, 6, and 7 are off (shut down).How can you shut down all pumps, after two minutes, let the pump P2 and P5 running, and after one hour, shut down the P2 pump and turn on the P6 pump simultaneously, and remain the P5 running too?。

2009-2010学年第2学期考试试题(B)卷课程名称《计算机网络》任课教师签名出题教师签名审题教师签名考试方式(闭)卷适用专业计算机各专业考试时间(120 )分钟一、选择题(每题2分,共40分)1. 下面哪种网络设备工作在OSI模型的第二层?A.共享式集线器B.交换机C.路由器D.转发器2. 物理层上传输数据的单位是A. 数据包B. 分组C. 数据帧D. 比特3. B类地址180.16.10.28默认的子网掩码是A. 255.255.255.0B. 255.255.0.0C. 255.0.0.0D. 255.255.254.04. 下列IP地址中是C类地址。
A. 127.233.13.34B.152.87.209.51C.169.196.30.54D. 202.96.209.215. FTP的熟知端口是A. 21B. 23C. 80D. 256. 以太网中使用的协议标准是_____。
A. 802.3B. 802.5C. 802.7D. 802.117. 逆地址解析协议(RARP)用于_____。
A.把IP地址映射为MAC地址B.把MAC地址映射为IP地址C.域名映射为IP地址D.IP地址映射为域名8. 在星型结构中,常见的中央节点为。
A.路由器B.集线器C.网络适配器D.调制解调器9. IPv6的地址长度为______位。
A.48B.32C.128D.1610. 计算机网络中可以共享的资源包括。
A.硬件、软件、数据B.主机、外设、软件C.硬件、程序、数据D.主机、程序、数据11. 在多个数据字符组成的数据块之前以一个或多个同步字符SYN作为开始,帧尾用ETX作为结束,这种传输方案称为。
A.面向比特的同步传输B.起止式传输C.面向字符的同步传输D.异步传输12. 下面哪个是应用层协议?。
A. TCPB. IPC. SMTPD. HDLC13. 在TCP/IP协议簇中,TCP协议工作在A.应用层B.传输层C. IP层D.数据链路层14. 在计算机网络中,为了保证通信的正确进行,通信双方必须共同遵守的规则叫A.协议B.TCP/IPC.InternetD.以太网15. 计算机网络可分为三类,它们是A. Internet、Intranet、ExtraneB. 广播式网络、移动网络、点-点式网络C. X.25、ATM、B-ISDND. LAN、MAN、WAN16. 传递需进行调制编码。

计算机导论复习题一一、选择题(每小题2分,共20分)1、Internet最早出现在______国家,是指由其______部门开发的______网。
( )A. ①⑤⑨B. ②⑦⑧C. ③⑦⑨D. ③⑥⑨①. 英国②. 加拿大③. 美国④. 教育部⑤. 科技部⑥. 邮电部⑦. 国防部⑧.NSFNET⑨. ARPANET ⑩. Internet2、Internet在中国的发展,主要经历了两个阶段,第一阶段是____,第二阶段是____ 。
( )A. ①④B. ⑤②C. ⑥③D. ①②①. 1987年9月20日,钱天白教授发出我国第一封电子邮件“越过长城,通向世界”②. 与Internet网实现全功能的TCP/IP连接③. 1989年5月,中国研究网(CRN)通过当时邮电部的X.25试验网(CNPAC)实现了与德国研究网(DFN)的互连。
④. 1994年5月15日,中国科学院高能物理研究所设立了国内第一个WEB服务器,推出中国第一套网页⑤. 与Internet网E-mail的连通⑥. 1995年5月,中国电信开始筹建中国公用计算机互联网(CHINANET)全国骨干网。
3、全球的DNS根服务器数量为____个。
()A. 12B. 13C. 14D. 154、IP地址202.197.108.89属于哪一类网络____,它的子网掩码是____ 。
()A. B类,255.255.255.0B. B类,255.255.0.0C. C类,255.255.255.0D. C类,255.255.0.05、在IP地址A类的网络数、主机数()A. 27个网络,224台主机B. 28个网络,224台主机C. 214个网络,216台主机D. 216个网络,216台主机6、在IP地址分类中C类的IP地址表示范围____ 。
A. IP地址范围为:128.0.0.0—191.255.255.255B. IP地址范围为:0.0.0.0—63.255.255.255C. 保留地址范围为:240.0.0.0—255.255.255.255D. IP地址范围为:192.0.0.0—223.255.255.2557、专业术语SLIP的中文名称:____A. 传输控制协议B. 客户机/服务器C. 点对点协议D. 串行线互联协议8、专业术语PPP的中文名称:____A.传输控制协议 B. 点对点协议C. 超文本传输协议D.客户机/服务器9、UDP属于TCP模型结构中的( )层。

Chapter 1 Computer and DataKnowledge point:1.1The computer as a black box.1.2von Neumann model1.3The components of a computer: hardware, software, and data.1.4The history of computers.REVIEW QUESTIONS1.How is computer science defined in this book?A:Issues related to the computer.2.What model is the basis for today’s computers? ( Knowledge point 1.2)A:The von Neumann model.3.Why shouldn’t you call a computer a data processor? ( Knowledge point 1.1)A:Computer is general-purpose machine. it can do many different types of tasks.4.What does a programmable data processor require to produce output data? ( Knowledgepoint 1.1)A:The input data and the program.5.What are the subsystems of the von Neumann computer model? ( Knowledge point 1.2) A:Memory, arithmetic logic unit, control unit, and input/output.6.What is the function of the memory subsystem in von Neumann’s model? ( Knowledgepoint 1.2)A:Memory is the storage area. It is where programs and data are stored during processing.7.What is the function of the ALU subsystem in von Neumann’s model? ( Knowledge point1.2)A:ALU is where calculation and logical operations take place.8.What is the function of the control unit subsystem in von Neumann’s model? ( Knowledgepoint 1.2)A:It controls the operations of the memory, ALU, and the input/output subsystem.9.What is the function of the input/output subsystem in von Neumann’s model?( Knowledge point 1.2)A:The input subsystem accepts input data and the program from outside the computer; the output subsystem sends the result of processing to the outside.pare and contrast the memory contents of early computers with the memory contentsof a computer based on the von Neumann model? ( Knowledge point 1.2)A:Computer based on the von Neumann model stores both the program and its corresponding data in the memory. Early computers only stored the data in the memory.11.How did the von Neumann model change the concept of programming? ( Knowledgepoint 1.2)A:A program in the von Neumann model is made of a finite number of instructions. The instructions are executed one after another.12.The first electronic special-purpose computer was called c( Knowledge point1.4)a. Pascalb. Pascalinec. ABCd. EDV AC13.One of the first computers based on the von Neumann model was called d( Knowledge point 1.4)a. Pascalb. Pascalinec. ABCd. EDV AC14.The first computing machine to use the idea of storage and programming was calledd( Knowledge point 1.4)a. the Madelineb. EDV ACc. the Babbage machined. the Jacquard loom15.d separated the programming task from the computer operation tasks.( Knowledge point 1.3)a. Algorithmsb. Data processorsc. High-level programming languagesd.Operating systems30. According to the von Neumann model, can the hard disk of today be used as input or output? Explain. ( Knowledge point 1.2)A:Yes. When the hard disk stores data that results from processing, it is considered an output device; when you read data from the hard disk, it is considered an input device. 32. Which is more expensive today, hardware or software? ( Knowledge point 1.3)A:Software.Chapter 2 Data RepresentationKnowledge point:2.1 Data Types.2.2 Data inside the Computer.2.3 Representing Data.2.4 Hexadecimal and Octal notation.REVIEW QUESTIONS five types of data that a computer can process. ( Knowledge point2.1)A:Numbers, text, images, audio, and video.2.How does a computer deal with all the data types it must process? ( Knowledge point 2.2) A:All data types are transformed into bit pattern.3.4.What is the difference between ASCII and extended ASCII? ( Knowledge point 2.3)A:ASCII is a bit pattern made of 7 bits and extended ASCII is a bit pattern made of 8 bits.5.What is EBCDIC? ( Knowledge point 2.3)A:Extended Binary Coded Decimal Interchange Code.6.How is bit pattern length related to the number of symbols the bit pattern can represent?( Knowledge point 2.3)A:The relationship is logarithmic.7.8.9.What steps are needed to convert audio data to bit patterns? ( Knowledge point 2.3)A:Sampling, Quantization, and Coding.10.What is the relationship between image data and video data? ( Knowledge point 2.3)A:Video is a representation of images in time.34. A company has decided to assign a unique bit pattern to each employee. If the company has 900 employees, what is the minimum number of bits needed to create this system of representation? How many patterns are unassigned? If the company hires another 300employees, should it increase the number of bits? Explain your answer. ( Knowledge point 2.3)A:log2900≈10,210-900=124,Yes, 900+300>210Chapter 3 Number RepresentationKnowledge point:3.1 Convert a number from decimal, hexadecimal, and octal to binary notation and vice versa.3.2 Integer representation: unsigned, sign-and-magnitude, one’s complement, and two’s complement.3.3 Excess system.3.4 Floating-point representation.REVIEW QUESTIONS5. What are three methods to represent signed integers? (Knowledge point 3.2)A:Sign-and-Magnitude, One’s Complement, and Two’s Complement.9. Name two uses of unsigned integers. ( Knowledge point 3.2)A:Counting and Addressing.10. What happens when you try to store decimal 130 using sign-and-magnitude representation with an 8-bit allocation? ( Knowledge point 3.2)A:Overflow.11. Compare and contrast the representation of positive integers in sing-and-magnitude, one’s complement, and two’s complement. ( Knowledge point 3.2)A:The representation of positive integers in sing-and-magnitude, one’s complement, and two’s complement is the same.14. Compare and contrast the range of numbers that can be represented in sign-and-magnitude, one’s complement, and two’s complement. ( Knowledge point 3.2)A:Sign-and-Magnitude range –(2N-1-1)~+(2N-1-1)One’s Complement range –(2N-1-1)~+(2N-1-1)Two’s Complement range –(2N-1)~+(2N-1-1)16. What is the primary use of the Excess_X system? ( Knowledge point 3.3)A:The primary use of the Excess_X system is in storing the exponential value of a fraction.17. Why is normalization necessary? ( Knowledge point 3.4)A:A fraction is normalized so that operations are simpler.Chapter 4 Operation On BitsKnowledge point:4.1 Arithmetic operations.4.2 Logical operations.4.3 Mask.4.4 Shift operations.REVIEW QUESTIONS3. What happens to a carry form the leftmost column in the final addition? ( Knowledge point4.1)A:The carry is discarded.5. Define the term overflow. ( Knowledge point 4.1)A:Overflow is an error that occurs when you try to store a number that is not within the range defined by the allocation.8. Name the logical binary operations. ( Knowledge point 4.2)A:NOT, AND, OR, and XOR.10. What does the NOT operator do? ( Knowledge point 4.2)A:It inverts bits.(it changes 0 to 1 and 1 to 0)11. When is the result of an AND operator true? ( Knowledge point 4.2)A:Both bits are 1.12. When is the result of an OR operator true? ( Knowledge point 4.2)A:Neither bit is 0.13. When is the result of an XOR operator true? ( Knowledge point 4.2)A:The two bits are not equal.17. What binary operation can be used to set bits? What bit pattern should the mask have? ( Knowledge point 4.3)A:OR. Use 1 for the corresponding bit in the mask.18. What binary operation can be used to unset bits? What bit pattern should the mask have? ( Knowledge point 4.3)A:AND. Use 0 for the corresponding bit in the mask.19. What binary operation can be used to flip bits? What bit pattern should the mask have? ( Knowledge point 4.3)A:XOR. Use 1 for the corresponding bit in the mask.Chapter 5 Computer OrganizationKnowledge point:5.1. three subsystems that make up a computer5.2. functionality of each subsystem5.3. memory addressing and calculating the number of bytes5.4. addressing system for input/output devices.5.5. the systems used to connect different components together.Review questions:1. What are the three subsystems that make up a computer?(Knowledge point 5.1) Answer: the CPU, main memory, and the input/output (I/O) subsystem.2. What are the parts of a CPU? (Knowledge point 5.1)Answer: The CPU performs operations on data and has a ALU, a control unit, and a set of registers.3. What‘s the function of the ALU? (Knowledge point 5.2)Answer: The ALU performs arithmetic and logical operations.Exercises:78. A computer has 64MB of memory. Each word is 4 bytes. How many bits are needed toaddress each single word in memory? (Knowledge point 5.3)Solution:The memory address space is 64 MB, that is 2 raised to the power 26. The size of each word in bytes is 2 raised to the power 2. So we need 24(subtract 2 from 26) bits to address each single word in memory.79. How many bytes of memory are needed to store a full screen of data if the screen is made of 24 lines with 80 characters in each line? The system uses ASCII code, with each ASCII character store as a byte. (Knowledge point 5.3)Solution:The quantity of bytes in a full screen is 1920 (24*80) while the system uses ASCII code with each ASCII character store as a byte. So we need 1920 bytes of memory to store the full screen of data.87. A computer uses isolated I/O addressing. Memory has 1024 words. If each controller has 16 registers, how many controllers can be accessed by this computer? (Knowledge point 5.4) Solution:Memory has 1024 words. So the address space is 1024. Each controller has 16 registers. Then we get 64 (divide 16 by 1024)controllers which can be accessed by this computer.88. A computer uses memory-mapped I/O addressing. The address bus uses 10 lines. If memory is made of 1000 words, how many four-register controllers can be accessed by this computer? (Knowledge point 5.4)Solution:The address bus uses 10 lines. So, the address space is 1024(2 raised to the power 10). The memory is made of 1000 words and each controller has four registers. Then we get (1024-1000)/4 = 6 four-register controllers which can be accessed by this computer.Chapter 6 Computer NetworksKnowledge point:6.1. OSI model6.2. TCP/IP protocol6.3. three types of networks6.4. connecting devices6.5. client-server modelReview questions:2. Name the layers of the OSI model? (6.1)Answer: Physical layer, Data link layer, Network layer, Transport layer, Session layer, Presentation layer and Application layer.3. Name the layers of the TCP/IP protocol suite. (6.2)Answer: The layers of the TCP/IP protocol suite are: physical and data-link layers network layer, transport layer, and application layer.8. What are the three common topologies in LANs? Which is the most popular today? (6.3) Answer: bus topology, star topology, ring topology, star topology9. Name four types of network connecting devices. (6.4)Answer: the four types of network connecting devices are repeater, bridge, router and gateway.Chapter 7 Operating SystemsKnowledge point:7.1. the definition of an operating system7.2. the components of an operating system7.3. Memory Manager7.4. Process manager7.5. deadlockReview questions:4. What are the components of an operating system? (7.2)Answer: An operating system includes: Memory Manager, Process Manager, Device Manager and File Manager13. What kinds of states can a process be in? (7.4)Answer: ready state, running state, waiting state.15. If a process is in the running state, what states can it go to next? (7.4)Answer: ready state, waiting state.What’s the definition of an operating system? (7.1)Answer: An operating system is an interface between the hardware of a computer and user(programs or humans) that facilitates the execution of other programs and the access to hardware and software resources.What are the four necessary conditions for deadlock? (7.5)Answer: mutual exclusion, resource holding, no preemption and circular waiting.51. A multiprogramming operating system uses paging. The available memory is 60 MB divided into 15 pages, each of 4MB. The first program needs 13 MB. The second program needs 12MB. The third program needs 27 MB. How many pages are used by the first program? How many pages are used by the second program? How many pages are used by the third program? How many pages are unused? What is the total memory wasted? What percentage of memory is wasted? (7.3)Answer:Each page is 4MB. The first program needs 13 MB. It is obviously that 4*3<13<4*4. So the first program uses 4 pages and wastes 3(16-3) MB. The second program needs 12 MB. It is obviously that 12=4*3. So the second program uses 3 pages and wastes 0 MB. The third program needs 27 MB. It is obviously that 4*6<27<4*7. So the first program uses 7 pages and wastes 1(28-27) MB. There are 1(15-4-3-7) page unused. There are totally 4(3+0+1) MB memory wasted. The percent of memory wasted is 4/(60-4*1)=7%.Chapter 8 AlgorithmsKnowledge point:8.1. the concepts of an algorithm and a subalgorithm8.2. three constructs for developing algorithms8.3. basic algorithms8.4. tools for algorithm representation8.5. recursionReview questions:1. What is the formal definition of an algorithm? (8.1)Answer: An ordered set of unambiguous steps that produces a result and terminates in a finite time.2. Define the three constructs used in structured programming. (8.2)Answer: The three constructs in structured programming are Sequence, Decision and Repetition.10. What are the three types of sorting algorithms? (8.3)Answer: bubble sort, selection sort and insertion sort.12 What is the purpose of a searching algorithm? (8.3)Answer: The purpose is to find the location of a target among a list of objects.13. What are the two major types of searches? How are they different? (8.3)Answer: sequential search and binary search. The difference is whether the list is ordered or not.55. A list contains the following elements. Using the binary search algorithm, trace the steps followed to find 20. At each step, show the values of first, last and mid.3, 7, 20, 29, 35, 50, 88, 200 (8.3)Solution:index 0---1---2---3---4---5---6---73, 7, 20, 29, 35, 50, 88, 200First=0, Last=7, Mid=(0+7)/2=3The data is D(3)=29, 20 smaller than the D(3), so remove the data from index 3 to 7. Change the new point First=0, Last= mid-1=2, and Mid=(0+2)/2=1The data is D(1)=7, 20 bigger than the D(1), so remove the data from index 0 to 1. Change the new point First=mid+1=2, Last=2, and Mid=(2+2)/2=2The data is D(2)=20, we find the data 20 in index=258. Write a recursive algorithm to find the combination of n objects taken k at a time using following definition.C(n,k)=1 , if k=0 or n=kC(n,k)=C(n-1,k)+(n-1,k-1) , if n>k>0 (8.5)Solution:A: CInput : n and kIf(k==0 or n==k)Then return 1End ifIf(n>k and k>0)Then Return C(n-1,k)+(n-1,k-1)End ifEnd。

2009年计算机统考考研试题及参考答案2009年计算机统考考研试题及参考答案12009年计算机统考考研试题12009年计算机统考试题参考答案92009年计算机统考考研试题及参考答案2009年计算机统考考研试题一.单项选择题,每小题2分,共80分。
1.为解决计算机与打印机之间速度不匹配的问题,通常设置一个打印数据缓冲区,主机将要输出的数据依次写入该缓冲区,而打印机则依次从该缓冲区中取出数据。
该缓冲区的逻辑结构应该是A.栈B.队列C.树D.图2.设栈S和队列Q的初始状态均为空,元素abcdefg依次进入栈S。
若每个元素出栈后立即进入队列Q,且7个元素出队的顺序是bdcfeag,则栈S的容量至少是A.1 B.2 C.3 D.43.给定二叉树图所示。
设N代表二叉树的根,L代表根结点的左子树,R代表根结点的右子树。
若遍历后的结点序列为3,1,7,5,6,2,4,则其遍历方式是A.LRN B.NRL C.RLN D.RNL4.下列二叉排序树中,满足平衡二叉树定义的是A. B. C. D.5.已知一棵完全二叉树的第6层(设根为第1层)有8个叶结点,则完全二叉树的结点个数最多是A.39 B.52 C.111 D.1196.将森林转换为对应的二叉树,若在二叉树中,结点u是结点v的父结点的父结点,则在原来的森林中,u和v可能具有的关系是I.父子关系 II.兄弟关系 III. u的父结点与v的父结点是兄弟关系A.只有IIB.I和IIC.I和IIID.I、II和III7.下列关于无向连通图特性的叙述中,正确的是I.所有顶点的度之和为偶数 II.边数大于顶点个数减1III.至少有一个顶点的度为1A.只有IB. 只有IIC.I和IID.I和III8.下列叙述中,不符合m阶B树定义要求的是A.根节点最多有m棵子树 B.所有叶结点都在同一层上C.各结点内关键字均升序或降序排列 D.叶结点之间通过指针链接9.已知关键序列5,8,12,19,28,20,15,22是小根堆(最小堆),插入关键字3,调整后得到的小根堆是A.3,5,12,8,28,20,15,22,19B. 3,5,12,19,20,15,22,8,28C.3,8,12,5,20,15,22,28,19D. 3,12,5,8,28,20,15,22,1910.若数据元素序列11,12,13,7,8,9,23,4,5是采用下列排序方法之一得到的第二趟排序后的结果,则该排序算法只能是A.起泡排序 B.插入排序 C.选择排序 D.二路归并排序11.冯·诺依曼计算机中指令和数据均以二进制形式存放在存储器中,CPU区分它们的依据是A.指令操作码的译码结果 B.指令和数据的寻址方式C.指令周期的不同阶段D.指令和数据所在的存储单元12.一个C语言程序在一台32位机器上运行。
2009-2010学年第1学期2009 级《计算机导论》考试试题A卷考试时间:2009年12月日班级学号姓名✧请将答案写在答题纸上,写明题号,不必抄题,字迹工整、清晰;✧请在答题纸和试题纸上都写上你的班级,学号和姓名,交卷时请将试题纸、答题纸和草纸一并交上来。
一、Choice Questions(20 questions, 1 score for each question)1. In the von Neumann model, the _______subsystem accepts data and programs and sends processing results to output devices.a. ALUb. Input/outputc. memoryd. control unit2. FORTRAN and COBOL are examples of ________.a. hardwareb. an operating systemsc. computer languagesd. algorithms3. The first computing machine to use the idea of storage and programming was called_______.a. the Madelineb. EDV ACc. the Babbage machined. the Jacquard loom4. A 32-bit code was developed by ______ to represent symbols in all languages.a. ANSIb. ISOc. EBCDICd. Hamming5. The bitmap graphic method and the vector graphic method are used to represent ______in a computer.a. audiob. videoc. imagesd. numbers6. When converting a decimal number to binary, you repeatedly divide by _______.a. 2b. 8c. 10d. 167. In ______ number representation, 1111 in memory represents –0.a. unsigned integersb. sign-and-magnitudec. one’s complementd. two’s complement8. Which number representation method is often used to convert analog signals to digital signals?a. unsigned integersb. sign-and magnitudec. one’s complementd. two’s complement9. For an 8-bit allocation, the smallest decimal number that can be represented in two’s complement form is _____.a. -8b. -127c. -128d. -25610. You use a bit pattern called a ________ to modify another bit pattern.a. maskb. carryc. floatd. byte11. ______ is a memory type with capacitors that need to be refreshed periodically.a. SRAMb. DRAMc. ROMd. a tape drive12. The _____ memory contains a copy of a portion of main memory.a. CPUb. cachec. maind. ROM13. The _____ controller is a high-speed serial interface that transfers data in packets.a. SCSIb. FireWirec. USBd. IDE14. The ______ layer of the OSI model is responsible for source-to-destination delivery of the entire message.a. transportb. networkc. data-linkd. session15. A ______ is a connecting device that only regenerates the signal.a. repeaterb. bridgec. routerd. gateway16. ______ is a protocol for mail services.a. FTPb. SMTPc. TELNETd. HTTP17. In paging, memory is divided into equally sized sections called _______.a. pagesb. framesc. segmentsd. partitions18. To prevent ______, an operating system can put resource restrictions on processes.a. starvationb. synchronizationc. pagingd. deadlock19. _______ is english like representation of the code.a. A flowchartb. A structure chartc. Pseudocoded. an algorithm20. A process in the ready state goes to the running state when _________.a. it enters memoryb. it gets access to the CPUc. it requests I/Od. it finishes running二、Questions(6 questions, 5 scores for each question)1. What is the formal definition of an algorithm?2. What kinds of states can a process be in?3. What are the three common topologies in LANs? Which is the most popular today?4. What is a bit pattern?5. What are the two major types of searches?6. Name the layers of the TCP/IP protocol suite.三、Calculation(5 subjects, 4 scores for each subject)1. Change the following 8-bit two’s complement numbers to decimal.(1). 10000000 (2). 01100100 (3). 11001000 (4). 11000011 (5).110101012. Change the following decimal numbers to 8-bit two’s complement integers, and then convert the result to hexadecimal.(1). -48 (2). 25 (3). -127 (4). 98 (5). -553. Using an 8-bit allocation, first convert each of the following numbers to two’s complement, do the operation, and then convert the result to hexadecimal.(1) 35+63 (2) 35-63 (3) -35 +63 (4) -35-63 (5) 63-14. Show the result of the following operations, and then convert the result to hexadecimal.(1) NOT 129 (2) 15 AND 10 (3) x55 OR xAA (4) 100 AND 255(5) (xFF XOR xBB) AND (xFF OR xBB)5. A computer has 64MB (megabytes) of memory. Each word is 4 bytes. How many bits are needed to address each single word in memory?四. Analyzing and Design (2 subjects, 10 scores for each subject)1. Using the selection sort algorithm, manually sort the following list and show your work in each pass:12, 6, 78, 31, 50, 46, 99, 2, 20, 442. A list contains the following elements. Using the binary search algorithm, trace the steps followed to find 18. At each step, show the values of first,last and mid.2, 5, 18, 28, 30, 40, 66, 1003. Write a recursive algorithm to find the greatest common divisor(gcd) of two integers using following definition.gcd(x, y)= gcd(y, x) , if x<ygcd(x, y)= x , if y=0gcd(x, y)= gcd(y, x mod y) , otherwise4. Imaging a power plant that pumps water to a city using eight pumps(P8, P7, P6, P5, P4, P3, P2, and P1). The states of the pumps (on or off) can be represented by 8-bit pattern. For example, the pattern 10001111 shows that pumps 1 to 4(from right), and 8 are on (running) while pumps 5, 6, and 7 are off (shut down). How can you shut down all pumps, after two minutes, let the pump P2 and P5 running, and after one hour, shut down the P2 pump and turn on the P6 pump simultaneously, and remain the P5 running too?5. An imaginary computer has sixteen data registers Rx(R0 to R15), 512M words in memory, the address can address words in the 64M words memory, and have 128 different instructions (ADD, SUB, etc.). A typical instruction of the computer uses the following format: ADD address, Rx(1) What is the minimum size of an instruction in bits?(2) If the instruction is in the minimum size and the computer uses the same size of word for data and instructions, what is the size of the data bus?(3) What is the size of the program counter?(4) What is the size of the address bus?(5) What is the minimum size of the control bus?。