puppet自定义facter说明
- 格式:doc
- 大小:28.50 KB
- 文档页数:2

详解Puppeteer⼊门教程1、Puppeteer 简介Puppeteer 是⼀个node库,他提供了⼀组⽤来操纵Chrome的API, 通俗来说就是⼀个 headless chrome浏览器 (当然你也可以配置成有UI的,默认是没有的)。
既然是浏览器,那么我们⼿⼯可以在浏览器上做的事情 Puppeteer 都能胜任, 另外,Puppeteer 翻译成中⽂是”⽊偶”意思,所以听名字就知道,操纵起来很⽅便,你可以很⽅便的操纵她去实现:1)⽣成⽹页截图或者 PDF2)⾼级爬⾍,可以爬取⼤量异步渲染内容的⽹页3)模拟键盘输⼊、表单⾃动提交、登录⽹页等,实现 UI ⾃动化测试4)捕获站点的时间线,以便追踪你的⽹站,帮助分析⽹站性能问题如果你⽤过 PhantomJS 的话,你会发现她们有点类似,但Puppeteer是Chrome官⽅团队进⾏维护的,⽤俗话说就是”有娘家的⼈“,前景更好。
2、运⾏环境查看 Puppeteer 的官⽅ API 你会发现满屏的 async, await 之类,这些都是 ES7 的规范,所以你需要:1. Nodejs 的版本不能低于 v7.6.0, 需要⽀持 async, await.2. 需要最新的 chrome driver, 这个你在通过 npm 安装 Puppeteer 的时候系统会⾃动下载的npm install puppeteer --save3、基本⽤法先开看看官⽅的⼊门的 DEMOconst puppeteer = require('puppeteer');(async () => {const browser = await unch();const page = await browser.newPage();await page.goto('https://');await page.screenshot({path: 'example.png'});await browser.close();})();上⾯这段代码就实现了⽹页截图,先⼤概解读⼀下上⾯⼏⾏代码:1. 先通过 unch() 创建⼀个浏览器实例 Browser 对象2. 然后通过 Browser 对象创建页⾯ Page 对象3. 然后 page.goto() 跳转到指定的页⾯4. 调⽤ page.screenshot() 对页⾯进⾏截图5. 关闭浏览器是不是觉得好简单?反正我是觉得⽐ PhantomJS 简单,⾄于跟 selenium-webdriver ⽐起来,那更不⽤说了。

开源自动化配置管理工具P u p p e t入门教程系统管理员经常陷入一系列的重复任务中:如升级软件包、管理配置文件、系统服务、cron任务以及添加新的配置、修复错误等。
这些任务通常是重复低效的,解决这类任务的第一反应是让他们自动化,于是出现了定制脚本。
由于环境复杂,定制脚本和应用程序一再被重复开发,并且很难适合多种平台,灵活性和功能也很难保证,于是像Puppet这样的自动化配置管理工具便出现了。
在开源世界里,有很多配置工具可供选择,这个领域一些关键的产品有:Puppet():Ruby写成的配置管理工具,使用C/S架构,使用declarative language配置客户端。
Cfengine():最先发布的开源配置工具之一,1993年发布,同样是C/S架构,通常应用于教育机构。
LCFG():C/S架构的配置管理工具,使用XML定义配置。
Bcfg2Python编写的C/S架构的配置管理工具,使用规格书和客户机响应配置目标主机。
本文档致力于描述使用Puppet管理你的主机、应用程序、后台程序和各种服务。
Puppet简介:1. Puppet的用途Puppet是开源的基于Ruby的系统配置管理工具,依赖于C/S的部署架构。
主要开发者是Luke Kanies,遵循GPLv2版权协议。
从1997年开始Kanies参与UNIX的系统管理工作,Puppet的开发源于这些经验。
因为对已有的配置工具不甚满意,从2001年到2005年间,Kanies开始在Reductive实验室从事工具的开发。
很快,Reductive实验室发布了他们的旗舰产品——Puppet。
2. Pupput的特性许多系统配置管理工具工作的方式非常类似,如cfengine。
是什么让Puppet与众不同Puppet的语法允许你创建一个单独脚本,用来在你所有的目标主机上建立一个用户。
所有的目标主机会依次使用适用于本地系统的语法解释和执行这个模块。
举例:如果这个配置是在Red Hat服务器上执行,建立用户使用useradd命令;如果这个配置是在FreeBSD主机上执行,使用的是adduser命令。

About the T utorialPuppet is a configuration management technology to manage the infrastructure on physical or virtual machines. It is an open-source software configuration management tool developed using Ruby which helps in managing complex infrastructure on the fly.This tutorial will help in understanding the building blocks of Puppet and how it works in an infrastructure environment. All the examples and code snippets used in this tutorial are tested. The working code snippets can be simply used in any Puppet setup by changing the current defined names and variables.AudienceThis tutorial has been prepared for those who want to understand the features and functionality of Puppet and how it can help in reducing the complexity of managing an infrastructure.After completing this tutorial one would gain moderate level understanding of Puppet and its workflow. It will also give you a fair idea on how to configure Puppet in a preconfigured infrastructure and use it for automation.PrerequisitesWe assume anyone who wants to understand and learn Puppet should have an understanding of the system administration, infrastructure, and network protocol communication. To automate the infrastructure provisioning, one should have a command over basic Ruby script writing and the underlying system where one wants to use Puppet. Copyright & DisclaimerCopyright 2018 by Tutorials Point (I) Pvt. Ltd.All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher.We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. If you discover any errors on our website or in this tutorial, please notify us at **************************T able of ContentsAbout the Tutorial (i)Audience (i)Prerequisites (i)Copyright & Disclaimer (i)Table of Contents (ii)BASIC PUPPET (1)1.Puppet ─ Overview (2)Features of Puppet System (2)Pupp et ─ Workflow (3)Puppet ─ Key Components (4)2.Puppet ─ Architecture (6)3.Puppet ─ Installation (8)Prerequisites (8)Facter Installation (8)4.Puppet ─ Configuration (10)Open Firewall Ports on Machines (10)Configuration File (10)Key Components of Config File (12)5.Puppet ─ Environment Conf (14)Allowed Settings (15)6.Puppet ─ Master (17)Prerequisites (17)Creating Puppet Master Server (17)Installing NTP (17)Setup Puppet Server Software (19)Configure Memory Allocation on the Puppet Server (19)7.Puppet – Agent Setup (21)8.P uppet ─ SSL Sign Certificate Setup (22)9.Puppet – Installing & Configuring r10K (24)10.Puppet – Validating Puppet Setup (26)Setting Up the Virtual Machine (26)Validating Multiple Machine Configuration (28)11.Puppet – Coding Style (30)Fundamental Units (30)Metaparameters (31)Resource Collections (32)Run Stages (35)Advanced Supported Features (38)Capitalization (38)Arrays (39)Variables (39)Conditionals (41)If-Else Statement (42)Virtual Resource (43)Comments (43)Operator Precedence (44)Working with Templates (46)Defining and Triggering Services (46)12.Puppet – Manifest Files (47)Manifest File Workflow (47)Writing Manifests (48)13.Puppet ─ Module (50)Module Configuration (50)Modules Source (50)Module Naming (51)Module Internal Organization (51)Module Lookup (53)14.Puppet – File Server (54)File Format (54)Security (55)15.Puppet – Facter & Facts (57)Puppet Facts (58)Custom Facts (62)Using FACTERLIB (64)External Facts (65)ADVANCED PUPPET (67)16.Puppet – Resource (68)Resource Type (68)Resource Title (70)Attributes & Values (71)17.Puppet – Resource Abstraction Layer (77)18.Puppet ─ Template (85)Evaluating Templates (85)Using Templates (85)19.Puppet ─ Classes (90)Parameterized Class (92)20.Puppet ─ Function (94)File Function (94)Include Function (94)Defined Function (95)21.Puppet – Custom Functions (96)Writing Custom Functions (96)Location to Put Custom Function (96)Creating a New Function (97)22.Puppet ─ Environment (98)Using the Environment on Puppet Master (98)Setting the Clients Environment (99)Puppet Search Path (100)23.Puppet – Type & Provider (101)24.Puppet – RESTful API (105)REST API Security (105)Puppet Master API Reference (106)Puppet Agent API Reference (107)25.Puppet – Live Project (108)Creating a New Module (108)Installing a HTTP Server (108)Running the httpd Server (110)Configuring httpd Server (111)Configuring the Firewall (113)Configuring the SELinux (115)Copying HTML Files in the Web Host (116)Basic Puppet1Puppet 2Puppet is a configuration management tool developed by Puppet Labs in order to automate infrastructure management and configuration. Puppet is a very powerful tool which helps in the concept of Infrastructure as code. This tool is written in Ruby DSL language that helps in converting a complete infrastructure in code format, which can be easily managed and configured.Puppet follows client-server model, where one machine in any cluster acts as client known as puppet master and the other acts as server known as slave on nodes. Puppet has the capability to manage any system from scratch, starting from initial configuration till end-of-life of any particular machine.Features of Puppet SystemFollowing are the most important features of Puppet.IdempotencyPuppet supports Idempotency which makes it unique. Similar to Chef, in Puppet, one can safely run the same set of configuration multiple times on the same machine. In this flow, Puppet checks for the current status of the target machine and will only make changes when there is any specific change in the configuration.Idempotency helps in managing any particular machine throughout its lifecycle starting from the creation of machine, configurational changes in the machine, till the end-of-life. Puppet Idempotency feature is very helpful in keeping the machine updated for years rather than rebuilding the same machine multiple times, when there is any configurational change.Cross-platformIn Puppet, with the help of Resource Abstraction Layer (RAL) which uses Puppet resources, one can target the specified configuration of system without worrying about the implementation details and how the configuration command will work inside the system, which are defined in the underlying configuration file.1.Puppet ─ WorkflowPuppet uses the following workflow to apply configuration on the system.∙In Puppet, the first thing what the Puppet master does is to collect the details of the target machine. Using the factor which is present on all Puppet nodes (similar to Ohai in Chef) it gets all the machine level configuration details. These details are collected and sent back to the Puppet master.∙Then the puppet master compares the retrieved configuration with defined configuration details, and with the defined configuration it creates a catalog and sends it to the targeted Puppet agents.∙The Puppet agent then applies those configurations to get the system into a desired state.∙Finally, once one has the target node in a desired state, it sends a report back to the Puppet master, which helps the Puppet master in understanding where thecurrent state of the system is, as defined in the catalog.3Puppet ─ Key ComponentsFollowing are the key components of Puppet.Puppet ResourcesPuppet resources are the key components for modeling any particular machine. These resources have their own implementation model. Puppet uses the same model to get any particular resource in the desired state.ProvidersProviders are basically fulfillers of any particular resource used in Puppet. For example, the package type ‘apt-get’ and ‘yum’ both are valid for package management. Some times, more than one provider would be available on a particular platform. Though each platform always have a default provider.ManifestManifest is a collection of resources which are coupled inside the function or classes to configure any target system. They contain a set of Ruby code in order to configure a system.4ModulesModule is the key building block of Puppet, which can be defined as a collection of resources, files, templates, etc. They can be easily distributed among different kinds of OS being defined that they are of the same flavor. As they can be easily distributed, one module can be used multiple times with the same configuration.TemplatesTemplates use Ruby expressions to define the customized content and variable input. They are used to develop custom content. Templates are defined in manifests and are copied to a location on the system. For example, if one wants to define httpd with a customizable port, then it can be done using the following expression.The httpd_port variable in this case is defined in the manifest that references this template.Static FilesStatic files can be defined as a general file which are sometimes required to perform specific tasks. They can be simply copied from one location to another using Puppet. All static files are located inside the files directory of any module. Any manipulation of the file in a manifest is done using the file resource.5Puppet6Following is the diagrammatic representation of Puppet architecture.Puppet MasterPuppet Master is the key mechanism which handles all the configuration related stuff. It applies the configuration to nodes using the Puppet agent.Puppet AgentPuppet Agents are the actual working machines which are managed by the Puppet master. They have the Puppet agent daemon service running inside them.Config RepositoryThis is the repo where all nodes and server-related configurations are saved and pulled when required.2. Puppet ─ ArchitecturePuppetFactsFacts are the details related to the node or the master machine, which are basically used for analyzing the current status of any node. On the basis of facts, changes are done on any target machine. There are pre-defined and custom facts in Puppet.CatalogAll the manifest files or configuration which are written in Puppet are first converted to a compiled format called catalog and later those catalogs are applied on the target machine.7Puppet8Puppet works on the client server architecture, wherein we call the server as the Puppet master and the client as the Puppet node. This setup is achieved by installing Puppet on both the client and well as on all the server machines.For most of the platforms, Puppet can be installed via the package manager of choice. However, for few platforms it can be done by installing the tarball or RubyGems .PrerequisitesFactor is the only pre-requisite that does not come along with the standard package edition of Puppet. This is similar to Ohai which is present in Chef.Standard OS LibraryWe need to have standard set of library of any underlying OS. Remaining all the system comes along with Ruby 1.8.2 + versions. Following is the list of library items, which an OS should consist of.∙ base64 ∙ cgi∙ digest/md5 ∙ etc ∙ fileutils ∙ ipaddr ∙ openssl ∙ strscan ∙ syslog ∙ uri ∙ webrick ∙ webrick/https ∙xmlrpcFacter InstallationAs discussed, the facter does not come along with the standard edition of Ruby. So, in order to get the facter in the target system one needs to install it manually from the source as the facter library is a pre-requisite of Puppet.This package is available for multiple platforms however just to be on the safer side it can be installed using tarball , which helps in getting the latest version.3.Puppet First, download the tarball from the official site of Puppet using the wget utility.Next, un-tar the tar file. Get inside the untarred directory using the CD command. Finally, install the facter using install.rb file present inside the facter directory.Installing Puppet from the SourceFirst, install the Puppet tarball from the Puppet site using wget. Then, extract the tarball to a target location. Move inside the created directory using the CD command. Using install.rb file, install Puppet on the underlying server.Installing Puppet and Facter Using Ruby Gem9Puppet10Once we have Puppet installed on the system, the next step is to configure it to perform certain initial operations.Open Firewall Ports on MachinesTo make the Puppet server manage the clie nt’s server centrally, one needs to open a specified port on all the machines, i.e. 8140 can be used if it is not in use in any of the machines which we are trying to configure. We need to enable both TCP and UDP communication on all the machines.Configuration FileThe main configuration file for Puppet is etc/puppet/puppet.conf . All the configuration files get created in a package-based configuration of Puppet. Most of the configuration which is required to configure Puppet is kept in these files and once the Puppet run takes place, it picks up those configurations automatically. However, for some specific tasks such as configuring a web server or an external Certificate Authority (CA), Puppet has separate configuration for files and settings.Server configuration files are located in conf.d directory which is also known as the Puppet master. These files are by default located under /etc/puppetlabs/puppetserver/conf.d path. These config files are in HOCON format, which keeps the basic structure of JSON but it is more readable. When the Puppet startup takes place it picks up all .cong files from conf.d directory and uses them for making any configurational changes. Any changes in these files only takes place when the server is restarted.List File and Settings File∙ global.conf ∙ webserver.conf ∙ web-routes.conf ∙ puppetserver.conf ∙ auth.conf∙ master.conf (deprecated) ∙ca.conf (deprecated)There are different configuration files in Puppet which are specific to each component in Puppet.4.Puppet.confPuppet.conf file is P uppet’s main config uration file. Puppet uses the same configuration file to configure all the required Puppet command and services. All Puppet related settings such as the definition of Puppet master, Puppet agent, Puppet apply and certificates are defined in this file. Puppet can refer them as per requirement.The config file resembles a standard ini file wherein the settings can go into the specific application section of the main section.Main Config SectionPuppet Master Config FileDetail OverviewIn Puppet configuration, the file which is going to be used has multiple configuration sections wherein each section has different kinds of multiple number of settings.11Config SectionPuppet configuration file mainly consists of the following config sections.∙Main: This is known as the global section which is used by all the commands and services in Puppet. One defines the default values in the main section which canbe overridden by any section present in puppet.conf file.∙Master: This section is referred by Puppet master service and Puppet cert command.∙Agent: This section is referred by Puppet agent service.∙User: It is mostly used by Puppet apply command as well as many of the less common commands.Key Components of Config FileFollowing are the key components of Config file.Comment LinesIn Puppet, any comment line starts with (#) sign. This may intend with any amount of space. We can have a partial comment as well within the same line.Settings LinesSettings line must consist of -∙Any amount of leading space (optional)∙Name of the settings∙An equals = to sign, which may be surrounded by any number of space∙ A value for the settingSetting VariablesIn most of the cases, the value of settings will be a single word but in some special cases, there are few special values.1213PathsIn configuration file settings, take a list of directories. While defining these directories, one should keep in mind that they should be separated by the system path separator character, which is (:) in *nix platforms and semicolons (;) on Windows.In the definition, the file directory which is listed first is scanned and then later moves to the other directory in the list, if it doesn’t find one.Files and DirectoriesAll the settings that take a single file or directory can acceptan optional hash of permissions. When the server is starting up, Puppet will enforce those files or directories in the list.In the above code, the allowed hash are owner, group, and mode. There are only two valid values of the owner and group keys.End of ebook previewIf you liked what you saw…Buy it from our store @ https://14。

playwright codegen 自定义方法要在Playwright Codegen中自定义方法,可以按照以下步骤操作:1. 打开Playwright Codegen的终端界面或命令行界面。
2. 使用以下命令启动Playwright Codegen:`npx playwright codegen`。
3. 导航到你想要自定义方法的页面。
4. 在页面上执行你想要自定义的操作。
例如,点击按钮、填写表单或获取元素属性等。
5. 执行操作时,在Playwright Codegen终端界面或命令行界面上,你会看到生成的代码。
这段代码是你自定义方法的基础。
6. 打开Playwright的文档(https://playwright.dev/docs/api/class-page)以获取页面类(`Page`)的更多方法和属性。
7. 在生成的代码中找到适当的位置,添加你自定义的方法。
8. 编辑自定义方法的逻辑和参数,使其符合你的需求。
9. 保存并退出编辑器。
10. 现在,你可以使用自定义的方法来产生你需要的行为。
例如,以下是一个在Playwright Codegen中自定义的方法的示例:```javascript// 原始生成的代码await page.click('input[type="submit"]');// 自定义方法async function clickSubmitButton() {await page.click('input[type="submit"]');}// 更新后的代码await clickSubmitButton();```通过这种方法,你可以自定义出许多在Playwright Codegen中没有直接生成的方法,以满足你的测试需求。

angular⾃定义指令详解指令(directive)是angular⾥⾯最核⼼也是最难懂的东西,在慕课⽹看了下⼤漠穷秋⽼湿的视频,⾃⼰百度半天做了⼀些⼩test,总算把⼀切都搞明⽩了。
先列出学习来源:指令中controller和link的区别:angular视频教程:指令中的隔离 Scope :angular学习笔记:⼀、指令的创建:⾸先你得先创建⼀个module:var module1 = angular.module('module1',[]);angular.bootstrap(document.body,['module1']);然后你还得有⼀个对应的controller:var module1 = angular.module('module1',[]);module1.controller('ctl1', function($scope) {$scope.content = 'i\'m, module 1';$ = 'module1';$scope.save = function() {console.log('is function save');};});angular.bootstrap(document.body,['module1']);然后你就可以安⼼的创建指令了:// 衔接上⾯的代码m1.directive('testDirective', function() {// 将对象return出去return{restrict: 'E',// 指令类型 E:element A:attribute M:comment C: classtemplate: '<div>我是指令⽣成的内容</div>';replace: true, //使⽤模板替换原始标记指令内原本的数据将被清空}});angular.bootstrap(document.body,['module1']);对应的html可以这样写:<body><div ng-controller="ctl1">{{content}}<test-directive>这是原本的内容</test-directive></div></body>以上代码需要注意⼀下⼏点:1.我们定义的指令名称是testDirective,但是在html中要写成test-directive。
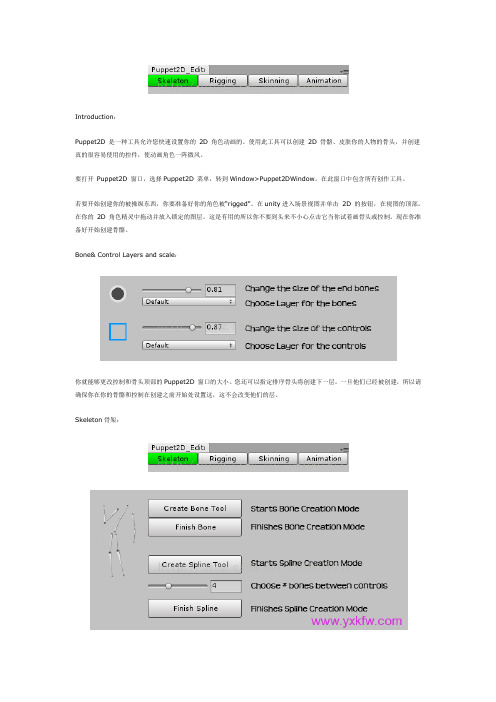
Introduction:Puppet2D 是一种工具允许您快速设置你的2D 角色动画的。
使用此工具可以创建2D 骨骼、皮肤你的人物的骨头,并创建真的很容易使用的控件,使动画角色一阵微风。
要打开Puppet2D 窗口,选择Puppet2D 菜单,转到Window>Puppet2DWindow。
在此窗口中包含所有创作工具。
若要开始创建你的被操纵东西,你要准备好你的角色被“rigged”。
在unity进入场景视图并单击2D 的按钮,在视图的顶部。
在你的2D 角色精灵中拖动并放入锁定的图层。
这是有用的所以你不要到头来不小心点击它当你试着画骨头或控制。
现在你准备好开始创建骨骼。
Bone& Control Layers and scale:你就能够更改控制和骨头顶部的Puppet2D 窗口的大小。
您还可以指定排序骨头将创建下一层。
一旦他们已经被创建,所以请确保你在你的骨骼和控制在创建之前开始处设置这,这不会改变他们的层。
Skeleton骨架:BoneCreation:骨骼是将控制你的小木偶是如何移动的支点。
若要开始创建一根骨头,请单击“Create Bone Tool”按钮。
这会设置你中骨创建模式。
你会留在这种模式下,直到您按输入或单击“Finish Bone”按钮。
2D 视图中开始使用鼠标左键,你会开始绘图的骨头。
每个骨骼会到父级无论您选择了。
Create Bone Tool按钮——开始创建骨骼鼠标左键单击——绘制的骨头退格键——删除选定的骨骼按住shift 键——移动选定的骨骼只按住ctrl 键——移动选定的骨骼和它的孩子Alt 单击鼠标左键——选定的骨骼和它的孩子之间插入骨单击鼠标右键——取消选择骨骼按enter 键/点击“Finish Bone”———–完成在中创建的骨头。
SplineCreation:这是一种特殊的表现为一条贝塞尔曲线的骨链。
当您绘制的控件而不是骨头,它是比正常骨骼以不同的方式创建。

activitimodeler任务节点⾃定义属性扩展 在⼯作中使⽤Activiti modeler时难免会遇到局限,如usertask中的属性,完全不够⽤,这时需要我们去扩展。
activiti modeler通过读取stencilset.json⽣成编辑器UI,在界⾯上的扩展需要了解stencilset.json配置⽂件,它定义元素的属性,规则的配置⽂件,页⾯的展⽰就是根据这个配置⽂件⽣成的。
配置⽂件说明:--属性的定义"propertyPackages" : [ {"name" : "process_idpackage","properties" : [ {"id" : "name", ---id"type" : "String", --类型,在赋值的时候会根据类型展⽰各种输⼊框,根据properties.js"title" : "名称", --显⽰的标题"value" : "", --值"description" : "BPMN元素的描述性名称.", --描述"category":"property", --分类,空的话位popular"popular" : true, --是否显⽰"refToView" : "text_name" --触发svg⾥⾯的效果}]--节点的定义"type" : "node","id" : "MailTask","title" : "邮件任务",--标题"description" : "邮件任务", --描述"view" : "<?xml version=\"1.0\" encoding=\"UTF-8\" standalone=\"no\"?>\n</svg>", --svg的xml"icon" : "activity/list/type.send.png", --图标"groups" : [ "任务" ], --归属的组"propertyPackages" : [ "overrideidpackage" ],--属性"hiddenPropertyPackages" : [ ],"roles" : [ "Activity" ] --规则配置步骤说明: 在stencilset.json⽂件中添加属性(各种类型可参照其它属性编写),如图: 并引⽤到UserTask节点中,如图: 这样,ORYX Designer会⾃动解析该JSON⽂件并在UI中展⽰新添加的属性,如图: 接着,我们需要将UI上扩展的属性与activiti进⾏绑定。

Puppet自动化配置管理教程第一章:什么是PuppetPuppet是一种开源的自动化配置管理工具,用于统一管理和自动化配置大规模的IT基础架构。
Puppet通过对服务器和网络设备进行配置管理,实现了快速部署和变更管理的一体化解决方案。
它使用声明式语言和基于模块的方法来描述和管理设备配置,从而提高了系统管理效率和一致性。
第二章:Puppet架构Puppet的架构由三个组件组成:Puppet Master、Puppet Agent 和PuppetDB。
Puppet Master是Puppet的主控节点,负责管理配置和策略,并将它们传送给Puppet Agent。
Puppet Agent是在被管理的节点上运行的代理程序,它执行从Puppet Master下载的配置,并将节点信息反馈给Puppet Master。
PuppetDB是一个数据库,用于存储Puppet Master和Puppet Agent之间的通信数据。
第三章:安装和配置Puppet安装Puppet非常简单,只需下载并安装Puppet Master和Puppet Agent的软件包即可。
配置Puppet Master包括指定节点、制定配置策略、创建模块等。
配置Puppet Agent包括指定Puppet Master的地址、执行更新的时间间隔等。
通过正确的设置配置文件,Puppet Master和Puppet Agent之间就可以进行通信了。
第四章:使用Puppet编写配置策略Puppet使用自定义的声明式语言来描述配置策略。
通过编写Puppet配置文件,可以定义节点的配置要求、服务的安装和启动、文件的权限和内容等。
Puppet提供了丰富的资源类型和函数,可以满足各种配置需求。
编写配置策略时,需要考虑节点之间的依赖关系和执行顺序,确保配置的一致性和稳定性。
第五章:模块化管理和重用Puppet通过模块化管理的方式提高了配置管理的可重用性和扩展性。

The Z9332F-ON 100/400GbE fixed switch comprises Dell Technologies’ latest disaggregated hardware and software data center networking solutions, providing state-of-the-art, high-density 100/400 GbE ports and a broad range of functionality to meet the growing demands of today’s data center environment. This innovative, next-generation open networking high-density aggregation switch offers optimum flexibility and cost-effectiveness for the web 2.0, enterprise, mid-market and cloud service provider with demanding compute and storage traffic environments.The compact PowerSwitch Z9332F-ON provides industry-leading density of either 32 ports of 400GbE in QSFP56-DD form factor or 128 ports of 100 or up to 144 ports of 10/25/501 (via breakout), in a 1RU design.Using industry-leading hardware and a choice of Dell EMC SmartFabric OS10 or select 3rd party network operating systems and tools, theZ9332F-ON switch incorporates multiple architectural features that optimize data center network flexibility, efficiency and availability, including IO panel to PSU airflow or PSU to IO panel airflow* for hot/ cold aisle environments, redundant, hot-swappable power supplies and fans and delivers non-blocking performance for workloads sensitive to packet loss. The compact Z9332F-ON model provides multi-rate speed, enabling denser footprints and simplifying migration to 400Gbps.Priority-based flow control (PFC), data center bridge exchange (DCBX) and enhanced transmission selection (ETS) make the Z9332F-ON ideally suited for DCB environments.The Dell EMC PowerSwitch Z9332F-ON switch supports the open source Open Network Install Environment (ONIE) for zero touch installation of Dell EMC SmartFabric OS10 networking operating system, as well as of alternative network operating systems.Key applications• Organizations looking to enter the software-defined data center era with a choice of networking technologies designed to maximize flexibility• High-density multi-rate 100/400GbE ToR server aggregation in high-performance data center environments at the desired fabric speed• Small-scale Fabric implementation via the Z9332F-ON switch in leaf and spine along with S-Series 10/25/40/50/100GbE ToR switches enabling cost-effective aggregation of 100/400 uplinks• High-density 10/25/40/50/100GbE ToR server access in high-performance data center environments • Multi-functional 10/25/40/50/100/400GbE switching in High Performance Computing Clusters or other business-sensitivedeployments requiring the highest bandwidth.• iSCSI and FCOE deployment, including DCB converged lossless transactionsKey features• 1RU high-density 100/400GbE aggregation switch with up to 32 ports of 400GbE (QSFP56-DD) or up to 128 ports of 100GbE or up to 144 ports of 10/25/50GbE1 (using breakout cable)• Multi-rate 400GbE ports support 10/25/40/50/100GbE. 40GbE ports support 10/40GbE• Scalable L2 and L3 Ethernet switching with QoS and a full comple-ment of standards-based IPv4 and IPv6 features, including OSPFand BGP routing support• 25.6Tbps non-blocking (full duplex), switching fabric delivers line-rate performance under full load on Z9332F-ON• L2 multipath support via Virtual Link Trunking (VLT) and Routed VLT support• Support for Dell EMC SmartFabric OS10• Converged network support for DCB, with priority flow control (802.1Qbb), ETS (802.1Qaz), DCBx and iSCSI TLV support• Z9332F-ON supports Routable RoCE to enable convergence of compute and storage on Active Fabric• IO panel to PSU airflow or PSU to IO panel airflow*• Redundant, hot-swappable power supplies and fans• Supports the open source Open Network Install Environment (ONIE) for zero touch installation of alternate network operating systems• Accelerated mounting kits reducing time and resources for switch rack installation• Power-efficient operation up to 45°C helping reduce cooling costs in temperature-constrained deploymentsDELL EMC POWERSWITCH Z9332F-ON SERIES SWITCHHigh-performance, high-density open networking 400GbE multi rate aggregation switch 1 50G breakout is a future release featureKey features with Dell EMC SmartFabric OS10• Consistent DevOps framework across compute, storage and networking elements• Standard networking features, interfaces and scripting functions for legacy network operations integration• Standards-based switching hardware abstraction via Switch Abstraction Interface (SAI)• Pervasive, unrestricted developer environment via Control Plane Services (CPS)• Dell EMC SmartFabric OS10 software enables Dell T echnologies’ Layer 2 and 3 switching and routing protocols with integrated IPservices, quality of service, manageability and automation features • Increase VM Mobility region by stretching L2 VLAN within or across two DCs with unique VLT capabilities• Scalable L2 and L3 Ethernet Switching with QoS, ACL and a full complement of standards based IPv4 and IPv6 features includingOSPF, BGP and PBR• Enhanced mirroring capabilities including local mirroring, Remote Port Mirroring (RPM), and Encapsulated Remote Port Mirroring(ERPM).• Converged network support for Data Center Bridging, with priorityflow control (802.1Qbb), ETS (802.1Qaz), DCBx and iSCSI TLV* Note that units configured in the PSU to IO airflow direction are subject to tighter restrictions for power consumptions on cables and optics used for 400GbE ports** Available post launchPhysical1 RJ45 console/management port with RS232signaling1 10/100/1000BASE-T Ethernet for management 1 USB 2.0 type A storage port32x400GbE QSFP56-DD ports + 2xSFP+10GbEChassisSize: 1 RU, 1.73”h x 17.3”w x 25.8”d(4.38h x 43.8w x 6.56d)Weight: 22 lbs (9.98 kg)EnvironmentalPower supply: 200-240 VAC 50/60 HzMax Power consumption: 1500 WattsT yp. Power consumption: 900 WattsMax Operating specifications:AC Max. Operating specifications:Operating temperature: 32° to 113°F(0° to 45°C)Operating humidity: 10 to 90% (RH),non-condensingMax. Non-operating specifications:Storage temperature: –40° to 158°F(–40° to 70°C)Storage humidity: 5 to 95% (RH),non-condensingFresh air Compliant to 45°CRedundancyHot swappable redundant power (2 per switch) Hot swappable redundant fans (7 per switch) PerformanceSwitch fabric capacity: 25.6Tbps (full duplex) Forwarding capacity: up to 5.1TppsLatency: sub 700nsPacket buffer memory: 64MBCPU memory: 32GBMAC addresses: 8KARP table: 16K standalone, 8K sharedIPv4 routes: up to 400K (ALPM)IPv6 routes: 300KMulticast hosts: 1KMulticast IPv6 Routes : 4KLayer 2 VLANs: 4KMSTP: 64 instancesLAG load balancing: Based on layer 2, IPv4 or IPv6 headersFollowing SW information relative to Dell EMC SmartFabric OS10:IEEE compliance802.1AB LLDPTIA-1057 LLDP-MED802.3ad Link Aggregation802.1D Bridging, STP802.1p L2 Prioritization802.1Q VLAN T agging802.1Qbb PFC802.1Qaz ETS802.1X Network Access Control802.3ac Frame Extensions forVLAN T agging802.3x Flow ControlLayer2 Protocols802.1D Compatible802.1p L2 Prioritization802.1Q VLAN T agging802.1s MSTP802.1w tRSTP 802.1t RPVST+VLT (Virtual Link Trunking)VRRP Active/ActiveRSTP & RPVST+Port Mirroring on VLT portsDCB, iSCSI, FSB on VLTRPM/ERPM over VLTVLT Minloss upgradeRFC Compliance768 UDP793 TCP854 Telnet959 FTP1321 MD51350 TFTP2474 Differentiated Services2698 Two Rate Three Color Marker3164 Syslog4254 SSHv2General IPv4 Protocols791 IPv4792 ICMP826 ARP1027 Proxy ARP1035 DNS (client)1042 Ethernet Transmission1191 Path MTU Discovery1305 NTPv41519 CIDR1812 Routers, Static Routes1858 IP Fragment Filtering2131 DHCPv4 (server and relay)5798 VRRPv33021 31-bit Prefixes1812 Requirements for IPv4 Routers1918 Address Allocation for PrivateI nternets2474 Diffserv Field in IPv4 and Ipv6Headers2597 Assured Forwarding PHB Group3195 Reliable Delivery for Syslog3246 Expedited Forwarding PHB GroupVRF (BGPv4/v6)General IPv6 Protocols1981 Path MTU for IPv62372 IPv6 Addressing2460 IPv6 Protocol Specification2461 Neighbor Discovery2462 Stateless Address AutoConfig2711 IPv6 Router alert2463 ICMPv62464 Ethernet Transmission2675 IPv6 Jumbograms3484 Default Address Selection3493 Basic Socket Interface4291 Addressing Architecture3542 Advanced Sockets API3587 Global Unicast Address Format4291 IPv6 Addressing2464 Transmission of IPv6 Packets overEthernet Networks2711 IPv6 Router Alert Option4007 IPv6 Scoped Address Architecture4213 Transition Mechanisms for IPv6Hosts and Routers3633 DHCPv6 RelayOSPF1745 OSPF/BGP interaction1765 OSPF Database overflow2154 OSPF with DigitalSignatures2328 OSPFv25340 OSPF for IPv6 (OSPFv3)2370 Opaque LSA3101 OSPF NSSA4552 OSPFv3 AuthenticationMulticast2236 IGMPv2 Snooping3810 MLDv2 SnoopingSecurity2865 RADIUS3162 Radius and IPv63579 Radius support for EAP3580 802.1X with RADIUS3826 AES Cipher in SNMP1492 TACACS (Authentication,Accounting)Control Plane, VTY & SNMP ACLsIP Access Control ListsBGP1997 Communities2385 MD52439 Route Flap Damping2796 Route Reflection2918 Route Refresh3065 Confederations4271 BGP-42545 BGP-4 Multiprotocol Extensions forIPv6 Inter-Domain Routing2858 Multiprotocol Extensions4360 Extended Communities4893 4-byte ASN5396 4-byte ASN Representation5492 Capabilities Advertisementdraft-ietf-idr-add-paths-04.txt ADD PATHLinux DistributionDebian Linux version 8Linux Kernel 3.16Network Management and MonitoringSNMPv1/2cIPv4/IPv6 Management support (T elnet, FTP,TACACS, RADIUS, SSH, NTP)SyslogPort MirroringRPM/ERPM3176 SFlowSupport Assist (Phone Home)RestConf APIs (Layer 2 features)XML SchemaCLI Commit (Scratchpad)Uplink Failure DetectionObject TrackingBidirectional Forwarding Detection (BFD)AutomationControl Plane Services APIsLinux Utilities and Scripting T oolsCLI Automation (Multiline Alias)Zero T ouch Deployment (ZTD)Ansible, Puppet, Chef, SaltStackQuality of ServicePrefix ListRoute-MapRate Shaping (Egress)Rate Policing (Ingress)Scheduling AlgorithmsRound RobinWeighted Round RobinDeficit Round RobinStrict PriorityWeighted Random Early DetectT echnical specifications3 © 2020 Dell Inc. All Rights Reserved.4© 2020 Dell Inc. All Rights Reserved.Data center bridging802.1Qbb Priority-Based Flow Control 802.1Qaz Enhanced Transmission Selection (ETS)Explicit Congestion NotificationData Center Bridging eXchange (DCBx)DCBx Application TLV (iSCSI, FCoE)RoCEv2Software Defined Networking OpenFlow 1.3 (Native)MIBS IP MIBIP Forward MIBHost Resources MIB IF MIBLLDP EXT1/3 MIB Entity MIB LAG MIBDell-Vendor MIB TCP MIB UDP MIB SNMPv2 MIB ETHERLIKE-MIB SFLOW-MIB PFC-MIBRegulatory compliance SafetyUL/CSA 60950-1, Second Edition EN 60950-1, Second EditionIEC 60950-1, Second Edition Including All National Deviations and Group DifferencesEN 60825-1 Safety of Laser Products Part 1: Equipment Classification Requirements and User’s GuideEN 60825-2 Safety of Laser Products Part 2: Safety of Optical Fibre Communication SystemsFDA Regulation 21 CFR 1040.10 and 1040.11EmissionsAustralia/New Zealand: AS/NZS CISPR 22:2006, Class ACanada: ICES-003, Issue-4, Class AEurope: EN 55022: 2006+A1:2007 (CISPR 22: 2006), Class AJapan: VCCI V3/2009 Class AUSA: FCC CFR 47 Part 15, Subpart B: 2011, Class A ImmunityEN 300 386 V1.4.1:2008 EMC for Network EquipmentEN 55024: 1998 + A1: 2001 + A2: 2003EN 61000-3-2: Harmonic Current Emissions EN 61000-3-3: Voltage Fluctuations and FlickerEN 61000-4-2: ESDEN 61000-4-3: Radiated Immunity EN 61000-4-4: EFT EN 61000-4-5: SurgeEN 61000-4-6: Low Frequency Conducted Immunity RoHSAll S Series components are EU RoHS compliant.CertificationsAvailable with US Trade Agreements Act (TAA) complianceUSGv6 Host and Router Certified on Dell Networking OS 9.5 and greater IPv6 Ready for both Host and Router UCR DoD APL (core and distribution ALSAN switch Warranty1 year return to depot constrainedLearn more at DellT /Networking© 2020 Dell Inc. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners.October 2020 | v1.8Dell EMC Z9332F-ON Series Spec SheetDellTechnologies ServicesConsultingDell T echnologies Consulting Services provides industryprofessionals with a wide range of tools and the experience your need to design and execute plans to transform your business. DeploymentAccelerate technology adoption with ProDeploy Enterprise Suite. Trust our experts to lead deployments through planning, configuration and complex integrations.ManagementRegain control of operations with flexible IT management options. Our Residency Services help you adopt and optimize new technologies and our Managed Services allow you to outsource portions of your environment to us.SupportIncrease productivity and reduce downtime with ProSupportEnterprise Suite. Expert support backed by proactive and predictive artificial intelligence cationDell T echnologies Education Services help you develop the IT skills required to lead and execute transformational strategies. Get certified today.Learn more atDellT /ServicesPlan, deploy, manage and support your IT transformation with our top-rated services。

Puppet⽂档:语⾔指南原⽂地址:Puppet语⾔通过资源描述的⽅式管理我们的机器,它让这⼀切⼯作都变得简单⽽有效。
本指南展⽰了Puppet语⾔是如何⼯作的,以及Puppet语⾔的⼀些基础概念。
学习Puppet语⾔⾮常重要,它是帮助你理解Puppet如何管理你的机器的关键。
Puppet语⾔相⽐其它编程语⾔⽽⾔是相当简单的。
阅读本指南,也可以帮助你了解⼤量其它⼈已经写好的Puppet模块。
页提供了关于模块的更多信息和链接。
名称中可接受的字符集变量名只能够包含字母数字和下划线,⼤⼩写敏感。
连字符是不允许的,有些Puppet版本允许它们,这是⼀个Bug。
类名,模块名,the names of defined,和⾃定义的资源类型被限制为只能使⽤⼩写字母,数字和下划线,且必须以⼩写字母开头,也就是必须匹配表达式[a-z][a-z0-9_]*。
有些名称违反了这些限制,但是⽬前能够正常⼯作,这是不建议的。
连字符是严重反对使⽤的,在新版本⾥⾯它会让类⾥⾯的变量不能够正常⼯作。
类和资源类型定义可以使⽤命名空间分割符(::)。
Class and defined resource type names can use :: as a namespace separator, which is both semantically useful and a means of directing the behavior of the module autoloader. The final segment of a name must obey the restrictions on variable names, and the preceding segments must obey the restrictions on class names.Parameters used in parameterized classes and defined resource types can include alphanumeric characters and underscores, cannot begin with an underscore, and are case-sensitive. In practice, they should be treated as though they were under the same restrictions as class names in order to maximize future compatibility.There is no practical restriction on resource names.Any word that the syntax uses for special meaning is a reserved word, meaning you cannot use it for variable or type names. Wordslike true, define, inherits, and class are all reserved. If you ever need to use a reserved word as a value, be sure to quote it.资源Puppet的基础是资源。

©2019 Mellanox Technologies. All rights reserved.†For illustration only. Actual products may vary.Mellanox SN2700 provides the most predictable, highest density 100GbE switching platform for the growing demands of today’s data centers.The SN2700 switch is an ONIE (Open Network Install Environment) based platform that supports amultitude of operating systems, as well as utilizing the advantages of Open Ethernet and the capabilities of the Mellanox Spectrum ® ASIC.The SN2700 has three modes of operation:–Preinstalled with Mellanox Onyx™ (successor to MLNX-OS Ethernet), a home-grown operating system utilizing common networking user experiences and industry standard CLI.–Preinstalled with Cumulus ® Linux, a revolutionary operating system taking the Linux user experience from servers to switches and providing a rich routing functionality for large scale applications. –Provided with a bare ONIE image ready to be installed with the aforementioned or other ONIE-based operating systems.The SN2700 switch is an ideal spine and top-of-rack (ToR) solution, allowing maximum flexibility, with port speeds spanning from 10Gb/s to 100Gb/s per port and port density that enables full rack connectivity to any server at any speed. The uplink ports allow a variety of blocking ratios that suit any application requirement.Powered by the Spectrum ASIC and packed with 32 ports running at 100GbE, the SN2700 carries a whopping throughput of 6.4Tb/s with a landmark 4.76Bpps processing capacity in a compact 1RU form factor.Keeping with the Mellanox tradition of setting performance record switch systems, the SN2700introduces the world’s lowest latency for a 100GbE switching and routing element, and does so while having the lowest power consumption in the market. With the SN2700, the use of 25, 40, 50 and 100GbE in large scale is enabled without changing power infrastructure facilities.The SN2700 is part of Mellanox’s complete end-to-end solution which provides 10GbE through 100GbE interconnectivity within the data center. Other devices in this solution include the ConnectX ® family of network interface cards, and LinkX ® copper or fiber cabling. This end-to-end solution is topped with Mellanox NEO® a management application that relieves some of the major obstacles when deploying a network. NEO enables a fully certified and interoperable design, speeds up time to service and eventually speeds up ROI.Spectrum-based 32-port 100GbE Open Ethernet PlatformSN2700 Open Ethernet SwitchPRODUCT BRIEFSWITCH SYSTEM †©2019 Mellanox Technologies. All rights reserved.The SN2700 introduces superior hardware capabilities including dynamic flexible shared buffers and predictable wire speed performance with no packet loss for any packet size.While Spectrum provides the thrust and acceleration that powers the SN2700, the system gets yet another angle of capabilities while running with a powerful x86-based processor, which allows this system to not only be the highest performing switch fabric element, but also gives the ability to incorporate a Linux running server into thesame device. This opens up multiple application aspects of utilizing the high CPU processing power and the best switching fabric to create a powerful machine with unique appliance capabilities that can improve numerous network implementation paradigms.While the SN2700 Ethernet switch series is aimed at the100/50/25GbE market, Mellanox offers the SN2700B series for the 40/10GbE market. SN2700B switches are priced comfortably for the 40/10GbE market and provide the superior feature set of Spectrum.FEATURESPower Specifications–Typical Power with passive cables (ATIS): 150W –Input range:100-127 VAC, 200-240VAC –Frequency: 50-60Hz, single phase AC, 4.5A, 2.9APhysical Characteristics–Dimensions:1.72’’ (43.8mm) H x 16.84’’ (427.83mm) W x 27’’ (686mm) D–Weight: 11.1kg (24.5lb)Supported Modules and Cables* –QSFP28, SFP28 (with QSA) shortand long range optics –QSFP28 to QSFP28 DAC cable –QSFP breakout cables 100GbE to4x25GbE and 40GbE to 4x10GbE DAC, optical–QSFP breakout cables 100GbE to2x50GbE DAC, optical –QSFP AOC –1000BASE-T and 1000BASE-SX/LX/ZX modules SPECIFICATIONS* Systems limited to 40GbE will support modules and cables accordingly* This section describes hardware features and capabilities. Please refer to the driver and firmware release notes for feature availability.Layer 2 Feature Set–Multi Chassis LAG (MLAG) –IGMP V2/V3, Snooping, Querier –VLAN 802.1Q (4K) –Q-In-Q–802.1W Rapid Spanning Tree –BPDU Filter, Root Guard –Loop Guard, BPDU Guard –802.1Q Multiple STP–PVRST+ (Rapid Per VLAN STP+)–802.3ad Link Aggregation (LAG) & LACP –32 Ports/Channel - 64 Groups Per System –Port Isolation –LLDP–Store & Forward / Cut-through mode of work –HLL–10/25/40/50/56/100GbE –Jumbo Frames (9216 BYTES)Layer 3 Feature Set–64 VRFs–IPv4 & IPv6 Routing inc Route maps: –BGP4, OSPFv2–PIM-SM & PIM-SSM (inc PIM-SM over MLAG)–BFD (BGP , OSPF, static routes) –VRRP–DHCPv4/v6 Relay–Router Port, int Vlan, NULL Interface for Routing–ECMP , 64-way–IGMPv2/v3 Snooping QuerierSynchronization–PTP IEEE-1588 (SMPTE profile) –NTPQuality of Service–802.3X Flow Control –WRED, Fast ECN & PFC–802.1Qbb Priority Flow Control –802.1Qaz ETS–DCBX – App TLV support–Advanced QoS- qualification, Rewrite, Policers – 802.1AB–Shared buffer managementManagement & Automation–ZTP–Ansible, SALT Stack, Puppet –FTP \ TFTP \ SCP–AAA , RADIUS \ TACACS+ \ LDAP –JSON & CLI , Enhanced Web UI –SNMP v1,2,3–In-band Management –DHCP , SSHv2, Telnet –SYSLOG–10/100/1000 ETH RJ45 MNG ports –USB Console port for Management –Dual SW image –Events history –ONIENetwork Virtualization–VXLAN EVPN – L2 stretch use case –VXLAN Hardware VTEP – L2 GW–Integration with VMware NSX & OpenStack, etcSoftware Defined Network (SDN)–OpenFlow 1.3: • Hybrid• Supported controllers: ODL, ONOS, FloodLight, RYU Docker Container–Full SDK access through the container –Persistent container & shared storageMonitoring & Telemetry–What Just Happened (WJH) –sFlow–Real time queue depth histograms & thresholds–Port mirroring (SPAN & RSPAN) –Enhanced Link & Phy Monitoring –BER degradation monitor –Enhanced health mechanism –3rd party integration (Splunk, etc.)Security–USA Department of Defense certification – UC APL–System secure mode – FIPS 140-2 compliance –Storm Control–Access Control Lists (ACLs L2-L4 & user defined)–802.1X - Port Based Network Access Control –SSH server strict mode – NIST 800-181A –CoPP (IP filter) –Port isolation© Copyright 2019. Mellanox Technologies. All rights reserved.Mellanox, Mellanox logo, Mellanox Open Ethernet, MLNX-OS, LinkX, Mellanox NEO, Mellanox Spectrum and ConnectX are registered trademarks of Mellanox Technologies, Ltd. Mellanox Onyx is a trademark of Mellanox Technologies, Ltd. All other trademarks are property of their respective owners.52993PB Ver 2.4T able 2 - SN2700B Series Part Numbers and DescriptionsC2P – Connector-to-Power supply airflow, P2C – Power supply-to-Connector airflow.。

前端开发中的自定义滚动条样式技巧前端开发中,滚动条是一个经常出现的组件。
然而,浏览器默认的滚动条样式往往单调且不够美观。
为了提升用户体验,工程师们开始探索如何自定义滚动条样式。
下面将介绍一些自定义滚动条样式的技巧。
1. 使用CSS属性`overflow`来实现滚动条的显示与隐藏。
在CSS中,我们可以将一个元素的`overflow`设置为`scroll`或`auto`来显示滚动条,或者将其设置为`hidden`来隐藏滚动条。
2. 通过使用`::-webkit-scrollbar`伪类来对滚动条进行自定义样式。
这个伪类可以针对WebKit内核浏览器(如Chrome和Safari)进行样式的设置。
例如,我们可以使用`::-webkit-scrollbar`来设置滚动条的宽度、颜色和背景。
3. 使用`::-webkit-scrollbar-track`伪类来设置滚动条的轨道样式。
通过设置这个伪类的背景色或背景图片,我们可以改变滚动条轨道的外观。
4. 通过使用`::-webkit-scrollbar-thumb`伪类来设置滚动条的滑块样式。
我们可以通过设置这个伪类的背景色或背景图片,来改变滚动条滑块的外观。
5. 使用`::-webkit-scrollbar-corner`伪类来设置滚动条的角落样式。
通过设置这个伪类的背景色或背景图片,我们可以改变滚动条角落的外观。
6. 使用`::-webkit-scrollbar-button`伪类来设置滚动条的按钮样式。
通过设置这个伪类的背景色或背景图片,我们可以改变滚动条按钮的外观。
7. 在非WebKit内核的浏览器中,我们可以使用一些JavaScript库来实现对滚动条样式的自定义。
例如,`perfect-scrollbar`是一个非常流行的用于自定义滚动条样式的轻量级库。
它通过提供一组API来改变滚动条的外观,如设置滑块颜色、宽度和高度等。
8. 在自定义滚动条样式时,我们还可以考虑一些交互设计。
Puppet使用方法总结1. 概述puppet是一个开源的软件自动化配置和部署工具,它使用简单且功能强大,正得到了越来越多地关注,现在很多大型IT公司均在使用puppet 对集群中的软件进行管理和部署,如google利用puppet管理超过6000台地mac桌面电脑。
本文主要介绍puppet安装方法,设计架构及使用方法。
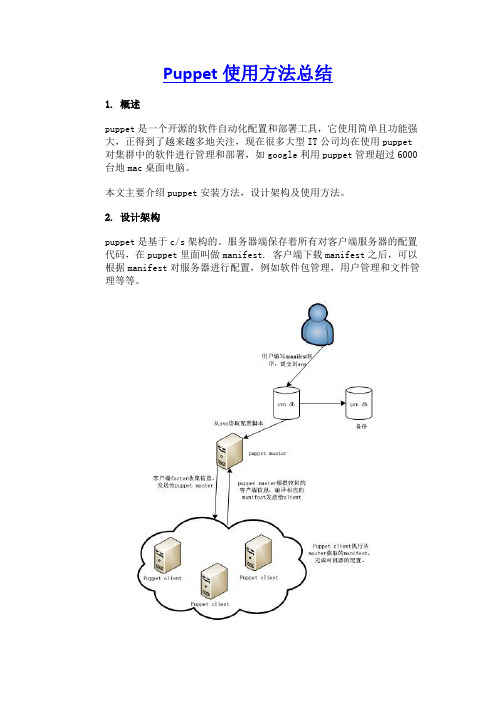
2. 设计架构puppet是基于c/s架构的。
服务器端保存着所有对客户端服务器的配置代码,在puppet里面叫做manifest. 客户端下载manifest之后,可以根据manifest对服务器进行配置,例如软件包管理,用户管理和文件管理等等。
如上图所示,puppet的工作流程如下:(1)客户端puppetd调用facter,facter探测出主机的一些变量,例如主机名,内存大小,ip地址等。
pupppetd 把这些信息通过ssl连接发送到服务器端;(2)服务器端的puppetmaster 检测客户端的主机名,然后找到manifest里面对应的node 配置,并对该部分内容进行解析,facter送过来的信息可以作为变量处理,node牵涉到的代码才解析,其他没牵涉的代码不解析。
解析分为几个阶段,语法检查,如果语法错误就报错。
如果语法没错,就继续解析,解析的结果生成一个中间的“伪代码”,然后把伪代码发给客户端;(3)客户端接收到“伪代码”,并且执行,客户端把执行结果发送给服务器;(4)服务器端把客户端的执行结果写入日志。
puppet工作过程中有两点值得注意,第一,为了保证安全,client和master之间是基于ssl和证书的,只有经master证书认证的client可以与master通信;第二,puppet会让系统保持在你所期望的某种状态并一直维持下去,如检测某个文件并保证其一直存在,保证ssh服务始终开启,如果文件被删除了或者ssh服务被关闭了,puppet下次执行时(默认30分钟),会重新创建该文件或者启动ssh服务。

mescroll-uni 自定义参数-概述说明以及解释1.引言1.1 概述mescroll-uni是一种用于实现上拉加载更多和下拉刷新功能的uni-app插件,它提供了丰富的参数和事件监听,可以灵活地定制页面滚动效果。
通过简单的配置,开发者可以轻松地实现页面的无限滚动和数据的动态加载,提升用户体验和页面性能。
mescroll-uni插件的设计理念是简单易用,开发者只需要简单的配置参数就可以实现各种滚动效果,无需复杂的逻辑和代码编写。
同时,mescroll-uni也提供了丰富的文档和示例,帮助开发者快速上手并加速开发进度。
在现如今移动应用开发的日益普及的环境下,mescroll-uni插件的出现为开发者提供了更加方便快捷的解决方案,使得开发者可以更加专注于业务逻辑的实现,而不必花费大量时间和精力在页面滚动效果的实现上。
随着移动应用的发展和用户体验的需求不断提升,mescroll-uni插件无疑将成为开发者们不可或缺的利器。
1.2 文章结构本文共分为三个部分,分别是引言、正文和结论。
在引言部分,将介绍mescroll-uni的概述、文章结构和目的,为读者提供对整篇文章的整体认识。
在正文部分,将详细介绍什么是mescroll-uni以及它的优势,帮助读者更深入地了解这一工具的功能和特点。
同时,还将说明如何使用mescroll-uni自定义参数,为读者提供具体的操作指导。
在结论部分,将总结mescroll-uni的重要性,并探讨其在未来的应用前景。
同时,还将引导读者进一步了解mescroll-uni的相关信息,为他们深入学习和应用提供指导。
通过以上三个部分的内容,本文旨在全面介绍mescroll-uni,帮助读者更好地理解和运用这一工具。
1.3 目的本文的主要目的是介绍如何在使用mescroll-uni插件时自定义参数,以满足不同项目的需求。
通过了解mescroll-uni的自定义参数功能,开发者可以更灵活地控制插件的行为和样式,从而提升用户体验和页面交互效果。

puphpeteer 手册
Puppeteer是一个由Google开发的Node.js库,它提供了一个高级API来通过DevTools协议控制Chromium或Chrome浏览器。
它可以用于模拟用户操作,进行自动化测试,截取页面截图,生成PDF等操作。
Puppeteer的手册包括了许多方面的内容,我会从以下几个方面来回答你的问题。
首先,我们来看Puppeteer的基本用法。
你可以通过安装Node.js和npm来安装Puppeteer,然后编写代码来启动浏览器、打开页面、进行操作等。
手册中会详细介绍如何使用Puppeteer的API来实现这些功能。
其次,Puppeteer还提供了丰富的API来模拟用户操作,比如点击、输入、滚动等。
手册中会详细介绍这些API的使用方法,以及如何结合这些API来实现复杂的操作。
此外,Puppeteer还支持截取页面截图、生成PDF等功能。
手册中也会介绍如何使用Puppeteer来实现这些功能,并且会给出一些示例代码来帮助你快速上手。
最后,Puppeteer的手册还会介绍一些高级功能,比如如何进行性能分析、如何调试代码等。
这些内容会帮助你更深入地了解Puppeteer,并且能够帮助你解决一些复杂的问题。
总的来说,Puppeteer的手册会从基础到高级,从简单的操作到复杂的功能,全面地介绍Puppeteer的使用方法和技巧。
阅读手册可以帮助你更好地掌握Puppeteer,提高自己的开发效率。
希望这些信息能够帮助到你。


uni-appswiper设置⾃定义⾼度话不多少先上图,⼤家可以看到图⽚中红⾊区域是头部区域,黄⾊区域则是我们要滑动的区域。
⼤家可以在uni-app官⽹上看到swiper⾼度是默认100%,⽽swiper-item则是要有固定宽⾼的,要的效果是什么呢?1.点击tab可以切换黄⾊区域视图2.滑动黄⾊区域改变视图,⽀持横向滑动以及纵向滑动我的思路:因为swiper是要固定⾼度的,它并不会因为内容⽽⾃动撑开,那么我的想法呢就是,1.给swiper⼀个⽗元素,⽗元素设置⾃适应⾼度,也就是黄⾊区域的⾼度,然后动态赋值给swiper,1.先考虑整个视图的⾼度,以及布局,我是把他分为两⼤块,也就是红⾊区域以及黄⾊区域,⽤flex布局,让红⾊区域固定⾼度,黄⾊区域⾃动撑满全屏。
注意:当然也可以使⽤定位的⽅法,计算出红⾊区域的⾼度然后黄⾊区域设置定位就可以啦,因为我们要的布局⽅式是黄⾊区域超出范围后可以上下滑动。
上代码:home是整个页⾯的盒⼦,footer是黄⾊区域的盒⼦,给home设置flex上下排列,footer设置flex不会flex弹性盒⼦布局的⼩伙伴可以问度娘。
2.这个时候你会发现你设置完成之后还是⽆法⽣效的,这是因为你的最外层盒⼦的⾼度并没有改变,这个时候我们就要动态设置最外层盒⼦的⾼度了。
我的实现思路是:获取⼿机屏幕⾼度,然后赋值给最外层盒⼦,也就是上边的home,这个时候就会撑满全屏,当然也会根据屏幕的⼤⼩⾃动改变的。
我⽤的⽅法呢是uni-app ⾥边的⼀个原⽣⽅法 uni.getSystemInfo()这个⽅法呢可以获取⼿机的基本信息,给⼤家看下所有信息。
⼤家可以看到⾥边有两个⾼度,⼀个是屏幕⾼度,⼀个是可视区域⾼度,我们使⽤第⼆个得到⼿机可视区域后赋值给home这个时候布局就会⽣效,3.在footer,也就是黄⾊区域⾃动撑满之后,我们就可以获得到黄⾊区域的⾼度,当然使⽤uni-app提供的⽅法uni.createSelectorQuery().select('.footer'); //获取某个元素的信息,然后动态赋值给swiper,这个时候swiper就会撑满黄⾊区域,当然我们结合scroll-view就可以实现上下滑动,以及左右滑动的效果了。

Puppet之ruby模块说明1 说明使用自定义facter分别获取客户端ip地址和网卡名称,不需要在客户端安装脚本2 配置管理服务器和被管理服务器都要配置#vim /etc/puppet/puppet.conf[main]factpath=$vardir/lib/facterpluginsync=true新建目录以nrpe模块为例mkdir -p /etc/puppet/modules/nrpe/lib/facter3 脚本#cd /etc/puppet/modules/nrpe/lib/facter获取外网网卡脚本vim wannetcard.rbFacter.add(:wanname) dosetcode do%x{ /sbin/ifconfig|egrep -v "127\.0\.0\.1\|192\.168\.7\."|grep -B 1 "inet addr:"|grep "eth"|/usr/bin/awk '{print $1}'|grep -v ":" }.chompendend获取内网网卡脚本vim lannetcard.rbFacter.add(:lanname) dosetcode do%x{/sbin/ifconfig|grep -B 1 "192\.168\.7\."|grep "eth"|awk '{print $1}'|grep -v ":"}.chompendend获取客户端外网IPFacter.add(:getip) doconfine :kernel => :linuxsetcode doip = niloutput = %x{/sbin/ifconfig|egrep -v 'eth0[::]|eth1[:space:]'|grep -A1 "eth"|grep "inet addr:"}# a=output.split(/^\S/)# a.each { |str| print str}output.split(/^\S/).each { |str|if str =~ /inet addr:([0-9]+\.[0-9]+\.[0-9]+\.[0-9]+)/tmp = $1unless tmp =~ /^192\.168\.7/ip = tmpbreakendend}ipendEnd获取本地snmpd的pid值Facter.add(:getkey) docase RUBY_PLA TFORMwhen /linux/ios_family = "redhat"when /solaris/ios_family = "solaris"when /ix/i, /gnu/i,/sysv/i,/sunos/i,/bsd/ios_family = "unix"when /win/i, /ming/ios_family = "windows"elseos_family = "other"endif os_family == "redhat" thenif File.exist?("/etc/rndc.key")thensetcode do%x{/bin/cat /var/run/snmpd.pid }.chompendendendend4 erb模版调用# vim test.erb外网IP::<%= getip %>外网网卡:<%= wanname %>内网网卡:<%= lanname %>。

Puppeteer使⽤⽰例详解PhantomJS曾经是⽆头浏览器⾥的王者,测试、爬⾍等都在使⽤,随着GoogleChrome Headless的出现,PhantomJS的作者已经明确表⽰不在更新,⽽GoogleChrome Headless将会是未来爬⾍的趋势,⽽测试将依然会使⽤Webdriver那套⽅案,GoogleChrome Headless 可以利⽤WebDriver调⽤,也可以使⽤其集成的API——Puppeteer(操纵⽊偶的⼈),他的功能和他的名字⼀样强⼤,可以随意操控Chrome或Chromeium,缺点就是只有node的API,来看看他的图标:Puppeteer是基于DevTools协议来控制headless Chrome的Node库,依赖6.4以上版本的node,本⼈是在接触这个软件时才开始学习node,依然感觉到它的异步async/await超级强⼤,在Puppeteer中也⼤量使⽤异步来完成任务。
Puppeteer的安装可以使⽤node的包管理⼯具npm来安装:npm i puppeteer这⾥安装时会⾃动安装Chromeium,如果不需要则可以通过配置npm跳过下载,做为⼀名爬⾍⼯程师我不会去讨论测试相关的使⽤,接下来看看如何使⽤,和WebDriver类似,⾸先需要实例化brower,代码如下:const puppeteer = require('puppeteer');(async () => {const browser = await unch();const page = await browser.newPage();await page.goto('');await browser.close();})();这段代码执⾏结束时,你可能什么也没有感觉到,因为它在后台启动了⼀个Chromeium进程,打开了百度⾸页,接着就关闭了,当然我们可以在前台打开Chromeium,这⾥就需要配置⼀下,所配置参数只需传⼊launch()即可,常⽤参数如下:headless: 是否打开浏览器,默认为trueignoreHTTPSErrors: 是否忽略https错误,默认为trueexecutablePath: 配置要调⽤浏览器的可执⾏路径,默认是同Puppeteer⼀起安装的ChromeiumslowMo:指定的毫秒延缓Puppeteer的操作args:设置浏览器的相关参数,⽐如是否启动沙箱模式“--no-sandbox”,是否更换代理“--proxy-server”,具体参数请使⽤⽰例如下:const browser = await unch({headless:false, args: ["--no-sandbox",]}) //打开浏览器打开新的窗⼝:const page = await browser.newPage();设置窗⼝⼤⼩await page.setViewport({width: 1920,height: 1080过滤不需要的请求:await page.setRequestInterception(true);page.on('request', interceptedRequest => {if (interceptedRequest.url().endsWith('.png') || interceptedRequest.url().endsWith('.jpg'))interceptedRequest.abort();elseinterceptedRequest.continue();});为浏览器设置userAgent:await page.setUserAgent("Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36 Edge/16.16299")设置cookie,const data = {name: "smidB2",domain: "",value: "201806051502283cf43902aa8991a248f9c605204f92530032f23ef22c16270"}await page.setCookie(data)⽰例中只是演⽰,真实的cookie是⼀个列表形式的,需要循环添加才可以for(let data of cookies){await page.setCookie(data)}请求url:const url = ""await page.goto(url, { waitUntil: "networkidle2" });设置页⾯等待时间:await page.waitFor(1000); // 单位是毫秒等待页⾯某个元素加载完成await page.waitForSelector("input[class='usrname']")点击某个元素await page.click("input[class='submit']")利⽤page.evaluate()函数拖动⿏标⾄页⾯底部,原理就是在页⾯注⼊js代码。
Puppet之ruby模块说明
1 说明
使用自定义facter分别获取客户端ip地址和网卡名称,不需要在客户端安装脚本
2 配置
管理服务器和被管理服务器都要配置
#vim /etc/puppet/puppet.conf
[main]
factpath=$vardir/lib/facter
pluginsync=true
新建目录
以nrpe模块为例
mkdir -p /etc/puppet/modules/nrpe/lib/facter
3 脚本
#cd /etc/puppet/modules/nrpe/lib/facter
获取外网网卡脚本
vim wannetcard.rb
Facter.add(:wanname) do
setcode do
%x{ /sbin/ifconfig|egrep -v "127\.0\.0\.1\|192\.168\.7\."|grep -B 1 "inet addr:"|grep "eth"|/usr/bin/awk '{print $1}'|grep -v ":" }.chomp
end
end
获取内网网卡脚本
vim lannetcard.rb
Facter.add(:lanname) do
setcode do
%x{/sbin/ifconfig|grep -B 1 "192\.168\.7\."|grep "eth"|awk '{print $1}'|grep -v ":"}.chomp
end
end
获取客户端外网IP
Facter.add(:getip) do
confine :kernel => :linux
setcode do
ip = nil
output = %x{/sbin/ifconfig|egrep -v 'eth0[::]|eth1[:space:]'|grep -A1 "eth"|grep "inet addr:"}
# a=output.split(/^\S/)
# a.each { |str| print str}
output.split(/^\S/).each { |str|
if str =~ /inet addr:([0-9]+\.[0-9]+\.[0-9]+\.[0-9]+)/
tmp = $1
unless tmp =~ /^192\.168\.7/
ip = tmp
break
end
end
}
ip
end
End
获取本地snmpd的pid值
Facter.add(:getkey) do
case RUBY_PLA TFORM
when /linux/i
os_family = "redhat"
when /solaris/i
os_family = "solaris"
when /ix/i, /gnu/i,/sysv/i,/sunos/i,/bsd/i
os_family = "unix"
when /win/i, /ming/i
os_family = "windows"
else
os_family = "other"
end
if os_family == "redhat" then
if File.exist?("/etc/rndc.key")
then
setcode do
%x{/bin/cat /var/run/snmpd.pid }.chomp
end
end
end
end
4 erb模版调用
# vim test.erb
外网IP::<%= getip %>
外网网卡:<%= wanname %>
内网网卡:<%= lanname %>。