On the multiplicity of terminal singularities on threefolds
- 格式:pdf
- 大小:95.43 KB
- 文档页数:8
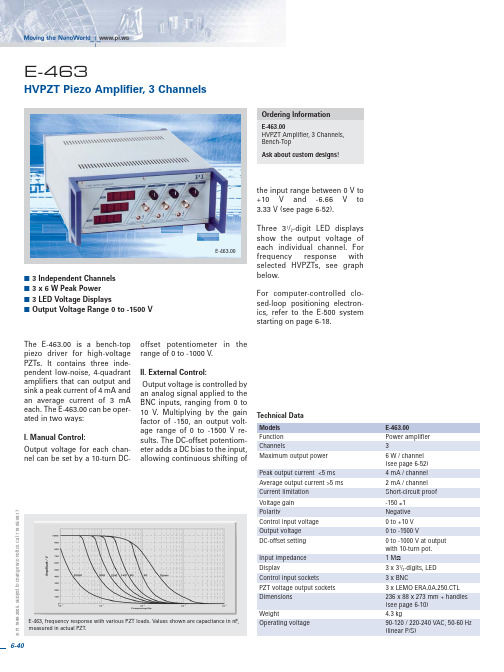
HVPZT Piezo Amplifier, 3 ChannelsE-4633 Independent Channels 3 x 6 W Peak Power 3 LED Voltage DisplaysOutput Voltage Range 0 to -1500 VE-463.00E-463, frequency response with various PZT loads. Values shown are capacitance in nF , measured in actual PZT.the input range between 0 V to +10 V and -6.66 V to 3.33 V (see page 6-52). Three 31/2-digit LED displays show the output voltage of each individual channel. For frequency response with selected HVPZTs, see graph below.For computer-controlled clo-sed-loop positioning electron-ics, refer to the E-500 system starting on page 6-18.Technical DataModels E-463.00Function Power amplifier Channels3Maximum output power 6 W / channel (see page 6-52)Peak output current <5 ms 4 mA / channel Average output current >5 ms 2 mA / channel Current limitation Short-circuit proof Voltage gain-150 ±1PolarityNegative Control input voltage 0 to +10 V Output voltage 0 to -1500 VDC-offset setting 0 to -1000 V at output with 10-turn pot.Input impedance 1 M ΩDisplay3 x 31/2-digits, LED Control input sockets 3 x BNCPZT voltage output sockets 3 x LEMO ERA.0A.250.CTL Dimensions 236 x 88 x 273 mm + handles (see page 6-10) Weight4.3 kgOperating voltage90-120 / 220-240 VAC, 50-60 Hz (linear P/S)The E-463.00 is a bench-top piezo driver for high-voltage PZTs. It contains three inde-pendent low-noise, 4-quadrant amplifiers that can output and sink a peak current of 4 mA and an average current of 3 mA each. The E-463.00 can be oper-ated in two ways:I. Manual Control:Output voltage for each chan-nel can be set by a 10-turn DC-offset potentiometer in the range of 0 to -1000 V.II. External Control:Output voltage is controlled by an analog signal applied to the BN C inputs, ranging from 0 to 10 V. Multiplying by the gain factor of -150, an output volt-age range of 0 to -1500 V re-sults. The DC-offset potentiom-eter adds a DC bias to the input,allowing continuous shifting of6-40© P I 1998-2005. S u b j e c t t o c h a n g e w /o n o t i c e . C a t 118 05/09.17。


IGMP协议概述The Internet Group Management Protocol(IGMP)is a network‑layer protocol used by hosts and ad‑jacent routers on an Internet Protocol(IP)network to report their multicast group memberships.It is an essential component of IP multicast,which enables efficient delivery of data to multiple hosts simultaneously.BackgroundIn traditional IP networks,data packets are typically sent to a unicast address,which means they are delivered to a specific destination host.However,in scenarios where data needs to be sent to multiple recipients simultaneously,such as multimedia streaming or real‑time collaboration applications,the unicast approach becomes inefficient and resource‑consuming.This is where multicast comes into play.What is Multicast?Multicast is a communication method that allows a single sender to transmit data packets to a group of receivers.Instead of sending separate copies of the data to each receiver,the sender multicasts the data once,and it is then replicated and delivered only to the members of the multicast group who have expressed interest in receiving the data.Role of IGMPIGMP plays a crucial role in enabling hosts to join and leave multicast groups dynamically.It allows routers to learn which hosts are interested in receiving multicast traffic for specific groups and effi‑ciently forward the data only to those interested hosts.How IGMP Works1.Host Joins a Multicast Group:When a host wants to receive multicast traffic for a specific group,it sends an IGMP join message to its local router,indicating its interest in joining the group. 2.Router Membership Query:Routers periodically send IGMP membership queries on the networkto discover which hosts belong to multicast groups.These queries elicit IGMP membership re‑ports from the hosts.3.Host Membership Reports:Upon receiving a query,hosts respond with IGMP membership re‑ports,indicating the multicast groups they are interested in.4.Router Forwarding:Routers maintain a list of active multicast groups and their associated hosts.They use this information to forward multicast traffic only to the hosts that have joined the re‑spective groups.Benefits and ApplicationsIGMP enables efficient distribution of multicast traffic,reducing network congestion and bandwidth consumption.It finds applications in various scenarios,including:•Video streaming and IPTV•Online gaming and interactive applications•Software‑defined networking(SDN)•Content delivery networks(CDNs)•Collaborative tools and virtual classroomsSecurity and LimitationsWhile IGMP facilitates multicast communication,it’s important to consider security aspects and im‑plement appropriate measures to prevent unauthorized access or malicious activities.Additionally, IGMP has some limitations,such as scalability challenges in large networks and potential issues with router performance under heavy multicast traffic.In conclusion,IGMP is a critical protocol for managing multicast group memberships in IP networks. By allowing hosts to join and leave multicast groups dynamically,IGMP enables efficient and scalable delivery of multicast traffic,catering to various applications and improving network performance. IGMP协议的工作原理IGMP(Internet Group Management Protocol)是一种网络层协议,用于在Internet协议(IP)网络上的主机和相邻路由器之间报告它们的组播组成员关系。

组合逻辑电路英语Combinational logic circuits are electronic circuits that perform logical operations on input signals to generate output signals. Combinational logic circuits are primarily composed of digital logic gates such as NAND gates, AND gates, NOT gates, XOR gates, and OR gates. These circuits do not have any memory as they only perform operations based on the current inputs. The output of a combinational logic circuit is determined by the combination of inputs applied to the circuit.A combinational logic circuit is composed of basic building blocks such as logic gates and interconnecting wires. These building blocks are combined in different configurations to form more complex circuits that perform more advanced functions. The basic logic gates are designed to perform simple Boolean operations such as AND, OR, NOT, and XOR.AND gates are often used in combinational logic circuits to implement logical operations that require the simultaneous satisfaction of multiple conditions. For example, an AND gate can be used to generate an output signal when two or more input signals are high at the same time. The output signal from an AND gate is high only if all its input signals are high.OR gates are used to perform logical operations that require at least one of the input signals to be high. The output of an OR gate is high if any of its input signals is high.NOT gates are used to invert the input signal. The output of a NOT gate is the complement of its input signal. If the input signal is high,the output of the NOT gate will be low, and vice versa.XOR gates are used to generate an output signal when the inputs are unequal. The output of an XOR gate is high if the input signals are different.Combinational logic circuits are used in a wide variety of applications such as data processing, digital signal processing, and control systems. These circuits are designed to perform specific functions and are often combined with other circuits to form more complex systems. The design of combinational circuits requires a good understanding of digital logic and Boolean algebra, as well as the ability to analyze and design circuits using simulation and modeling tools.In conclusion, combinational logic circuits are an important part of digital electronics. These circuits are simple, easy to design, and implement logical operations without the use of memory. Their applications are widespread, from calculators to spacecraft. The basic building blocks of combinational logic circuits are logic gates, and they are combined in different configurations to form more complex circuits. The design of these circuits requires knowledge of Boolean algebra and the ability to analyze and design circuits using simulation tools.。

SUGGESTED SPECIFICATIONS SINGLE DUCT AIR TERMINAL UNITSSECTION 1. GENERAL1.1Basic Unit. Furnish and install METALAIRE Single Duct Air Terminal Units. The units shall be the sizeand capacity as outlined in the plans and specifications. Casing dimensions shall be checked to ensure the terminals fit the available space.1.2Quality, Agency, Standards. Air terminals shall be certified under the Air Conditioning, Heating andRefrigeration Institute (AHRI) Standard 880-08 Certification Program and carry the AHRI seal. All NCvalues shall be calculated per AHRI Standard 885-08. Units with NC values calculated per AHRI-885-90 or 98 will not be accepted. Terminal units shall be either ETL® or UL® listed as a complete assembly.Terminal electrical components, including actuators and low voltage controls shall be UL® listed. Allelectrical components including both line voltage and low voltage shall be mounted in a metal control enclosure. Units shall have a single point field wiring connection. Units shall be manufactured and wired per UL-1995 and in accordance with the National Electric Code.1.3Shipping. All terminals shall be shipped as a single unit requiring no field assembly. Accessoriesincluding hot water coils and electric heaters shall be factory mounted.SECTION 2. CONSTRUCTION2.1General. Single Duct Terminal Units shall be METALAIRE Air Terminal Units. The units shall be the sizeand capacity as outlined in the plans and specifications. Casing dimensions shall be checked to ensure the terminals fit the available space.2.2Casing. The air terminals shall be constructed of galvanized steel. The casing shall be a minimum of22-gauge. The terminal primary air inlet valve shall have a round (oval or rectangular for larger sizes) inlet for field duct connection. The terminal unit discharge shall allow for a slip and drive ductconnection. Units shall have a universal control-mounting panel constructed of minimum 22-gaugesteel. Control panel shall include stand-offs to allow controls to be mounted without penetrating theterminal casing. Control panels without stand-offs are not acceptable.2.2.1Optional Sliding Door Control Panel Cover. Provide a sliding control panel cover that slidestowards the primary inlet and prevents the cover from being removed.SECTION 3. PRIMARY INLET AIR VALVE3.1Inlet Tube. Primary inlet air valve assembly shall have a seamless butt weld on round inlet tube tominimize leakage and prevent the damper from binding on overlapping seam welds. Inlet tubeswith overlapping welds or non- continuous, skipped welds are not acceptable. Inlet air valve shall have three structural beads machine formed into the tube. One external bead shall be provided for the attach- ment of flexible duct. Inlet air valves without three structural beads are not acceptable.3.2Flow Sensor. Primary inlet air valve flow sensor shall be multi-quadrant averaging sensor with flowsampling of both velocity pressure and flow differential pressure from four quadrants, and shallcontain two control ports and two accessory ports. Flow sensors sampling only velocity pressure in all four quadrants are not acceptable. Sensors reading differential pressure with fewer than 8 measuring points are not acceptable. All piping connections to the flow sensor must be made with external ports that extend through damper tube. Units with piping connections made in the primary air stream are not acceptable. Flow sensors with plastic piping connections of any kind are not acceptable. At an inlet velocity of 2000 fpm, the differential static pressure required to operate any terminal size shall not exceed 0.14” wg. for the basic terminal.3.2.1Damper Assembly. Air terminals with inlet flow sensing devices shall be provided with agasketed access door to permit removal, inspection and cleaning of the air flow sensor.3.3Damper Assembly. Damper shaft shall rotate in a self-lubricating, long life, low friction thermo-plastic bearing. Damper shaft construction shall be one piece, continuous extruded aluminum.Damper shaft end shall include a permanent cast damper position indicator. Damper tube shall be free of obstructions including damper stops to allow the free rotation of the damper. Mechanicaldamper stops located in the inlet tube are not acceptable. A flexible gasket-mounted damper blade without adhesives shall provide damper seal. Damper gasket shall include slit partitioning around the perimeter to prevent damper noise at low flows near full close off. Damper gaskets withoutperimeter slit partitioning are not acceptable. Mechanically fastened damper assembly shall be double layer, 18 gauge equivalent, galvanized steel with integral blade seal. Leakage through the damper assembly shall be less than 1% of maximum CFM at 3” static pressure.SECTION 4. INSULATION4.1Standard Fiberglass Insulation. Air Terminals shall be internally insulated with (½”or 1”) thick,1.5 lb. /ft3, dual density fiberglass. Insulation and edges shall be coated to prevent air erosion to6000FPM surface velocity. Insulation shall comply with UL 181 and NFPA 90A.4.2Optional Foil-Faced Fiberglass Insulation. Air Terminals shall be internally insulated with (½”, ¾”,1”) thick, 1.5 lb. /ft3 dual density or 1” 4 lb. /ft3 dual density, fiberglass covered with scrim backed foil facing. All surfaces and edges of the insulation shall be sealed with scrim backed foil facing so that there is no exposed fiberglass in the airstream. Insulation shall comply with UL 181 andNFPA 90A.4.3Optional Closed-Cell Foam Insulation. Air Terminals shall be internally insulated with (½”, 1”) thick,1.5lb. /ft3 density, closed-cell foam insulation and shall be Thermopure for fiber free application.Exposed fiberglass is not acceptable. Insulation shall comply with UL 181 and NFPA 255 (25/50).Material shall be chemically resistant to most hydrocarbon based solvents. Material shall not support mold growth or demonstrated degradation while subject to air erosion when tested in accordance to UL 181 and UMC 10.1.2.4.4Optional Solid Double - Wall/Metal Lined Insulation. Air Terminals shall be internally insulated andthoroughly sealed with solid metal/double walled liner to completely isolate the internal (½”, 1”) fiber glass insulation from the airstream. The insulation shall provide a virtually non-destructible, non- porous duct surface and shall inhibit bacteria growth. Internal insulation shall comply with UL 181 and NFPA 90A.SECTION 5. HOT WATER COIL5.1Construction. Hot Water Coils are to be factory mounted to the discharge outlet of the terminal. Thenumber of rows and circuits shall meet the capacities as shown in the schedule. Hot water coils shall be enclosed in a minimum 20-gauge coated steel casing allowing attachment to metal ductwork witha slip and drive connection. Fins shall be rippled and sine wave type, constructed from heavy gaugealuminum, and mechanically bonded to the tubes. Tubes shall be copper with a minimum wallthickness is 0.016” with male sweat header connections.5.2Performance. Coils shall be leak tested to 300 psi with minimum burst of 2000 psi at ambienttemperature. Coil performance data shall be rated and presented in accordance with AHRI standard 410. Coils must be ARI rated, certified and include an AHRI label. Coils that are not AHRI rated,certified or labeled AHRI are not acceptable.SECTION 6. ELECTRIC HEAT6.1Construction. Electric Reheat Coils are to be factory mounted on the discharge of the Air Terminalwith the sizes, kilowatts, steps, operating voltage, control voltage, and accessories as outlined in the plans and specifications. Heater casings shall be constructed of galvanized steel. Elementwire shall be high grade nichrome alloy rated to 45 watts per square inch density. Element wire shall be supported by moisture resistant steatite ceramics. Ceramics to be enclosed in reinforcementbrackets spaced across the heater element rack at 2” to 4” intervals. Controls shall be contained in NEMA 1 control cabinet with a hinged, latching door. A permanent wiring diagram shall be affixed to the inside of the control cabinet door for field reference. The heating element rack shall be recessed 1” into the duct to assure adequate air temperature readings for proper operation of safety switches.Each Electric Duct Heater shall be shipped with an ETL ® label certifying that it meets or exceeds the safety requirements of Standard 1996. Each heater will have an automatic primary high temperature limit switch, a manual reset high temperature limit switch, air static or fan relay type air proving switch and fusing if the heater exceeds 48 amps as required by UL®. A terminal block for line and control voltage shall be provided for simplified field wiring. A P. E. switch or contractor per step shall be provided for each stage of heat.6.2Performance. The heaters shall be ETL® listed for zero clearance, tested in accordance with UL®Standard 1995, CSA-C22.2 No. 236 and in accordance with the National Electric Code (NEC).SECTION 7. ACCESS PANELS AND MOUNTING7.1Access Panels. An optional separate bottom primary inlet access panel is available.7.2Mounting. Terminal shall include 3” wide bottom-mounting surfaces on opposite ends designedto accept bottom-mounting hardware including trapeze type. Bottom-mounting surfaces shall allow mounting hardware to be installed without interfering with access or removal of the bottomaccess panels.7.2.1Optional Mounting. Field mounted hanger brackets designed to accept threaded rods up to5/16” in. diameter are acceptable.SECTION 8. SOUND8.1Sound Ratings. The terminal manufacturer shall provide AHRI certified sound power data for radiatedand discharge sound. All NC values shall be calculated per AHRI standard 885-98. Verify soundratings for the terminal do not exceed specified value at scheduled static pressure. Sound performance shall be AHRI certified. Each individual terminal unit shall bear an AHRI label.8.2Attenuators. Sound attenuator shall be provided where scheduled to meet acoustical performancerequirements. The attenuator and terminal unit shall be single piece construction. Attenuatorinsulation shall be the same as the unit casing insulation.SECTION 9. CONTROLS9.1Digital Controls. Factory mounting and wiring of DDC controls shall be as specified in the schedule.Mounting shall include manufacturer’s flow sensor, transformer (if required by DDC controls manufac- turer), and an enclosure protecting DDC controls and wiring.9.2Analog Controls. Analog electronic controls with flow adjustments shall be as specified in theschedule and be provided by the terminal unit manufacturer.9.3Pneumatic Controls. Pneumatic controls shall be as specified in the schedule. Manufacturer shallprovide terminal units with factory set flow adjustments as required per the Terminal Unit schedule.。

METHOD211ASTRENGTHTERMINAL1. PURPOSE. This test is performed to determine whether the design of the terminals and their method ofattachment can withstand one or more of the applicable mechanical stresses to which they will be subjected duringinstallation or disassembly in equipment. These stresses must be withstood by the component part withoutsustaining damage which would affect either the utility of the terminals or the operation of the component part itself.Evidence of damage caused by this test may not become evident until subsequent environmental tests areperformed, such as seal, moisture resistance, or life. Procedures are established in this method for testing wire-leadterminals, flexible-flat-strip or tab-lead terminals, and rigid-type terminals which are threaded or have otherarrangements for attaching conductors. The forces applied consist of direct axial, radial or tension pulls, twist,bending torsion, and the torque exerted by the application of nuts or screws on threaded terminals. These appliedstresses will disclose poor workmanship, faulty designs, and inadequate methods of attaching terminals to the bodyof the part. Other evidence of damage may be disclosed by mechanical distortion of the part, breaking of seals,cracking of materials surrounding the terminals, or changes in electrical characteristics, such as shorted orinterrupted circuits and changes in resistance values.2. TEST CONDITIONS.2.1 Selection. In this method there are five test conditions, A, B, C, D, and E. The selection of test conditions toperform the terminal-strength test depends on the type of terminal to be tested. The individual specification shallspecify the test condition required. The following is included as a guide to be used, as applicable:Test condition A: Pull test - also known as a tension or tensile test for terminals. It is usually applicable tomost types of terminals.Test condition B: Flat-terminal bend test - also known as a bend test. It is applicable to flexible-flat-strip ortab-lead terminals which can be bent by finger pressure.Test condition C: Wire-lead bend test - also known as a lead-fatigue, bend, or flexibility test. It is applicable tosolid-wire-lead terminals of limited ductility, such as nickel-alloy-type leads and those usedin hermetically-sealed component parts.Test condition D: Twist test - also known as a torsion test. It is usually applicable to ductile, solid-wire-leadterminals intended for wraparound connections.Test condition E: Torque test - It is applicable to rigid-type terminals having either external screw threads orthreaded inserts which are located at the center of the terminal, or to other non-wire, rigid-type terminals which should withstand the turning moment that results from a force appliedfrom an off-center point on the terminal.3. PROCEDURE. One or more of the following test condition letters shall be specified in the individualspecification:3.1 Test condition A (pull test).3.1.1 Method of holding. If the method of holding or clamping is pertinent, it shall be specified in the individualspecification.3.1.2 Applied force. The force applied to the terminal shall be 1/2, 1, 2, 3, 5, 10, or 20 pounds, as specified in theindividual specification.3.1.3 Direction of applied force. The point of application of the force and the force applied shall be in the directionof the axes of the terminations, as shown on figure 211-1.211AMETHOD14 April 19691 of 73.1.4 Duration of applied force. The force shall be applied gradually to the terminal and then maintained for a period of 5 to 10 seconds.3.2 Test condition B (flat-terminal bend test).3.2.1 Starting position of terminal. Prior to the test, the terminal shall be observed to determine if it is oriented in its normal or unbent position, or if it is permanently bent out of position, as could occur as a result of prior testing.3.2.2 Bending cycle. If the method of bending is not critical, the terminals may be bent by finger pressure througha bending cycle of three bends, as shown on figure 211-2. The bending cycle shall start with a 45° bend to one side of the normal position. If the terminal is already bent to an angle between 0° and 45° to one side of the normal position prior to test, it shall be bent in the same direction until an angle of 45° is achieved. The terminal shall then be bent 90° in the opposite direction to a point 45° on the opposite side of the normal position, and then back 45° to normal. If the method of bending is critical, the individual specification shall specify the method of bending and any fixture required to control the point of application. The rate of bending shall be approximately 3 seconds per bend in each direction.3.2.3 Number of bending operations. The number of bending operations shall be two or five, as specified in the individual specification.3.3 Test condition C (wire-lead bend test).3.3.1 Preparation of specimen. A load of 1/4, 1/2, 1, 5, or 10 pounds, as specified in the individual specification, shall be suspended from the terminal. The load selected shall be that closest in value to one-half the load applied during the pull test. The body of the component part shall be held with a suitable clamping or attaching device, so that the terminal is in its normal position with respect to the component part. The load shall be suspended at a point within 1/4 inch from the free end of the terminal.3.3.2 Bending cycle. The body of the component part shall be slowly inclined so as to bend the terminal through 90° and then return it to normal position, as shown on figure 211-3. This entire action shall be limited to one vertical plane. A bend through 90° and return to normal position shall be defined as one bend. Consecutive bends shall be in the same direction. The load shall be restricted such that the bend starts 3/32 ±1/32 inch from the body of the component part. The rate of bending shall be approximately 3 seconds per bend in each direction.3.3.3 Number of bending operations. The number of bending operations shall be three.3.4 Test condition D (twist test).3.4.1 Preparation of specimen. The solid-wire-lead terminal shall be bent 90° at a point 1/4 inch from its juncture with the body of the component part, as shown on figure 211-4. The radius of curvature of the 90° bend shall be approximately 1/32 inch. The free end of the terminal shall be clamped at a point 3/64 ±1/64 inch away from the bend, as shown on figure 211-4.3.4.2 Application of torsion. The body of the component part or the clamped terminal shall be rotated through 360° about the original axis of the bent terminal, in alternating directions, for a total of three rotations 1080°, at the rate of approximately 5 seconds per rotation.METHOD 211A14 April 196923.5 Test condition E (torque test).3.5.1 Direction and application of torque. The torque shall be applied clockwise and then counterclockwise in aplane perpendicular to the axis of the terminal, as shown on figure 211-5.3.5.2 Duration of applied force. The force shall be applied gradually to the terminal and then maintained for aperiod of 5 to 15 seconds.3.5.3 Screw-thread terminals. When testing screw-thread terminals, the torque, in accordance with the terminalsize, shall be applied to the centerline of the terminal assembly, as follows:Screw-thread Torqueterminals (pound-inches)No. 4 -------------------------------3.0No. 6 -------------------------------5.0No. 8 ------------------------------11.0No. 10 ----------------------------15.0No. 12 ----------------------------24.01/4 inch --------------------------32.03.5.4 Other non-wire, rigid-type terminals. When testing other non-wire, rigid-type terminals, the applied torque isdependent on the equivalent diameter of the external portion of the terminal assembly. The equivalent diameter isdefined as equal to twice the distance from the terminal axis to the point of normal wire connection, as shown in theexamples on figure 211-6. The torque shall be applied in accordance with the equivalent diameter, as follows:Equivalent diameter Torque(inch) (ounce-inches)1/16 or less ---------------------0>1/16 to 1/8 inclusive ---------8>1/8 to 3/16 inclusive ---------18>3/16 to 5/16 inclusive -------40>5/16 to 1/2 inclusive ---------80>1/2 -------------------------------As specified in the individual specification4. MEASUREMENTS. Measurements to be made before and after the test, as applicable, shall be as specified inthe individual specification.METHOD211A14 April 196935. SUMMARY. The following details are to be specified in the individual specification:a. Test condition letter(s) (see 3).b. If test condition letter A is specified:(1) If pertinent, the method of holding or clamping (see 3.1.1).(2) Whether applied force shall be 1/2, 1, 2, 3, 5, 10, or 20 pounds (see 3.1.2).c. If test condition letter B is specified:(1) If critical, the method of bending and fixture required (see 3.2.2).(2) Whether number of bends shall be 2 or 5 (see 3.2.3).d. If test condition letter C is specified:(1) Whether the load shall be 1/4, 1/2, 1, 5, or 10 pounds (see 3.3.1).e. If test condition letter E is specified:(1) Torque to be applied to non-wire, rigid-type terminals when equivalent diameter is greater than1/2 inch (see 3.5.4).f. Measurements before and after test, as applicable (see 4).METHOD 211A14 April 19694METHOD 211A14 April 1969 5STEP 1. Bend lead with fingers, over rounded edge of metal plate as shown in (a).STEP 2. Center component part in chuck; secure lead in clamp as shown in (b).STEP 3. Rotate chuck part through 360° at a rate of approximately 5 seconds per 360° rotation. Successive rotations shall be in alternate directions. A total of three such 360° rotations shall be performed. Duringthis test, the chuck shall rotate around an axis which is fixed with respect to the padded clamp, or viceversa. The chuck shall have no appreciable end play during rotation.NOTE: Metric equivalents are in parentheses.FIGURE 211-4. Test condition D.METHOD 211A14 April 19696NOTE: Equivalent diameter is twice the distance between the lines indicated by the arrows.FIGURE 211-6. Method of determining equivalent diameter.METHOD 211A14 April 19697。
RTK P725LOMTL display faciaEaton Electric Limited,Great Marlings, Butterfield, Luton Beds, LU2 8DL, UK.Tel: + 44 (0)1582 723633 Fax: + 44 (0)1582 422283E-mail:********************© 2016 EatonAll Rights ReservedPublication No. INS P725LO Rev 6October 2016DescriptionThe RTK P725LO range of display facias has been designed to complement the our range of MTLalarm annunciators and instrumentation products. In particular the RTK P725 alarm annunciator with which it shares many common components and is identical in appearance from the front.The P725LO range is modular in design and can besupplied in any overall size comprising different window sizes. Switches, pushbuttons and audible sounders can also be integrated to provide a complete solution for plant status monitoring.The outer frame on the P725LO is designed forpanel mounting and is supplied with suitable clamps. Illumination is available with either bulbs rated at 28VDC or 48VDC or 24VDC ultra-high brightness LED’s for low current applications.InstallationThe P725LO is supplied with rising clamp terminal blocks on the rear of the unit to accept pin crimps or ferrules.The rear of the unit is marked with the channel numbers corresponding to the windows on the front. Separate terminals are also provided for the power input and lamp test functions.Refer to the specification section to calculate the cut-out dimensions to fit the unit into a panel. Use the clampsprovided around the perimeter of the unit to secure it into place.On the rear of the unit, each module will have up to 8 rising clamp terminals fitted. Each terminal has the following function:0V – 0V supply to power the unit +V – 24VDC supply to power the unit LT – Lamp test function HN – Horn function1 – Illuminate the first window in that cell2 – Illuminate the second window in that cell 3– Illuminate the third window in that cell 4 – Illuminate the forth window in that cellElectrical connectionsOn the rear of the unit, locate the terminals for 0V and +V . Connect these to your power supply. Note on larger units, more than one set of terminals may be provided to share the power. Ensure all are connected to the common power supplyWindow illumination with common connection Each window may be illuminated by connecting to the appropriate terminal on the rear of the unit. The polarity of this connection must be specified at the time of ordering.Refer to page 2 for individual connection diagrams depending on window size and input polarity.Switches, pushbuttons and audible sounders If specified at the time of ordering, the unit will be supplied with DPDT pushbuttons, DPDT switches or audible sounders, and these are normally fitted in the bottom right hand corner of the unit. To connect refer to the diagrams below.Pushbuttons and switches:Audible sounders:If specified at the time ordering an integral horn is fitted and driven from terminals on the back. See the connection diagrams below.Example connection diagramsSince the design of the P725LO unit is modular, please refer to the example connection diagrams below.Front view Common Negative contacts Common Positive ContactsSmall windows Medium windowsLarge windows2INS P725LO Rev 6Power supply, lamp test and horn connectionsSpecificationWindow sizeSmall: 30x30mmMedium: 30x60mm (H x W)Large: 60x60mmBulb illumination28VDC bulb rated at 50mA per bulb (24VDC units)48VDC bulb rated at 30mA per bulb (48VDC units) Small windows have 1 bulbMedium windows have 2 bulbs in parallelLarge windows have 4 bulbs in parallelLED illumination (24VDC only)LED modules are available in the following colours: Red, Amber, Y ellow, White, Green and BlueSmall windows have 1 LED moduleMedium windows have 2 LED modules in parallel Large windows have 4 LED modules in parallelEnvironmentalOperating temperature: -20°C to 50°C (bulb units) Operating temperature: -20°C to 60°C (LED units) Storage temperature: -20°C to 80°CHumidity: 0-95% RH non-condensingProtection (front of panel): IP41Protection (rear of panel): IP20Audible module (24VDC only)Sound level: 95dB @ 30cm at 24VDCFrequency: 3.3kHzCurrent consumption: 25mA at 24VDCConnectionRear mounted, rising clamp, screw terminals suitable for 2.5mm2 solid or stranded cable for bulbs or LED’s and 1.25mm2 for switches and pushbuttons Recommended torque:0.6 to 1.0Nm (M3.5 Switches and pushbuttons)1.0 to 1.3Nm (M3 Bulb and LED holders)Pushbuttons and switchesMaximum switch voltage: 250VAC/DCThermal current: 5AOperating voltage / and current (resistive load):125VAC/3A, 250VAC/2A30VDC/2A, 125VDC/0.4AContact type: SilverInsulation resistance: 100MΩ min (500VDC Megger) Dielectric strength: 2500VAC for 1 minute (Between terminals of the same pole: 1000VAC for 1 minute)Overall dimensions and panel cut-outP725LO with small windows:Height = 24 + (rows x 30)Width = 24 + (columns x 30)P725LO with medium windows:Height = 24 + (rows x 30)Width = 24 + (columns x 60)P725LO with large windows:Height = 24 + (rows x 60)Width = 24 + (columns x 60)For cut-out size, subtract 10mm from each dimension.3INS P725LO Rev 6Eaton Electric Limited,Great Marlings, Butterfield, Luton Beds, LU2 8DL, UK.Tel: + 44 (0)1582 723633 Fax: + 44 (0)1582 422283E-mail:********************© 2016 EatonAll Rights ReservedPublication No. INS P725LO Rev 6 121016October 2016EUROPE (EMEA): +44 (0)1582 723633 ********************THE AMERICAS: +1 800 835 7075*********************ASIA-PACIFIC:+65 6645 9864 / 6645 9865 ***********************The given data is only intended as a productdescription and should not be regarded as a legal warranty of properties or guarantee. In the interest of further technical developments, we reserve the right to make design changes.4Operating instructionsAfter installation and testing, the unit may be operated according to the wiring configuration. T o eliminate any potential wiring faults, please ensure all the switches and windows are fully tested in all conditions prior to use.MaintenanceFor P725LO facias with bulb illumination it is important to ensure all the bulbs are in working order. If the unit incorporates a lamp-test function, it should be used periodically. Any bulbs found to be defective should be replaced by carefully levering out the corresponding window and removing the bulb using a bulb extractortool. Refer to the diagram below.Adding or changing film legendsEach lens assembly has a small slot in the upper ridge of the surround bezel, which allows a flat blade terminal screwdriver to be used to gently lever the assembly forward. Once the assembly has been removed the diffuser, coloured filter and film legend can be accessed using a flat blade screwdriver to gently lever the lens clear of the associated parts as indicated in the diagram below. This MUST be levered on the side NOT the top or bottom.Recommended sparesFor bulb illumination it is recommended that 10% of the total number of bulbs in the system are kept as spares. No other spare parts are recommended.Part number: LP-28V-004 - 28VDC bulb (for 24VDC units) and LP-48V-001 (For 48VDC units).Due to our policy of continuous product development, we reserve the right to amend these specifications without notice.。

Unit OneTask 1⑩④⑧③⑥⑦②⑤①⑨Task 2① be consistent with他说,未来的改革必须符合自由贸易和开放投资的原则。
② specialize in启动成本较低,因为每个企业都可以只专门从事一个很窄的领域。
③ d erive from以上这些能力都源自一种叫机器学习的东西,它在许多现代人工智能应用中都处于核心地位。
④ A range of创业公司和成熟品牌推出的一系列穿戴式产品让人们欢欣鼓舞,跃跃欲试。
⑤ date back to置身硅谷的我们时常淹没在各种"新新"方式之中,我们常常忘记了,我们只是在重新发现一些可追溯至涉及商业根本的朴素教训。
Task 3T F F T FTask 4The most common viewThe principle task of engineering: To take into account the customers ‘ needs and to find the appropriate technical means to accommodate these needs.Commonly accepted claims:Technology tries to find appropriate means for given ends or desires;Technology is applied science;Technology is the aggregate of all technological artifacts;Technology is the total of all actions and institutions required to create artefacts or products and the total of all actions which make use of these artefacts or products.The author’s opinion: it is a viewpoint with flaws.Arguments: It must of course be taken for granted that the given simplified view of engineers with regard to technology has taken a turn within the last few decades. Observable changes: In many technical universities, the inter‐disciplinary courses arealready inherent parts of the curriculum.Task 5① 工程师对于自己的职业行为最常见的观点是:他们是通过应用科学结论来计划、开发、设计和推出技术产品的。

Chapter 3Breakdown VoltageThe most unique feature of power semiconductor devices is their ability to withstand high voltages. In transistors designed for microprocessors and semiconductor memories, the pressure to reduce their size to integrate more devices on a monolithic chip has resulted in a reduction in their operating voltage. In contrast, the desire to control larger power levels in motor drive and power distribution systems has encouraged the development of power devices with larger breakdown voltages. Typical applications for power devices were illustrated in Fig. 1.2. Depending upon the application, the breakdown voltage of devices can range from 20 to 30 V for voltage regulator modules (power supplies) used to deliver power to microprocessors in personal computers and servers to over 5,000 V for devices used in power transmission networks.In a semiconductor, the ability to support high voltages without the onset of significant current flow is limited by the avalanche breakdown phenomenon, which is dependent on the electric field distribution within the structure. High electric fields can be created within the interior of power devices as well as at their edges. The design optimization of power devices must be performed to meet the breakdown voltage requirements for the application while minimizing the on-state voltage drop, so that the power dissipation is reduced.Power devices are designed to support high voltages within a depletion layer formed across either a P–N junction, a metal–semiconductor (Schottky barrier) contact, or a metal–oxide–semiconductor (MOS) interface. Any electrons or holes – that enter the depletion layer either due to the space-charge generation phenomenon or by diffusion from adjacent quasineutral regions – are swept out by the electric field produced in the region by the applied voltage. As the applied voltage is increased, the electric field in the depletion region increases, resulting in acceleration of the mobile carriers to higher velocities. In the case of silicon, the mobile carriers attain a saturated drift velocity of 1 × 107 cm s−1 when the electric B.J. Baliga, Fundamentals of Power Semiconductor Devices, doi: 10.1007/978-0-387-47314-7_3,© Springer Science + Business Media, LLC 200892 FUNDAMENTALS OF POWER SEMICONDUCTOR DEVICESfield exceeds 1 × 105 V cm −1 as discussed in Chap. 2. With further increase in the electric field, the mobile carriers gain sufficient kinetic energy from the electric field, so that their interaction with the lattice atoms produces the excitation of electrons from the valence band into the conduction band. The generation of electron–hole pairs due to energy acquired from the electric field in the semiconductor is referred to as the impact ionization . Since the electron–hole pairs created by impact ionization also undergo acceleration by the electric field in the depletion region, they participate in the creation of further pairs of electrons and holes. Consequently, impact ionization is a multiplicative phenomenon, which produces a cascade of mobile carriers being transported through the depletion region leading to a signi-ficant current flow through it. Since the device is unable to sustain the application of higher voltages due to a rapid increase in the current, it is considered to undergo avalanche breakdown . Thus, avalanche breakdown limits the maximum operating voltage for power devices. In this chapter, the physics of avalanche breakdown is analyzed in relation to the properties of the semiconductor region that is supporting the voltage. After treating the one-dimensional junction, the edge terminations for power devices are described. Power devices require special edge terminations due to their finite area. The electric field at the edges usually becomes larger than in the middle of the device leading to a reduction of the breakdown voltage. Significant effort has been undertaken to develop a good understanding of the electric field enhancement at the edges, and methods have been proposed to mitigate the increase in the electric field. Various edge termination approaches are discussed in detail in this chapter because of their importance to maximizing the performance of power devices.3.1 Avalanche BreakdownThe maximum voltage that can be supported by a power device before the onset of significant current flow is limited by the avalanche breakdown phenomenon. In power devices, the voltage is supported across depletion regions. As discussed in Chap. 2, mobile carriers are accelerated in the presence of a high electric field until they gain sufficient energy to create hole–electron pairs upon collision with the lattice atoms. This impact ionization process determines the current flowing through the depletion region in the presence of a large electric field. An impact ionization coefficient was defined in Chap. 2 as the number of electron–hole pairs created by a mobile carrier traversing 1 cm through the depletion region along the direction of the electric field. The impact ionization coefficients for electrons and holes are a strong function of the magnitude of the electric field as shown in Fig. 2.10.3.1.1 Power Law Approximations for the Impact Ionization CoefficientsIt is convenient to use a power law, referred to as the Fulop’s approximation 1:357F (Si) 1.810E α−=×(3.1)Breakdown Voltage93for the impact ionization coefficients even though they actually increase exponentially with increasing electric field, when performing analytical derivations pertinent to the performance of silicon power devices. The impact ionization coefficient obtained by using this approximation is shown in Fig. 3.1 by the dashed line together with the impact ionization coefficient for electrons in silicon as governed by the Chynoweth’s law (shown by the solid line). In the same manner, it is convenient to use the Baliga’s power law approximation 2 for the impact ionization coefficients for 4H-SiC for analytical derivations:427B (4H-SiC) 3.910.E α−=×(3.2)The impact ionization coefficient obtained by using this approximation is also shown in Fig. 3.1 by the dashed line together with the impact ionization coefficient for holes in 4H-SiC as governed by the Chynoweth’s law (shown by a solid line).various edge terminations on the breakdown voltage. These analytical solutions the design of improved device structures.provide insight into the physics determining the breakdown phenomenon, enabling94 FUNDAMENTALS OF POWER SEMICONDUCTOR DEVICES3.1.2 Multiplication CoefficientThe avalanche breakdown condition is defined by the impact ionization rate becoming infinite. To analyze this, consider a one-dimensional reverse-biased N +/P junction with a depletion region extending primarily in the P-region. If an electron–hole pair is generated at a distance x from the junction, the hole will be swept toward the contact to the P-region, while the electron is simultaneously swept toward the junction with the N + region. If the electric field in the depletion region is large, these carriers will be accelerated until they gain sufficient energy to create electron–hole pairs during collisions with the lattice atoms. Based upon the definitions for the impact ionization coefficients, the hole will create [αp d x ] electron–hole pairs when traversing a distance d x through the depletion region. Simultaneously, the electron will create [αn d x ] electron–hole pairs when traversing a distance d x through the depletion region. The total number of electron–hole pairs created in the depletion region due to a single electron–hole pair initially generated at a distance x from the junction is given by 3,4n p 0()1()d ()d ,x WxM x M x x M x x αα=++∫∫(3.3)where W is the width of the depletion layer. A solution for this equation is given byn p 0()(0)exp ()d ,xM x M x αα⎡⎤=−⎢⎥⎣⎦∫ (3.4)where M (0) is the total number of electron–hole pairs at the edge of the depletionregion. Using this expression in (3.3) with x = 0 provides a solution for M (0):{}1p n p 00(0)1exp ()d d .Wx M x xααα−⎡⎤=−−⎢⎥⎣⎦∫∫ (3.5)Using this expression in (3.4) givesn p 0p n p 00exp ()d ().1exp ()d d xW xx M x x x ααααα⎡⎤−⎢⎥⎣⎦=⎡⎤−−⎢⎥⎣⎦∫∫∫ (3.6)This expression for M (x ), referred to as the multiplication coefficient , allowscalculation of the total number of electron–holes pairs created as a result of the generation of a single electron–hole pair at a distance x from the junction if the electric field distribution along the impact ionization path is known. The avalanche breakdown condition, defined to occur when the total number of electron–hole pairs generated within the depletion region approaches infinity, corresponds to M becoming equal to infinity. This condition is attained by setting the denominator of (3.6) to zero:Breakdown Voltage95{}p n p 0exp ()d d 1.Wxx x ααα⎡⎤−=⎢⎥⎣⎦∫∫(3.7)The expression on the left-hand side of (3.7) is known as the ionization integral .During the analysis of avalanche breakdown in power devices, it is common practice to find the voltage at which the ionization integral becomes equal to unity. If the impact ionization coefficients for electrons and holes are assumed to be equal, the avalanche breakdown condition can be written asd 1.Wx α=∫(3.8)This approach to the determination of the breakdown voltage is valid for power rectifiers and MOSFETs where the current flowing through the depletion region is not amplified. In devices, such as thyristors and IGBTs, the current flowing through the depletion region becomes amplified by the gain of the internal transistors. In these cases, it becomes necessary to solve for the multiplication coefficient instead of using the ionization integral. The multiplication coefficient for a high-voltage P +/N diode is given by 5p 61,1(/BV)M V =− (3.9)where V is the applied reverse bias voltage and BV is the breakdown voltage, while that for an N +/P diode is given byn 41.1(/BV)M V =−(3.10)Thus, the reverse current for a P +/N diode approaches infinity at a faster rate with increasing voltage than for an N +/P diode. This has been related to the diffusion current due to holes from the N-region in the P +/N diode.3.2 Abrupt One-Dimensional DiodePower devices are designed to support high voltages across a depletion layer formed at either a P–N junction, a metal–semiconductor (Schottky barrier) contact, or a metal–oxide–semiconductor (MOS) interface. The onset of the avalanche breakdown condition can be analyzed for all these cases, by assuming that the voltage is supported across only one side of the structure. This holds true for an abrupt P–N junction with a very high doping concentration on one side when compared with the other side. In junctions formed with a shallow depth and a high surface concentration with a lightly doped underlying region of opposite conductivity type, the depletion region extends primarily in the lightly doped region allowing their treatment as abrupt junctions.96 FUNDAMENTALS OF POWER SEMICONDUCTOR DEVICESThe analysis of a one-dimensional abrupt junction can be used to understand the design of the drift region within power devices. The case of a P +/N junction is illustrated in Fig. 3.2 where the P + side is assumed to be very highly doped, so that the electric field supported within it can be neglected. When this junction is reverse biased by the application of a positive bias to the N-region, a depletion region is formed in the N-region together with the generation of a strong electric field within it that supports the voltage. The Poisson’s equation for the N-region is then given by2D 2S Sd d (),d d V EQ x qN x x εε=−=−=−(3.11)where Q (x ) is the charge within the depletion region due to the presence of ionizeddonors, εS is the dielectric constant for the semiconductor, q is the electron charge, and N D is the donor concentration in the uniformly doped N-region.Integration of (3.11) with the boundary condition that the electric field must go to zero at the edge of the depletion region (i.e., at x = W D ) provides the electric field distribution:DD S()().qN E x W x ε=−−(3.12)Breakdown Voltage97The electric field has a maximum value of E m at the P +/N junction (x = 0) and decreases linearly to zero at x = W D . Integration of the electric field distribution through the depletion region provides the potential distribution:2D D S ().2qN x V x W x ε⎛⎞=−⎜⎟⎝⎠(3.13)This equation is obtained by using the boundary condition that the potential is zeroat x = 0 within the P + region. The potential varies quadratically as illustrated in the figure. The thickness of the depletion region (W D ) can be related to the applied reverse bias (V a ) by using the boundary condition:D a (),V W V =(3.14) D W =(3.15)Using these equations, the maximum electric field at the junction can be obtained:m E =(3.16)When the applied bias increases, the maximum electric field approaches values at which significant impact ionization begins to occur. The breakdown voltage is determined by the ionization integral becoming equal to unity:d 1,Wx α=∫(3.17)where α is the impact ionization coefficient discussed in Chap. 2. To obtain a closed-form solution for the breakdown voltage, it is convenient to use the power law for the impact ionization coefficient in place of Chynoweth’s law. Substituting the Fulop’s power law into (3.17) with the electric field distribution given by (3.12), analytical solutions for the breakdown voltage and the corresponding maximum depletion layer width can be derived for silicon:133/4PP DBV (Si) 5.3410N −=× (3.18) and107/8PP D (Si) 2.6710.W N −=×(3.19)In a similar manner, substituting the Baliga’s power law into (3.17) with theelectric field distribution given by (3.12), analytical solutions for the breakdown voltage and the corresponding maximum depletion layer width can be derived for 4H-SiC:98 FUNDAMENTALS OF POWER SEMICONDUCTOR DEVICES153/4PP DBV (4H-SiC) 3.010N −=× (3.20)and117/8PP D (4H-SiC) 1.8210.W N −=×(3.21)The breakdown voltage is plotted in Fig. 3.3 as a function of the doping concentration on the lightly doped side of the junction. It can be seen that the breakdown voltage decreases with increasing doping concentration. It is worth pointing out that it is possible to support a much larger voltage in 4H-SiC when compared with silicon for any given doping concentration. The ratio of the breakdown voltage in 4H-SiC to that in silicon for the same doping concentration is found to be 56.2. It is also obvious from this figure that for a given breakdown voltage, it is possible to use a much higher doping concentration in the drift region for 4H-SiC devices when compared with silicon devices. The ratio of the doping concentration in the drift region for a 4H-SiC device to that for a silicon device with the same breakdown voltage is found to be 200. The maximum depletion width reached at the onset of breakdown is shown in Fig. 3.4 for silicon and 4H-SiC. It can be seen that the thickness of the lightly doped side of the junction must be increased to support larger voltages. For the same doping concentration, the maximum depletion width in 4H-SiC is 6.8 times larger than that in silicon because it can sustain a much larger electric field. However, for a given breakdown voltage, the depletion width in 4H-SiC is smaller than for a silicon device because of the much larger doping concentration in the drift region. This smaller depletion width, in conjunction with the far larger dopingBreakdown Voltage 99 concentration, results in an enormous reduction in the specific on-resistance of the drift region in 4H-SiC when compared with silicon.The onset of the avalanche breakdown for an abrupt parallel-plane junction, as defined by the above equations, is accompanied by a maximum electric field at the junction referred to as the critical electric field for breakdown.100 FUNDAMENTALS OF POWER SEMICONDUCTOR DEVICESCombining (3.16) and (3.18), the critical electric field for breakdown in silicon is given by1/8C D (Si)4010,E N =(3.22)while that for 4H-SiC is given by41/8C D (4H-SiC) 3.310.E N =× (3.23)The critical electric field for 4H-SiC can be compared with that for silicon inFig. 3.5. In both cases, the critical electric field is a weak function of the doping concentration. For the same doping concentration, the critical electric field in 4H-SiC is 8.2 times larger than in silicon. The larger critical electric field in 4H-SiC results in a much larger Baliga’s Figure of Merit (see Chap. 1). The critical electric field is a useful parameter for identifying the onset of avalanche breakdown in power device structures. Due to the very strong dependence of the impact ionization coefficients on the electric field strength, avalanche breakdown can be usually assumed to occur when the electric field within any local region of a power device approaches the critical electric field. However, it is important to note that this provides only an indication of the onset of breakdown and the exact breakdown voltage must be determined by extracting the ionization integral. This is particularly true for devices where the electric field deviates from the triangular shape pertinent to an abrupt parallel-plane junction.3.3 Ideal Specific On-ResistanceThe specific on-resistance of the drift region is related to the breakdown voltage by (1.11) which is repeated here for discussion:2on,sp3S n C4BV .R E εµ= (3.24)An accurate modeling of the specific on-resistance requires taking into account the dependence of the critical electric field and mobility on the doping concentration, which varies as the breakdown voltage is changed. It is possible to do this by computing the doping concentration for achieving a given breakdown voltage and then using the equations for the depletion width and mobility as a function of doping concentration to obtain the specific on-resistance:PPon,sp n D.W R q N µ=(3.25)The specific on-resistance projected for the drift region in 4H-SiC devices by using the above method is compared with that for silicon devices in Fig. 3.6. The values for 4H-SiC are about 2,000 times smaller than for silicon devices for the samebreakdown voltage. This has encouraged the development of unipolar power devices,2 such as Schottky rectifiers and MOSFETs, from 4H-SiC.3.4 Abrupt Punch-Through DiodeIn the case of some power devices, such as P-i-N rectifiers, the resistance of the drift region is greatly reduced during on-state current flow by the injection of a large concentration of minority carriers. In these cases, the doping concentration of the drift region does not determine the resistance to the on-state current flow. Consequently, it is preferable to use a thinner depletion region with a reduceddoping concentration to support the voltage. This configuration for the drift region is called the punch-through design .The electric field distribution for the punch-through design is shown in Fig. 3.7. In comparison with the triangular electric field distribution shown in Fig. 3.2, the electric field for the punch-through design takes a trapezoidal shape. The electric field varies more gradually through the drift region due to its lower doping concentration and then very rapidly with distance within the N + end region due to its very high doping concentration. The electric field at the interface between the drift region and the N + end region is given byDP1m P S ,qN E E W ε=− (3.26)where E m is the maximum electric field at the junction, N DP is the doping concentration in the N-type drift region, and W P is the width of the N-type drift region.The voltage supported by the punch-through diode is given bym 1PT P 2E E V W +⎛⎞=⎜⎟⎝⎠ (3.27)if the small voltage supported within the N + end region is neglected. The punch-through diode undergoes avalanche breakdown when the maximum electric field (E m ) becomes equal to the critical electric field (E C ) for breakdown. Using this condition in (3.27) together with the field distribution in (3.26), the breakdown voltage for the punch-through diode is given by2DP P PT C P S BV .2qN W E W ε=− (3.28)The breakdown voltages calculated using this relationship are shown in Fig. 3.8 for silicon punch-through diodes with various thicknesses for the drift region. In performing these calculations, the change in the critical electric field with doping concentration was taken into account. For any doping concentration for the drift region, the breakdown voltage for the punch-through diode is reduced due to the truncation of the electric field at the N + end region. The breakdown voltage becomes smaller as the thickness of the drift region is reduced. From the point of view of designing the drift region for a P-i-N rectifier, it is possible to obtain a breakdown voltage of 1,000 V with a drift region thickness of about 50 µm. In contrast, a drift region thickness of 80 µm would be required in the nonpunch-through case. This reduced drift region thickness with the punch-through design is beneficial not only for reducing the on-state voltage drop but also for reducing the stored charge and consequently the reverse recovery power loss as discussed later in the book.A similar analysis for the breakdown voltages can be performed for punch-through diodes fabricated from 4H-SiC with various thicknesses for the drift region (Fig. 3.9). In performing these calculations, the change in the critical electric field with doping concentration, as described by (3.23), must be taken into account. In comparison with silicon punch-through diodes, a much higher (∼10 times) doping concentration can be used in the drift region for 4H-SiC to achievethe punch-through design with a given thickness for the drift region. From the point of view of designing the drift region for a P-i-N rectifier, it is possible to obtain a breakdown voltage of 10,000 V with a drift region thickness of about 50 µm in 4H-SiC. In contrast, a drift region thickness of 80 µm would be required in the nonpunch-through case. This reduced drift region thickness with the punch-through design is beneficial for reducing the on-state voltage drop. However, the minority carrier lifetime in 4H-SiC has been found to be low resulting in poor conductivity modulation of the drift region. It is therefore advisable to maintain a high doping concentration in the drift region for P-i-N rectifiers fabricated from 4H-SiC.3.5 Linearly Graded Junction DiodePower devices fabricated using junctions with high surface doping concentration and shallow thickness tend to behave like the abrupt junction diodes that were discussed in the previous sections. Power devices, such as thyristors, that are designed to support very high voltages (above 2,000 V) rely upon junctions with low surface concentration and large depth to enhance the blocking voltage capability. In addition, power devices with low (<50 V) blocking voltages, such as low-voltage power MOSFETs, require drift regions with relatively high doping concentrations that are comparable with the doping level on the diffused side of thejunction. A significant fraction of the reverse bias voltage is supported within the diffused side of the junction in this case as well.These types of junctions can be analyzed by assuming a linearly graded doping profile in the vicinity of the junction. A typical doping profile for a diffused junction diode is illustrated in Fig. 3.10. For diffused junctions, it is customary to plot the profile with the doping concentration displayed using a logarithmic scale as shown in the upper part of the figure. Due to the compensation of the N-region by the P-type dopant in the vicinity of the junction, the profile has a linear net doping distribution as illustrated in the lower portion of the figure. The diffused junction can therefore be treated as a combination of a linearly graded junction and a uniformly doped junction.If the linear doping grading is sufficiently steep, the maximum electric field at the junction can reach the critical electric field with the depletion region confined to this portion of the doping profile. The linearly graded junction is illustrated in Fig. 3.11 together with the electric field and potential distributions. Note that the depletion region extends to both side of the metallurgical junction by a distance W. With a positive voltage applied to the N-region, the junction becomes reverse biased with a net negative charge on the P-side due to the ionized acceptors having a greater concentration than the donors, while a net positive charge develops on the N-side due to the ionized donors having a greater concentration than the acceptors. The concentration of the net charge varies linearly with distance with a grade constant G.The breakdown voltage of this linearly graded junction can be analyzed by using the following charge distribution profile in Poisson’s equation:().Q x qGx = (3.29) Applying this charge distribution to the Poisson’s equation gives2S S d d ().d d V E Q x qGx x x εε−=−=−= (3.30)Integration of this equation with the boundary condition that the electric field must be zero at the edge of the depletion region (x = W ) provides the electric field distribution:22S()().2qG E x x W ε=− (3.31) The electric field varies parabolically with distance with its maximum value at the junction given by2m S .2qGW E ε= (3.32)Integration of the electric field distribution through the depletion region with the boundary conditions that the potential is zero at x = −W on the P-side of the junction yields323S ().326qG W W x x V x ε⎛⎞=+−⎜⎟⎝⎠ (3.33)This voltage distribution is shown at the bottom of Fig. 3.11. The depletion layer width (W ) on both sides of the junction can be obtained by using the boundary condition that the voltage on the N-side of the junction is equal to the applied bias (V a ):1/3S a 3.V W qG ε⎛⎞=⎜⎟⎝⎠ (3.34)In the case of devices, such as power MOSFETs, the extension of the depletion layer on the diffused side of the junction can lead to reach-thorough breakdown at well below the avalanche breakdown voltage. The depletion width calculated by using (3.34), based upon approximation of the diffused junction by a linearly graded junction, provides an analytical approach to designing the width of the P-base region.A closed-form analytical solution for the breakdown voltage of the linearly graded junction can be obtained by determination of the voltage at which theimpact ionization integral becomes equal to unity. Using the ionization integral given by (3.17) with Fulop’s approximation for the impact ionization coefficients and the electric field distribution given by (3.31),73522S 1.810()d 1.2W W qG x W x ε−−⎡⎤×−=⎢⎥⎣⎦∫ (3.35)The solution for this equation provides the depletion width at the point of breakdown for the linearly graded junction:57/15CL 9.110.W G −=× (3.36)Using this depletion width in (3.34), the breakdown voltage for the linearly graded junction is found to be given by92/5L BV 9.210.G −=× (3.37)As illustrated by the electric field distribution in Fig. 3.10, the diffused junction diode usually behaves as a combination of a linearly graded junction and an abrupt junction with uniform doping on the lightly doped side. The extension of the depletion region into the diffused side of the junction enhances the breakdown voltage to above that derived earlier for the abrupt parallel-plane junction because of the additional voltage that is supported on the diffused side of the junction. This can be taken advantage of during the design of low-voltage (<30 V) power MOSFETs.3.6 Edge TerminationsAll semiconductor devices have a finite size, which is achieved by sawing through the wafers to produce the chips that go into packages. The sawing of wafers, performed by using diamond-coated blades, produces severe damage to the crystal. In the case of power devices, if the sawing is performed through the junction that must support a high voltage, the crystal damage creates a high leakage current that degrades the breakdown voltage and its stability with respect to time. This problem can be addressed by using special junction terminations around the edges of the power devices, so that the depletion regions of the high-voltage junctions do not intersect with the saw lanes where the damage is located. Another approach that can be used to control and preserve a high breakdown voltage is by shaping the surface of the edges of the device. The earliest method for shaping the edges was by mesa etching. Subsequently, the beveling of the edges of wafers was found to be very effective in preserving the breakdown voltage of high-voltage power rectifiers and thyristors. With the widespread availability of ion implantation for the fabrication of power devices in the 1980s, the use of a lightly doped zone at the edges of junctions has been found to be effective in achieving high breakdown。

Reprinted with corrections from The Bell System Technical Journal,V ol.27,pp.379–423,623–656,July,October,1948.A Mathematical Theory of CommunicationBy C.E.SHANNONI NTRODUCTIONHE recent development of various methods of modulation such as PCM and PPM which exchangebandwidth for signal-to-noise ratio has intensified the interest in a general theory of communication.A basis for such a theory is contained in the important papers of Nyquist1and Hartley2on this subject.In the present paper we will extend the theory to include a number of new factors,in particular the effect of noise in the channel,and the savings possible due to the statistical structure of the original message and due to the nature of thefinal destination of the information.The fundamental problem of communication is that of reproducing at one point either exactly or ap-proximately a message selected at another point.Frequently the messages have meaning;that is they refer to or are correlated according to some system with certain physical or conceptual entities.These semantic aspects of communication are irrelevant to the engineering problem.The significant aspect is that the actual message is one selected from a set of possible messages.The system must be designed to operate for each possible selection,not just the one which will actually be chosen since this is unknown at the time of design.If the number of messages in the set isfinite then this number or any monotonic function of this number can be regarded as a measure of the information produced when one message is chosen from the set,all choices being equally likely.As was pointed out by Hartley the most natural choice is the logarithmic function.Although this definition must be generalized considerably when we consider the influence of the statistics of the message and when we have a continuous range of messages,we will in all cases use an essentially logarithmic measure.The logarithmic measure is more convenient for various reasons:1.It is practically more useful.Parameters of engineering importance such as time,bandwidth,numberof relays,etc.,tend to vary linearly with the logarithm of the number of possibilities.For example,adding one relay to a group doubles the number of possible states of the relays.It adds1to the base2logarithm of this number.Doubling the time roughly squares the number of possible messages,ordoubles the logarithm,etc.2.It is nearer to our intuitive feeling as to the proper measure.This is closely related to(1)since we in-tuitively measures entities by linear comparison with common standards.One feels,for example,thattwo punched cards should have twice the capacity of one for information storage,and two identicalchannels twice the capacity of one for transmitting information.3.It is mathematically more suitable.Many of the limiting operations are simple in terms of the loga-rithm but would require clumsy restatement in terms of the number of possibilities.The choice of a logarithmic base corresponds to the choice of a unit for measuring information.If the base2is used the resulting units may be called binary digits,or more briefly bits,a word suggested by J.W.Tukey.A device with two stable positions,such as a relay or aflip-flop circuit,can store one bit of information.N such devices can store N bits,since the total number of possible states is2N and log22N N.If the base10is used the units may be called decimal digits.Sincelog2M log10M log102332log10M1Nyquist,H.,“Certain Factors Affecting Telegraph Speed,”Bell System Technical Journal,April1924,p.324;“Certain Topics in Telegraph Transmission Theory,”A.I.E.E.Trans.,v.47,April1928,p.617.2Hartley,R.V.L.,“Transmission of Information,”Bell System Technical Journal,July1928,p.535.INFORMATIONSOURCE TRANSMITTER RECEIVER DESTINATIONNOISE SOURCEFig.1—Schematic diagram of a general communication system.a decimal digit is about 313bits.A digit wheel on a desk computing machine has ten stable positions and therefore has a storage capacity of one decimal digit.In analytical work where integration and differentiation are involved the base e is sometimes useful.The resulting units of information will be called natural units.Change from the base a to baseb merely requires multiplication by log b a .By a communication system we will mean a system of the type indicated schematically in Fig.1.It consists of essentially five parts:1.An information source which produces a message or sequence of messages to be communicated to thereceiving terminal.The message may be of various types:(a)A sequence of letters as in a telegraph of teletype system;(b)A single function of time f t as in radio or telephony;(c)A function of time and other variables as in black and white television —here the message may be thought of as a function f x y t of two space coordinates and time,the light intensity at point x y and time t on a pickup tube plate;(d)Two or more functions of time,say f t ,g t ,h t —this is the case in “three-dimensional”sound transmission or if the system is intended to service several individual channels in multiplex;(e)Several functions of several variables —in color television the message consists of three functions f x y t ,g x y t ,h x y t defined in a three-dimensional continuum —we may also think of these three functions as components of a vector field defined in the region —similarly,several black and white television sources would produce “messages”consisting of a number of functions of three variables;(f)Various combinations also occur,for example in television with an associated audio channel.2.A transmitter which operates on the message in some way to produce a signal suitable for trans-mission over the channel.In telephony this operation consists merely of changing sound pressure into a proportional electrical current.In telegraphy we have an encoding operation which produces a sequence of dots,dashes and spaces on the channel corresponding to the message.In a multiplex PCM system the different speech functions must be sampled,compressed,quantized and encoded,and finally interleaved properly to construct the signal.V ocoder systems,television and frequency modulation are other examples of complex operations applied to the message to obtain the signal.3.The channel is merely the medium used to transmit the signal from transmitter to receiver.It may bea pair of wires,a coaxial cable,a band of radio frequencies,a beam of light,etc.4.The receiver ordinarily performs the inverse operation of that done by the transmitter,reconstructingthe message from the signal.5.The destination is the person (or thing)for whom the message is intended.We wish to consider certain general problems involving communication systems.To do this it is first necessary to represent the various elements involved as mathematical entities,suitably idealized from theirphysical counterparts.We may roughly classify communication systems into three main categories:discrete, continuous and mixed.By a discrete system we will mean one in which both the message and the signal are a sequence of discrete symbols.A typical case is telegraphy where the message is a sequence of lettersand the signal a sequence of dots,dashes and spaces.A continuous system is one in which the message and signal are both treated as continuous functions,e.g.,radio or television.A mixed system is one in which both discrete and continuous variables appear,e.g.,PCM transmission of speech.Wefirst consider the discrete case.This case has applications not only in communication theory,but also in the theory of computing machines,the design of telephone exchanges and otherfields.In additionthe discrete case forms a foundation for the continuous and mixed cases which will be treated in the second half of the paper.PART I:DISCRETE NOISELESS SYSTEMS1.T HE D ISCRETE N OISELESS C HANNELTeletype and telegraphy are two simple examples of a discrete channel for transmitting information.Gen-erally,a discrete channel will mean a system whereby a sequence of choices from afinite set of elementarysymbols S1S n can be transmitted from one point to another.Each of the symbols S i is assumed to have a certain duration in time t i seconds(not necessarily the same for different S i,for example the dots anddashes in telegraphy).It is not required that all possible sequences of the S i be capable of transmission on the system;certain sequences only may be allowed.These will be possible signals for the channel.Thus in telegraphy suppose the symbols are:(1)A dot,consisting of line closure for a unit of time and then line open for a unit of time;(2)A dash,consisting of three time units of closure and one unit open;(3)A letter space consisting of,say,three units of line open;(4)A word space of six units of line open.We might place the restriction on allowable sequences that no spaces follow each other(for if two letter spaces are adjacent, it is identical with a word space).The question we now consider is how one can measure the capacity of such a channel to transmit information.In the teletype case where all symbols are of the same duration,and any sequence of the32symbols is allowed the answer is easy.Each symbol representsfive bits of information.If the system transmits n symbols per second it is natural to say that the channel has a capacity of5n bits per second.This does not mean that the teletype channel will always be transmitting information at this rate—this is the maximum possible rate and whether or not the actual rate reaches this maximum depends on the source of information which feeds the channel,as will appear later.In the more general case with different lengths of symbols and constraints on the allowed sequences,we make the following definition:Definition:The capacity C of a discrete channel is given byC LimT∞log N TTwhere N T is the number of allowed signals of duration T.It is easily seen that in the teletype case this reduces to the previous result.It can be shown that the limit in question will exist as afinite number in most cases of interest.Suppose all sequences of the symbols S1S n are allowed and these symbols have durations t1t n.What is the channel capacity?If N t represents the number of sequences of duration t we haveN t N t t1N t t2N t t nThe total number is equal to the sum of the numbers of sequences ending in S1S2S n and these are N t t1N t t2N t t n,respectively.According to a well-known result infinite differences,N t is then asymptotic for large t to X t0where X0is the largest real solution of the characteristic equation:X t1X t2X t n1and thereforeC log X0In case there are restrictions on allowed sequences we may still often obtain a difference equation of this type andfind C from the characteristic equation.In the telegraphy case mentioned aboveN t N t2N t4N t5N t7N t8N t10as we see by counting sequences of symbols according to the last or next to the last symbol occurring. Hence C is log0where0is the positive root of12457810.Solving this wefind C0539.A very general type of restriction which may be placed on allowed sequences is the following:We imagine a number of possible states a1a2a m.For each state only certain symbols from the set S1S n can be transmitted(different subsets for the different states).When one of these has been transmitted the state changes to a new state depending both on the old state and the particular symbol transmitted.The telegraph case is a simple example of this.There are two states depending on whether or not a space was the last symbol transmitted.If so,then only a dot or a dash can be sent next and the state always changes. If not,any symbol can be transmitted and the state changes if a space is sent,otherwise it remains the same. The conditions can be indicated in a linear graph as shown in Fig.2.The junction points correspond totheFig.2—Graphical representation of the constraints on telegraph symbols.states and the lines indicate the symbols possible in a state and the resulting state.In Appendix1it is shown that if the conditions on allowed sequences can be described in this form C will exist and can be calculated in accordance with the following result:Theorem1:Let b s i j be the duration of the s th symbol which is allowable in state i and leads to state j. Then the channel capacity C is equal to log W where W is the largest real root of the determinant equation:∑s W bsi j i j0where i j1if i j and is zero otherwise.For example,in the telegraph case(Fig.2)the determinant is:1W2W4W3W6W2W410On expansion this leads to the equation given above for this case.2.T HE D ISCRETE S OURCE OF I NFORMATIONWe have seen that under very general conditions the logarithm of the number of possible signals in a discrete channel increases linearly with time.The capacity to transmit information can be specified by giving this rate of increase,the number of bits per second required to specify the particular signal used.We now consider the information source.How is an information source to be described mathematically, and how much information in bits per second is produced in a given source?The main point at issue is the effect of statistical knowledge about the source in reducing the required capacity of the channel,by the useof proper encoding of the information.In telegraphy,for example,the messages to be transmitted consist of sequences of letters.These sequences,however,are not completely random.In general,they form sentences and have the statistical structure of,say,English.The letter E occurs more frequently than Q,the sequence TH more frequently than XP,etc.The existence of this structure allows one to make a saving in time(or channel capacity)by properly encoding the message sequences into signal sequences.This is already done to a limited extent in telegraphy by using the shortest channel symbol,a dot,for the most common English letter E;while the infrequent letters,Q,X,Z are represented by longer sequences of dots and dashes.This idea is carried still further in certain commercial codes where common words and phrases are represented by four-orfive-letter code groups with a considerable saving in average time.The standardized greeting and anniversary telegrams now in use extend this to the point of encoding a sentence or two into a relatively short sequence of numbers.We can think of a discrete source as generating the message,symbol by symbol.It will choose succes-sive symbols according to certain probabilities depending,in general,on preceding choices as well as the particular symbols in question.A physical system,or a mathematical model of a system which produces such a sequence of symbols governed by a set of probabilities,is known as a stochastic process.3We may consider a discrete source,therefore,to be represented by a stochastic process.Conversely,any stochastic process which produces a discrete sequence of symbols chosen from afinite set may be considered a discrete source.This will include such cases as:1.Natural written languages such as English,German,Chinese.2.Continuous information sources that have been rendered discrete by some quantizing process.Forexample,the quantized speech from a PCM transmitter,or a quantized television signal.3.Mathematical cases where we merely define abstractly a stochastic process which generates a se-quence of symbols.The following are examples of this last type of source.(A)Suppose we havefive letters A,B,C,D,E which are chosen each with probability.2,successivechoices being independent.This would lead to a sequence of which the following is a typicalexample.B DC B C E C C C AD C B D D A AE C E E AA B B D A E E C A C E E B A E E C B C E A D.This was constructed with the use of a table of random numbers.4(B)Using the samefive letters let the probabilities be.4,.1,.2,.2,.1,respectively,with successivechoices independent.A typical message from this source is then:A A A C D CB DC E A AD A D A CE D AE A D C A B E D A D D C E C A A A A A D.(C)A more complicated structure is obtained if successive symbols are not chosen independentlybut their probabilities depend on preceding letters.In the simplest case of this type a choicedepends only on the preceding letter and not on ones before that.The statistical structure canthen be described by a set of transition probabilities p i j,the probability that letter i is followedby letter j.The indices i and j range over all the possible symbols.A second equivalent way ofspecifying the structure is to give the“digram”probabilities p i j,i.e.,the relative frequency ofthe digram i j.The letter frequencies p i,(the probability of letter i),the transition probabilities 3See,for example,S.Chandrasekhar,“Stochastic Problems in Physics and Astronomy,”Reviews of Modern Physics,v.15,No.1, January1943,p.1.4Kendall and Smith,Tables of Random Sampling Numbers,Cambridge,1939.p i j and the digram probabilities p i j are related by the following formulas:p i∑j p i j∑jp j i∑jp j p j ip i j p i p i j∑j p i j∑ip i∑i jp i j1As a specific example suppose there are three letters A,B,C with the probability tables: p i j jA B CA0451 5i B1212C1225110i p iA927B1627C227p i j jA B CA0415115i B827827C12741351135A typical message from this source is the following:A B B A B A B A B A B A B A B B B A B B B B B A B A B A B A B A B B B A C A C A BB A B B B B A B B A B AC B B B A B A.The next increase in complexity would involve trigram frequencies but no more.The choice ofa letter would depend on the preceding two letters but not on the message before that point.Aset of trigram frequencies p i j k or equivalently a set of transition probabilities p i j k wouldbe required.Continuing in this way one obtains successively more complicated stochastic pro-cesses.In the general n-gram case a set of n-gram probabilities p i1i2i n or of transitionprobabilities p i1i2i n1i n is required to specify the statistical structure.(D)Stochastic processes can also be defined which produce a text consisting of a sequence of“words.”Suppose there arefive letters A,B,C,D,E and16“words”in the language withassociated probabilities:.10A.16BEBE.11CABED.04DEB.04ADEB.04BED.05CEED.15DEED.05ADEE.02BEED.08DAB.01EAB.01BADD.05CA.04DAD.05EESuppose successive“words”are chosen independently and are separated by a space.A typicalmessage might be:DAB EE A BEBE DEED DEB ADEE ADEE EE DEB BEBE BEBE BEBE ADEE BED DEEDDEED CEED ADEE A DEED DEED BEBE CABED BEBE BED DAB DEED ADEB.If all the words are offinite length this process is equivalent to one of the preceding type,butthe description may be simpler in terms of the word structure and probabilities.We may alsogeneralize here and introduce transition probabilities between words,etc.These artificial languages are useful in constructing simple problems and examples to illustrate vari-ous possibilities.We can also approximate to a natural language by means of a series of simple artificial languages.The zero-order approximation is obtained by choosing all letters with the same probability and independently.Thefirst-order approximation is obtained by choosing successive letters independently but each letter having the same probability that it has in the natural language.5Thus,in thefirst-order ap-proximation to English,E is chosen with probability.12(its frequency in normal English)and W with probability.02,but there is no influence between adjacent letters and no tendency to form the preferred 5Letter,digram and trigram frequencies are given in Secret and Urgent by Fletcher Pratt,Blue Ribbon Books,1939.Word frequen-cies are tabulated in Relative Frequency of English Speech Sounds,G.Dewey,Harvard University Press,1923.digrams such as TH,ED,etc.In the second-order approximation,digram structure is introduced.After aletter is chosen,the next one is chosen in accordance with the frequencies with which the various lettersfollow thefirst one.This requires a table of digram frequencies p i j.In the third-order approximation, trigram structure is introduced.Each letter is chosen with probabilities which depend on the preceding twoletters.3.T HE S ERIES OF A PPROXIMATIONS TO E NGLISHTo give a visual idea of how this series of processes approaches a language,typical sequences in the approx-imations to English have been constructed and are given below.In all cases we have assumed a27-symbol “alphabet,”the26letters and a space.1.Zero-order approximation(symbols independent and equiprobable).XFOML RXKHRJFFJUJ ZLPWCFWKCYJ FFJEYVKCQSGHYD QPAAMKBZAACIBZL-HJQD.2.First-order approximation(symbols independent but with frequencies of English text).OCRO HLI RGWR NMIELWIS EU LL NBNESEBYA TH EEI ALHENHTTPA OOBTTV ANAH BRL.3.Second-order approximation(digram structure as in English).ON IE ANTSOUTINYS ARE T INCTORE ST BE S DEAMY ACHIN D ILONASIVE TU-COOWE AT TEASONARE FUSO TIZIN ANDY TOBE SEACE CTISBE.4.Third-order approximation(trigram structure as in English).IN NO IST LAT WHEY CRATICT FROURE BIRS GROCID PONDENOME OF DEMONS-TURES OF THE REPTAGIN IS REGOACTIONA OF CRE.5.First-order word approximation.Rather than continue with tetragram,,n-gram structure it is easierand better to jump at this point to word units.Here words are chosen independently but with their appropriate frequencies.REPRESENTING AND SPEEDILY IS AN GOOD APT OR COME CAN DIFFERENT NAT-URAL HERE HE THE A IN CAME THE TO OF TO EXPERT GRAY COME TO FURNISHESTHE LINE MESSAGE HAD BE THESE.6.Second-order word approximation.The word transition probabilities are correct but no further struc-ture is included.THE HEAD AND IN FRONTAL ATTACK ON AN ENGLISH WRITER THAT THE CHAR-ACTER OF THIS POINT IS THEREFORE ANOTHER METHOD FOR THE LETTERS THATTHE TIME OF WHO EVER TOLD THE PROBLEM FOR AN UNEXPECTED.The resemblance to ordinary English text increases quite noticeably at each of the above steps.Note that these samples have reasonably good structure out to about twice the range that is taken into account in their construction.Thus in(3)the statistical process insures reasonable text for two-letter sequences,but four-letter sequences from the sample can usually befitted into good sentences.In(6)sequences of four or more words can easily be placed in sentences without unusual or strained constructions.The particular sequence of ten words“attack on an English writer that the character of this”is not at all unreasonable.It appears then that a sufficiently complex stochastic process will give a satisfactory representation of a discrete source.Thefirst two samples were constructed by the use of a book of random numbers in conjunction with(for example2)a table of letter frequencies.This method might have been continued for(3),(4)and(5), since digram,trigram and word frequency tables are available,but a simpler equivalent method was used.To construct(3)for example,one opens a book at random and selects a letter at random on the page.This letter is recorded.The book is then opened to another page and one reads until this letter is encountered. The succeeding letter is then recorded.Turning to another page this second letter is searched for and the succeeding letter recorded,etc.A similar process was used for(4),(5)and(6).It would be interesting if further approximations could be constructed,but the labor involved becomes enormous at the next stage.4.G RAPHICAL R EPRESENTATION OF A M ARKOFF P ROCESSStochastic processes of the type described above are known mathematically as discrete Markoff processes and have been extensively studied in the literature.6The general case can be described as follows:There exist afinite number of possible“states”of a system;S1S2S n.In addition there is a set of transition probabilities;p i j the probability that if the system is in state S i it will next go to state S j.To make thisMarkoff process into an information source we need only assume that a letter is produced for each transition from one state to another.The states will correspond to the“residue of influence”from preceding letters.The situation can be represented graphically as shown in Figs.3,4and5.The“states”are thejunctionFig.3—A graph corresponding to the source in example B.points in the graph and the probabilities and letters produced for a transition are given beside the correspond-ing line.Figure3is for the example B in Section2,while Fig.4corresponds to the example C.In Fig.3Fig.4—A graph corresponding to the source in example C.there is only one state since successive letters are independent.In Fig.4there are as many states as letters. If a trigram example were constructed there would be at most n2states corresponding to the possible pairs of letters preceding the one being chosen.Figure5is a graph for the case of word structure in example D. Here S corresponds to the“space”symbol.5.E RGODIC AND M IXED S OURCESAs we have indicated above a discrete source for our purposes can be considered to be represented by a Markoff process.Among the possible discrete Markoff processes there is a group with special properties of significance in communication theory.This special class consists of the“ergodic”processes and we shall call the corresponding sources ergodic sources.Although a rigorous definition of an ergodic process is somewhat involved,the general idea is simple.In an ergodic process every sequence produced by the process 6For a detailed treatment see M.Fr´e chet,M´e thode des fonctions arbitraires.Th´e orie des´e v´e nements en chaˆıne dans le cas d’un nombrefini d’´e tats possibles.Paris,Gauthier-Villars,1938.is the same in statistical properties.Thus the letter frequencies,digram frequencies,etc.,obtained from particular sequences,will,as the lengths of the sequences increase,approach definite limits independent of the particular sequence.Actually this is not true of every sequence but the set for which it is false has probability zero.Roughly the ergodic property means statistical homogeneity.All the examples of artificial languages given above are ergodic.This property is related to the structure of the corresponding graph.If the graph has the following two properties7the corresponding process will be ergodic:1.The graph does not consist of two isolated parts A and B such that it is impossible to go from junctionpoints in part A to junction points in part B along lines of the graph in the direction of arrows and also impossible to go from junctions in part B to junctions in part A.2.A closed series of lines in the graph with all arrows on the lines pointing in the same orientation willbe called a“circuit.”The“length”of a circuit is the number of lines in it.Thus in Fig.5series BEBES is a circuit of length5.The second property required is that the greatest common divisor of the lengths of all circuits in the graph beone.If thefirst condition is satisfied but the second one violated by having the greatest common divisor equal to d1,the sequences have a certain type of periodic structure.The various sequences fall into d different classes which are statistically the same apart from a shift of the origin(i.e.,which letter in the sequence is called letter1).By a shift of from0up to d1any sequence can be made statistically equivalent to any other.A simple example with d2is the following:There are three possible letters a b c.Letter a isfollowed with either b or c with probabilities13and23respectively.Either b or c is always followed by lettera.Thus a typical sequence isa b a c a c a c a b a c a b a b a c a cThis type of situation is not of much importance for our work.If thefirst condition is violated the graph may be separated into a set of subgraphs each of which satisfies thefirst condition.We will assume that the second condition is also satisfied for each subgraph.We have in this case what may be called a“mixed”source made up of a number of pure components.The components correspond to the various subgraphs.If L1,L2,L3are the component sources we may writeL p1L1p2L2p3L37These are restatements in terms of the graph of conditions given in Fr´e chet.。


IT技术论坛TECHNOLOGY AND INFORMATION 浅谈电力企业终端类问题的排查处理方法封祐钧广东电网有限责任公司东莞供电局广东东莞523000摘要随着勒索病毒、暗云病毒和远程代码执行漏洞等风险消息的发布,引起了各行各业对信息安全的高度重视,电力行业也不例外,积极采取防护措施。
在信息安全中,终端是源生性威胁,在大企业大安全的前提下,终端计算机必须进行安全加固及安全防护策略的应用,一旦出现终端问题,由于问题处理思路及方法不统一,在处理流程不明确的情况下,往往会出现终端问题无法进行闭环管理,严重影响终端问题排查处理效率。
本文就电力企业里终端类问题的排查和处理方法进行了阐述。
关键词终端运维;问题排查;效率提升Talking about the methods of checking and dealing with terminal problems in electric powerenterprisesYoujun-FENGCSG Guangdong Power Grid Dongguan Power Supply Bureau,Dongguan,Guangdong523008Abstract With the release of risk information such as extortion virus,dark cloud virus and remote code executionvulnerability,all walks of l ife attach great importance to information security,and the power industry is no exception,activelytake protective measures.In information security,the terminal is a source threat.On the premise of large enterprise security,the terminal computer must carry out security reinforcement and application of security protection strategy.Once the terminalproblem arises,due to the inconsistent ideas and methods of handling the problem,the terminal problem often occurs whenthe processing flow is not clear.The closed-loop management method is adopted,which seriously affects the efficiency ofterminal problem investigation and processing.This paper expounds the methods of checking and dealing with terminalproblems in electric power enterprisesKeywords Terminal operation and maintenance;Problem troubleshooting;Efficiency improvement1相关概念1.1信息服务工程师在ITSM系统中,信息服务工程师分为一线工程师、二线工程师和三线工程师,其中,二线工程师分为二线现场工程师和二线经理,二线现场工程师负责接收并处理ITSM系统工单,而二线经理则负责对二线现场工程师进行管理,并对ITSM系统工单进行分析。

超大规模集成电路英语Diving into the heart of modern technology, the realm of Very Large Scale Integration (VLSI) is a marvel of human ingenuity, where millions of transistors are woven togetheron a single silicon chip, creating the backbone of ourdigital world. This intricate dance of microelectronics is nothing short of a technological symphony, where each component plays a crucial role in processing information at lightning speeds. VLSI has revolutionized industries, from consumer electronics to aerospace, enabling devices that are not only smaller but also more powerful and energy-efficient than ever before.The journey of VLSI began with the quest for miniaturization, pushing the boundaries of what was thought possible. Today, it stands as a testament to human innovation, where the complexity of a circuit can be so vast that itrivals the intricacy of a city's infrastructure. The design process is a meticulous affair, involving architects of the silicon landscape who carefully plan the placement of each transistor and wire to optimize performance and reduce power consumption.As we stand on the cusp of new breakthroughs, VLSI continues to evolve, with technologies like 3D integration promising to stack layers of circuits on top of one another, further increasing the density and capabilities of these chips. The implications are profound, from enabling advancedartificial intelligence algorithms to powering the Internetof Things, where everyday objects become smart and interconnected.The future of VLSI is as bright as the circuits it powers, with ongoing research exploring new materials and designsthat could push the limits of Moore's Law. As we venture deeper into this microcosm, the potential for innovation is boundless, promising a future where the line between reality and the digital world becomes increasingly blurred. The quest for the ultimate VLSI design is not just a pursuit of technological perfection; it is a journey into the very essence of what it means to create and connect in the digital age.。

Shared Future in a New World OrderMany have been aware that the West-dominatedarchitecture of globalgovernance has been failing developing countries for some time. Both China and India are in the unique position of doing something concrete at a time of deepening global division and changing global order.The initial reaction from the G7 was not encouraging. They do not want others to shape the contours of new arrangements even though they recognize that parts of it have outlived its utility for them. Chinese President Xi Jinping has already called for a new type ofinternational relations based on win-win cooperation and put forward the Global Development Initiative, the Global Security Initiative and the Global Civilization Initiative. India has sought to give a voice to the Global South at the G20.New thinking strikes at the foundation of the current architecture.Multilateral trade rulesBy Mukul SanwalThe West is still stuck in the colonial mindset as global power while human wellbeing and digital technology are the foundation of theproductivity growth shift to Asia.10OPENING ESSAYhave been ignored as supply chains are restructured by unilateral sanctions, and countries are moving away from reliance on the U.S. dollar for trade. Efforts to ensure food security for developing countries have met resistance in the World Trade Organization (WTO). In areas ranging from energy flow to human rights, China and India have been treated unfairly compared to some Western countries with much smaller populations.The multilateral negotiating process is alsoin question. By failing to nominate members, the U.S. has unilaterally stymiedthe dispute settlementmechanism of the WTO. In other vital areas like climate change, subsequent rounds of negotiation create new issues instead of narrowing differences like linkages with trade, to the detriment of poor countries. In key areas like climate finance and technology transfer for vaccines, the gap between what is promised and what is achieved is causing deep resentment in poor countries, which are ready and willing for alternative arrangements. China and India have identified similar priorities for the 2030 Agenda for Sustainable Development. NEW ORDER REPRESENTED BY BRICSGlobal geopolitics has changed. Revitalizing BRICS is a stepping stone for reform of global governance. BRICS members are characterized as industrialized developingcountries with large andemerging economies thattogether account for over halfof the world’s population.Interest has been growingfor an alternative political-economic grouping to counterthe G7, whose influence isdeclining on the world stage.To move this process forward,the New Development Bankwas established by BRICSas a counterweight to theInternational MonetaryFund and the World Bank. Italready has several countriesoutside of BRICS involvedsuch as Bangladesh and theUnited Arab Emirates, withother countries such as Egyptand Uruguay expected to joinsoon.As the G7 over-relies onsanctions as an economicweapon, BRICS isestablishing its own financialtransaction arrangement.This is of significantinterest to sanctionedcountries, and Iran andTürkiye have submittedmembership applications.This suggests that thesecountries find BRICS to bea medium to settle theirdifferences and pursuecommon interests. Such amix of underlying ideas hasattracted expressions ofinterest from 20 countriesacross all continents. Theysee BRICS as an alternativeglobal institution not asa counterweight to othergroups but as a platform toleverage the potential toform issue-based groupings,including sharing digitaltechnologies and usingChina, India, and Asia asmodels.ASIAN CENTURYThe spread of digitaltechnologies is a globalphenomenon, but it isA send-off ceremony for three Chinese astronauts manning the Shenzhou-13 space mission at Jiuquan Satellite Launch Center in northwestern China, October 15, 2021. Chinese astronauts Zhai Zhigang (right), Wang Yaping (center), and Ye Guangfu stayed in space for about six months during the mission. (Photo by Wan Quan/China Pictorial)CHINA-INDIA DIALOGUE11The author is a former UN diplomat who has served as director in the Climate Change Secretariat.spreading in Asia atunprecedented pace and scale. In 2010, the region accounted for 52 percent of global growth in technology company revenue, 43 percent of start-up funding, and 87 percent of the world’s patent filings. Digitization of consumer markets is blurring global boundaries, and Asia is becoming more “borderless” with a less rigid industry structure than other regions. This may create more room to boost development in Asia. The phenomenon of “super apps” is much more prevalent in Asia than in Western economies. Having been pioneered in China, they have spread to India and even across the entire Asian region. By 2040, Asia is expected to represent 40 percent of globalconsumption and 52 percent of global GDP.In 2020, Asian countries produced 76 percent of the world’s science, technology, engineering, and mathematics (STEM) graduates, and Indiacontinued to produce the most computer sciencegraduates in the world, with over 200,000 a year. Asia accounts for more than 50 percent of global growth in research and development (R&D) spending and more than 80 percent of patents filed around the world. Technologies such as cloud computing, analytics, Internet of Things, and artificial intelligence (AI) are expected to grow at a rate of over 20 percent per year. Asia is characterizedby commercialization of new ideas and eventually advanced productivity growth.QUESTIONING THE WESTERN MODELThe global divide is now focused on the technology sphere and in particular on the information and communication technology (ICT) sector. China’s data-based development model has great relevance for other countries. The world’s top voice recognition start-up, China’s iFlytek, has 700 million users, almost twice the number of people who speak to Apple’s Siri. WeChat Pay’s 900 million Chinese users outnumber Apple Pay’s 44 million in the U.S. While two-thirds of Americans still rely on credit cards, 90 percent of Chinese urban residents primarily use mobile payments. Using granular data, SenseTime and Megvii have developed cutting-edge applications like instantaneous facial recognition to identify individuals from China’s population of 1.4 billion in seconds. China has increased R&D spending over the past two decades, reaching 90 percent of U.S. spending today. Last year, China overtook the U.S. in overall AI citations, andproduced four times as many STEM graduates compared to America. Moreover, it is on track to award twice as many STEM PhDs by 2025. By contrast, the number of domestic-born AI PhDs inthe U.S. has not increased since 1990.China and India provide a better developmentmodel than the U.S. At last year’s UN climate change conference, Egypt backed India’s stress on climate justice and raised questions about the relationshipbetween climate justice and social justice. The market share of the U.S. dollar in the world’s forex reserves fell to nearly 58 percent in March 2022 from 71 percent in 2001. New thinking on global governance is steadily spreading around the world. China and India have set a new model for an urbanized world by redefining global goods based on population, R&D and sharing digital technology to enhancecooperation, productivity and human wellbeing steadily.12OPENING ESSAY。

Unit 13Comparison between GSM and CDMA GSM与CDMA之比较Using CDMA/FDD technology, subscribers of CDMA cellular mobile communication system can transmit their information simultaneously through the same channel. On the other hand, the GSM system adopts TDMA/FDD method to transmit and distinguish information from different GSM mobile stations. In addition, in favor of QCELP arithmetic, RAKE receiver, power control and soft switching etc., CDMA shows more advantages in its system performance than the GSM, such as greater anti-interference capability, bigger system capacity, higher successful connection ratio, fewer off-line chances, low probability of intercept(LPI), and so on.使用码分多址/频分双工技术,用户的蜂窝移动通信系统的传输信息的同时,通过同样的渠道。
另一方面,该系统采用时分多址/频分双工传输的方法和识别信息从不同的移动台。
此外,有利于中国电信集团广州研发中心算术,耙式接收器,功率控制和软开关等,显示出更多的优势在码分多址系统性能比,如更高的抗干扰能力,更大的系统容量,连接成功率较高,离线的机会少,低截获概率(低截获概率),等。
656© Fritz Kübler GmbH, subject to errors and changes. 09/2018Optical fiber transmission modulesOptical fiber transmission system for SSI absolute encoders The system is made up of an optical fiber transmitter and an optical fiber receiver. The optical fiber transmitter converts the electrical signals of a normal absolute encoder with Synchronous Serial Interface (SSI) into a light signal for transmission by means of an optical fiber. The receiving module converts the optical signal back into electrical signals.Absolute signals can be transmitted safely through one glass fiber over distances of up to 2000 m. A rotary switch on the front side of the module allows adjusting the SSI clock between 1 and 99 bits.Simplex Patch cable ST-ST - MultimodeST Multimode couplingplus* Comparison of costs:Costs per meter standard copper cable compared to costs per meter optical fiber signal cable + costs of transmitter + costs of receiverReliable transmission• Safe signal transmission up to 2000 m.• Resists extremely strong electro-magnetic fields.Easy installation• Signal transmission via a single glass fiber.• Clock of 1 ... 99 bit can be set via rotary switch.• LED for monitoring of power supply and clock.• DIN-rail mounting – requires min. installation space – only 19 mm wide.Application areas• Process control technology and automation technology.• Crane systems.• High voltage plants.• Heavy industry.• Wind power plants.• Drive technology.• Rolling mills.657© Fritz Kübler GmbH, subject to errors and changes. 09/2018Optical fiber transmission modulesTechnical data EMCStandards Emitted interference EN 55011 class B1Immunity to interference EN 61000-6-2Terminal assignmentOptical fiber receiverPower supplyOptical fiber transmitterContacts 1/2 of the 2-pin plug-in screw terminal are connected to contacts 1/2 of the 11-pin plug-in screw terminal or with contacts 1/2 of the Sub-D connector.+V: Power supply +V DC0 V: Power supply ground GND (0 V)C+, C- : Clock signal D+, D- : Data signal H : Shield658© Fritz Kübler GmbH, subject to errors and changes. 09/2018Connection technologyDimensionsDimensions in mm [inch]。

U.S. spying, immigration dominate EUsummitTop leaders of the European Union (EU) mainly focused on the U.S. spying scandal and growing immigration concerns in the Mediterranean during a two-day summit that ended Friday in Brussels.The digital market as well as jobs and growth had been scheduled as the main topics for the summit. Instead, EU leaders spent rather limited time on those issues and only reached broad consensus on next steps for the digital economy among others.In addition, EU leaders called for maximum simplicity and minimum hassle for business, while European Commission President Jose Manuel Barroso promised to cut red tape and make regulations fit for purpose. The calls to cut red tape had been brought up by British Prime Minister David Cameron prior to the summit.TALKS WITH U.S. OVER SPYINGFrance and Germany launched an initiative of seeking talks with the United States over the alleged spying on its European allies, and all 28 EU member states agreed on the nature of the initiative, according to European Council President Herman Van Rompuy."The UK has a special relationship [with the U.S.], but they are completely on board," Van Rompuy told reporters.Both Berlin and Paris wanted to seek an agreement or an understanding with the U.S. in the field of secret service by the end of the year, while inviting all the other member states to join their initiative, Van Rompuy said at the press conference ending the summit's first day in the early hours of Friday.EU leaders expressed their conviction that the partnership must be based on respect and trust, including with respect to the work and cooperation of secret services, according to a statement adopted during the summit."A lack of trust could prejudice the necessary cooperation in the field of intelligence gathering," said the statement.On Thursday, Berlin summoned the U.S. ambassador over allegations of spying on the mobile phone of German Chancellor Angela Merkel, which was denied by the White House.Merkel said upon arrival on Thursday afternoon that the U.S. conduct of bugging her phone was "unacceptable." She had called U.S. President Barack Obama on the eve of the summit, warning of a breach of trust.Earlier this week, French President Francois Hollande had also asked for an explanation from Obama over the phone, following allegations of U.S. spying on millions of French phone calls.The fresh round of spying scandals came only months afterEuropean media reported about the U.S. national security agency' s bugging EU offices, based on the information leaked by Edward Snowden.IMMIGRATION TASK FORCEOn the second day of the summit, EU leaders vowed to tackle immigration issues in the Mediterranean with a task force, in response to a shipwreck off an Italian island that had killed hundreds in early October."Leaders all agree determined actions should be taken in order to prevent the loss of lives at sea and to avoid that such tragedies happen again," Van Rompuy told a press conference on Friday."We will return to asylum and migration in December precisely with operational conclusions," Van Rompuy added, referring to the next summit in two months.The task force would address the root causes of illegal migration flows and work with countries of origin and transit, according to the president.Van Rompuy also called on member states to swiftly implement the new European border surveillance system Eurosur and reinforce the activities of the EU's border agency Frontex in the Mediterranean.The EU would have a longer-term reflection on asylum andmigration policies next June, during its wider debate on legislative and operational work in the field of freedom, justice and security, he added."All leaders agree to share responsibility with the member states most affected by migration flows," Van Rompuy said.。

联合调控英语The term "joint regulation" refers to the coordinated efforts of multiple entities to regulate a particular industry or activity. This can involve government agencies, industry groups, and other stakeholders working together to establish and enforce rules and standards.In the context of financial regulation, joint regulation often involves multiple regulatory bodies working together to oversee the activities of banks, investment firms, and other financial institutions. This can include coordinating efforts to monitor risk, enforce compliance with regulations, and investigate potential violations.One example of joint regulation in the financial sector is the Basel Committee on Banking Supervision, which is made up of representatives from central banks and regulatory authorities from around the world. The committee works to develop and promote international standards for banking regulation, with the goal of ensuring the safety and stability of the global financial system.Another example of joint regulation is the Financial Stability Oversight Council (FSOC) in the United States. The FSOC was established in thewake of the 2008 financial crisis to coordinate the efforts of multiple regulatory agencies in identifying and addressing systemic risks to the financial system.Joint regulation can also be used in other industries, such as healthcare and environmental regulation. In these contexts, it often involves collaboration between government agencies, industry groups, and other stakeholders to establish and enforce standards for safety, quality, and environmental protection.Overall, joint regulation can be an effective way to ensure that industries are operating in a safe and responsible manner, while also promoting innovation and growth. However, it requires careful coordination and cooperation between multiple entities, and may face challenges in balancing competing interests and priorities.。
a r X i v :m a t h /0004105v 2 [m a t h .A G ] 22 J a n 2001On the multiplicity of terminal singularities onthreefoldsNobuyuki KakimiDepartment of Mathematical Sciences,University of Tokyo,Komaba,Meguro,Tokyo 153,Japan (e-mail:kakimi@318uo.ms.u-tokyo.ac.jp )Abstract.We give the multiplicity of terminal singularities on threefolds by simple calculation.Then we obtain the best inequalities for the multiplicity and the index.By using this,we can improve the boundedness number of terminal weak Q -Fano 3-folds in [KMMT,Theorem 1.2].Furthermore,we can extend [K,Theorem 3.6]for Fujita freeness conditions to nonhypersurface terminal singularities.0IntroductionOur results are the multiplicity of terminal singularities and the best inequal-ities for the multiplicity and the index of terminal singularities on threefolds.Our results are partially generalizations of Artin [A]’s result,that,for a nor-mal surface S ,a rational singular point p of S ,embdim p S =mult p S +1.We shall prove the following results in this paper:(Theorem 2.1)Let (X,p )be a 3-fold terminal singular point over C .Then,for all integers kdim m k X p /m k +1X p =mult p X ·k (k +1)/2+k +1and embdim p X =mult p X +2and mult p X ≤index p X +2(if index p X =1,then mult p X ≤2).We can improve [KMMT Theorem 1.2(2)]by (Theorem 2.1)to the fol-lowing:(Theorem 3.4)Let X be a terminal weak Q -Fano 3-fold.Then the following hold.(1)−K x ·c 2(X )≥0,and hence I (X )|24!.(2)Assume furtherthat the anti-canonical morphism g :X →¯Xdoes not contract any divisors.Then (−K X )3≤63·(2+24!).(3)The terminal Q -Fano 3-folds are bounded.We also can extend [K 3.6]by (Theorem 2.1)to the following:(Theorem 4.1)Let X be a normal projective variety of dimension 3,x 0∈X a nonhy-persurface terminal singular point for index x 0X =r ≥2,and L an ample Q -Cartier divisor such that K X +L is Cartier at x 0.Assume that there are positive numbers σp for p =1,2,3which satisfy the following conditions:(1)pr +3,and σ3>(1+1/r )3√|K X+L|is free at x0.Acknowledgment:The author would like to express his thanks to Professor Yujiro Kawamata for his advice and warm encouragement.He also would like to express his thanks to Mr.Masayuki Kawakita for teaching him RIMS-1273 [KMMT]preprint’s existence.1PreliminariesDefinition1.1.Let m X p be the maximal ideal of p of X.The embedding dimension of X at p is the dimension of the Zariski tangent space,m X pembdim p X=dim=k mult p S+1,m S k+1pand embdim p S=mult p S+1.We would like to calculate the multiplicity of terminal singularities on threefolds.We shall need the following Mori’s classification theorem of ter-minal singularities in dimension3.Theorem1.3([M]).Let0∈X be a3-fold terminal nonhypersurface sin-gular point over C.Then0∈X is isomorphic to a singularity described by the following list:(1)cA/r,{xy+f(z,u r)=0,f∈C{z,u r},(r,a)=1}⊂C4/Z r(a,r−a,r,1),(2)cAx/4,{x2+y2+f(z,u2)=0,f∈C{z,u2}}⊂C4/Z4(1,3,2,1),(3)cAx/2,{x2+y2+f(z,u)=0,f∈(z,u)4C{z,u}}⊂C4/Z2(1,2,1,1),(4)cD/2,{u2+z3+xyz+f(x,y)=0,f∈(x,y)4},or{u2+xyz+z n+f(x,y)= 0,f∈(x,y)4,n≥4},{u2+y2z+z n+f(x,y)=0,f∈(x,y)4,n≥3}⊂C4/Z2(1,1,2,1),(5)cD/3,u2+x3+y3+z3=0,or{u2+x3+yz2+f(x,y,z)=0,f∈(x,y,z)4},{u2+x3+y3+f(x,y,z)=0,f∈(x,y,z)4}⊂C4/Z3(1,2,2,3),2(6)cE/2,{u 2+x 3+g (y,z )x +h (y,z )=0,g,h ∈C {y,z },g,h ∈(y,z )4}⊂C 4/Z 2(2,1,1,1).The equations have to satisfy 2obvious conditions:1.The equations define a terminal hypersurface singularity.2.The equations are Z n -equivariant.(In fact Z n -invariant,except for cAx/4.)2Main TheoremTheorem 2.1.Let (X,p )be a 3-fold terminal singular point over C .Then,for all integers k dimm X p k2+k +1,embdim p X =mult p X +2,and mult p X ≤index p X +2(if index p X =1,then mult p X ≤2).Moreover,we assume that (X,p )∼=(xy +f (z,u r )=0⊂C 4/Z r (a,r −a,r,1),0)or (C 3/Z r (a,r −a,1),0)for (r,a )=1and r >1.Let r i :=min {r i −1−a i −1,a i −1}(r 0>r 1>···>r n =1)and a i =r i −1(mod r i )for r 0=r ,a 0=a .Then,mult p X =⌊r 0r 2⌋+···+⌊r n −1m k +1X p=2(k +2)(k +1)2+k +1.Hence mult p X =2and embdim p X =mult p X +2=4.Case 2.Let (X,p )be a terminal quotient singular point of typeC 3/Z r (a,−a,1)with (r,a )=1Let S i =C 2/Z r (i,1)for i =a,−a .For i =a,−a ,we have (xy )w ·m k −w Si pm k +1X pandm k −wSa pm k −w +1S −a p=(z r )k −w for 0≤w ≤k.3Then by Theorem 1.2,dimm X k pm S a k −w +1p+dimm S −a k −wp2+k +1.Hence,mult p X =mult p S a +mult p S −a and embdim p X =mult p X +2.Since we haver ir i +1⌋+1)−r i +1−a i +1r i +1⌋−1+mult p C 2/Z r i +1(r i +1−a i +1,1).Since we have thatr ir i −r i +1,thatr i −r i +1r i −2r i +1,···,and thatr i −(⌊r i /r i +1⌋−2)r i +1r i −(⌊r i /r i +1⌋−1)r i +1,then mult p C 2/Z r i (r i −r i +1,1)=1+mult p C 2/Z r i +1(a i +1,1).Thus mult p C 2/Z r i (r i +1,1)+mult p C 2/Z r i (r i −r i +1,1)=⌊r i /r i +1⌋+mult p C 2/Z r i +1(r i +2,1)+mult p C 2/Z r i +1(r i +1−r i +2,1).Hnece,mult p X =⌊r 0r 2⌋+···+⌊r n −1m S i k −w +1p∈m k X pm S a k −w +1p∩m S −a k −wpThe rest of the proof is the same as Case2.Hence,embdim p X=mult p X+2,mult p X=⌊r0r2⌋+···+⌊r n−1m X k+1p =kt=0{(2k−2t+1)+(2k−2t)+(k−t)+(k−t)} =kt=0(6k−6t+1)=6k(k+1)m X k+1p =ks=0(2k−2s+1)+k−1t=0(2k−2t)=4k(k+1)m X k+1p =kt=0(k−t+1)+k−1t=0(k−t+3)+k−2t=0k−t−2s=03=12·k(k+7)+32+k+1.Hence mult p X=index p X+2=5and embdim p X=mult p X+2=7.5We give the following concrete example:Example2.2.Let(X,p)be a quotient singular point of type C3/Z13(5,8,1). Then,mult p X=[(13/5)]+[(5/2)]+[(2/1)]+2=8.Theorem2.1is wrong on the following canonical singularity on threefolds. Example2.3.Let(X,p)be a quotient singular point of type C3/Z3(1,1,1). We have mult p X=9and embdim p X=10Then,embdim p X=10< mult p X+2=11and mult p X=9>index p X+2=5.3Application1We can improve the boundedness number in[KMMT,Theorem1.2(2)]by Theorem2.1.Definition3.1(KMMT Theorem1.2).Let X be a normal projective variety and X is called a terminal(resp.klt)Q-Fano variety,if X has only terminal singularities and−K X is ample.By replacing’ample’with’nef and big’,terminal(resp.klt)weak Q-Fano varieties are similarly defined.Let I(X)be the smallest positive integer I such that IK X is Cartier;I(X)is called the Gorenstein index of X.We note that if X is a klt Q-Fano variety then|−mK X|is free for some m>0.The induced birational morphism X→¯X is said to be the anti-canonical morphism of X.Lemma3.2([KMMT Lemma4.1]).Let X be an n-dimensional projec-tive variety and x a closed point with multiplicity r.Let D be a nef and big Q-Cartier divisor on X and l a covering family of curves containing x such that D·l≤d.Then D n≤rd n.The following is our improvement for[KMMT Theorem5.1]. Theorem3.3.Let X be a Q-factorial terminal Q-Fano3-fold withρ(X)= 1.Then(−K X)3≤63·(2+24!).Proof.(cf.[KMMT Theorem5.1])By[MM86,Thm.5],there is a covering family of rational curves{l}such that−K X·l≤6.If{l}has afixed point x,then Lemma3.2,we have(−K X)3≤63·mult x X.We have mult x X≤2+index x X.By[KMMT Theorem1.2(1)],we have index x X≤24!.Hence(−K X)3≤63·(2+24!)in this case.6If{l}has afixed point x,the proof is the same as the one of[KMM92a, Theorem.].By[KMMT,Construction-Proposition4.4and Claim5.2],there is a cov-ering family of rational curves{l′}with afixed point x such that−K X·{l′}≤3×6.Hence by Lemma3.2,(−K X)3≤63·33in this case.The following is our improvement for[KMMT Theorem1.2].Theorem3.4.Let X be a terminal weak Q-Fano3-fold.Then the following hold.(1)−K x·c2(X)≥0,and hence I(X)|24!.(2)Assume further that the anti-canonical morphism g:X→¯X does not contract any divisors.Then (−K X)3≤63·(2+24!).(3)The terminal Q-Fano3-folds are bounded. Proof.The proof is the same as the one of[KMMT Theorem1.2]except that we can use Theorem3.3instead of[KMMT Theorem5.1].4Application2We can extend[K,Theorem3.6]to nonhypersurface terminal singularities in the following.Theorem4.1.Let X be a normal projective variety of dimension3,x0∈XX=r≥2,and L an a nonhypersurface terminal singular point for index xample Q-Cartier divisor such that K X+L is Cartier at x0.Assume that there are positive numbersσp for p=1,2,3which satisfy the following conditions: (1)p√r+3,andσ3>(1+1/r)3[K]N.Kakimi:Freeness of adjoint linear systems on threefolds with terminal Gorenstein singularities or some quotient singularities.J.Math.Sci.Univ.Tokyo.7(2000)347–368[Ka1]Y.Kawamata:On the plurigenera of minimal algebraic3-folds with K≡0.Math.Ann.275(1986)539–546[Ka2]Y.Kawamata:Boundedness of Q-Fano threefolds.Proc.Int.Conf.Algebra,Contemp.Math.131Amer.Math.Soc.Providence,RI(1992)439–445[Ka3]Y.Kawamata:The minimal discrepancy of a3-fold terminal sin-gularity,appendix to“3-folds logflips”by V.V.Shokurov.RussianAcad.Sci.Izv.Math.40(1993)201–203[Ka4]Y.Kawamata:Divisorial contractions to3-dimensional termi-nal quotient singularities.Higher Dimensional complex Varieties(Proc.Trento),Walter de Gruyter J(1996)241–246[KMM]Y.Kawamata,K.Matsuda,and K.Matsuki:Introduction to the minimal model problem.Adv.St.Pure Math.10(1987)283–360[KMMT]J.Koll´a r,Y.Miyaoka,S.Mori,and H.Takagi:Boundedness of canonical Q-Fano3-folds.RIMS-1273preprint[KSB]J.Koll´a r and N.Shepherd-Barron:Threefolds and deformations of surface singularities,Invent.Math.91(1998)299–338[M]S.Mori:On3-dimensional terminal singularities,Nagoya Math.J.98(1985)43–66[MM]Y.Miyaoka and S.Mori:A numerical criterion for uniruledness, Ann.of Math.124(1986)65–69[R]M.Reid:Young person’s guide to canonical singularities.Algebraic Geometry,Bowdoin,1985,Proc.Symp.Pure Math.46(1987)345–4148。